1.1. Introduction
Welcome to OpenNAC Enterprise documentation.
1.1.1. What is OpenNAC Enterprise?
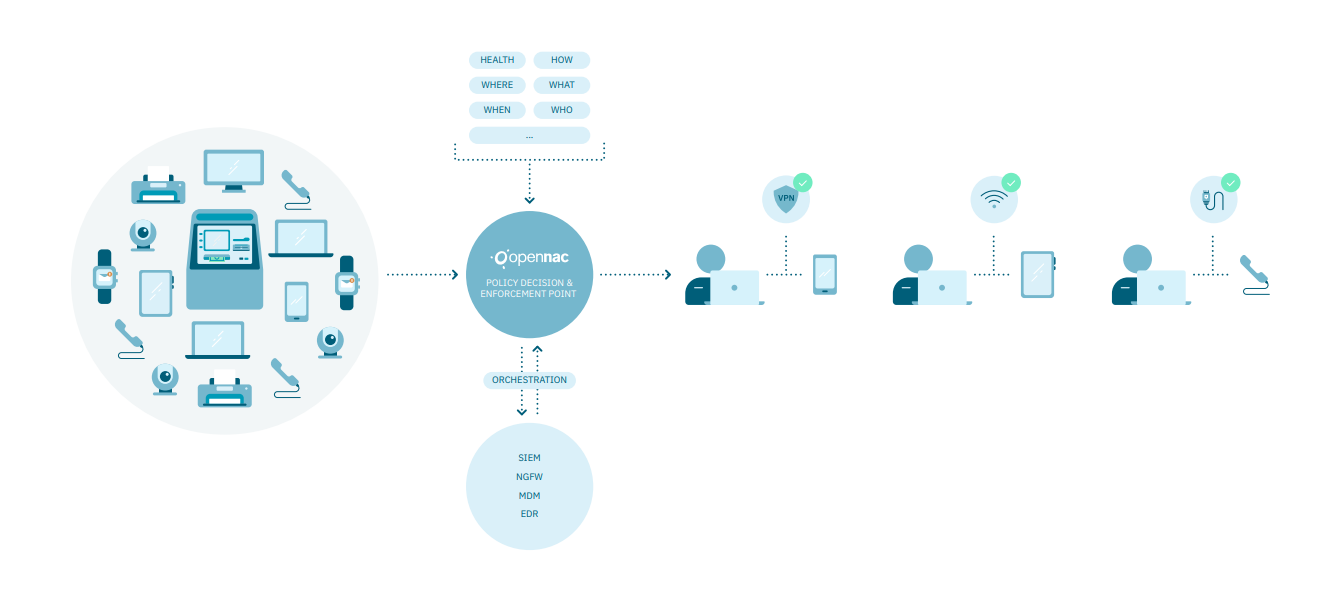
OpenNAC Enterprise is a network access control platform for LAN/WAN environments that allows corporations to authenticate, authorize and audit all access based on a set of rules or policies.
OpenNAC Enterprise is a software-based solution that increases network security by giving organizations 100% visibility and control of assets (devices + identities) connected to the network (Cable, Wi-Fi & VPN).
OpenNAC Enterprise is the only EU vendor mentioned by Gartner since 2018 in NAC (Network Access Control) Market Guides and the only Modular Approach solution.
THE RESPONSE: Modularity. What you need, when you need it.
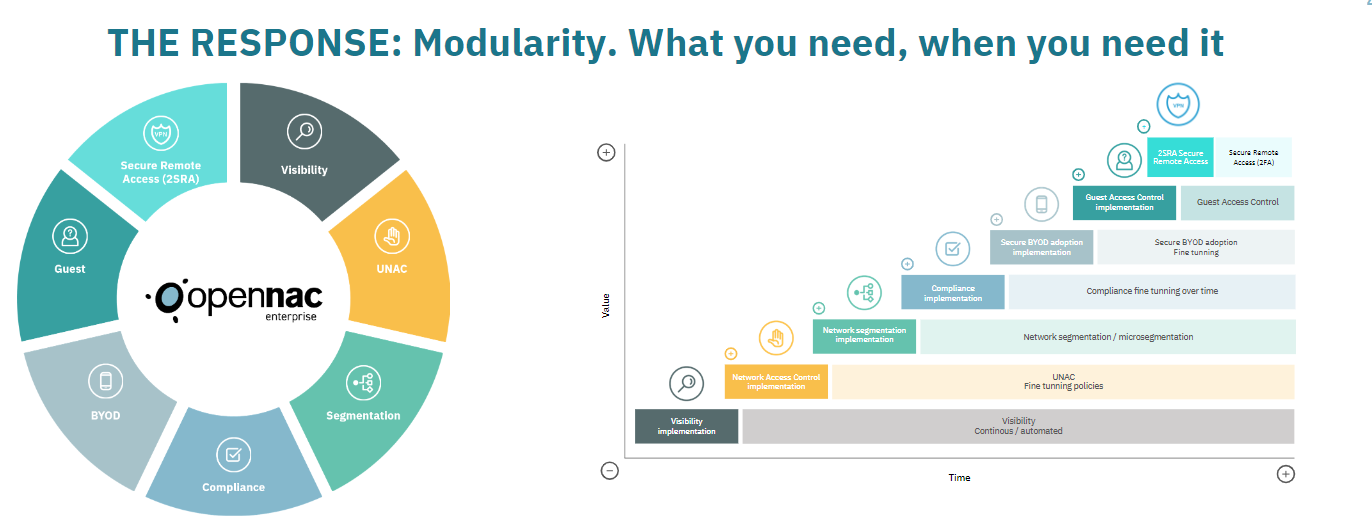
With the all-or-nothing approach most organizations cannot buy a full solution only to use 20% of it.
Invest ONLY in the modules that respond to your needs today.
Gain quick wins and reduce financial and operation risk by reducing the scope of each phase.
1.1.1.1. OpenNAC Enterprise Key Benefits
OpenNAC Enterprise helps organizations gain up to 60%+ more visibility and full control of their assets to mitigate the impact of IoT, business disruption attacks & auditing pressure.
So the main benefits for our customers are mainly:
Visibility: A software solution that Increases network security by giving organization 100% visibility.
Control: Control of assets (devices + identities) connected to the network.
Modularity: Use your security depending on your needs.
Efficiency: Combines uniqueness, centralized management, automated visibility, and seamless policy application for your security needs.
1.1.1.2. OpenNAC Enterprise Key Functionalities
The main functionalities of OpenNAC Enterprise are the following:
Authentication: |
It allows checking the identity of the entities (users and/or devices) that access the corporate network. The identity can be validated against several repositories of information (eg Active Directory), through digital certificate, or MAC address, among others. |
Authorization: |
It offers the possibility to assign specific privileges to each entity that connects to the corporate network, for example assigning a certain VLAN. |
Audit: |
It allows collecting, grouping and evaluating access events or attempts to access the corporate network and thus have a history of the activity on the network. |
Inventory: |
The solution has a configuration management database (CMDB) that gathers the details of each identity that connects to the network. |
Profiling: |
It provides the ability to establish and check a profile of a specific state for an identity, which can also be determined to be obligatory to access the network. For example, a particular version of an operating system, a particular level of update, antivirus presence, or similar might be required. |
Posturing: |
It allows to evaluate in real time the behavior of each of the devices connected to the network and to determine if that behavior is within the expected parameters, taking corrective measures otherwise. |
Remediation: |
Linked to the previous point, this functionality offers the possibility of executing the necessary actions to remediate, or at least minimize, the detected threat. Examples of remediation may be to isolate the compromised entity from the corporate network. |
Double Authentication Factor (2FA): |
This functionality is specially designed to complement access control through VPNs with a second factor of authentication. The technology that supports this second factor of authentication can be Google Authenticator among others. |
Native Agent: |
Installed in the device (Windows / Linux / Mac) allows to extract information from the connected entity in a more agile way and respond more quickly to detected anomalies and threats. |
Integration with SIEM: |
It allows to integrate OpenNAC Enterprise with a third-party SIEM, and to send and concentrate the NAC logs with the rest of corporate information systems. |
Orchestration Security: |
It allows to use OpenNAC Enterprise as a security orchestration element, thanks to the communication with other security elements in the network (next generation firewalls, antivirus, IDS probes, MDM, …). These integrations are bidirectional, ie, on the one hand, OpenNAC Enterprise can supplement its CMDB with information received from third parties and thus take more informed decisions. On the other hand, OpenNAC Enterprise can provide information to those same third parties so that they can make decisions based on more complete information. |
Sensor: |
This module allows to complement the vision of the behavior of the entities through the inspection and classification of the network traffic arriving at the application level (layer 7). It also allows visibility over network segments that are not managed by the NAC. |
1.1.2. OpenNAC Enterprise Scenario
OpenNAC Enterprise is a suitable solution for large corporations with the need to limit access to network resources according to devices and users’ identities. The network infrastructure can be wired or wireless, and the network devices (switches and access points) may support the 802.1x protocol, but it is not mandatory.
