Policies¶
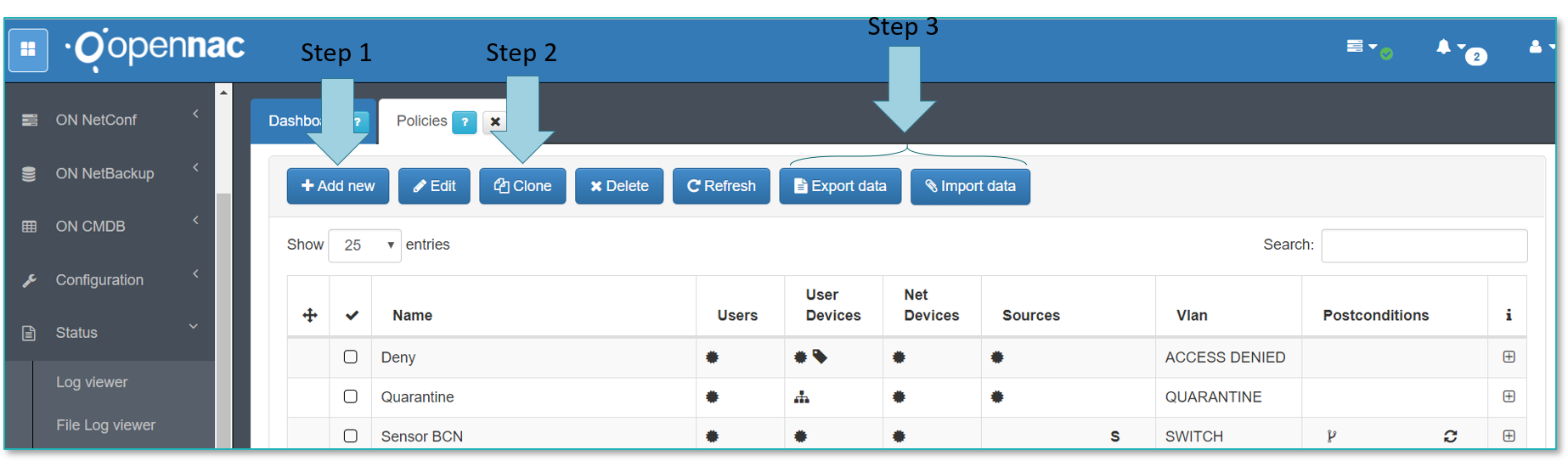
In order to apply/create , remove or edit a Network Access control Policies go to ON NAC -> Policies as shown by the step 1 and 2, from this component is possible to manage network access control policies and its objects.
Before creating any policy we have to mention that at the policy engine there are two implicit policies, these policies will match if no one policy has matched before:
1: First one, this define that all the traffic is sent to register VLAN.
2: Second one, this is the an implicit rule that is created when a end user devices is sent to quarantine, this is automatic but remember that manually can be done as well as shown by the step 3.
Security Behaviour:
Any network access request will be processed by the security policy from top to down way, and as soon as a policy is matched the access is granted or denied.
Important:
Is strongly recommended to apply a policy to match all the authentication in order to know which events are out of the current policy, these events can be used for further investigations.
openNAC includes a policy engine that allows to manage and operate the security policy in a very intuitive way.
Add new or edit openNAC rule is possible as shown by Step 1, to simplify rules operation is possible to clone from existing rule as shown by Step 2.
Export and import capabilities are also available for the users as shown by Step 3.
After create new policy, we have to understand the main sections that are included in a policy evaluation process.
The section 1 named general* allows to add a policy name and a policy comment, also allow us to enable or disable the policy, something are created rules for monitoring proposes and can be enabled and disable on demand.
The section 2 named Preconditions allows to add conditions before the authentication happens, Time of the connection, Users, User and Network devices evolved, and type of authentication (Sources), right after we will detail all the options available.
The section 3 named Postconditions allows to add conditions after that authentication happens, Vlan assignment, Security Profiles or ACLS at ingress port, plugins and its parameters, notifications
The section 4 named Other allows to defined a message for network access request, learn user devices automatically and define that those a TAG.
As any security policy engine the logic used by openNAC technologies is explained in this picture, we have two main principles that have to take into account to avoid mistakes and undesirables behaviors.
Principle 1: Vertical components act as a logic “AND” during policy evaluation.
Principle 2: “Preconditions: Sources” will act as a logic “OR” because each event only have one source. This lets the user create an unique policy for more than one source event. “Precondition: Users”, “Precondition: User devices” and “Precondition: Network devices” only lets to set one of the possible options. For instance, if we try to add an user and after an user group in “Precondition: Users” in the same policy, user group will overwrite the user condition.
General¶
This section included in the policy creation allow us to define a policy name as shown by the step 1.
Policy comments can be added, this comment is related with the policy itself, as much detail as possible will improve future policy reviews as shown by the step 2 , sometimes is included additional information such as a change number, date of policy creation, technical reasons for deny or allow the access or many others…
Policy can be enabled and disabled as shown by the step 3.
Preconditions¶
Time¶
One of policy component that can be used by the policy engine is the Time component, this allows to select what hours the policy is enabled and then what hours the network access is allowed and active for the end users. A hour time range can be selected as shown by the step 1.
Users¶
One of component that can be used by the policy engine is the Users component , this component allow us to select users identities to allow or deny network access to the end users. In this picture the users are listed are local.
At the step 1 we can select a single user from user local database, however this is just used for test.
At the step 2 we can select a group of users, in this case are local groups only, is very easy to create local users groups and use it.
Local users are stored in a internal CMDB along with all the NAC Assets, openNAC CMDB is located at openNAC Core.
At the precondition section Users, we are able to use User Datasources or UDS, UDS are the identity repository that can be used by the policy engine. Many UDS can be configured (Active Directory, LDAP Server, Database or many others), also is possible to search over then.
To include a User data source follow the step 1.
in order to select the type of UDS follow the step 2.
and to search any user, follow the step 3 and type the name you are searching for.
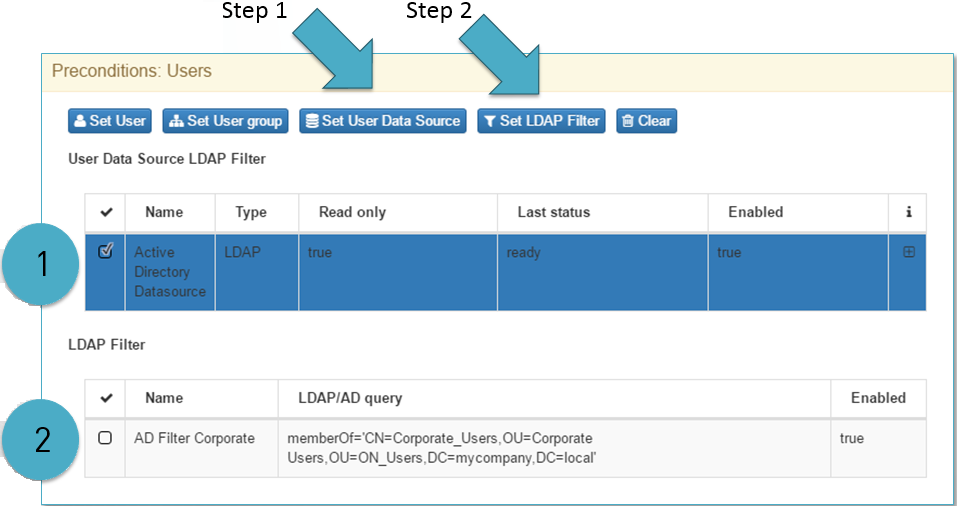
One of the option available for the User preconditions are the User Data source and the LDAP Filters.
User Data source allow us to choose where we want to get users identities, by default we have a local repository but with UDS can be used remotes repositories, in this case Active Directory is chosen.
In order to choose Active Directory follows the Step 1.
Once we have the authentication selected (UDS), select the conditions that must be met to be allowed, in other words the LDAP Filters is the authorization process during policy evaluation.
In order to have a full integration with Active Directory the first step will be add the openNAC Core into the domain, there is a wizard available for that, going to Configuration -> Wizards -> Join domain wizard, with that integration we allow the radius server to use AD as authenticator server, only authentication. For this step review Join Domain.
Set user data source allows to select the binding connection with the Active Directory, and LDAP Filter allow us to choose which LDAP attributes are used for authorization processes, in the example is used “MemberOF” ldap filter.
