3.1.10.2.7. fortiGateAccounting
This plugin allows sending session information to a fortiGate firewall. This information is sent through a RADIUS protocol and its port, and PSK (Preshared key) must be exchanged between peers to accept messages. The information includes the username associated and its IP address in the network.
This plugin allows that as soon as the user gains access to the network through OpenNAC Enterprise network access policies, it registers its information in the FortiGate Firewalls to allow access and unified network policies inside the OpenNAC Enterprise management.
For that, a User Group is used. For instance, it can be defined as a fortiGateAccounting_UserGroup, this means that the information is registered in a User Group that belongs to the Fortigate platform. In case the user accessing the network uses a Domain and sends this information in the events is required to be defined.
This plugin allows sending information related to the username associated with an IP address to the FortiGate firewall.
This information is sent by accounting radius protocol based on FortiGate RADIUS Single Sign-On (RSSO), for further information check: https://docs.fortinet.com/document/fortigate/7.4.3/administration-guide/85730/radius-single-sign-on-agent
To configure the fortiGateAccounting plugin we need to enter the following information:
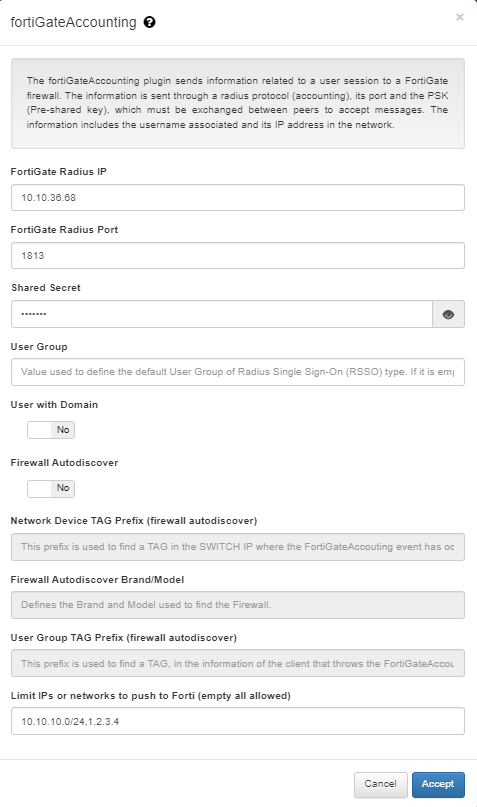
FortiGate Radius IP: IP to send radius accounting messages to FortiGate.
FortiGate Radius Port: Port to send RADIUS accounting messages to FortiGate.
Shared Secret: The shared secret to connect to FortiGate radius.
User Group: Value used to define the default User Group of Radius Single Sign-On (RSSO) type. If it is empty, any user group is used.
User with Domain: It indicates if the username sent to FortiGate has to include the domain name in case it is included in the user request.
Limit IPs or networks to push to Forti (empty all allowed): This parameter defines the range of IPs that can trigger the execution of the plugin. If an event occurs without an IP within the configured range in this field, the plugin will not be executed. On the other hand, if no IPs are configured, the plugin will always run regardless of the IP received in the initiating event.
Custom properties
The fortiGateAccounting plugin allows you to send a custom user group for all users who match the policy, overwriting the default user group specified in general plugin properties.
To provide this custom user group, you have to define a Custom param in the policy. The custom param has to be named fortiGateAccounting_UserGroup and its value has to be the user group associated with all users who match this policy.
To continue the FortiGate NGFW configuration, please read NGFW FortiGate Configurations.
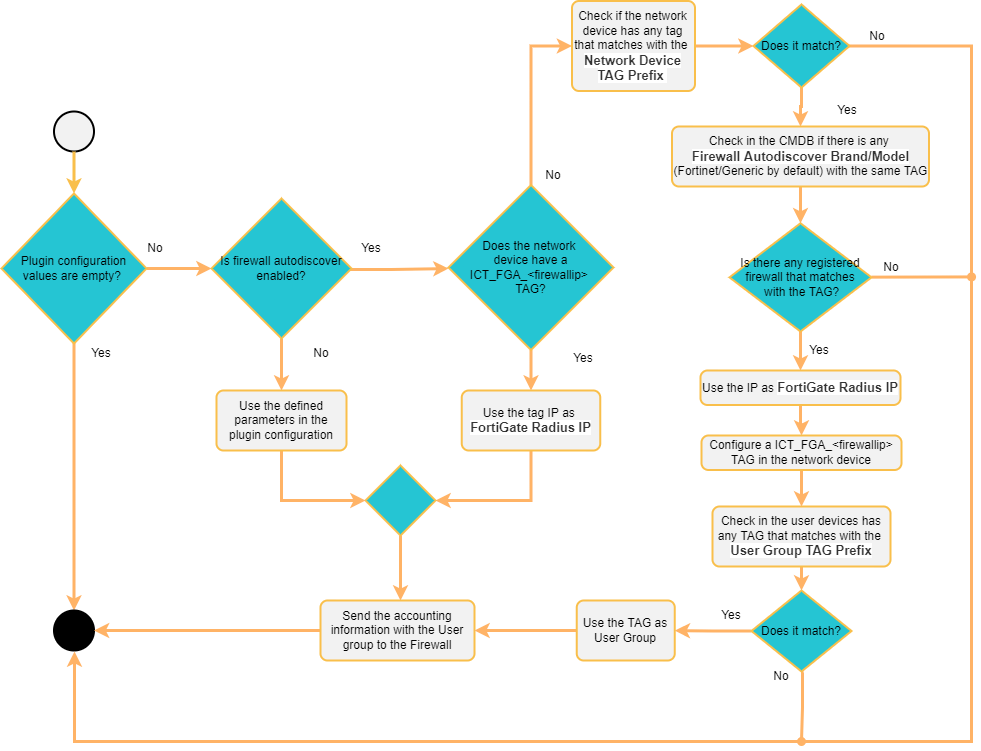
3.1.10.2.7.1. (Feature) fortiGateAccounting Firewall Autodiscover
The fortiGateAccounting plugin has the Firewall Autodiscover feature that allows you to dynamically relate which Fortinet Firewall is associated to a network device (firewall, switch, AP, etc.) that processes a user event.
