VPN + User/Pass Use case¶
The following scenario will guide you to deploy the UNAC (Universal Network Access) use case. There will be an integration between openNAC and any moderm VPN concentator, it doesnt matter if there are an SSL-VPN or IPSEC one.
Before starting is required to ensure that the following steps are been taken.
- To introduce to openNAC technologies is recommended to follow and read the overview about openNAC solution.
- To design an openNAC technologies is required to understand and follow network requirements.
- As soon as you have deployed the openNAC is recommended to select the proper use case that fits with you requirements.
- Selecting the use case, an scenario must be configured to covert as much as possible customer needs.
This page shows which steps are required to configure UNAC with VPNs based on User and Password.
1. DEFINITION (What is it?)¶
This scenario allows manage secure remote access for all your assets, endpoints and users using corporative identities/credentials, commonly LDAP, Active directory or local users registered in openNAC. In the following guide will be used a VPN using as authentication method username and password. Certificate based or OTP is out of this scope.
2. REQUIREMENTS¶
- Is required to have an openNAC Core server deployed, please use the following link to deploy openNAC CORE,(Mandatory), previous configuration must be in place because those components will be used when configuration is created as explained in the settings sections.
- This guide will include the openNAC Core deployment.
- Is not required to carry out the Active directoy joining process.
- In this scenario is not required to configure any UDS (user data source configuration).
- Please complete all the steps before starting this scenario.
- Is required to have an openNAC Analytics deployed,please use the following link to deploy openNAC Analytics,(optional), this module is not required to the usecase itself but is critical to provide customer’s value, reporting, dashboard and search engine are available with its installation.
- Network device(VPN concentator), the solution support SSL and IPSEC, Please use the following link to review VPN concentrator configuration guides., if you dont find you concentator in the network compatibility matrix for VPNs. the please ask for support.
- A Client PC to establish the VPN connection, in the following scenario will be used vendor VPN agent (fortigate, paloalto o any other agent) or the connection plugin in the VPN-SSL webportals, openNAC support IPSEC and SSL VPNs.
