End Point Compliance¶
This use case allows to check in every assets which OpenNac agent installed different parameters as software installed, anti-virus updates, specific software versions, etc. After identify the value of an specific parameter, the users can create a tag and later use the tag into pre-conditions in policy details.
1. DEFINITION (What is it?)¶
Compliance, this is a use case that look for critical features to be evaluated in corporate and non corporate end-points, the evaluation objective is to determine the minimum requirements to access network based on agent collected information.
2. MECHANISMS (How does it work?)¶
The main source in this use case is the agent collected information, the agent collects a detailed inventory from each asset, you can use that information to create a customize tag and later use the tag in policy pre-conditions
3. MINIMUM REQUERIMENTS (What do we get?)¶
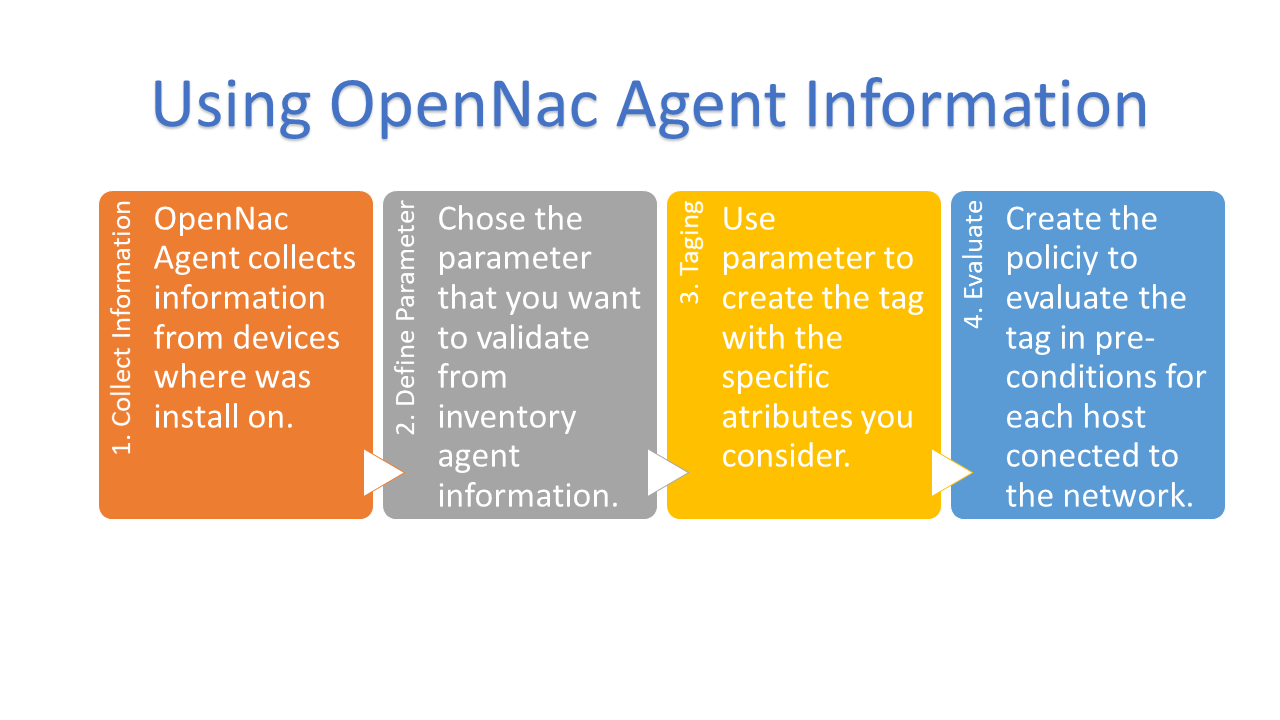
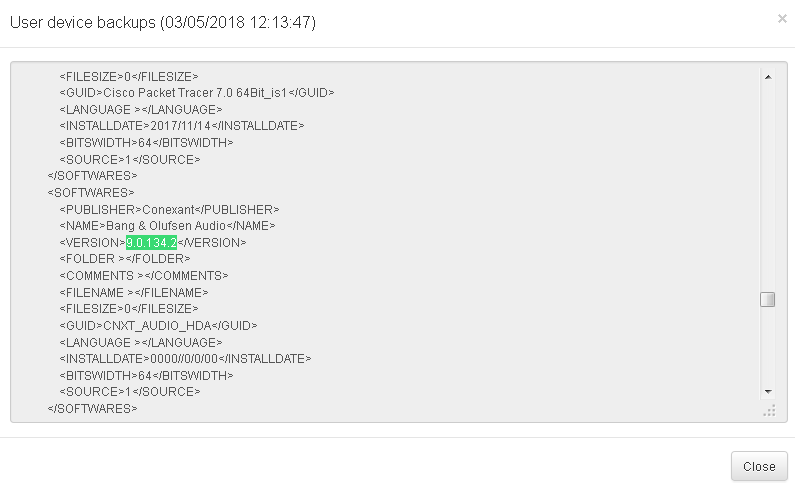
The main objective of End-Point Compliance is to filter the assets which meets the minimum requirements to access network, you can build a policy that evaluated generic parameters as antivirus update version, or you can be as specific as you want based on Agent collected information called inventory. The next image shows the inventory collected by OpenNac agent, for example the user can select an specific value from this inventory as Anti-virus version, and later build a tag using this parameter. As Anti-virus version information, this inform contains a complete software and hardware inventory of each asset on network, then use any data to define a specific tag.
4. DASHBOARD (How do we display what we know?)¶
On OpenNac dashboard ON CMDB –> User Devices. Filter by Tags and use agent string. The list will show the agents installed on network devices and its details.
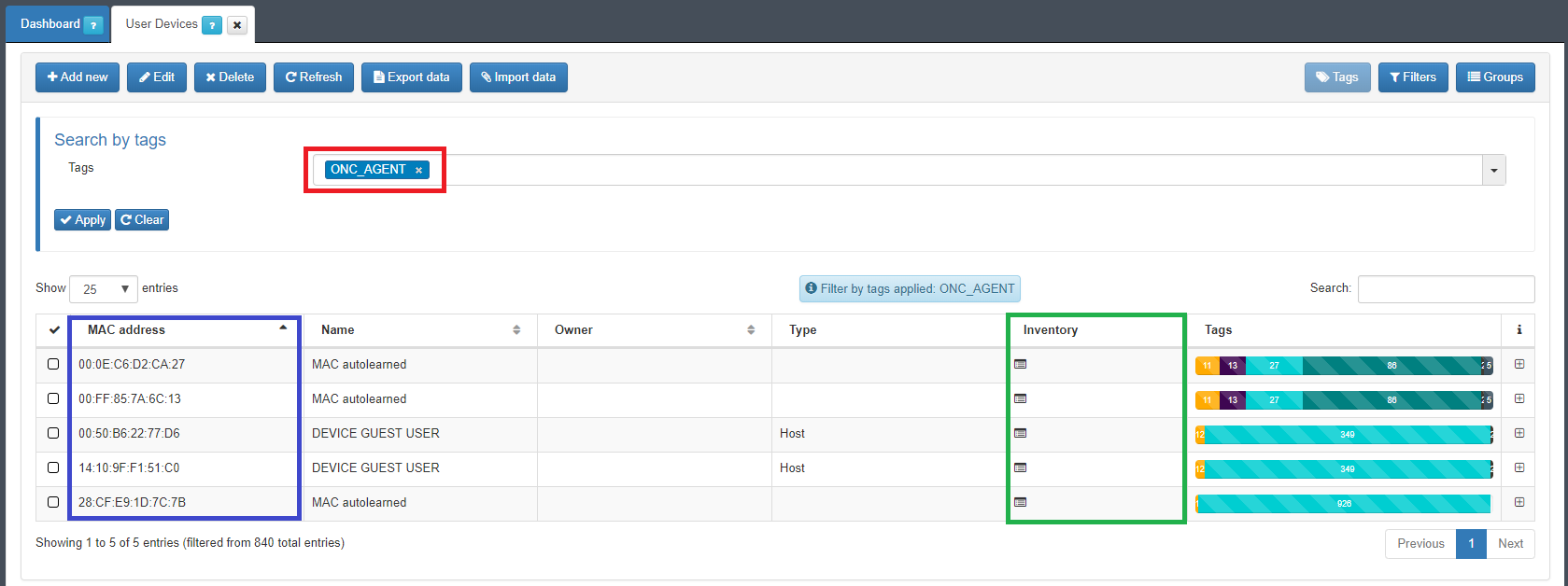
Blue: MAC address which has the OpenNac agent installed.
Green: The inventory of each host, the details for each asset which contains the agent collected information
Red: String used to search the host with OpenNac agent
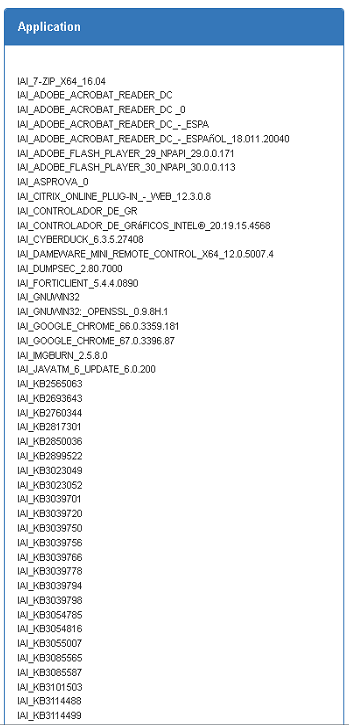
The application list is shown in business profiles, you can review that list and verify the software installed on the devices; later select one of them for future evaluation. Based on this information the administrator can select one software on list and establish it as a minimum requirement.
5. DEPLOYMENT (Do it yourself)¶
Next we are going to deploy single architecture for End-Point Compliance and use a specific parameter collected by agent to define a compliance policy.
5.1 REQUIREMENTS:¶
- OpenNac Core
- Network devices(switch, ap..).
- OpenNac Analytics.
- Client PC + OpenNac Agent.
We are going to use OpenNac Discovery plugin.
