MAB¶
- Is recommended to follow and read the overview about openNAC solution.
- To deploy an openNAC is required to understand and follow network requirements.
- As soon as you have deployed the openNAC is recommended to select the proper use case that fits with you requirements.
- Selecting the use case, an scenario must be configured to covert as much as possible customer needs.
This page shows which steps are required to configure UNAC Radius MAB based on.
1. DEFINITION¶
This scenario allows to authenticate the assets connected to your corporate network using the MAC address of the devices.
2. MECHANISMS (How does it work?)¶
Using MAB approach openNAC can perform a Network Access Control.
- When the host is connected to a network device (ND) interface, the ND sends MAC address to openNAC.
- The ND sends authentication package for openNAC Core. Then openNAC executes the authentication and authorization process, answering the ND if the host has allowed access and, in addition, the corresponding vlan defined in the policy.
- ND fixes the port in the vlan received by openNAC.
- The host ask for DHCP and continues with the normal process of accessing the network.
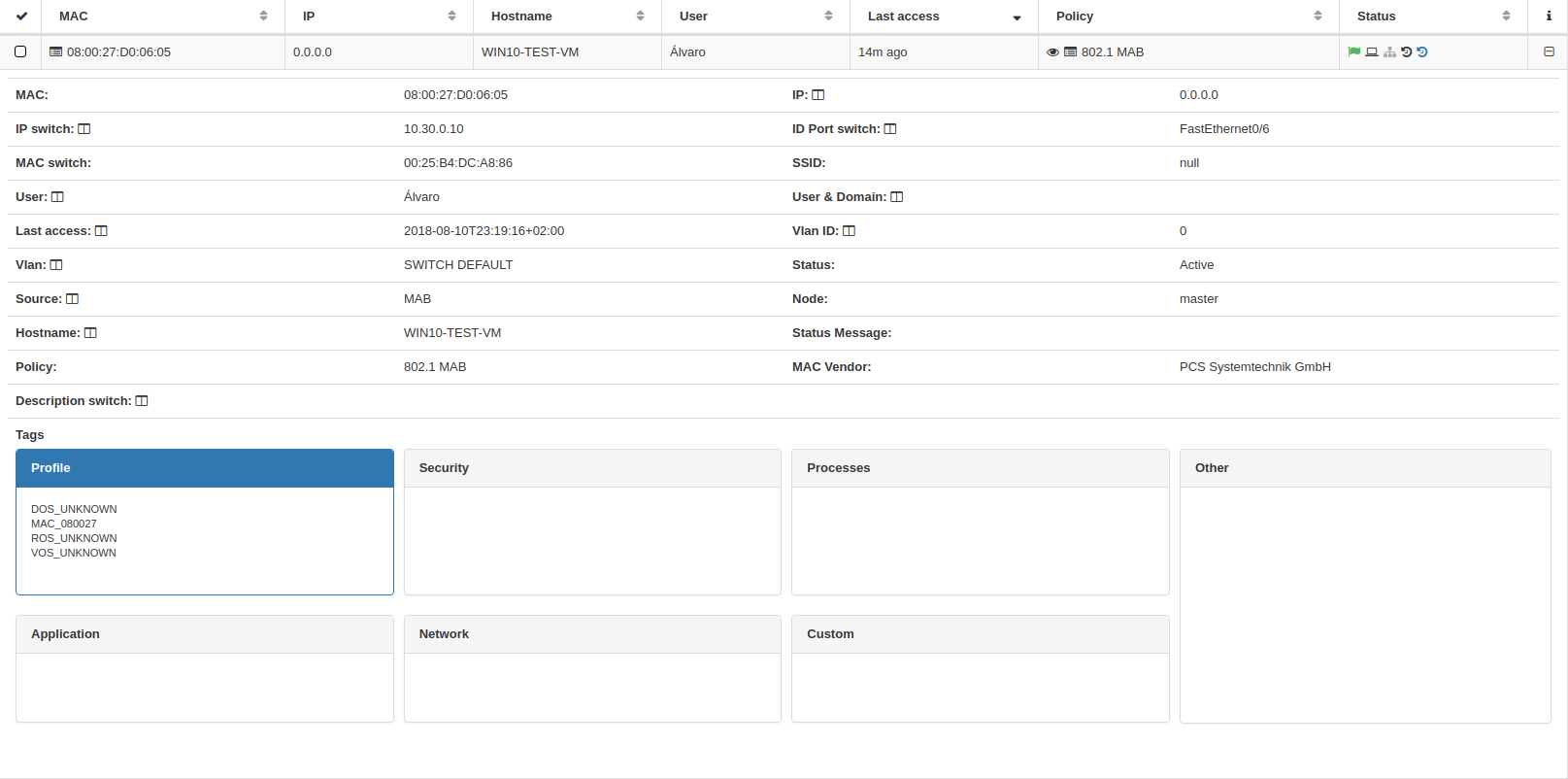
3. DASHBOARD (How do we display the information?)¶
For each authenticated device that connects to the network, openNAC displays the following information.