- To have an Active server deployed for user autentication, in the following example is not used groups in active directory for authorization. The user used is “user1”, this authentication process is managed by radius component that in the openNAC Core server.
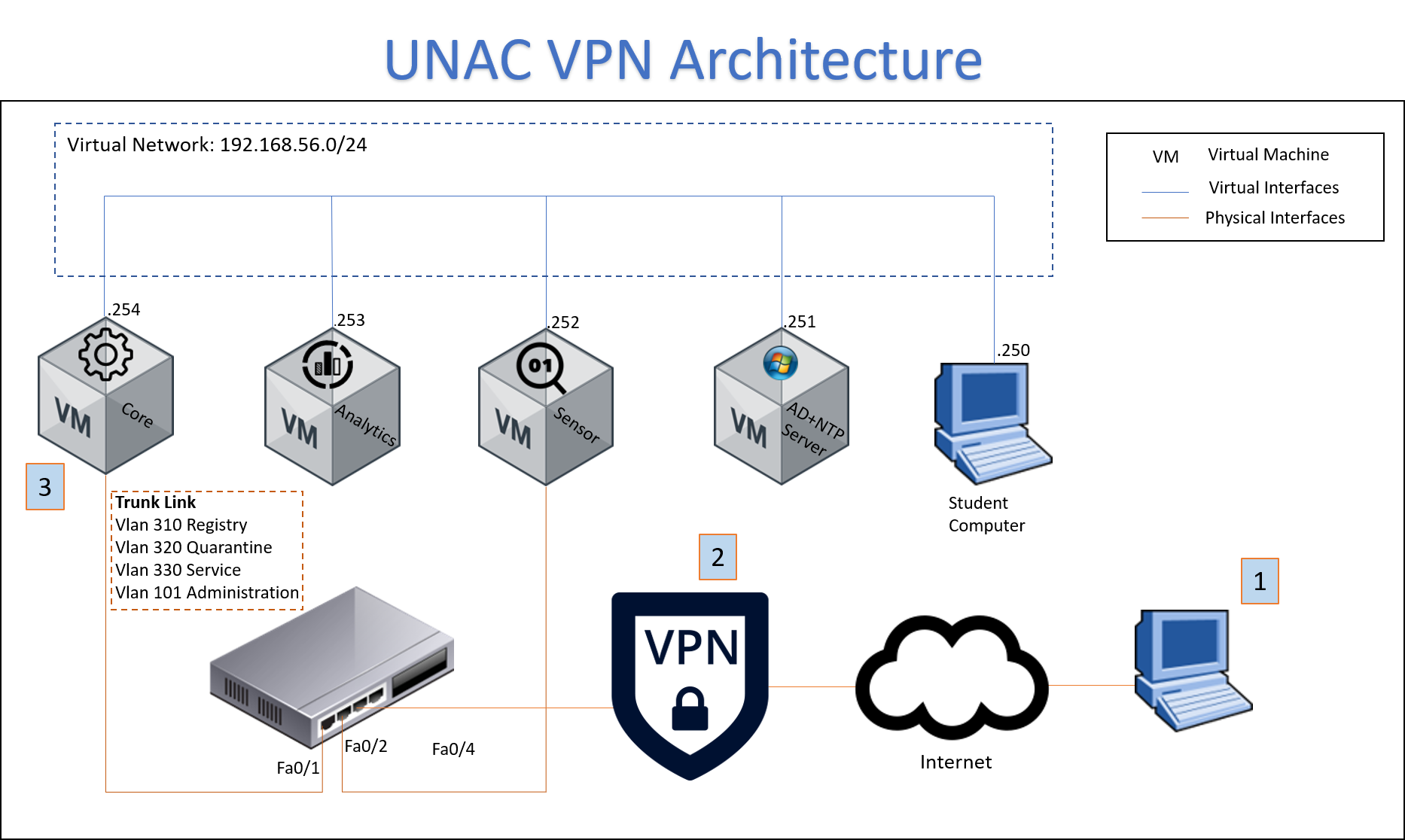
3. SCENARIO ARCHITECTURE¶
To understand the scenario please understand the following steps as shown by the following picture.
- Number 1 is the client which tries to connect to enterprise network and start the process for network access against the VPN concentrator.
- Number 2 is the the VPN concentrator which receive the autentication attempt from the client and send an authentication request to the openNAC Core Server.
- Number 3 is the openNAC Core with receive the network access request from the VPN concentator (via radius).
- openNAC Core use its policy engine to allow and deny the access and check the credential against corporative active directory.
- If there is a rule where authentication is granted the openNAC Core will send and message to accept the network access attempts (via radius).
4. DEPLOYMENT (Do it yourself)¶
On VPN Concentrator
Now its time to prepare the configuration related with VPN concentrator, many vendor has been tested and certified with openNAC tecnologies, please visit the VPN configuration section, there you will have the documented vendor, openNAC use standar protocols and methods and this means that any moderm VPN concentrator could be easily integrated with openNAC technologies.
On Core
As soon as the VPN concentrator is configured via Radius with openNAC, now it’s time to start with the configuration over openNAC Core.
Step 1. Allows Network access from VPN¶
Connec to the openNAC Core via ssh and carry out the following changes:
First at all is required to allow VPN access, go to the file /etc/raddb/huntgroups, in this file is required to add the VPN concentrator to the “vpn” group, in the following scenario will be used the IP 10.10.36.254. This huntgroup can be changed and it’s related with the openNAC radius module, this is defined at /etc/raddb/modules/opennac with the following paramters, vpnHuntgroupName = vpn.
Both configuration are shown in the following two pictures.
Picture 1
Picture 2
As soon as the concentrator is required in the openNAC Core, go to the file /etc/raddb/clients.conf, with this there will be allowed the access to any network device (VPN, switch or WLC/APs) with the same preshared key to the entire network 10.0.0.0/8, in this case the preshared key (“testing123”) must match with the VPN PSK configured.