The basic components of the network are:
ON Core
ON Analytics
ON Sensor
ON VPNGW
RADIUS Server
DNS Server
DHCP Server
Network devices: Switches, Access Points and Firewalls.
User devices: PCs, Laptops, Smartphone, voIP Phones, Printers, Tablets and others.
In case the corporate network has no RADIUS Server, DNS Server, or DHCP Server, OpenNAC Enterprise itself can provide them.
In addition, a directory server can be added to authenticate users.
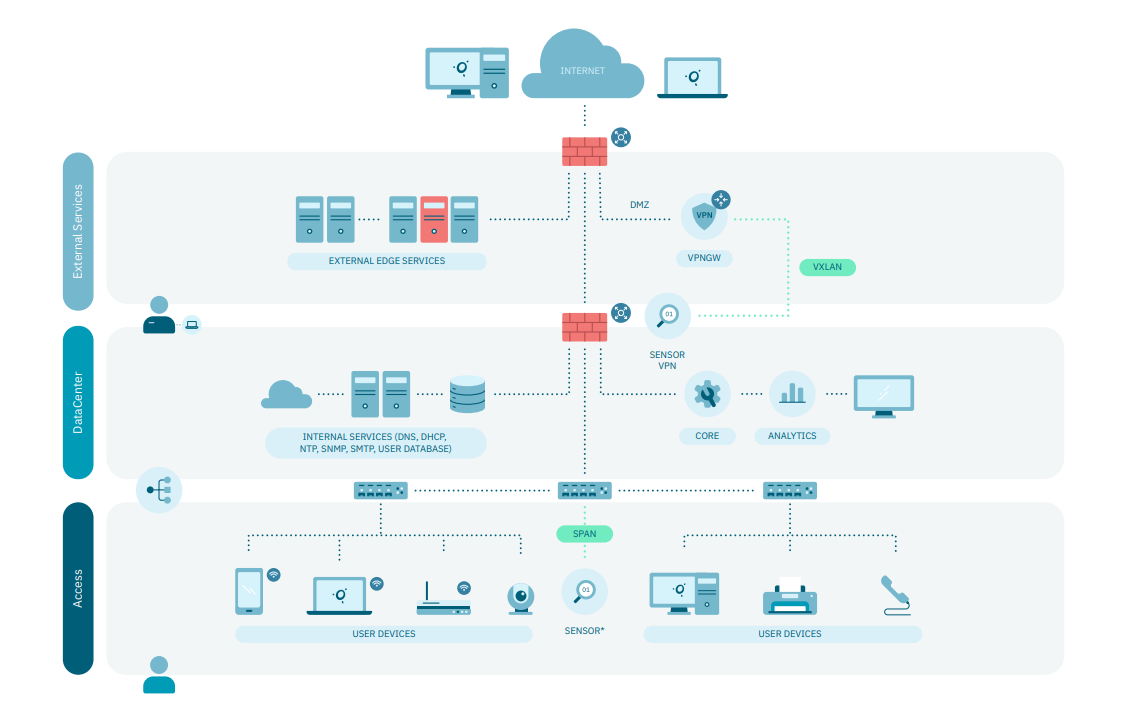
The graphic above depicts a typical architecture, where OpenNAC Enterprise establishes three subnets to the user devices to provide secure access to resources:
1. Registry VLAN: OpenNAC Enterprise assigns the new network users to the Registry VLAN so they can register from there.
2. Quarantine VLAN: User devices that don’t comply with the policies configured in OpenNAC Enterprise are allocated to the Quarantine VLAN until they are updated to comply with those policies.
3. Service VLAN: The Service VLAN is the network that provides corporate resources to the user’s device. Depending on the number of user devices and access rights to these resources, there may be one or more service VLANs.
Note
OpenNAC Enterprise assigns user devices to the different service VLANs based on policy compliance defined by the administrator.
1.1.3. Choose Your Use Case
One of the most important steps in the process of selecting a security tool, or any kind of business tool for that matter, is understanding and defining the use cases that the tool should cover. The Use cases chapter describes examples of use cases covered by OpenNAC Enterprise.
When defining your own Use Cases there are a few questions you should be asking yourself, like for example:
Currently, do I have visibility over users and devices accessing my network? How?
What connection methods do I offer my users? (WiFi, Cable, VPN?)