Its call LDAP filter because we use common LDAP Filters that are compatible with LDAPsearch and its filters, at the point 2 the LDAP filter used is “MemberOF”, this means that if the user that tries to access to the network must be part of the Active Directory Group called ON_Users that belongs to organization unit called Corporate Users and this OU has inside a Security Group called Corporate_Users. In short, if the user have a valid credential and belong to the proper Active Directory group the policy evaluation follows normally. Any LDAP Filter used by Ldapsearch tool can be used, for instance memberOf or that the user has an Active Directory attributes or as simple as the user belongs to the Active Directory.
In case we select only a User data source (Active Directory for instance) and any LDAP filter is used, all AD users will be allowed to authenticate.
User Devices¶
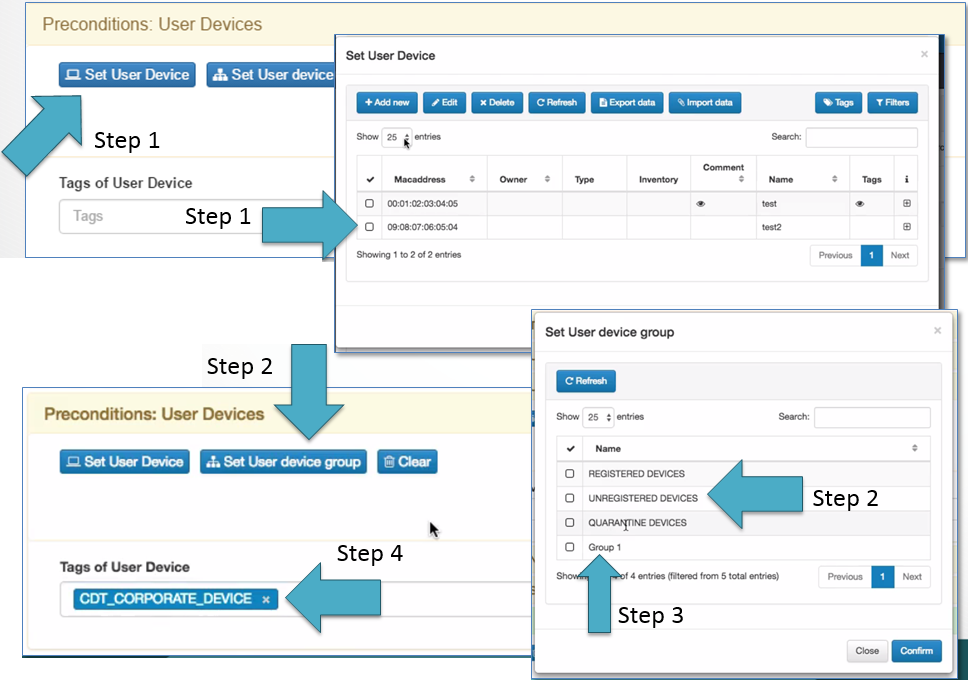
One of the preconditions available for the policy engine are the “User Devices”, the users devices registered in the openNAC CMDB can be selected by the policy. A list of users devices can ben selected following the steps 1.
The system out of the box includes a group of users devices as shown by the step 2 that can used:
- Register Devices: are all the user devices that are registered in the openNAC CMDB.
- Unregistered Devices: are all the user devices that are not register in the openNAC CMDB.
- Quarantine Devices: are all the devices that were sent to quarantine.
Any customized user device group can be created, for instance the manually created name “Group 1” as shown by the step 3.
The Tags can be used to reference a groups of user devices, with then we can chose User devices that share characteristics or security posture attributes, the example shows by the step 4 is CDT_CORPORATE_DEVICE tag that tries to groups corporate devices.