Step 2. Disable OTP autentication (optional)¶
By default openNAC has included OTP autentication for VPN access, in this scenario will not use OTP authentication and to modify it please make the following changes:
This configuration must be done the openNAC module for radius, this configuration file is localte at “/etc/raddb/modules/opennac” and set the otpAuth as shown by the picture bellow:
Step 3. Create a security policy¶
In order to allow the access to the VPN acces is required to create a policy as shown in the picture bellow:
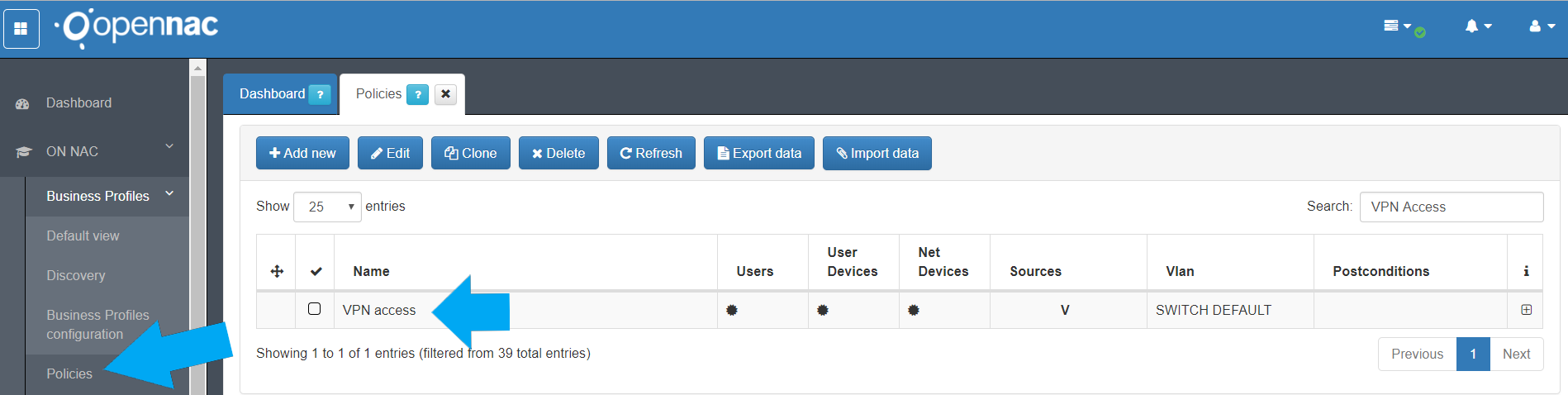
Note
The preconditions of “Users” is not set, openNAC will use all the options available, for instance, Active Directory users or local users.
The policy must have the following preconditions and conditions.
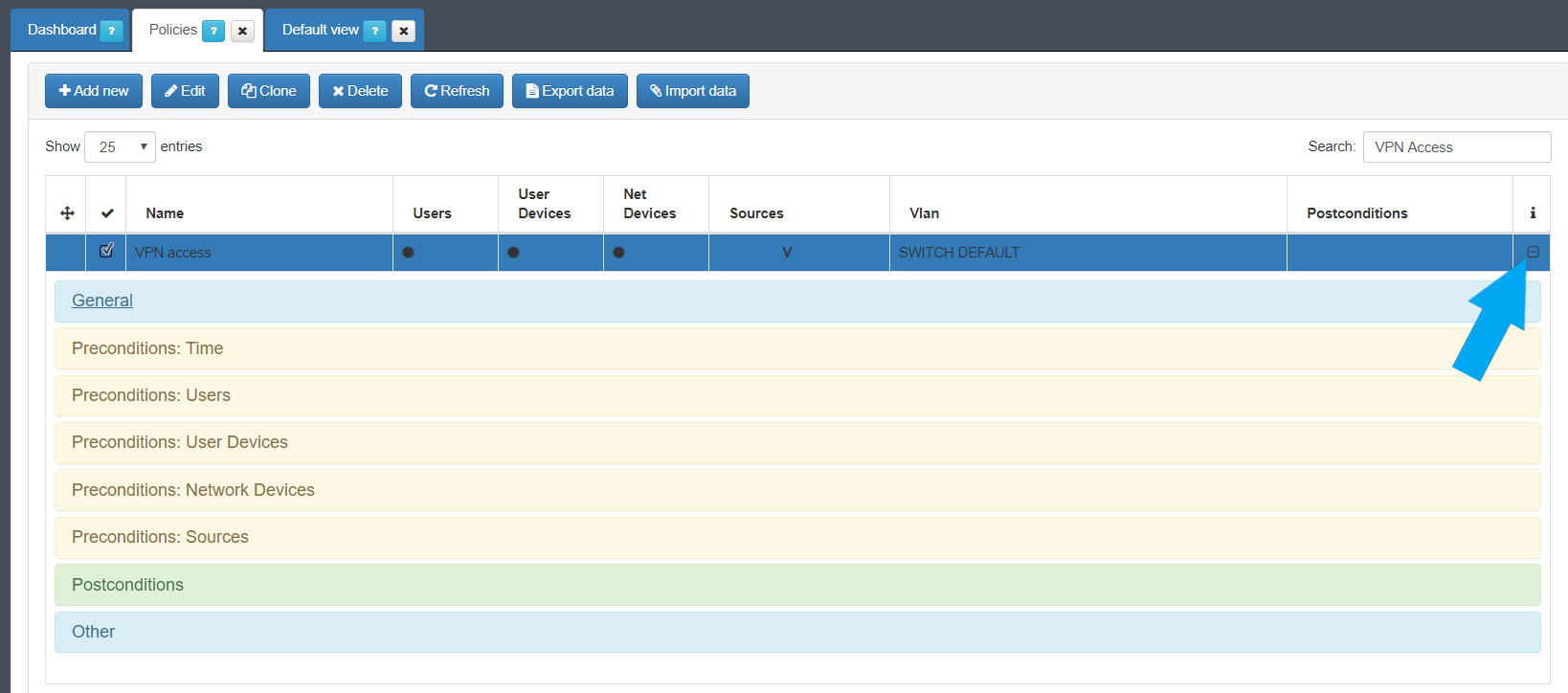
For the VPN access is required to modify the source:
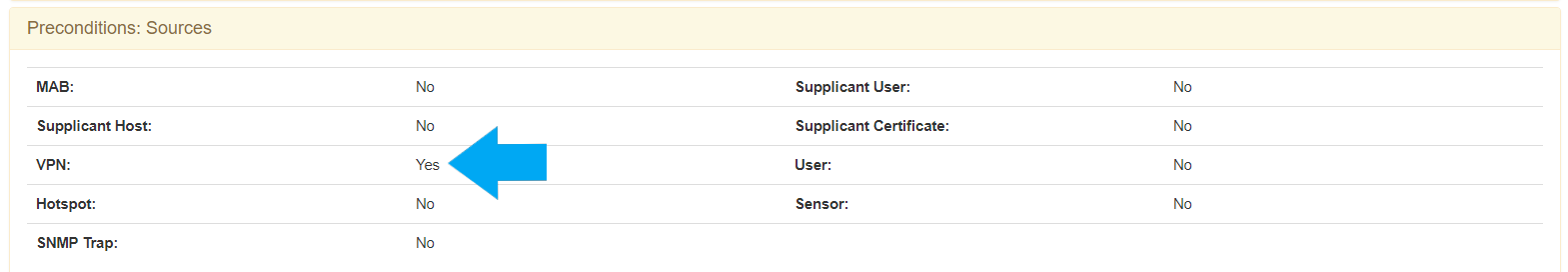
Is also required to define the post condition to assign the VLAN default.