Are users authenticated when accessing my network?
Are there external/guest users in my network?
What type of devices are accessing my network?
Only corporate devices or also external non-managed devices?
How do I define a corporate device?
What is my BYOD policy?
What about IoT devices?
Is my network segmented? If so, is the segmentation dynamic and efficient? What happens when a user changes location? Do I need to manually reconfigure the network?
What other security solutions do I have in place? Are they working in a collaborative and orchestrated manner?
At OpenCloud Factory, we would love to hear your answers and any other questions you may have and help you to evaluate how a network access control solution could enhance the visibility, control, and security of your network.
1.1.4. Design OpenNAC Enterprise Deployment
The following steps are necessary for OpenNAC Enterprise Deployment.
1.1.4.1. Understand the Network Architecture
In order to provide Network Access Control services, first of all, we have to consider OpenNAC Enterprise as a flexible technology that is able to adapt to your current network design, topology, and communications vendor. Depending on the Network Access services that are required to be provided, Layer2, Layer3, and Layer4 Network requirements must be clearly understood and considered.
To understand how OpenNAC Enterprise is flexible and very adaptive to your current network infrastructure, please:
Note
Please review the following section regarding Network Requirements.
As soon as you have a clear network Knowledge/Design:
- Layer 2 Requirements:
Ensure that VLANs are available and deployed to be used by the solution.
- Layer 3 Requirements:
Ensure IP connectivity between OpenNAC Enterprise Nodes, Roles (Core, Sensor, Analytics), communication devices (Switches, AP, Printers, Video conference, IOT….), and if required End users (Captive Portal).
- Layer 4 Requirements:
Ensure that no Firewall or Next Generation Firewall is filtering TCP/UDP network traffic.
1.1.4.2. OpenNAC Enterprise Infrastructure Sizing
As with every Network Access control provider, infrastructure must be sized properly to meet at least the minimal requirements. ON Core, ON Analytics, and ON Sensor have different roles and different hardware sizing requirements. Here you can find the sections created to understand hardware requirements:
Go to ON Core Hardware Sizing section
Go to ON Analytics Hardware Sizing section
Go to ON Sensor Hardware Sizing section
Go to ON VPNGW Hardware Sizing section
In order to define the scope, understand customer requirements, and which use cases fit better, we have created a bundle of questions to be used at the beginning of new projects:
Note
Understanding Project Qualification is crucial for successfully implementing Network Access Control solutions in Enterprise Networks. The Project Qualification is a document that consolidates all customer requirements for deployment. Grouped by general requirements and by each OpenNAC Enterprise Use Case.
1.1.5. OpenNAC Enterprise Technical Key Features
Authentication based on 802.1x Supplicant, UserName/Password, Computer, Certificates, Users, MAB, Captive Portal, Web Service, 2FA Supports (Gauth, MConnect..others).
Authentication backend based on LDAP, Active Directory, BBDD, and others.
Strong and Flexible Network Access solution without Agent dependency.
Easy Policy Engine to improve Security Operation, time, users, groups, devices, tags, network devices, type of authentication, and others can be used.
Actions: VLAN Dynamic assignment, Layer2,Layer3 and Layer 4 Access-Lists, Plugins support, Custom parameters allowed and status and assets tagging.
Policy grouping through Business Profiles.
Flexible supporting any type of devices such as PCs, Laptops, Smartphones, Tablets, voIP Phones, IOT, Videoconferece Systems, Applications, etc.
Flexible Proxy Radius capabilities included.
Guest Access Network solution based on sponsorization and flexible workflow.
Includes Multi-Platform OpenNAC Enterprise Agent, this includes plugins that provide additional capabilities.
Network Devices vendor agnostic.
Based on dynamic CMDB Attributes and Tags.
Powerful Assets Discovery and automatic classification.
Health and Security Posturing Services.
Thread Detection capabilities through Denylisted sources.
Events Geolocation Support.
Support to detect rogue devices using 802.1x or SNMP traps.
Bulk configuration of network devices using module onNetConf.
Bulk backup of configuration of network devices using module onNetBackup.
Detection of os, antivirus, firewall, and os updates of devices connected to enforce an access policy.
Inbound and outbound advanced network visibility based on protocol decodification.
API Rest system that improves ecosystem integrability.
Third Party Integration support, NGFW, AV, Patching using push and pull methods.
SIEM Integration supporting Syslog, CEF, LEEF and JSON output messages.
Administration portal is compatible for any Device and Browser.