When we enable this feature, the system will automatically look for the IP of the firewall that must process a new user event, for this, we must previously have all the network devices (firewall, switch, AP, etc.) registered in the CMDB with the tags correctly defined so that the system can make the association.
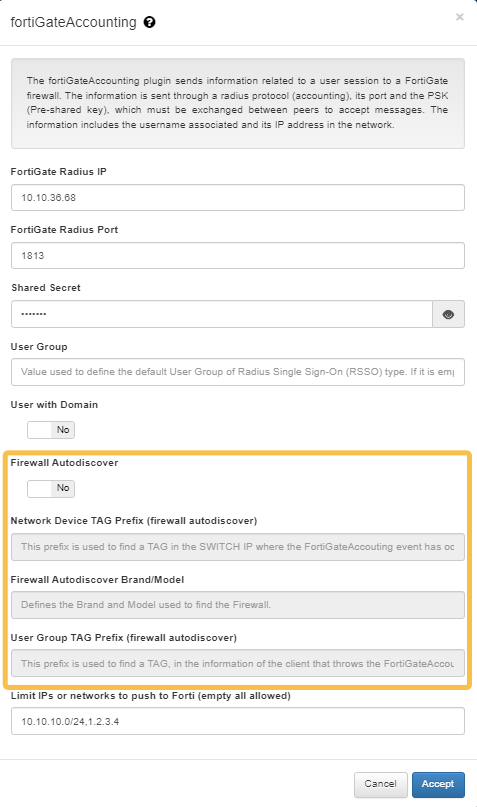
Firewall Autodiscover: This boolean enables the firewall auto-discover function and defines if the FortiGate Radius IP will be automatically filled in. If we enable this feature, the FortiGate Radius IP field will be ignored.
The Firewall Autodiscover flag must be enabled to configure the Network Device TAG Prefix, Firewall autodiscover Brand/Model, and UserGroup TAG prefix fields.
Network Device TAG Prefix (firewall autodiscover): TAG prefix that will be used to perform the association between the network device and the firewall associated.
Firewall autodiscover Brand/Model: Define which brand and model use to locate the firewall (which already has the “NetworkDevice TAG prefix”). Default Fortinet/Generic.
UserGroup TAG prefix (firewall autodiscover): TAG prefix that will be used as userGroup. If the user device in the new event contains a TAG that matches with the defined prefix, we will use it as userGroup (the userGroup must be previously defined on the Firewall).
Note
Network Device TAG Prefix and UserGroup TAG prefix should be unique. Consult the TAGS table.
For example, a new event in OpenNAC Enterprise executes the fortiGateAccounting plugin. This event will have a “switchIP” field with a network device associated. This network device is registered on the CMDB and it has some tags associated. Using the field “NetworkDevice TAG prefix” we can find a specific TAG in the network device. Once we find it, we will look for the different firewalls registered on the CMDB that match with the specified Brand/Model, and with the tag found on the network device. When the first Fortinet firewall matches these filters, its IP will be used as the ‘FortiGate Radius IP’, and we will send the information related to the event.
Once we have a match with a firewall and the switch, the system will store a TAG with the following format [ICT_FGA_{firewallIP} which means Internal Cache TAG _ FortiGate Accounting _ IP firewall] in the switch. That will indicate which FortiGate Radius IP is associated to the network device. This will help to speed up the process in future events since we will not need to repeat the search.
The “UserGroup TAG prefix” will be used to find a TAG inside the client tags. Once the TAG matches with the defined prefix, it will be used as userGroup and it will be send to the firewall.
Execution flow: