NETWORK SEGMENTATION DEPLOYMENT¶
1. DEFINITION (What is it?)¶
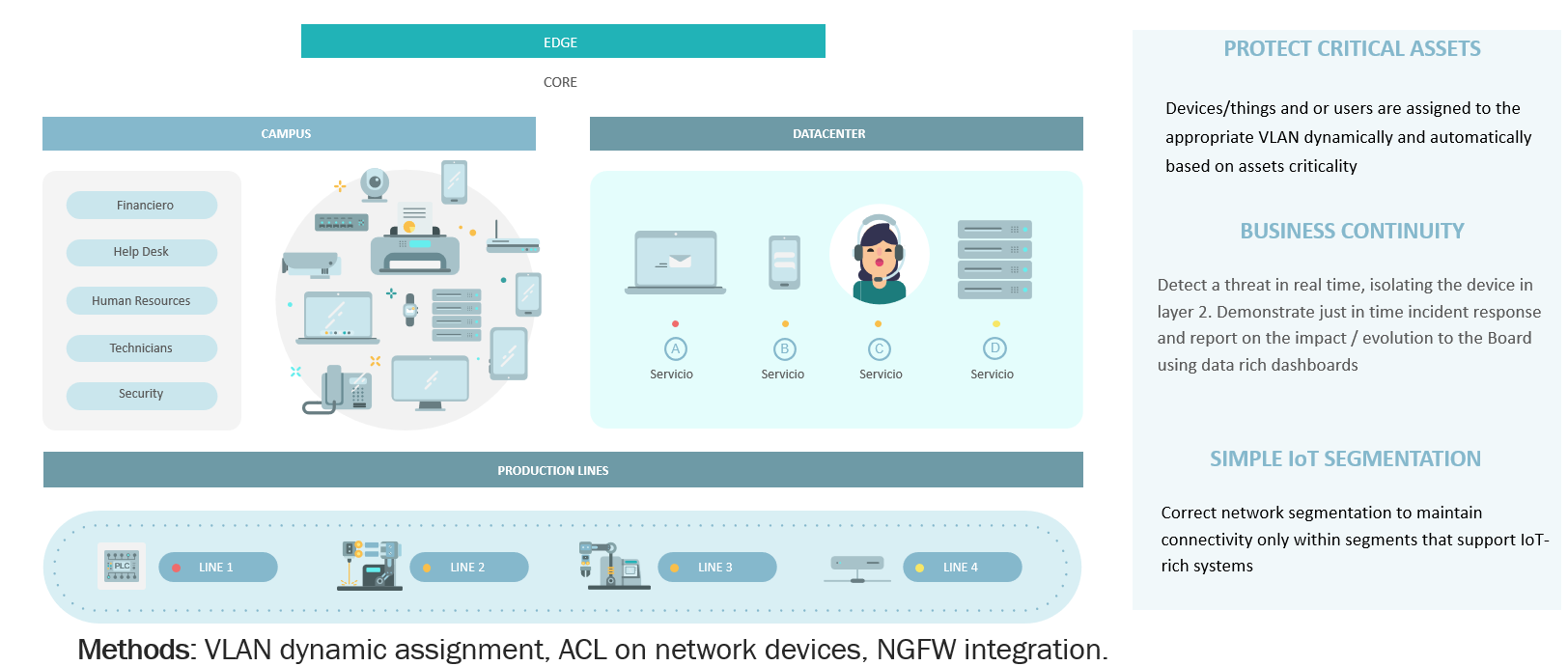
This use case allows you to define specific network segment and assign assets to its according with preconditions defined into openNAC policy, an administrator can use any preconditions described in Policy Preconditions
2. MECHANISMS (How does it work?)¶
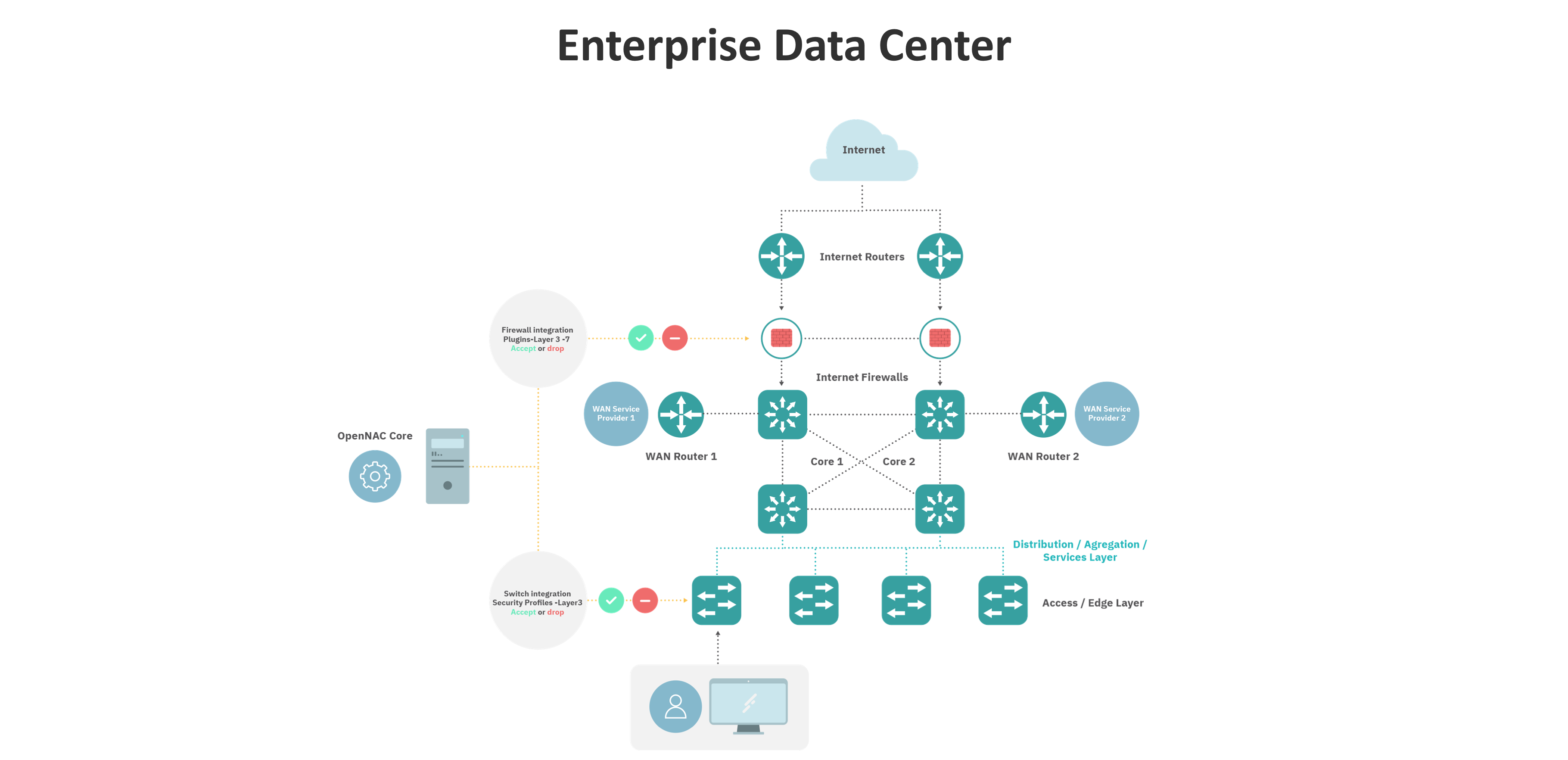
There are three ways for perform network segmentation using openNAC:
Dynamic VLAN assignment
This way is through radius parameters, into these parameters openNAC send VLAN ID information to switch for configure specific port of network device involved in this event.