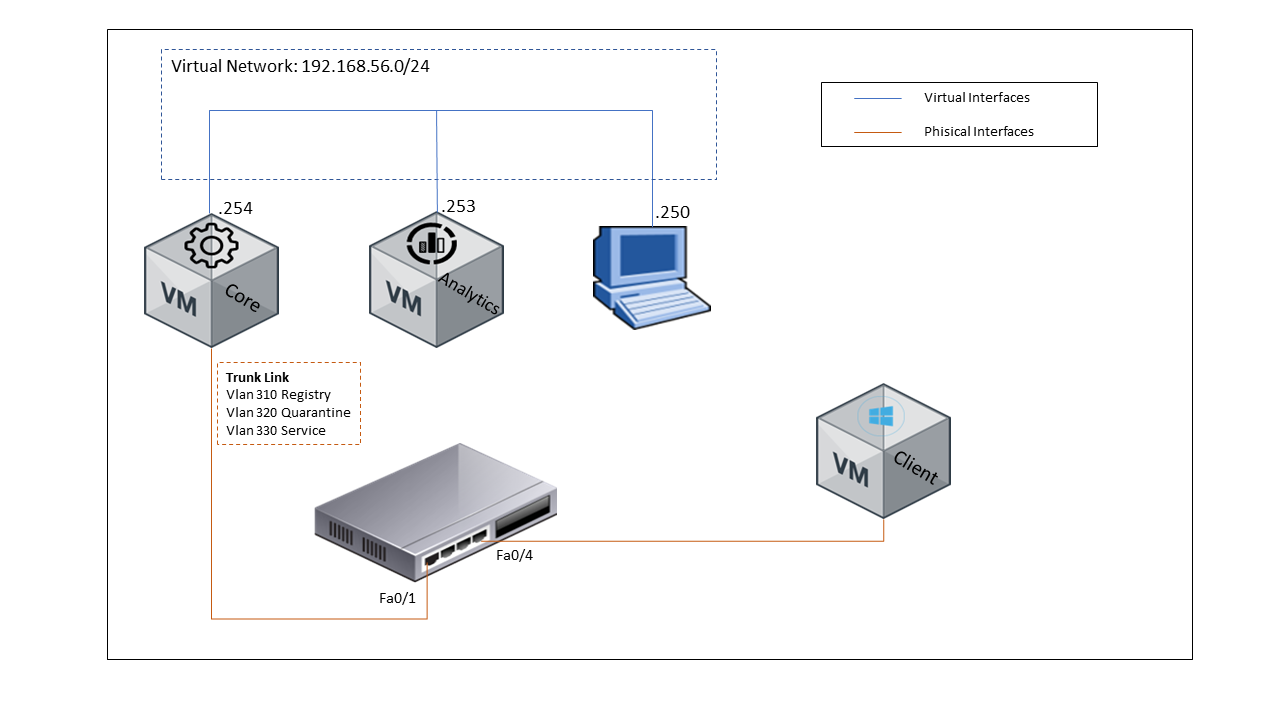
5.2 SCENARIO ARCHITECTURE¶
This is a single deployment for End-Point Compliance, be sure to access the OpenNac portal from client to download the OpenNac agent.
5.3 SETTINGS:¶
Review the basic steps to generate customizing tags based on inventory collected by OpenNac agent and later use the tag into a policy.
On Core
The IP user portal should be configured in . The users will use that IP address to download the OpenNac agent. Be sure to reach this IP from clients in network.
Be sure of select Autoload software tags and Autoload software compliance, these options allows OpenNac to create the tags for software installed. To enable this option go to Configuration –> Configuration Vars Select the tab User Portal.
Configuration –> Configuration Vars Option User Portal IP or name
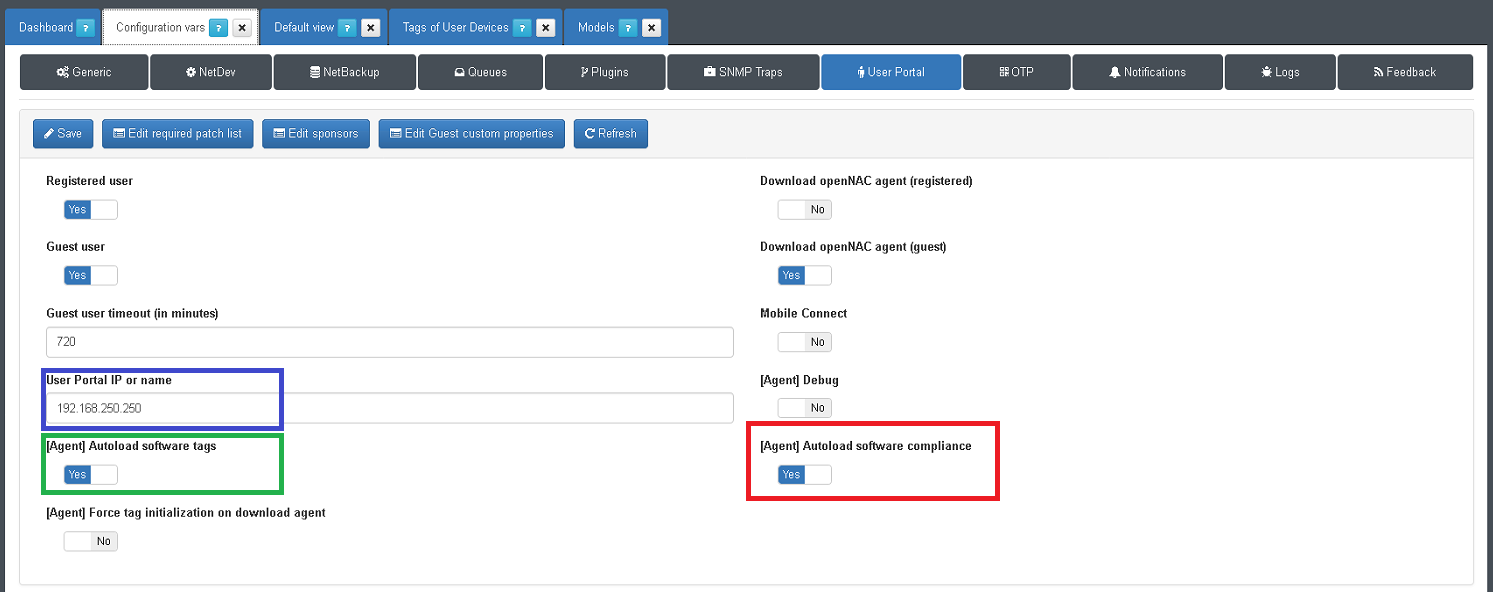
RED Autoload software compliance: Allows to evaluate the compliance software (tags) automatically
BLUE User Portal IP or Name: Allows to define the Portal name or IP address where the agent will report and send the inventory, the agent can be downloaded from this site.
GREEN Autoload software tags: Allows to create the tags for software inventory collected by OpenNac Agent.
- Review the collected information through the OpenNac agent, and choose the parameter for verify.
ON CMDB –> User Devices
Filter by tags, and fill the black with agent string.
There is other way to verify the collected information, and check the automatic insert tags for each asset. ON NAC –> Business Profiles –> Default view Select one item and verify the Application box on Tags section.
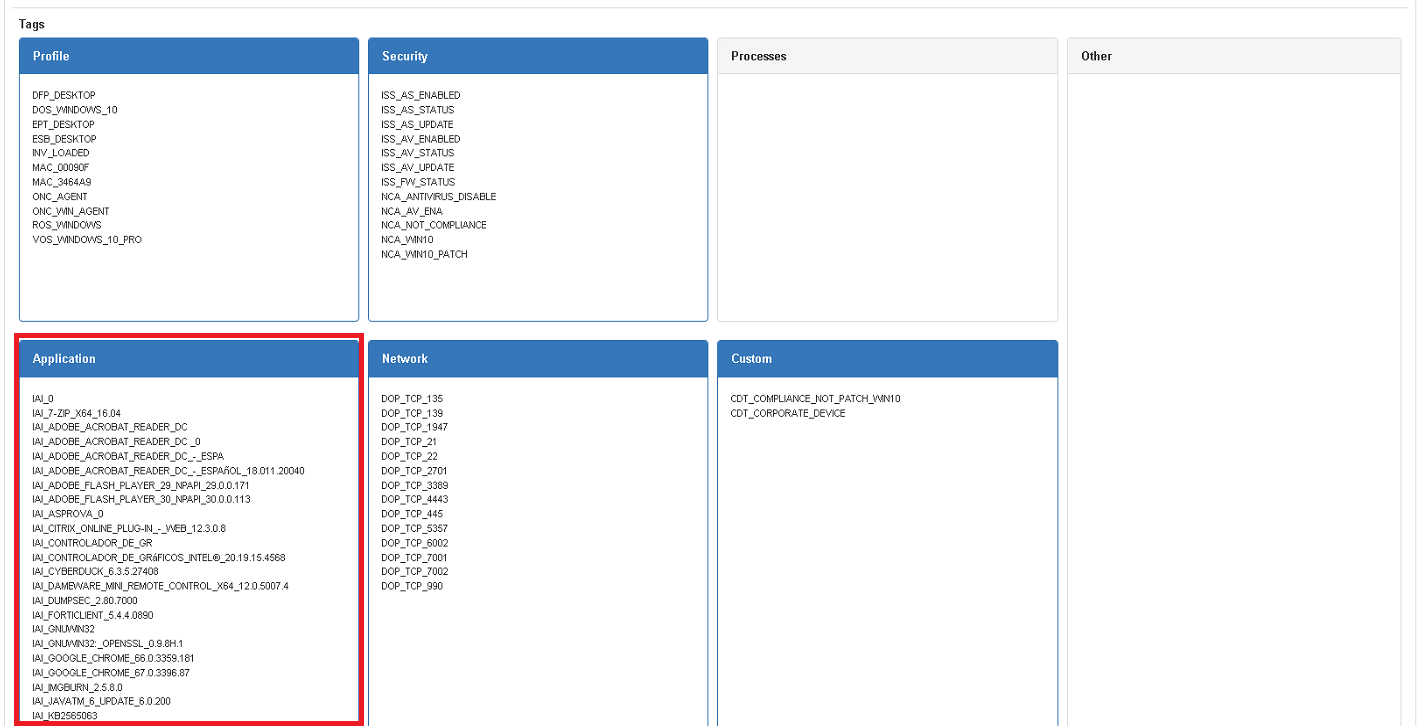
- Use the tag created by OpenNac in Application box of business profiles for each asset, declare a TAR (Target Application Release) tag changing the beginning for TAR as follows.
