COMPLIANCE DEPLOYMENT¶
This page shows which steps are required to configure endpoint compliance use case.
This use case allows to identify End-Points which compliance a defined policy customized by each company and aligned its internal security policy. The process for allow the End Point Compliance use case is described in the next image.
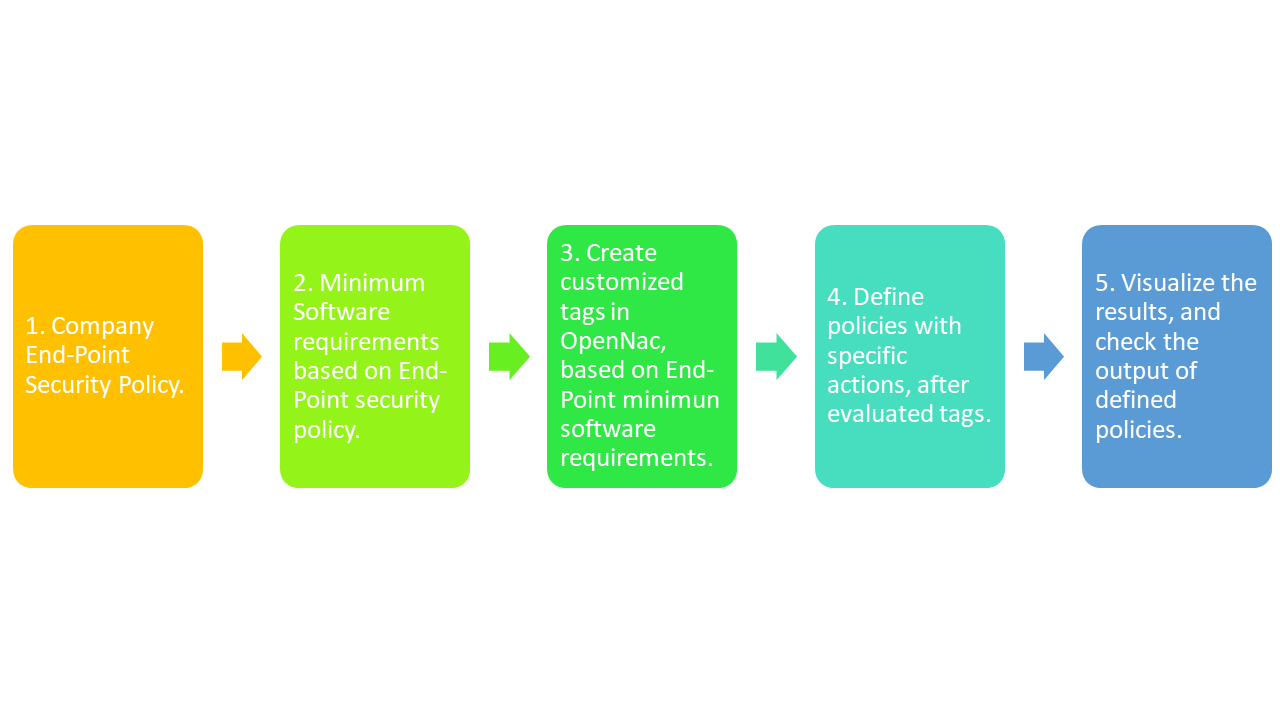
How OpenNac achieve the objective for End-Point compliance?
The main source of information for OpenNac is the OpenNac Agent, is a software that collects information and perform a complete software inventory of each asset. After collect that information the inventory is sent to OpenNac Core, and this device insert several tags for each feature included into inventory, finally OpenNac can use the tags for applying policies.
Agent Collected Information
- Operating System
- Anti-virus Information
- Firewall Information
- Software installed inventory
- Patches installed
- Network Interfaces Information
- Executing Process
- Current logged user
Each item collected by OpenNac is linked to a single tag, then using the generated tags the administrator can define the minimum requirements for each asset on network, this feature is known as profiling and consists in define specific features for any asset on your network and insurance the compliance, the administrator can create a remediation VLAN and send there the assets which doesn’t fit the minimum requirements.