Using ACL on Network Devices
This way works through Security Profiles, and you can configure using two types of ACL static and dynamic. It depends of network device ACL support, the configuration information goes by radius parameters in both cases Static and Dynamic.
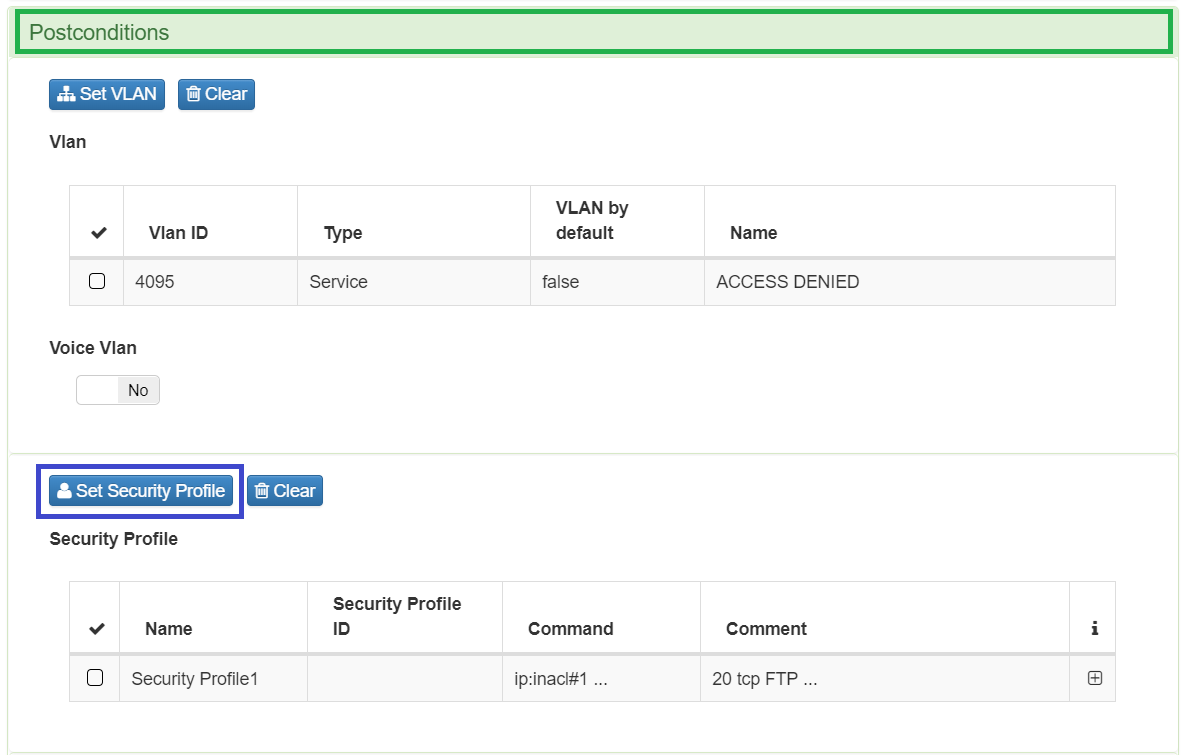
Using Static ACL’s, administrators needs to create the ACL(s) before use it in openNAC and call them by name through openNAC policy on Security Profile section, after validate policy preconditions the Security profiles acts as policy postconditions, assigned an ACL to the specific port of network device involved in this event.
Using Dynamic ACL’s, administrators needs to define the ACL sentences into business profiles, this sentences will be send by radius parameters. After validate policy preconditions the Security profiles acts as policy postconditions, setting the ACL sentences to the specific port of network device involved in this event.
For more information review, Security Profiles.
NGFW Integration
openNAC can be integrated with NGFW and modify access rules defined on that devices according with openNAC policies. Also openNAC can use NGFW information to perform settings over other network devices as an network orchestrator.
Note
Some settings performed by openNAC on network devices through segmentation use radius parameters, so be sure to perform the correct radius configuration before using. Sometimes additional radius parameters are needed, for this case use the extra radius params section on policy postconditions.