Tags are part of CMDB database, we have many tags created by default, other dynamic based on events or also can ben created by openNAC administrator following a simple procedure at ON CMDB –> Tags
As a user precondition administrators can use the tags. For review some available tags:ref:Tags table<tags_table>
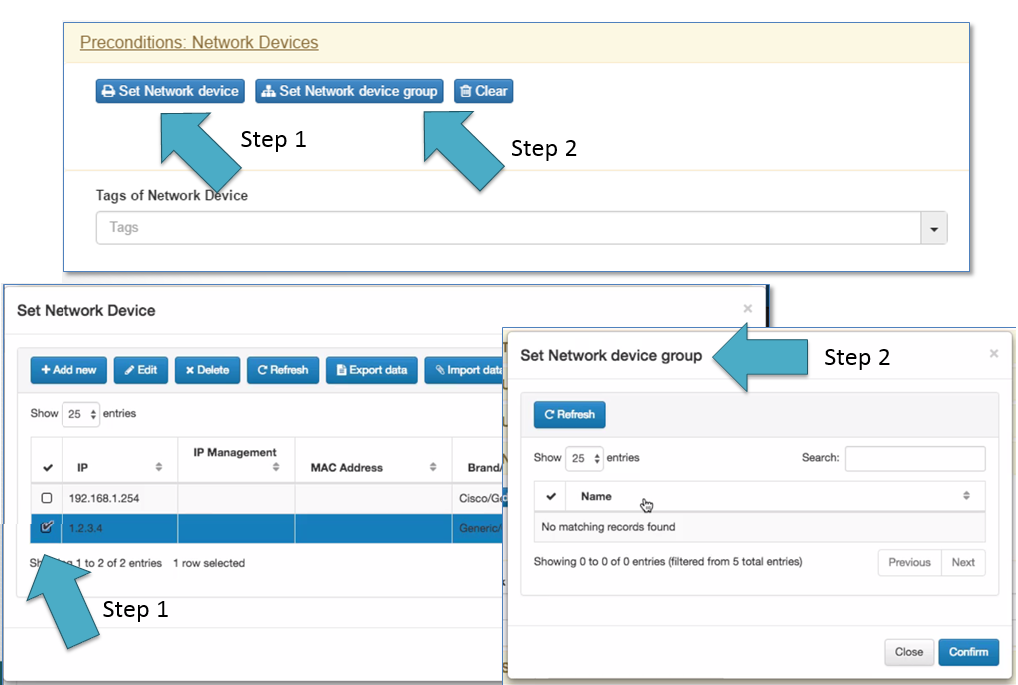
Network Devices¶
Network device is one of the Preconditions that can be used by the police engine.
Can be selected a single device as shown at the step 1.
Can be selected a group of network devices as shown by the step 2.
Instead of using Network devices or groups of network devices, we can use Tags, in this example we use a tag called NDT_WIFI as shown by step1. NDT means “Network Device Tag” and “WIFI” tries to name the group of WIFI Access points.
We can also define the name of an SSID on which the devices match with this policy Step 2. This field admits regular expression in pecl format.
Remember that openNAC has a common standard for Tag naming, which include 3 letter for prefix at the beginning.
Sources¶
Allow us to define the authentication method to be used during network access request, is not recommend to use all at the same time, with tuned policy we can ensure better policy results and avoid mistakes.
MAB:
Mac Authentication Bypass method method is a emulation of 802.1x and in the case there is not 802.1x supplicant listened by switch port, the switch sends the mac as authentication method. Depending on switch order authentication configuration that is assigned to the port.
PRINTER, PHONES, OTHER DEVICES that doesn’t have a supplicant 802.1x commonly use this authentication method.
Supplicant User:
Enabling it allows to authenticated 802.1x supplicant, a common scenario may be a supplicant configured with EAP-MSchapv2. Is common to use an user/name and password credentials. In this type of authentication is could be used server certificate and this be issued by a supplicant user trusted Certification authority (recommended).
Supplicant Host:
Enabling this type of authentication methods is allowed to authenticate the workstations using the computer account, this account is an Active directory, the workstation account must be registered in the Active Directory domain to be used. A common scenario could be if we have a support team and needs that corporate devices gain access to the network to provide remote connection with user logon.
In case you don’t have Supplicant Host configured you will not get network until user and password are introduced, only users with cached credential can access to the network.
A common practice is to create a TAG when the authentication comes from Supplicant host, we tag all the authentication attempts that comes from this type of authentication to identify which workstation are part of the Active directory domain or a Corporate account and with that tag we can take further policy actions.
Supplicant Certificate:
Enabling this type of authentication method we allow to use a digital certificates (This can be a user certificate or machine certificate), EAP-TLS adapts to this authentication method.
VPN:
Enabling this authentication method we allow commercial VPN servers to be authenticated, remember that openNAC technologies allows to use 2FA.We can use OTP using Google Authenticator OTP + Password. Mobile connect could be used. We have to define at radius level the IPS of the VPNS concentrator. Juniper, Cisco, Fortigate, Viapps, Checkpoint or other commonly used VPN concentrator are easy to be integrated, the communication protocol between openNAC technologies and VPNs is radius protocol.