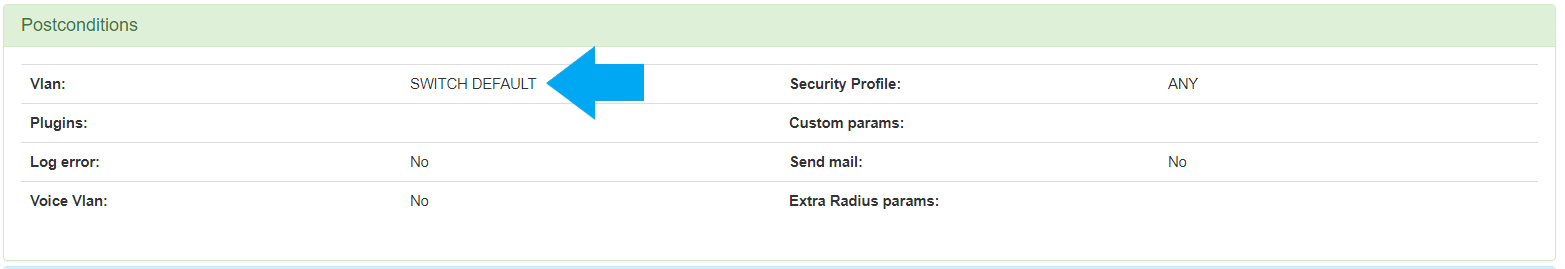
5. openNAC as VPN Authentication Backend (optional)¶
The purpose of this document is explain how to authenticate users from a VPN Server with openNAC, using radius capabilities as a backend authenticator.
Usually this kind of integration is to allow Active Directory users connect with VPN Server, and additionally One-Time Password (OTP) method could be used as two-factor authentication, so the following steps will be focused on it.
5.1 Join openNAC server to Active Directory¶
First of all, the openNAC server has to be joined with the domain to validate the user credentials. We recommend to follow the Active Directory Wizard or throught a manual integration
5.2 Install openNAC GAuth package¶
This package provides the required tools for One-Time Password (OTP) validation.
Once openNAC server is joined to an Active Directory, you have to check if opennac-gauth package is installed in your server:
rpm -qa | grep opennac-gauth
In case, it is not installed, you can install from openNAC repository:
yum install opennac-gauth
Note
Please ask for the proper package to be deployed.
With this package, two files will be installed in /usr/bin directory:
- gauth: It’s a binary executable to check the 6 digits OTP password concatenated with user password. The log is sent to /var/log/secure file.
- otp_auth: It’s a shell script to call gauth program, to check OTP password, and if OTP is correct then check the user credentials with ntlm_auth program.
5.3 Radius Configuration¶
- Configure a secret for the VPN server, depending on its IP address, in /etc/raddb/clients.conf file. These few lines could be as example to be added:
client 172.16.10.5 {
secret = testing123
shortname = VPNSever
}
- Configure a hunt group, in /etc/raddb/huntgroups file, to notify this IP address is a VPN server (multiple IP addresses can be defined in the same hunt group):
vpn NAS-IP-Address == 172.16.10.5
vpn NAS-IP-Address == 172.16.10.121
Note
The hunt group name used as VPN servers identification is “vpn” by default, but it can be modified in /usr/lib/python2.6/site-packages/opennac/log.config properties file, using the vpnHuntgroupName property.
- Create a new module to execute otp_auth. This module will be placed in /etc/raddb/modules/otp_auth file, with the following content:
exec otp_auth {
wait = yes
program = "/usr/bin/otp_auth '%{User-Name}' '%{User-Password}'"
}
- Use otp_auth if there is no other valid authentication methods found. So in authorize section of /etc/raddb/sites-available/default file, add these lines after pap line:
# If any module has set Auth-Type, neither PAP, we will try with OTPAuth.
if (!control:Auth-Type) {
update control {
Auth-Type = 'OTPAuth'
}
}
Note
In case there is configured previously a “NTLMAuth”, you have to replace to apply OTP check.
- In the same /etc/raddb/sites-available/default file, but in authenticate section, add these lines before any others:
Auth-Type OTPAuth {
otp_auth
}
- Restart radius service:
service radiusd restart
5.4 One-Time Password user configuration¶
In order to allow user to use OTP, we have to define a secret to share with him, to be used in a client program to generate a 6 digits Time-based OTP (TOTP).
This secret can be generated or regenerated using openNAC administration user interface and following Operation guide - OTP.