For more information about this scenario, please review the integration with Palo Alto NGFW using Palo Alto Plugin
3. DASHBOARD (How do we display what we know?)¶
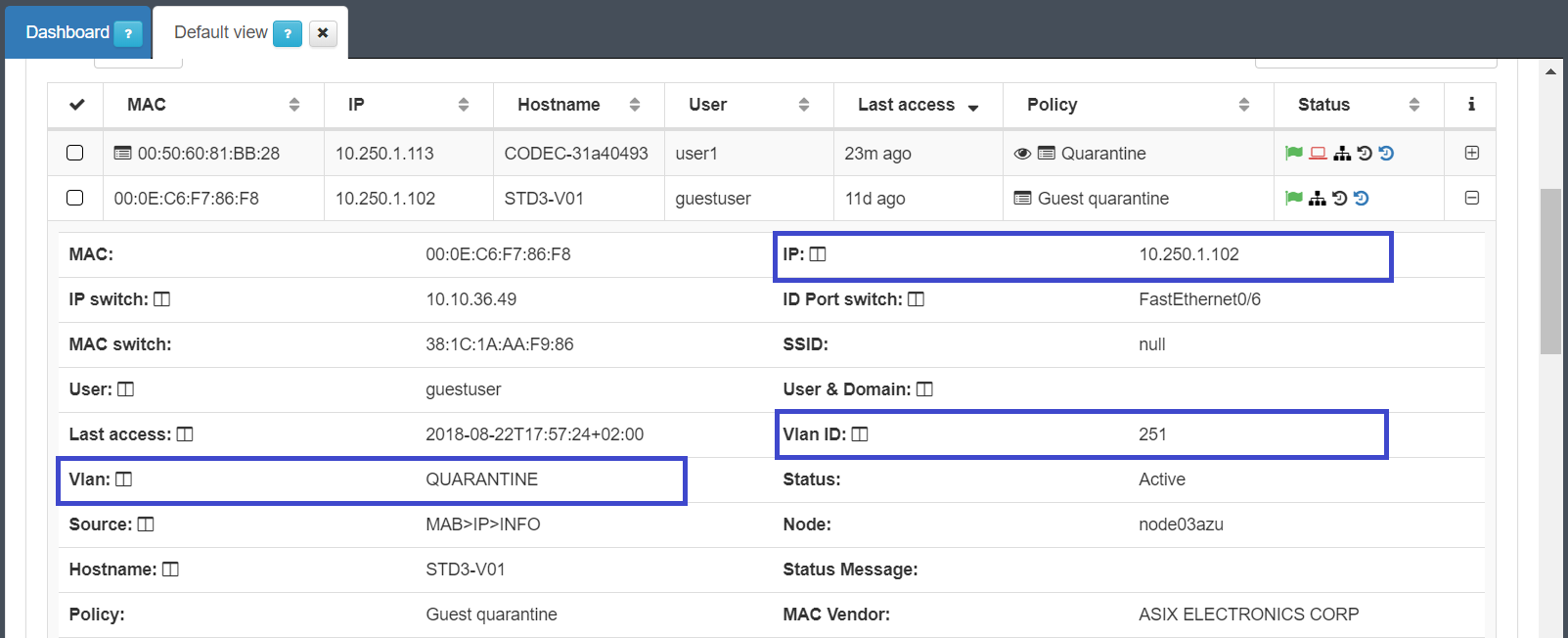
Administrators can verify the assigned VLAN into host information on business profiles, in the next image you can see the VLAN ID the IP address assigned for this network segment.
4. DEPLOYMENT (Do it yourself)¶
The following is a light guide to deploy Segmentation using on radius parameters based on basic lab.
- It is recommended that you follow and read the overview about openNAC solution.
- To deploy an openNAC technology you must understand and follow network requirements.
- As soon as you have deployed the openNAC you must select the correct use case that suits your requirements.
4.1 REQUIREMENTS:¶
- openNAC Core deployed on the network.
- Network devices(switch, ap..) with 802.1x and ACL’s support.
- openNAC Analytics.
- Client PC, in the following scenario we will use Windows but any asset with 802.1x can be used.
Depends the mechanisms used you will use one or another configuration. The following is a light guide to deploy visibility 802.1x mode based on basic lab.
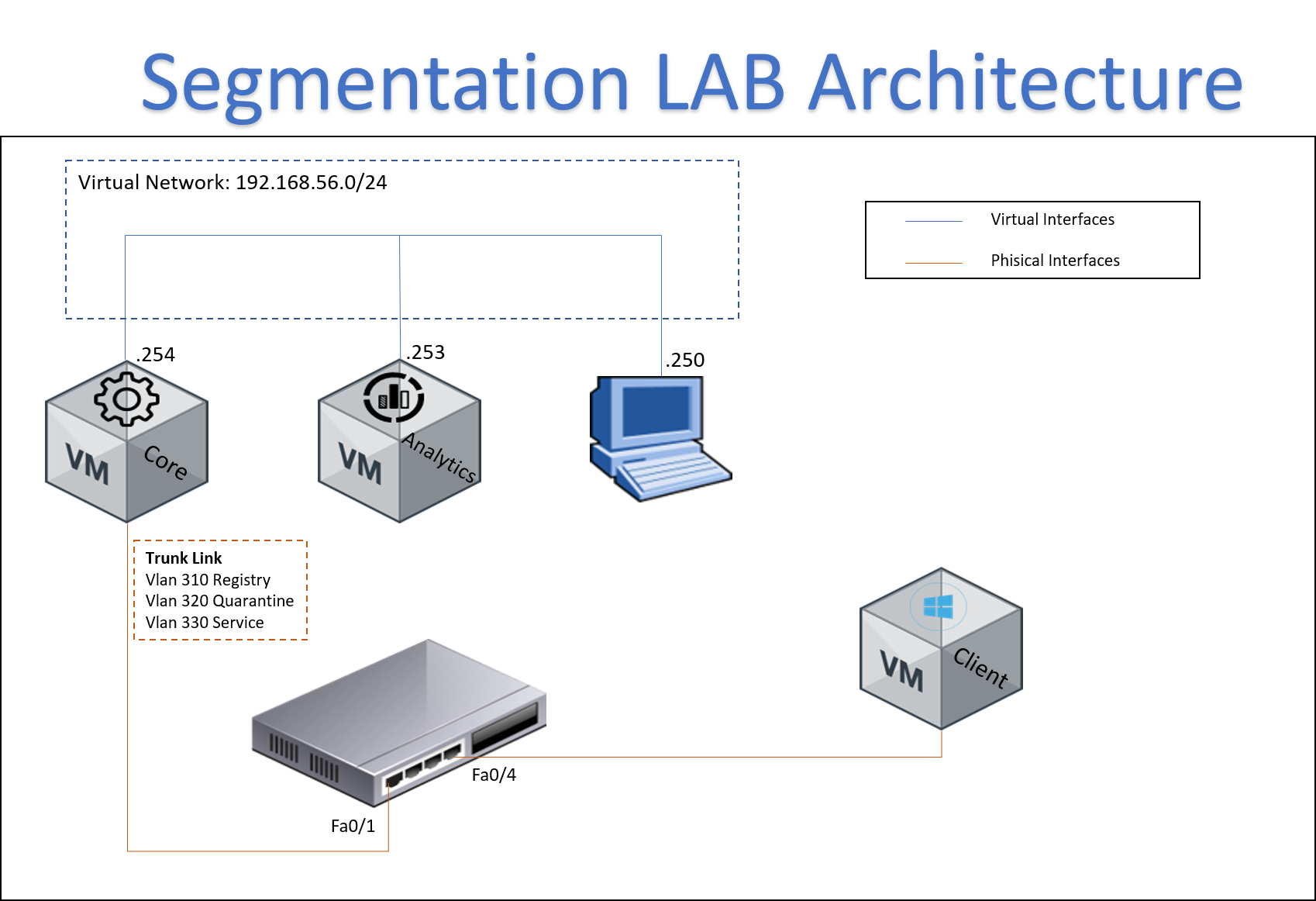
4.2 SCENARIO ARCHITECTURE¶
We are going to deploy segmentation use case using Dynamic VLAN assignment and ACL’s mechanism. So need a network device that supports 802.1x and ACL.
