1.2.6. 802.1x
8021x is a network access control protocol that permits or denies device access to the network by using authentication. Ethernet switch ports can be enabled dynamically based on the identity of the device that connects to it. Devices that are not authenticated cannot gain access to the network.
802.1x Authentication Components
A supplicant: a client device (such as a laptop or endpoint device) that attempts to access a LAN/Wireless LAN (WLAN), or the software that runs on this device and provides credentials to the authenticator.
An authenticator: a network device (such as an Ethernet switch or wireless access point) that acts as an access point to a protected network. For 802.1X authentication, the supplicant provides network credentials, such as username, password, digital security certificate, or a combination of these, to the authenticator. The authenticator then forwards the credentials to the authentication server for verification.
An authentication server: a server (such as ON Core) that guards the protected network. For 802.1X authentication, the authentication server receives the supplicant’s network credentials from the authenticator and verifies the supplicant’s identity so the supplicant can access the resources located on the network.
The figure below illustrates the fundamentals of the 802.1x protocol:
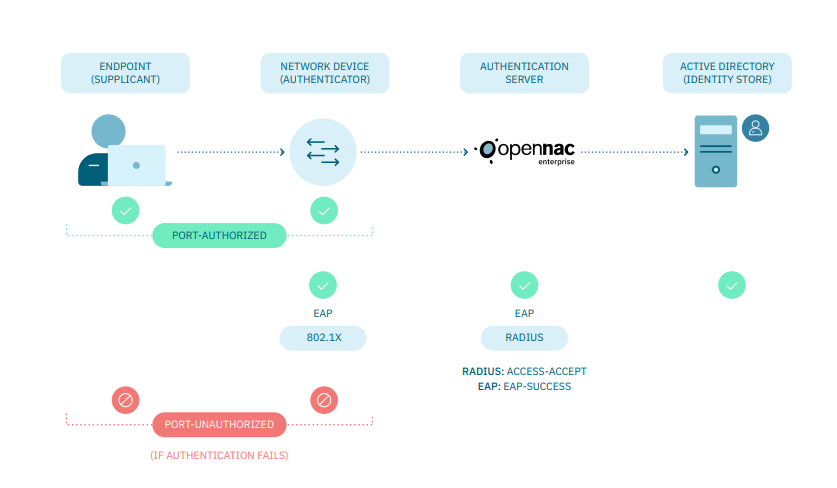
Supplicant: Software running on the client that provides credentials to the authentication (Network Device).
EAP: Extensible Authentication Protocol.
802.1x is based on RADIUS (Remote Authentication Dial In User Service) protocol which consist in a standardized method of information exchange between a device that provides network access to users called RADIUS client and a device that contains authentication information for those users called RADIUS server.
Here we can see the 802.1x request process:
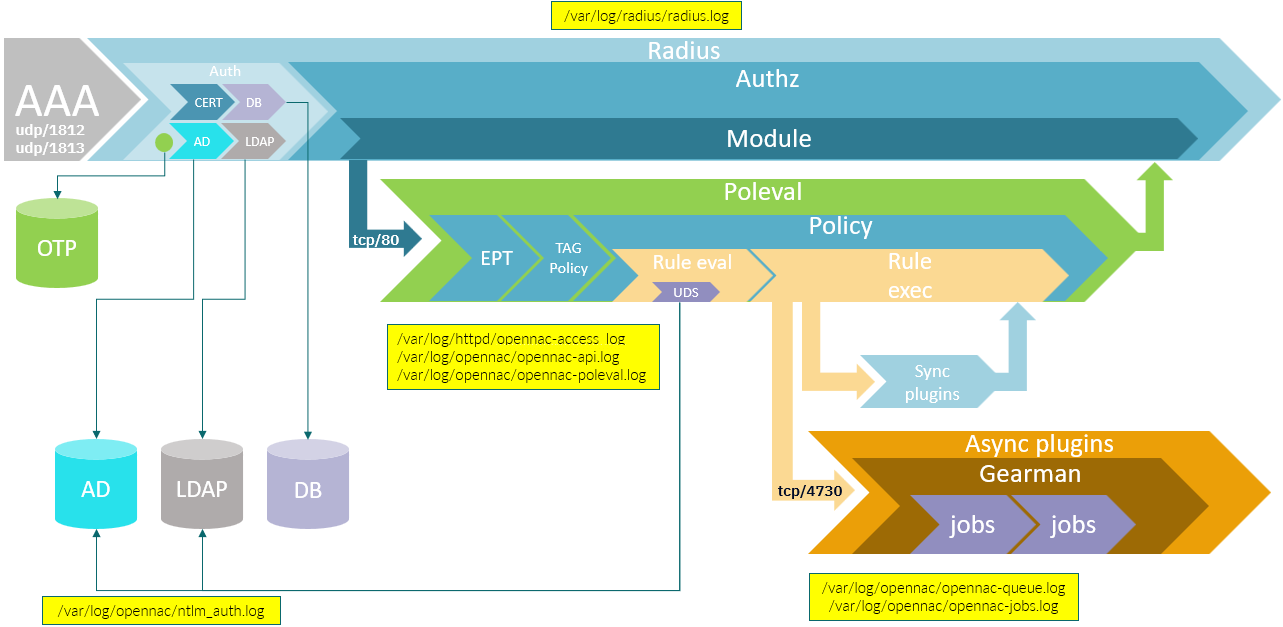
The process starts with an authentication request. A user device (that is already registered on the local database, AD o LDAP) attempts to access the network by providing its credentials (user/password or certificate) to the authenticator (network device. i.e. switch, access point, etc.).
The authentication server will execute a policy evaluation to check if the user device matches any of the policies that we have configured.
These policies contain some preconditions, to check user data source, user device tags, user session, source, etc. If all of them match, we will then apply the defined postconditions, this includes VLAN assignment, plugin execution, etc.