3.1.10.4. One Time Password OTP
A One Time Password or OTP is an authorization code or dynamic password that can only be used one time. It is often used on login and it prevents several deficiencies associated with the traditional static login methods.
OpenNAC Enterprise offers the possibility to configure and manage OTPs to use this second authentication password when accessing to the VPN or the Web Administration portal itself.
Perform the OTP general configurations in the:ref:Configuration > Configuration Vars > OTP<confvars_otp> section before proceeding.
Note
If you are using the OpenVPN service, you must also configure the Core component before proceeding to the Administration Portal. If you are using Wireguard authentication, skip to the Administration Portal configuration.
Edit the /etc/raddb/huntgroups file and add a line with your VPN
vpn NAS-IP-Address == <VPN_IP_address>
Edit the /etc/raddb/mods-available/opennac and add the following line
vpnHuntgroupName = vpn
Lastly, edit the /etc/raddb/clients.conf file to add the vpn network
client <VPN_IP_address> {
secret = <preshared_key>
shortname = <VPN_identifier>
}
You can manage all tasks related to OTP Network Access within the Configuration > OTP section:
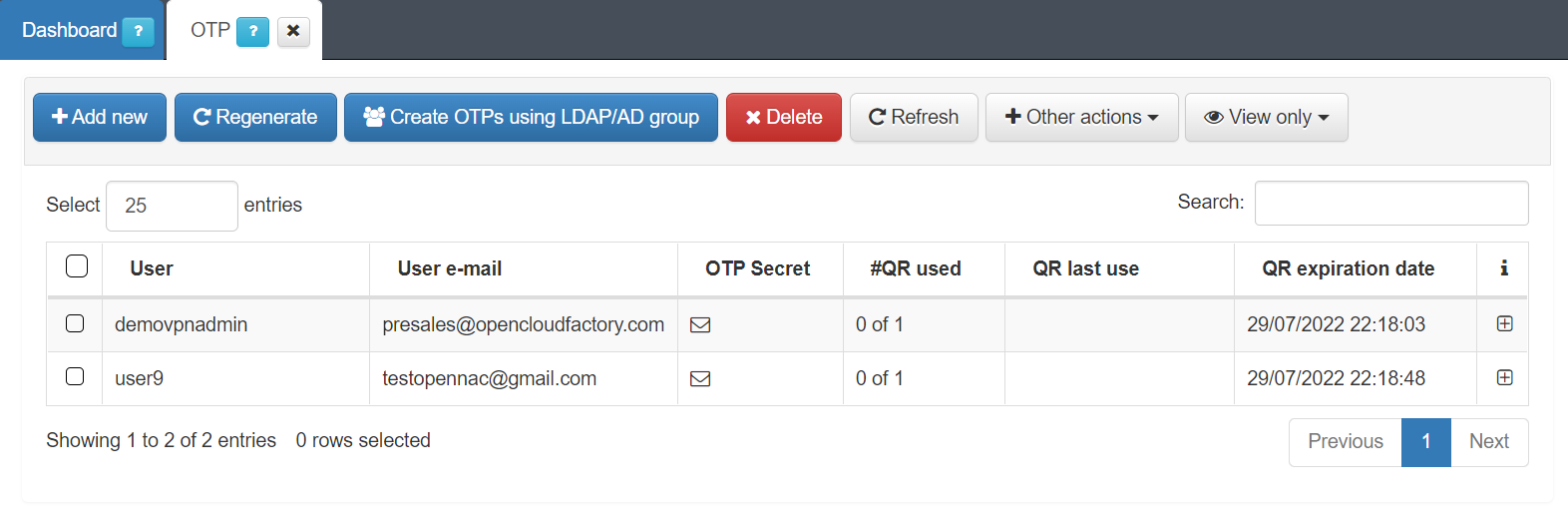
3.1.10.4.1. Adding new users
To add new users, click on the Add New button and enter the desired username for the QR owner. You can create OTPs for external users as well as for CMDB users (local users or admin users).

This view also allows you to Regenerate OTPs. To do so, select the user you need to regenerate the OTP for, and click on Regenerate.
Another way to generate OTPs is by selecting a group from an LDAP or AD directory. To do this, click on Create OTP using LDAP/AD group:
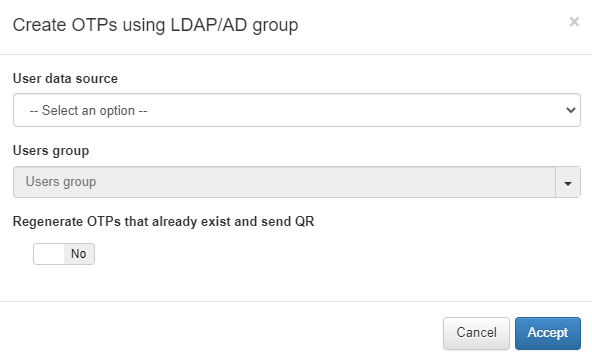
User data source: The LDAP or AD source we want to use.