4.3 SETTINGS:¶
4.3.1 Dynamic VLAN Asssignment¶
On Switch
The following link contains the required configuration on switch for visibility use case.
Basic 802.1x Cisco Switch Configuration
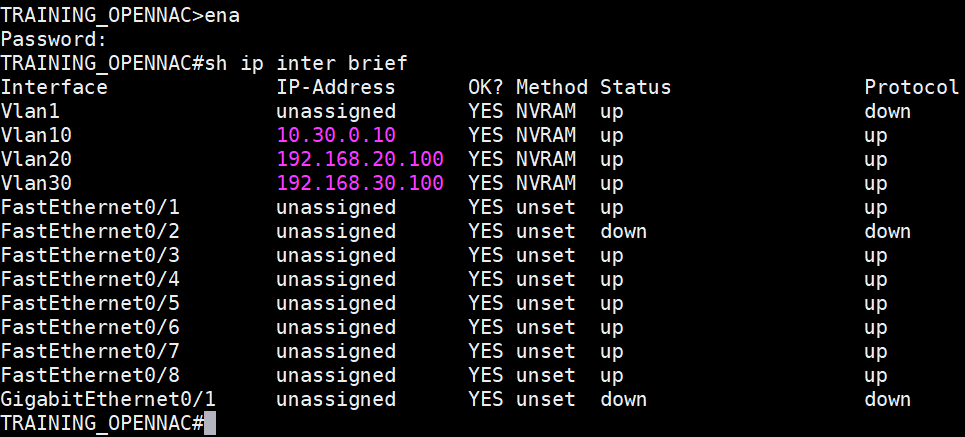
Additional create the necessary VLAN’s on switch device for this example
On Core
The first step is define if your are going to use a local or external database, for testing propose we recommend use local database.
Using Local Database
Create the two users into openNAC local database using web console. Go to ON CMDB –> Security –> Users. Select Add New option. The first user will be a valid user.
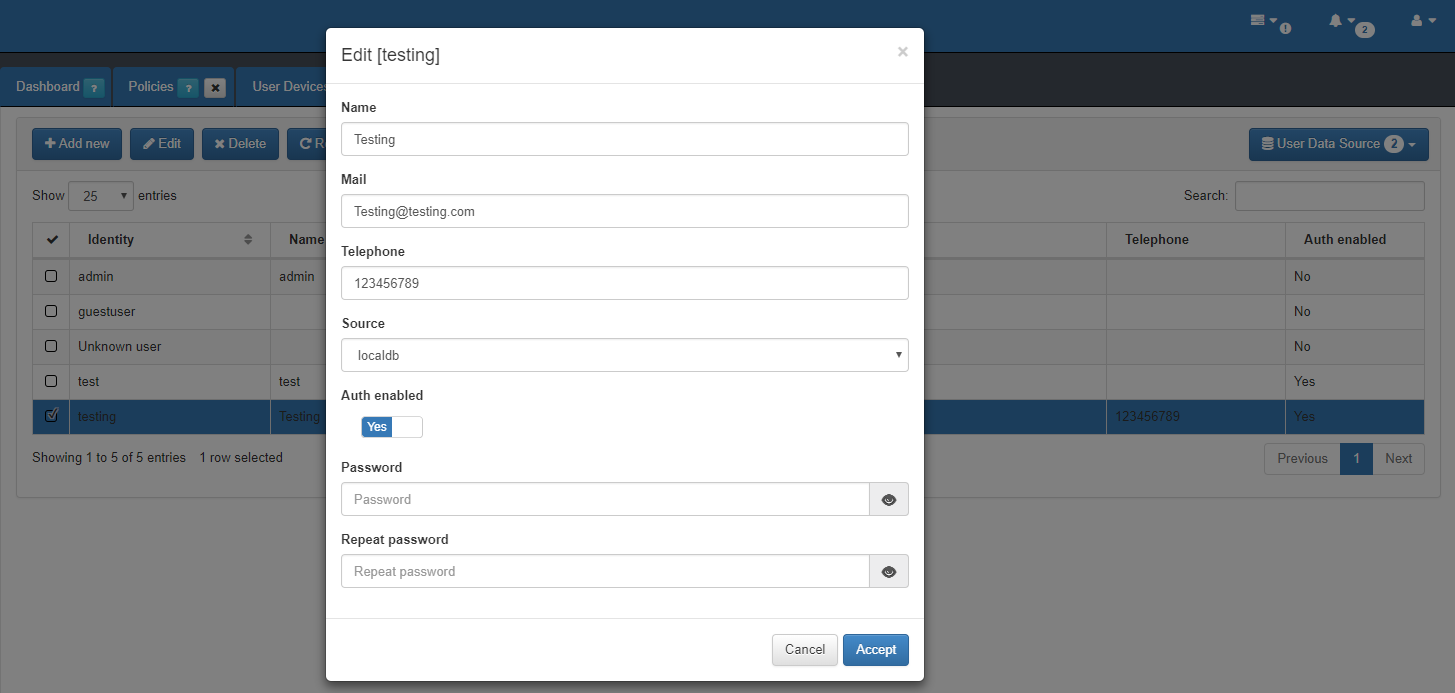
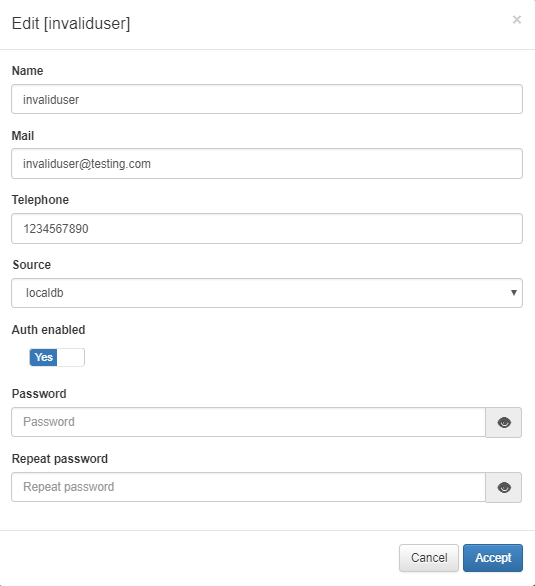
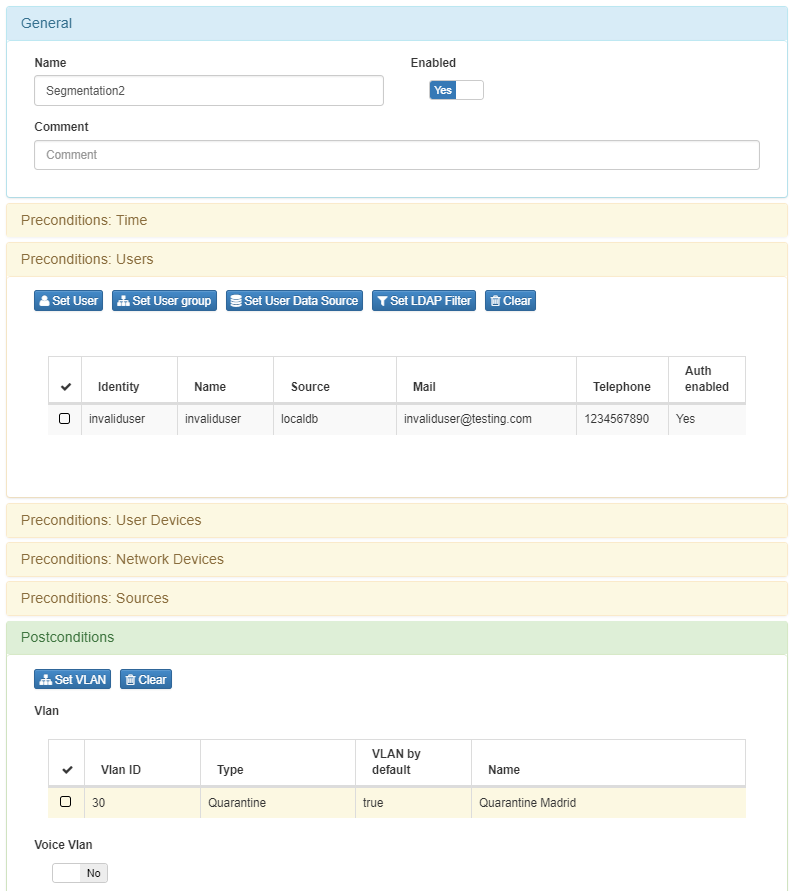