ON CMDB –> Tags –> Tags of User Devices
- Add New
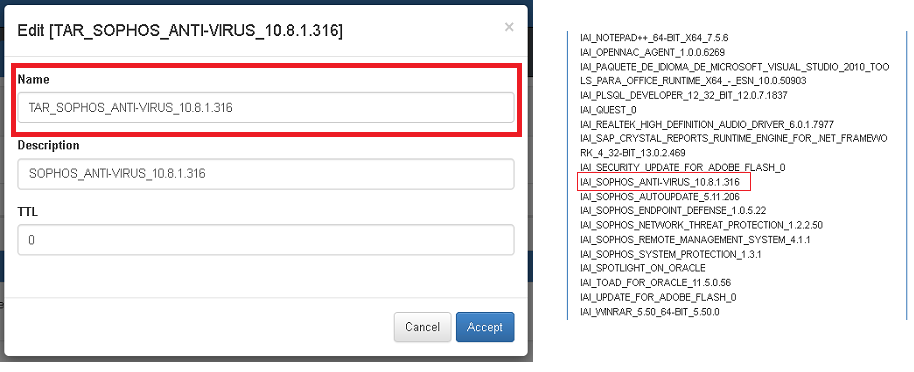
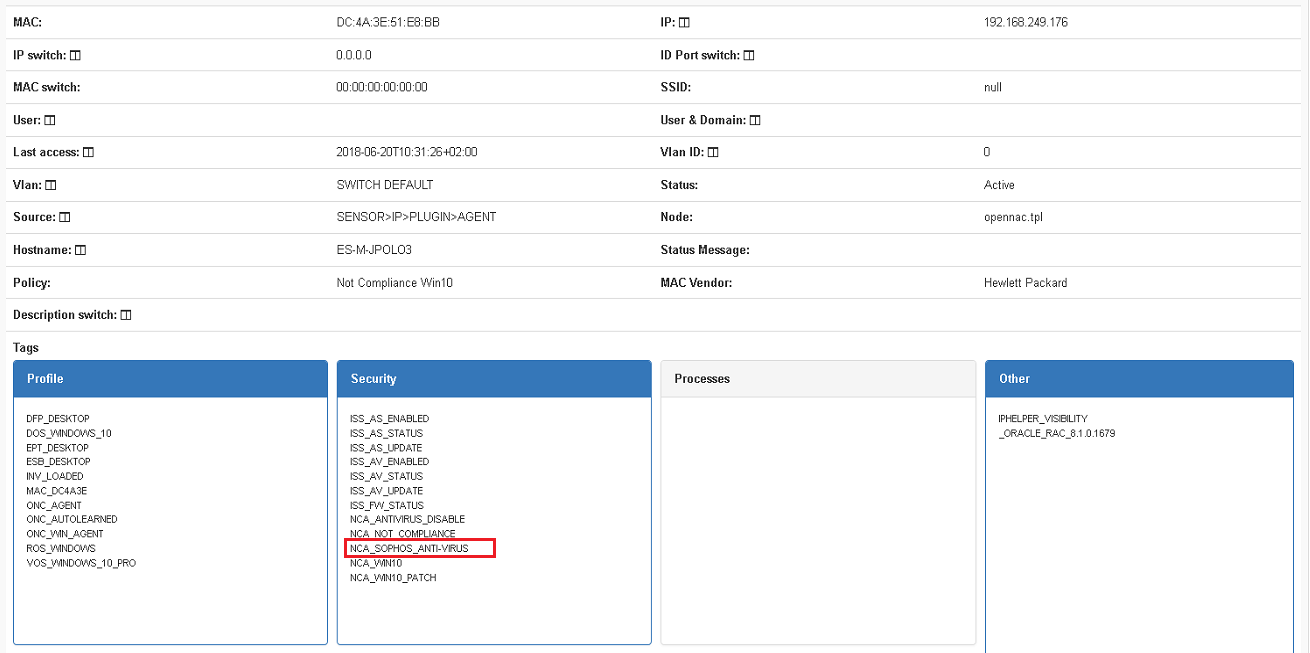
These TAR tags are going to evaluate the minimum software version for one of the software included into software inventory collected by openNAC agent. If the version doesn’t compliance as least with the explicit version a NCA (Not Compliance Application) tag will be inserted over device and you can verify it in security box at:
ON NAC –> Business Profiles –> Default View. Check Security box on asset
- Use NCA tags to create policies to filter the network assets which doesn’t compliance the software requirement.
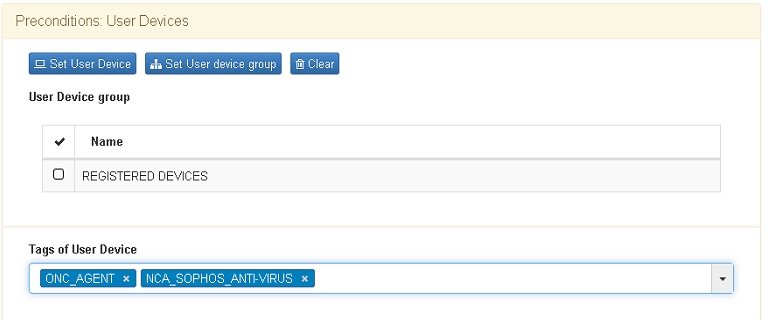
- Additional configuration. In this part of postconditions policy you can add a custom parameter to force the agent data update interval, for this example the value is set in 120 sec.
Red: Add custom parameter AGENT_CONFIG_FULL_INTERVAL
Blue: Set the name and the time (sec)
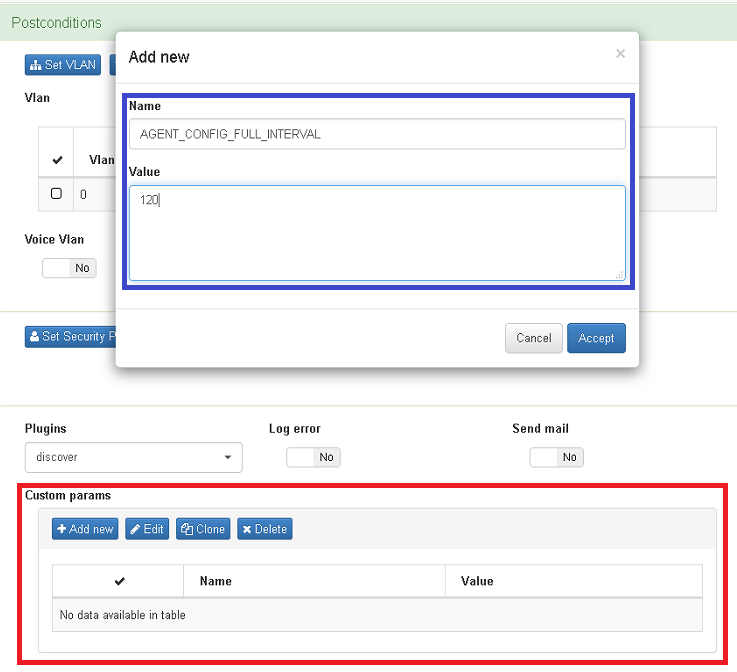
You can verify the section custom params:ref:openNAC Agent Parser<parser>.
For management information review Agent Parser.
On End-Point
Install the openNAC agent on End-Points. The administrator can use your own deployment software tool for massive deployments, or can do it manually. Follow the steps in the next link.
Note
You can use the microsoftupdate.php script to automatically get which new KBs should be defined as compliance baseline for each version of the Windows Operating System. Both scripts are available since openNAC release, Microsoft TAG Policies
5.4 TESTING:¶