4. DEPLOYMENT (Do it yourself)¶
The following is a light guide to deploy UNAC MAB mode based on basic lab.
4.1 REQUIREMENTS¶
- openNAC Core.
- Network device 802.1x (switch, ap..) in the following scenario will be used Cisco switch with IOS 12.2.55 or higher.
- openNAC Analytics. (Graphic Output)
- Client PC, in the following scenario will be used Windows 10.
4.2 SCENARIO ARCHITECTURE¶
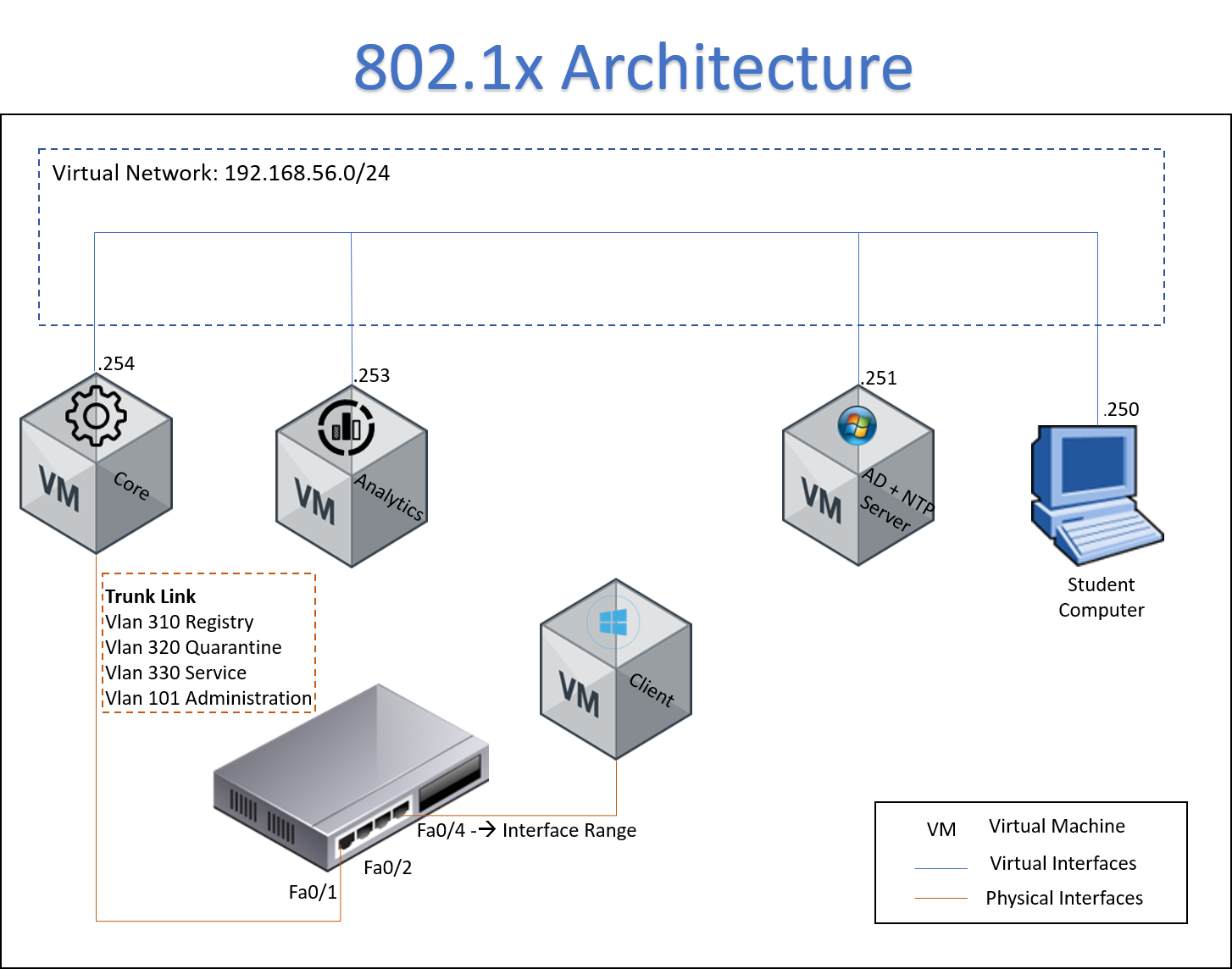
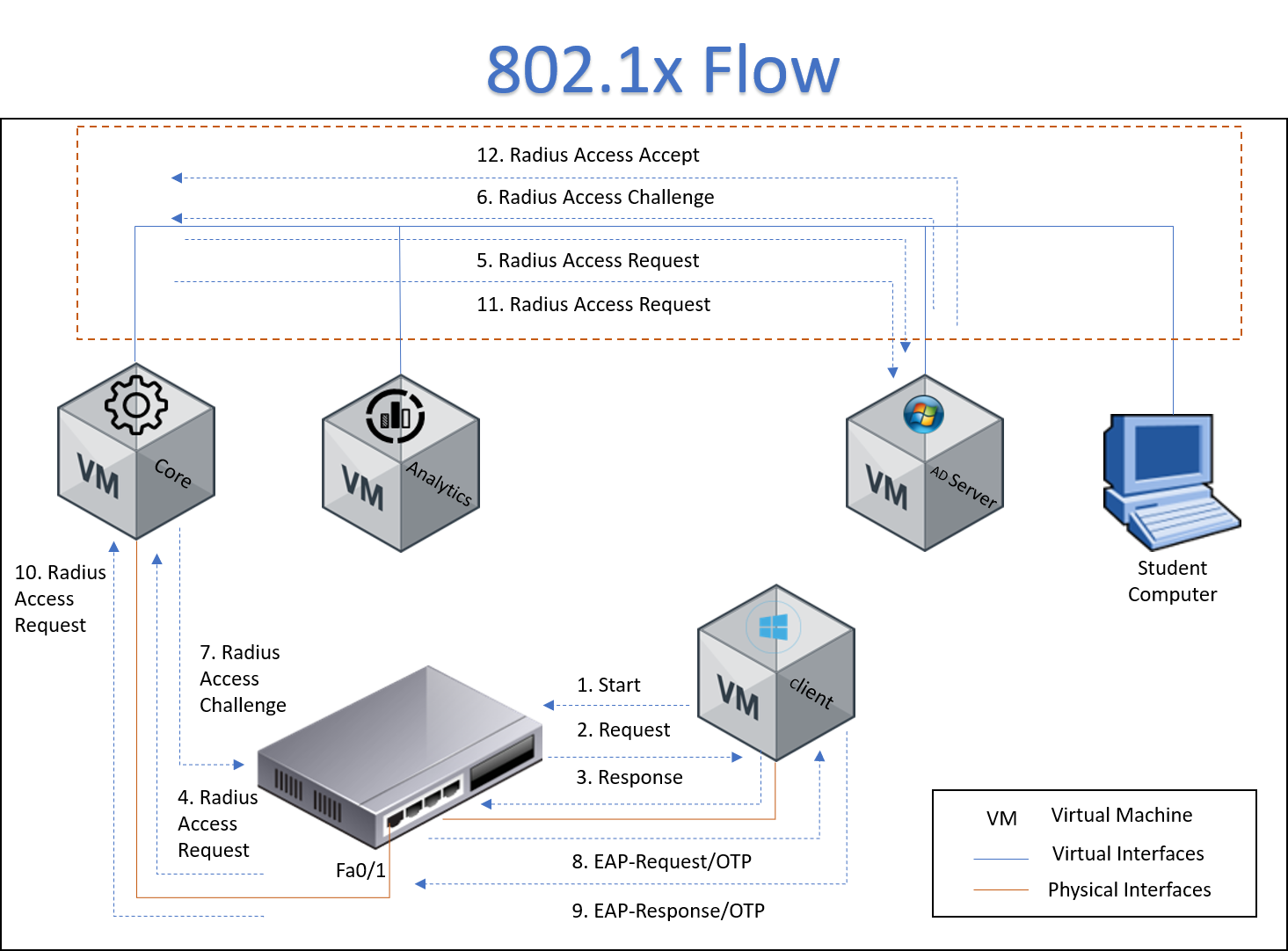