The second user will be an invalid user, and the VLAN segmentation will be based on specific user as precondition.
Note
Both user’s credentials will be used later to test.
Policy Configuration
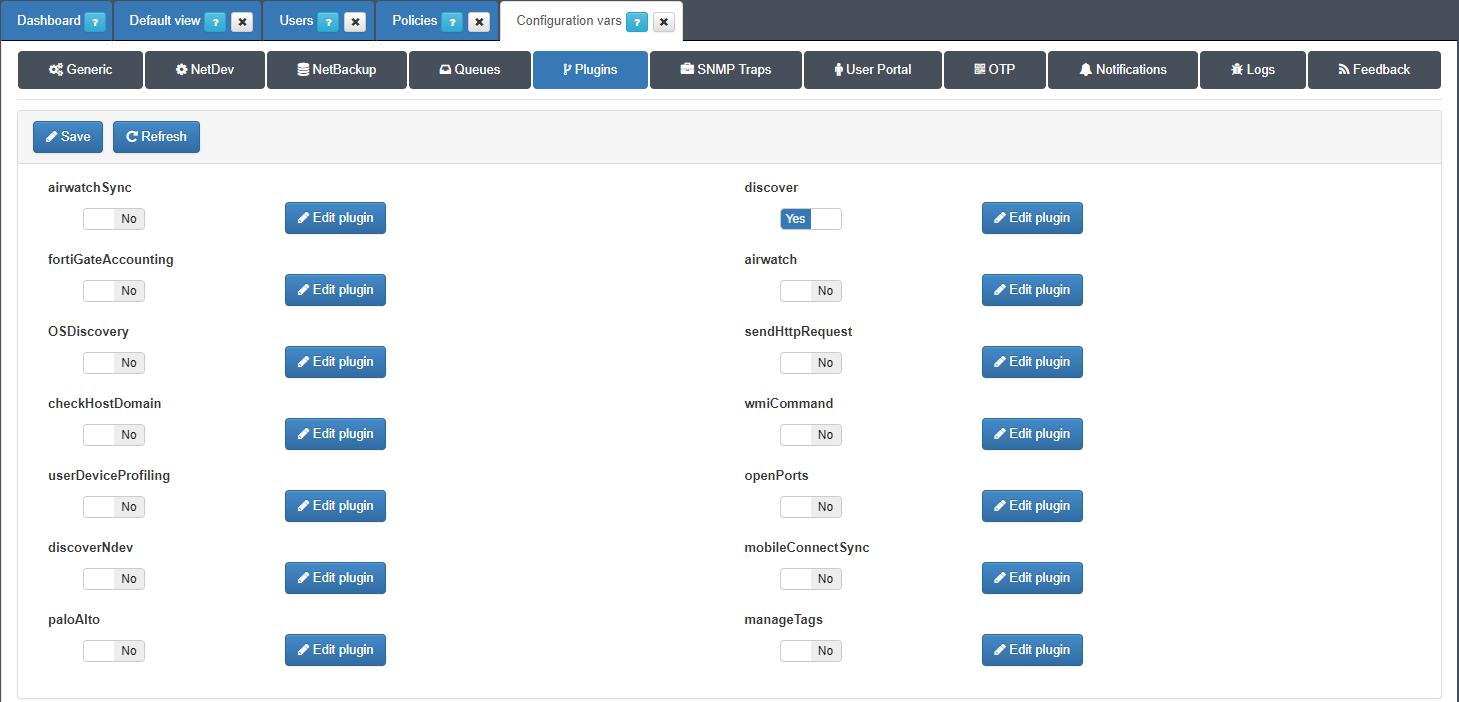
Before configure the policy rule enable Discover plugin, for visibility propose but it’s not mandatory for this use case, openNAC use a plugin knows as Discover, this plugin runs a “scan” over each endpoint which can reach through IP address. So the first step is enable the plugin.
Go to Configuration –> Configuration vars, select plugin tab and enable Discover plugin.
Policy for Local Database
Go to ON NAC –> Policies, click the option Add New. Named the policy in General Tab, Set the localdb as users database in Preconditions: User Tab.