User:
Enabling it an user connection and then authentication attempts through applications are allowed. Administrator of Network devices such as Switches, routers, VPNs….is a common example, This means that we can use openNAC to authenticated access to network devices, we can create also authorizations. For instance in a common authorization scheme Cisco Switches includes different authorization profiles (Privileges Levels) which allow to define a command available for every privilege level. Also is possible to map privileges with Active Directory Groups, for that implementation is used Radius attributes.
Visibility:
Enable the visibility source we allow the openNAC core to process events that comes from openNAC Sensor. openNAC technologies includes openNAC Core, Analytics and Sensor components. For instance and as a use case, devices learned by openNAC Sensor are sends to openNAC Core adding a TAG such us SRC_Sensor
SNMP Trap:
Enable the SNMP TRAP source we allow the openNAC core to process events that comes from SNMP TRAP sent by network device. This trap must be in version 1 or 2 and include the MAC address of the end point device.
openNAC technologies includes openNAC Core, Analytics and Sensor components. For instance and as a use case, devices learned by openNAC Sensor are sends to openNAC Core adding a TAG such us SRC_Sensor
Postconditions¶
When we talk about post conditions we have to mention a few points:
At the Step 1 we are able to assign VLANs dynamically (Logical segmentation), we have three important options to be considered.
VLAN 533 (Provide VLAN):
This is an example to define a service VLANs, any VLAN id can be used.
VLAN 0 (Provide switch default VLAN):
This is the value that needs to be sent to use Switch default VLANs, this means that the switch will assign the default VLAN configured on switch port.
VLAN 4095 (Wrong VLAN):
This is the value that needs to be sent to deny the Network access attempts, 4095 is out of valid VLAN scopes and for that matter sending it the network device will deny the access.
In case we have a voice VLAN in the access switch port , the step 2 allows to configure compatibility with voices VLANs.
At the step 3 is defined the Security Profiles, these can be set a dynamic and static ones, for further information ON CMDB –> Security Profiles Security Profiles.
At the step 4 are define and activate Plugins and its parameters.
At the step 5 is defined to sent log error through a syslog, by default this is in a disabled mode.
At the step 6 is defined openNAC Policy notifications, emails can be sent when a rule is matched (triggered), this can be really useful to send important security notifications to the Security operation Centers.
At the step 7 is possible to add extra radius parameters, vendor radius dictionaries (attributes and its values) must be considered and sometimes imported, For instance, modify session timeouts, assigning pool IP or apply policies based on identities and many others…
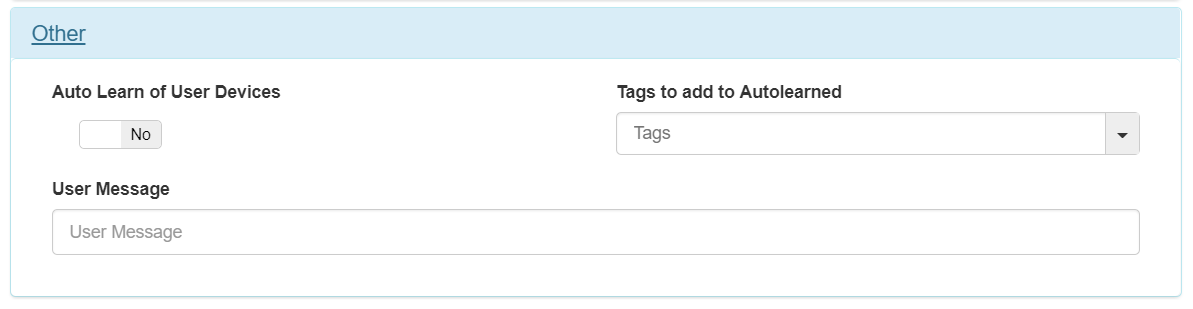
Other¶
Auto Learn of User Devices: allows openNAC to add the unknown devices that access this policy to the database.
Tags to add to Auto Learned: add tags in the devices that openNAC has self-learned. Only works with “Auto Learn of User Devices” activated.
User Message:: openNAC can send message for devices with openNAC agent installed, it will appear in a pop-up window at connection time, a message using the captive portal can be used as well.