- The client is connected to ND and start the process for network access
- The ND check if the host has supplicant (not in this case)
- The ND send the radius access request to ON Core with the mac address of the host
- ON Core check the mac address in the local DDBB
- ON Core validate the host via policy and send the OK to the ND
- The switch allow access to the host an set the vlan sended by openNAC
4.3 SETTINGS¶
On Switch
The following link contains the required configuration on switch for UNAC use case.
Basic 802.1x Cisco Switch Configuration
On Core
OpenNAC automatically can add the assets connected to network to a local CMBD using auto-learning option into policy rule AutoLearn Policy.
Administrators can also add assets (user devices) manually to local CMDB:
Add the device MAC address to openNAC DDBB. Go to ON CMDB –> User Devices. Select Add New option.
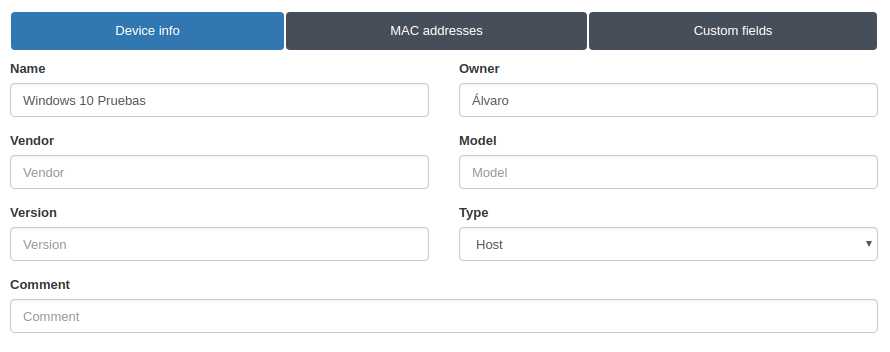
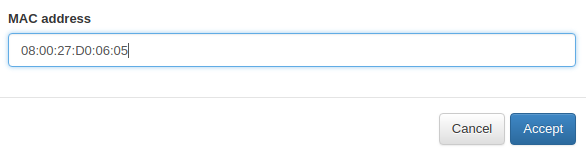
Fill the name field and go to MAC address tab. Select Add New option.
Policy Configuration
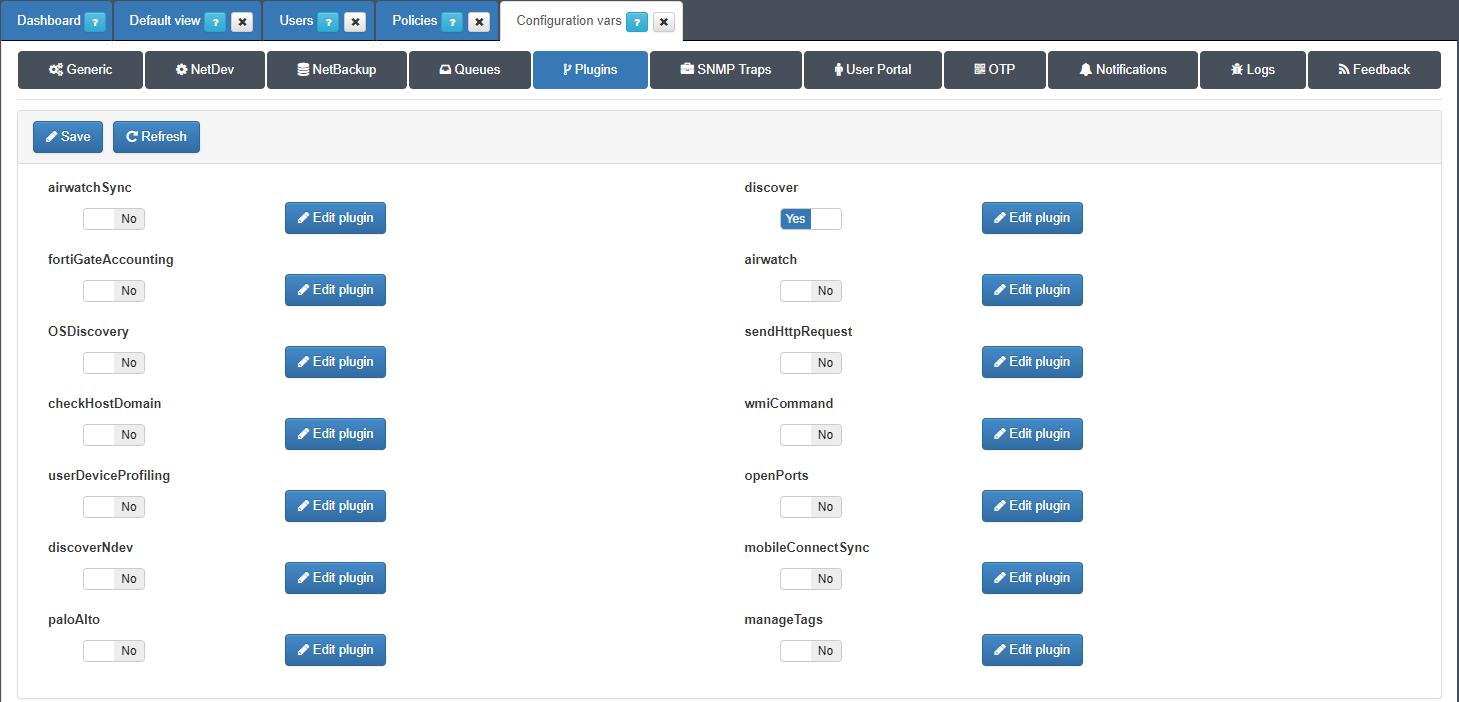
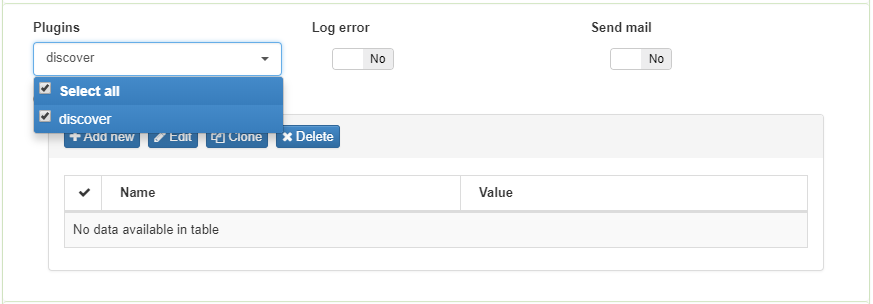
Before configure the policy rule enable Discover plugin. For visibility propose, openNAC use a plugin knows as Discover, this plugin runs a “scan” over each endpoint which can reach trough IP address. So the first step is enable the plugin.