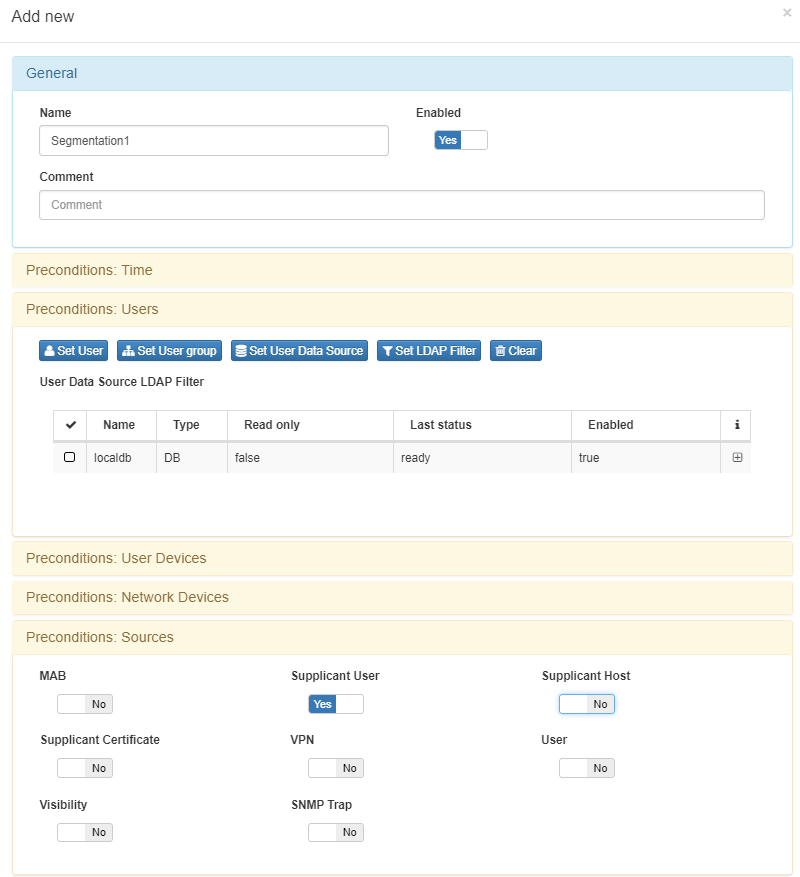
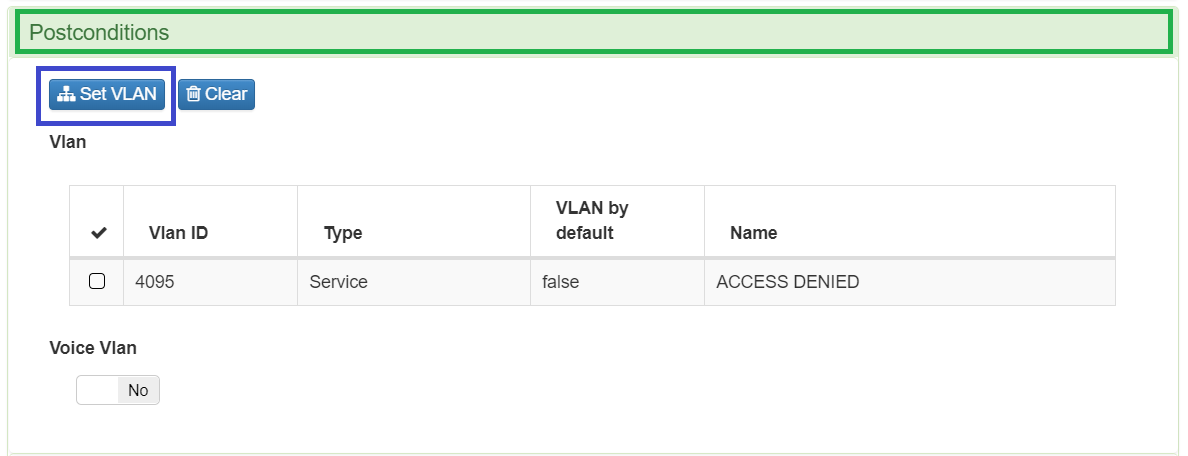
Into postconditions section select the service VLAN to assign it to authenticated users successfully, in this case Service VLAN (10)
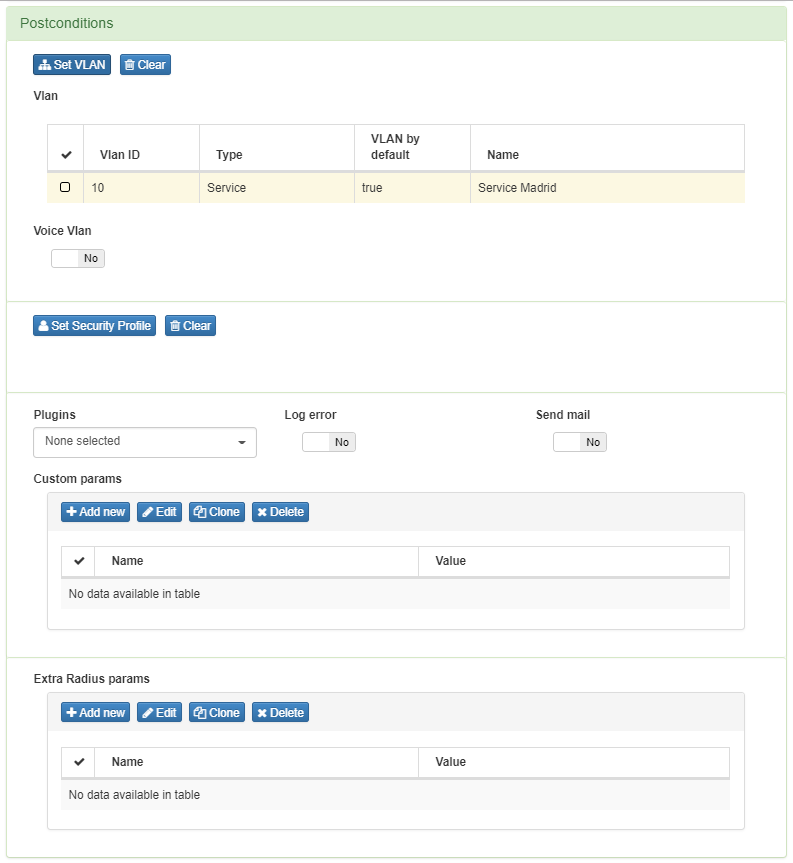
Add another policy rule but evaluating a specific user (invalid user), and assign to a different VLAN, for this propose use Set user option into Preconditions: Users Tab.