Each asset where the OpenNac is installed generate an inventory with different tags. List the agents which are communicating with OpenNac core on CMDB. From web console on left menu ON CMDB –> User Devices. Use the tags for filter by tag, use the tag ONC_AGENT, apply the filter.
MAC Address - Blue: Devices where OpenNac Agent is installed is listed
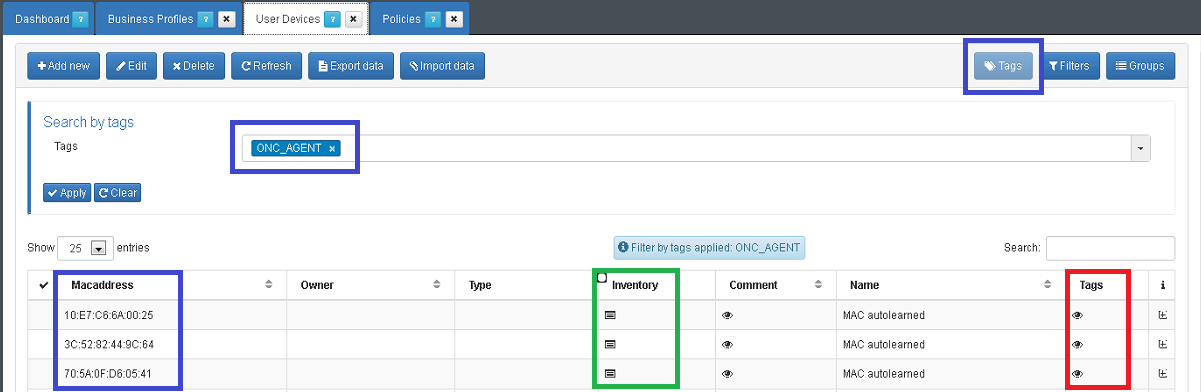
Inventory - Green: Inventory is collected, the administrator can watch the results in this option.
Tags - Red: You can review the tags inserted on each asset using this option
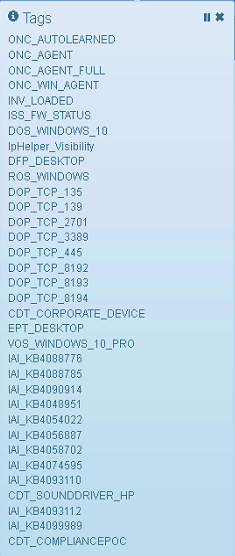
Check the inserted tags on each device with openNAC agent on business profiles section
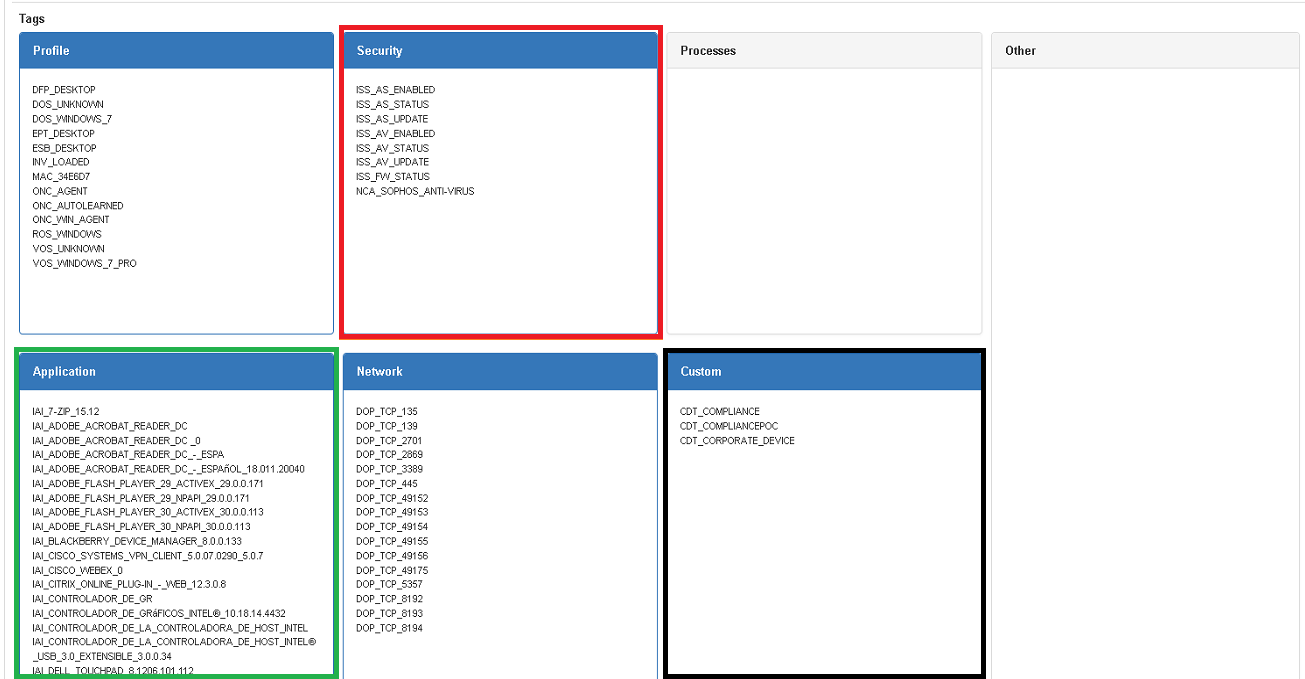
GREEN: Application Tags, the software inventory collected by openNAC agent should be explicit here, with every software version.
RED: Security Tags, the NCA (Not Compliance Application) tags for each assets should be listed here.