Go to Configuration –> Configuration vars, select plugin tab and enable Discover plugin.
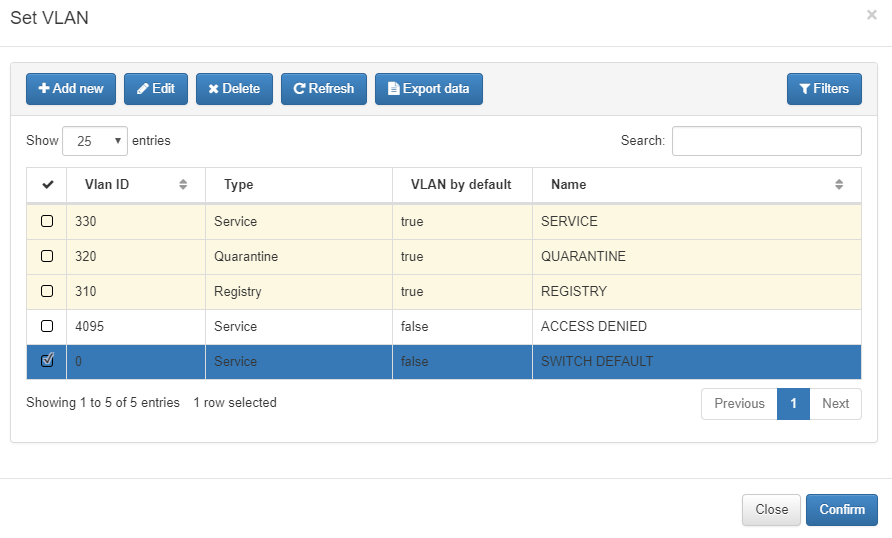
Policy for Local Database
In this case the assigned VLan will be the same, so set Switch default VLan.
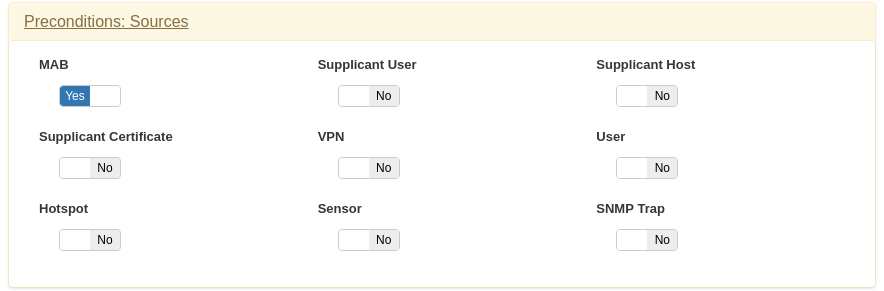
In Preconditions Sources activate MAB option.
Optional Enable plugin Discover into policy rule. This is to gain assets visibility. To get more assets information as output.
4.4 TESTING¶
Turn on the client VM, use the 802.1x configured interface on switch to connect the host.
After authentication process.
Go to ON NAC –> Business Profiles –> Default View. In this section you can see in real time the access from endpoints.