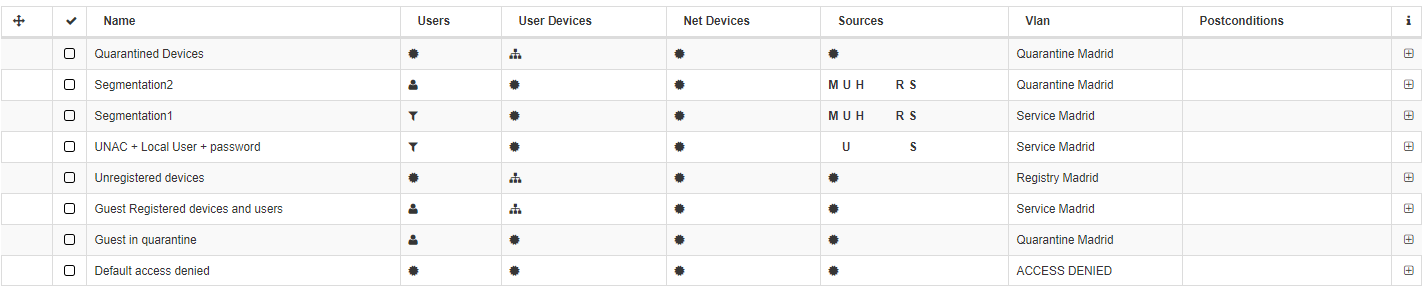
As one user is more specific than all the user database, put in order the policy rules to evaluate the preconditions from most specific to general ones. In this case you should put first Segmentation 2 before Segmentation 1.
Note
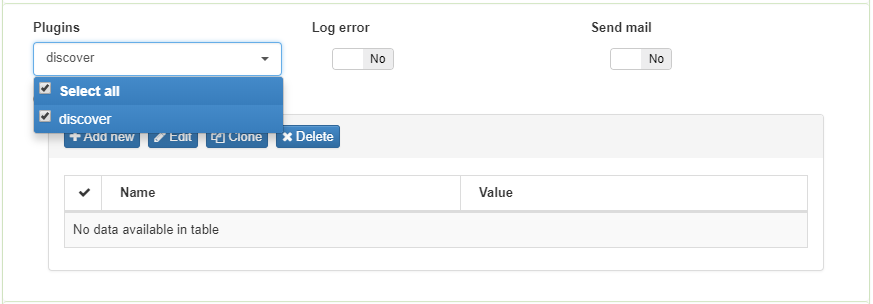
As optional postcondition, enable plugin Discover to improve visibility in each policy.
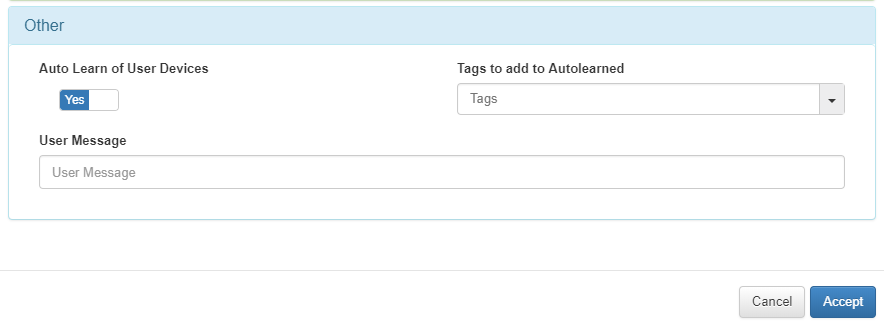
If this is the last policy or the only one you can check the option Auto Learn of User Device to add the devices to openNAC core database.
On EndPoint
Into Client VM.
You can verify the 802.1x EndPoint configuration for different devices in 801.X Clients Configuration
For testing go to Dynamic VLan Assignment Testing
4.3.2 Using ACL on Network Devices¶
For testing go to ACL VLAN Assignment Testing
4.3.3 NGFW Integration¶
The basic LAB doesn’t include a NGFW, so this scenario can’t be tested. But for more information about the NGFW integration, please review the integration with Palo Alto using NGFW Palo Alto Plugin
4.4 TESTING:¶
4.4.1 Dynamic VLAN Assignment Testing¶
Turn on the client VM, use the 802.1x configured interface on switch to connect the host. An authentication will be required.
At first time use the user testing. According with the VLAN ip address configuration, and the policy configuration for the host will be assigned to this network segment.
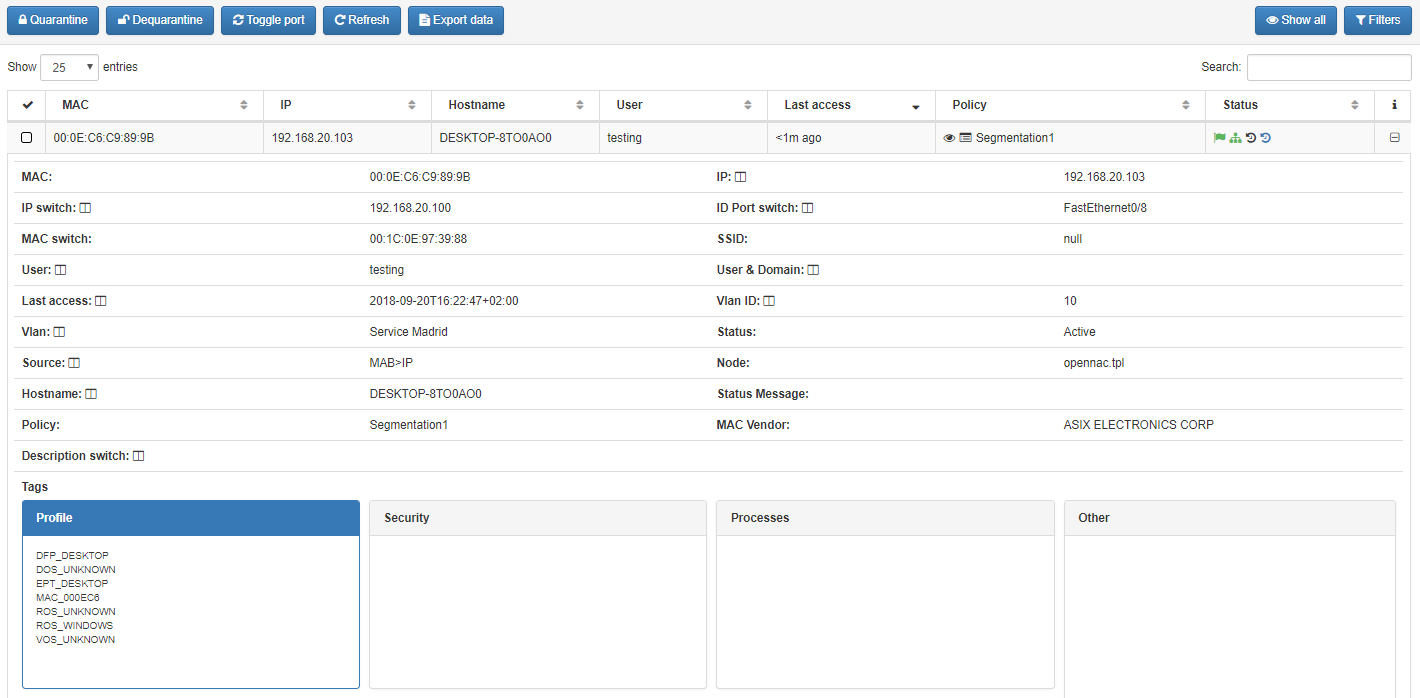
As you can see the assigned ip address in include on network segment assigned to VLAN 10.