BLACK: Custom Tags, If the administrator has created tags and used them in policy rules those created tags should be listed here.
Regular expressions defined in ON NAC –> Tag Policies –> UD Tag Policies will determine the compliance status of each device.
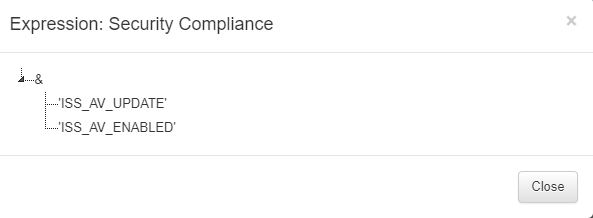
According with rule post-conditions the VLAN will be assigned.
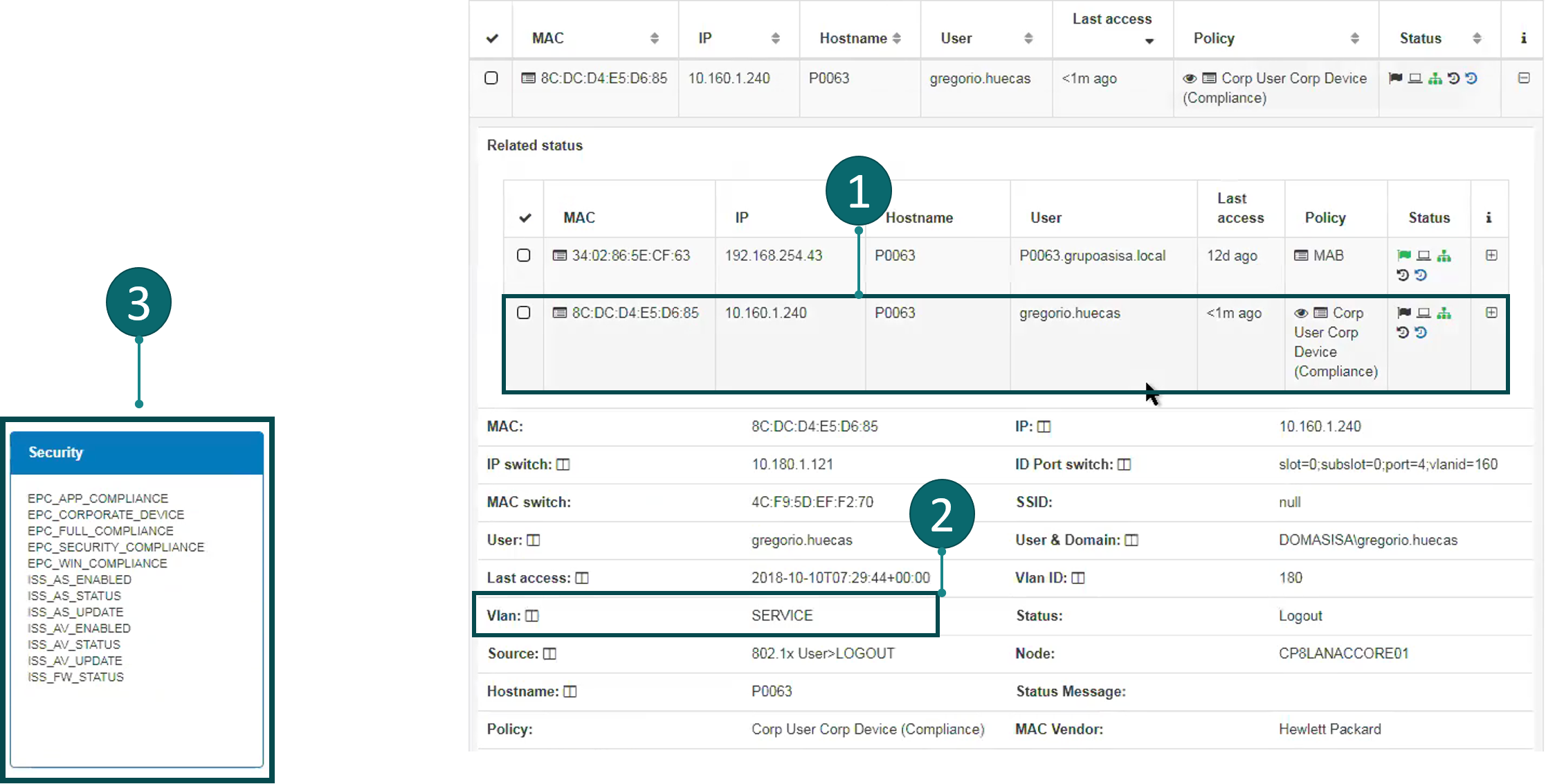
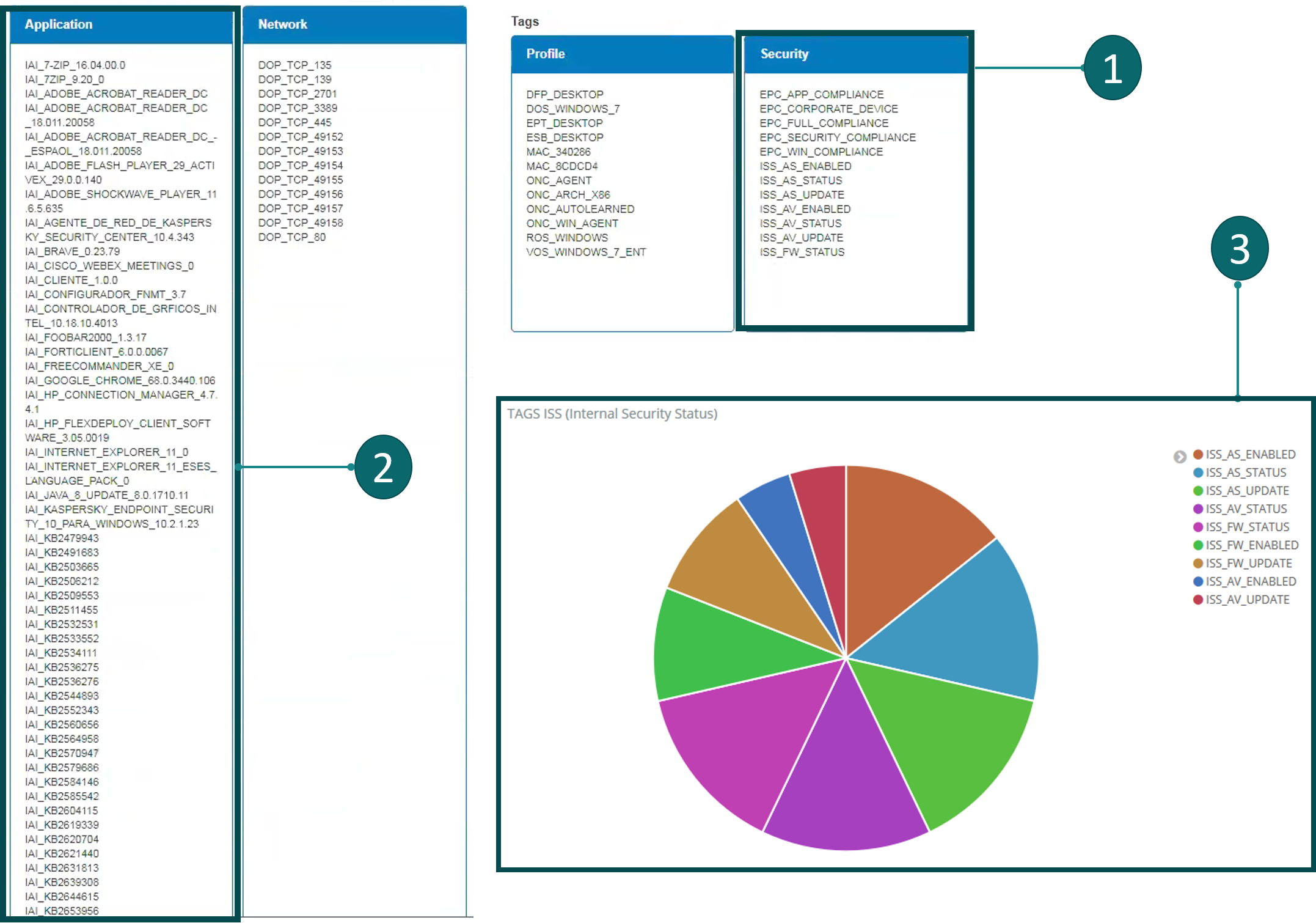
A graphic output can be generated as follows:
5.5 TROUBLESHOOTING:¶
Review the following link to review the basic troubleshooting for openNAC agent. openNAC Agent Troubleshooting.
The administrator can force a policy evaluation using CLI on Core device after performing policy changes to validate the application using: openNAC Forcing Policy Evaluation.