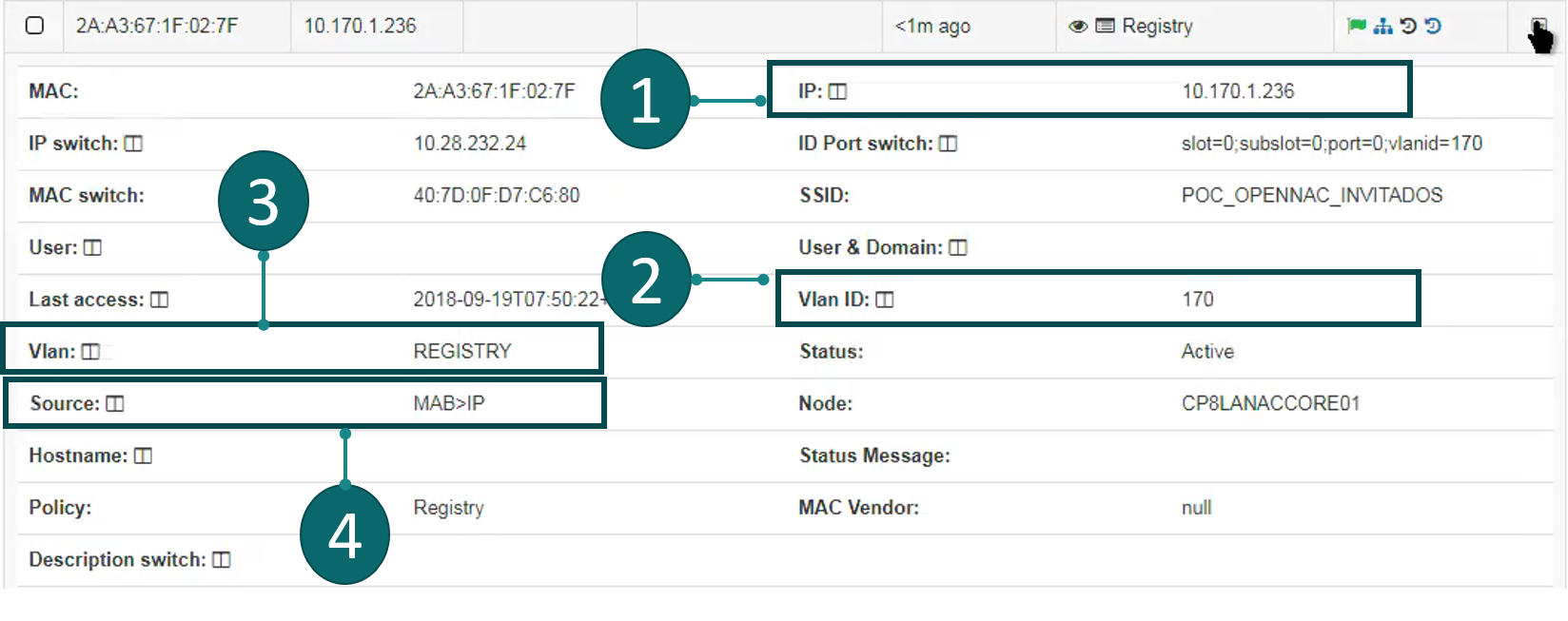
Is important to capture the IP address, using it openNAC will run the plugin over each know asset which match with the previous configured policy.
MAC, IP address, user group can be verified for each hit on the define policy access rule.
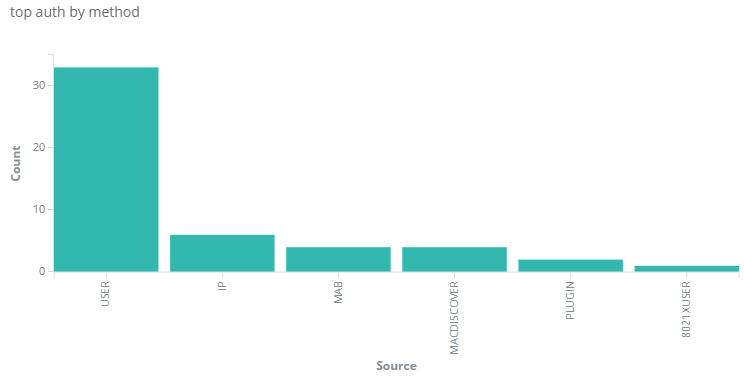
Also in the first console screen the authentication hits by method should be reflected.
4.5 TROUBLESHOOTING¶
- Please perform a basic review Basic Check
- To perform a debug of authentication proces you can verify the link Radius Troubleshooting