Users group: The group of users that will be using the OTP.
Regenerate OTPs that already exist and send QR: Flag that allows to enable or disable the OTP regeneration if it already existed.
The view also allows you to Delete a selected OTP or to Refresh the page.
By clicking on Other actions, you can see the following drop-down menu:
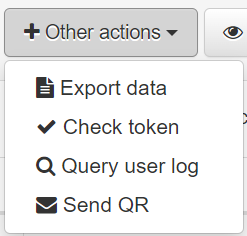
Export data: Export the data in JSON format.
Check token: Allows us to check a token based on a username.
Query user log: By selecting a user and clicking on this button, we will be able to see the log.
Send QR: To send an email with a QR to a specific user.
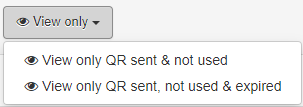
It is also possible to filter the entries by the QR that have been sent and not used, or sent not used and expired by clicking on View Only.
Search for a user and review its OTP parameters by clicking on the + icon.
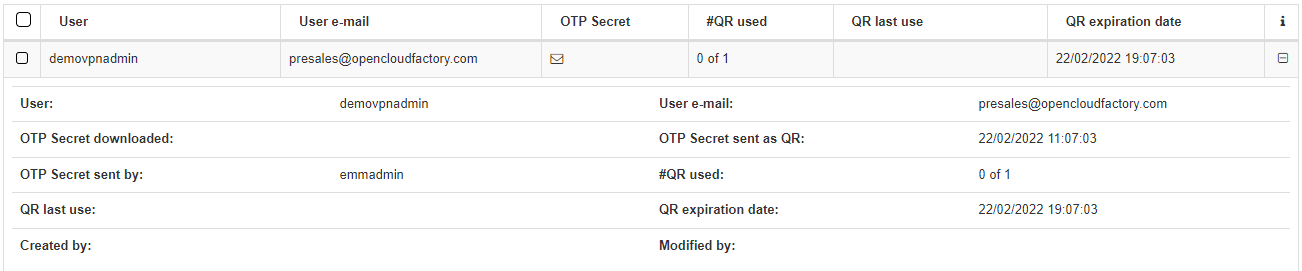
User: The owner of the QR.
User e-mail: The email where the QR has been sent.
OTP Secret downloaded: Boolean indicating whether the OTP has been downloaded or not.
OTP Secret sent as QR: Date and time indicating when the QR was sent.
OTP Secret sent by: The user that sent the QR.
#QR used: Number of times the QR was used.
QR last use: Date of the last use of the QR.
QR expiration date: Expiration date of the sent QR (in red if the QR has expired).
Created by: User who created the OTP.
Modified by: User who modified the OTP.
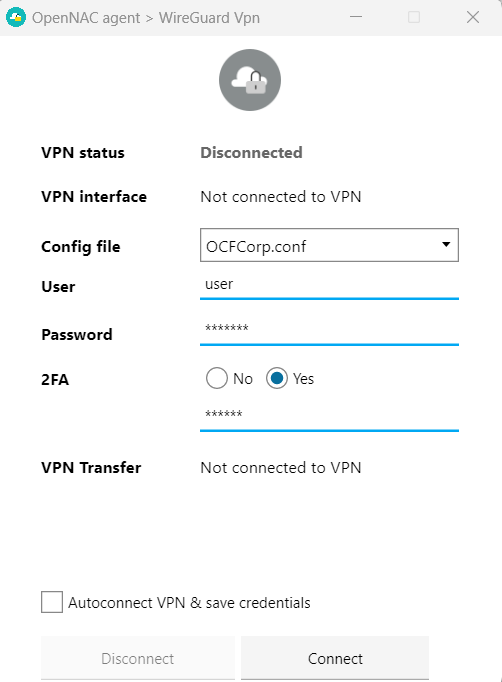
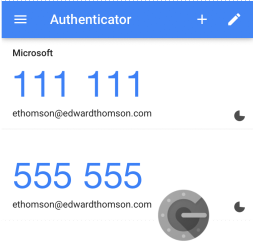
You can use your one-time QR with any authenticator app, such as Google authenticator. Once you scan the QR, a dynamic PIN will appear for about 30 seconds.
Now, you can connect to the VPN selecting the 2FA option on the authentication window and entering your username, password, and OTP pin.