Another option, is manage the OTP users with openNAC API
An example of how to use the API from console, can be found in How to test REST API calls from console and there is a sample OTP script using API_CLI in “/usr/share/opennac/utils/api_cli/otp_sample.php” file.
5.5 Check One-Time Password¶
In order to check the properly configuration of One-Time Password, you can configure the secret assigned to a user with a Google Authenticator client.
This Google Authenticator client will generate a 6-digit OTP and you can check it with the following command:
/usr/bin/otp_auth userID Password_ActiveDirectory+OTP
where “userID” is the username managed by Active Directory and “Password_ActiveDirectory+OTP” is the Active Directory password concatenated with the 6-digit OTP If you want to check only the Active Directory password without OTP, you can use this command:
/usr/bin/ntlm_auth --username userID --password Password_ActiveDirectory --domain domainName
5.6 Use openNAC agent to connect OpenVPN server¶
If you would use openNAC agent as client to connect OpenVPN server, you can update the OpenVPN client configuration files from openNAC server. The OpenVPN client configuration files has to be defined from the openNAC Administration Portal in Configuration -> Agent -> OpenVPN option. More information can be found at openNAC Operational Guide.
With the server is fully configured, the agent is configured and we have the TOPT application.
- Go to the the task bar of the equipment that will be connected to the VPN and right-click the openNAC logo.
- Click on the VPN that you wish to connect.
- Fill in the connection information:
- Username: Active Directory username for VPN connection.
- Password: Active Directory password;
- OTP: 6 number code, displayed on Google Authenticator or another TOPT application.
6. TESTING¶
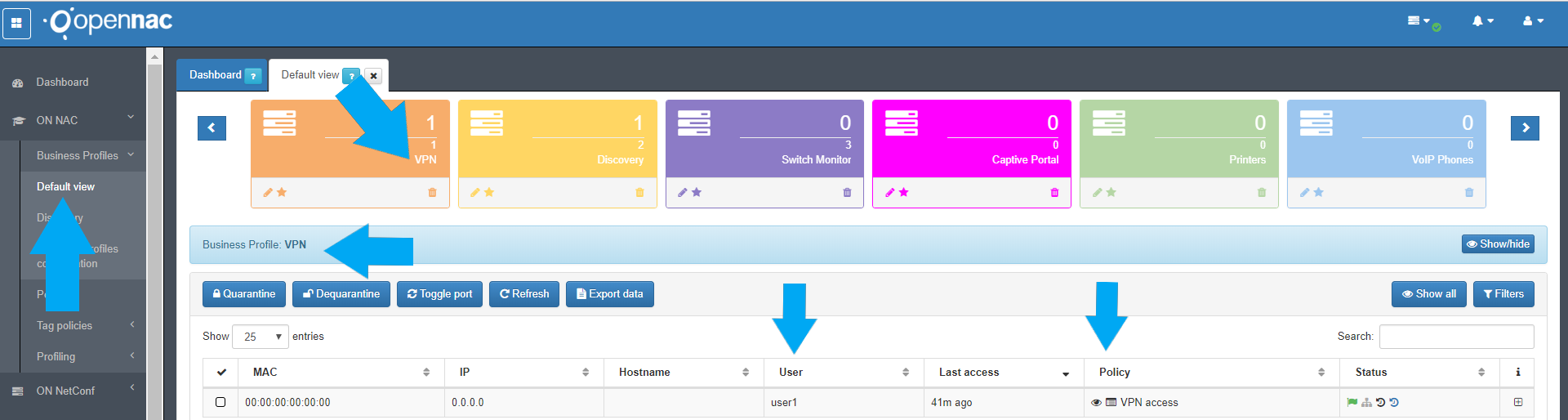
openNAC allows us to view the current sessions status using the business profiles as shown by the picture bellow:
- Go to ON NAC -> Business Profiles.
- Go to Default view.
- Select the business profile VPN which is being used as filter to find the VPN easily, to know more about business profiles please, go to :ref:business profile section`<business_profiles>`.
- When the connection has been established.
- Which policy math the conection.
- Whic user was used.