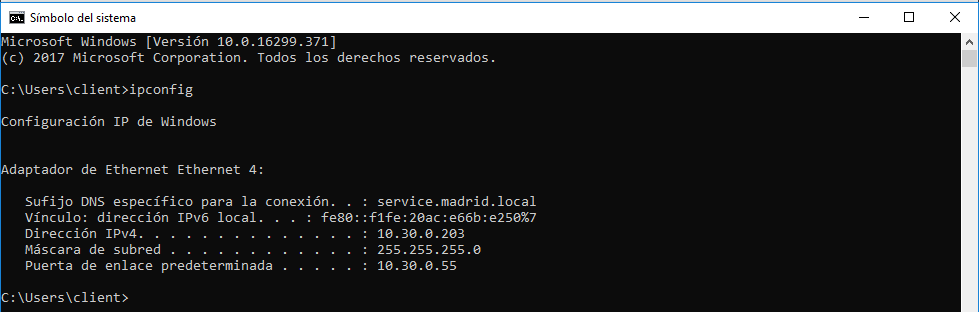
Then, disconnect the interface and connect again, but this time use the invalid user.
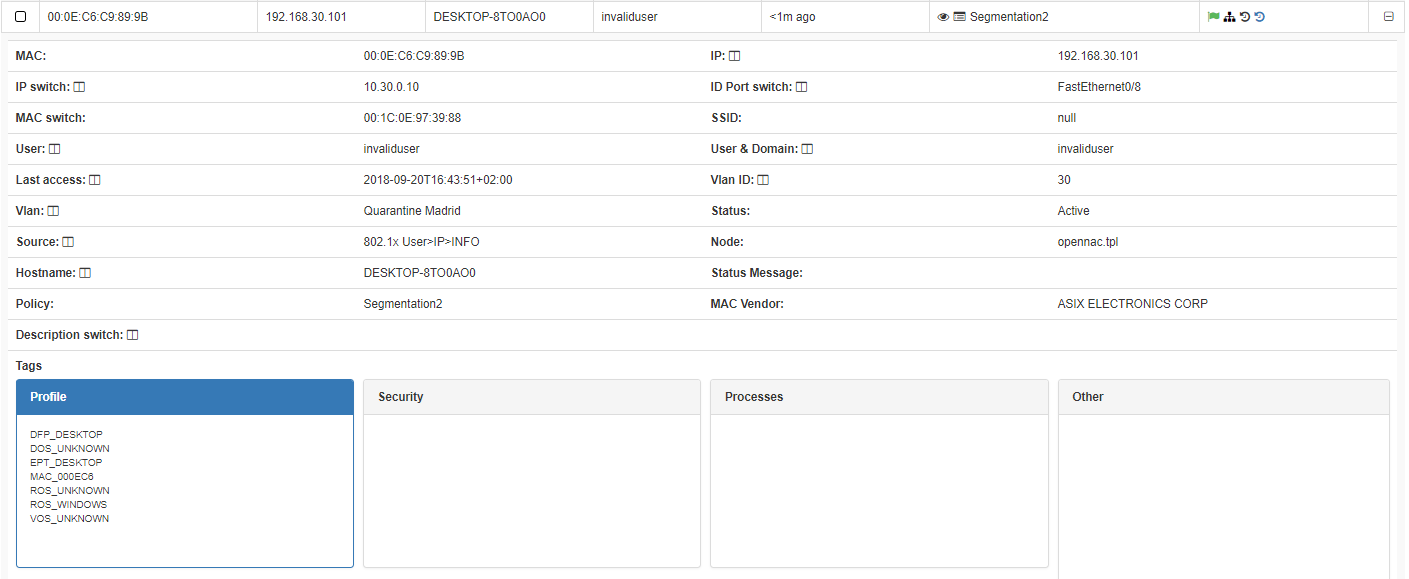
As you can see this time the assigned VLAN is 30, the IP address assigned to host belongs to this network segment.
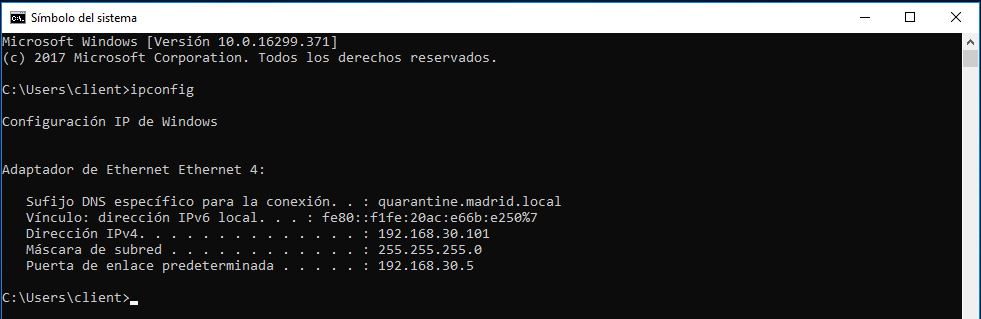
4.4.2 ACL VLAN Assignment Testing¶
4.5 TROUBLESHOOTING:¶
- Please perform a basic review Basic Check
- To perform a debug of authentication process you can verify the link Radius Troubleshooting