3.1.10.2.6. discover
This plugin uses the device’s IP address to gain visibility on them. Discover plugin executes NMAP and SNMPWalk commands over discover assets. The plugin discovers all the devices using SNMP protocol and tries to use the communities defined. It also uses plenty of different types of scans, TCP, UDP, ICMP, extract banners, and gets fingerprints over operating systems and services.
The discover plugin is also executed when the tag ONC_FORCE_DISCOVER_FULL is found on the device.
We can add the following parameters in the discover plugin.
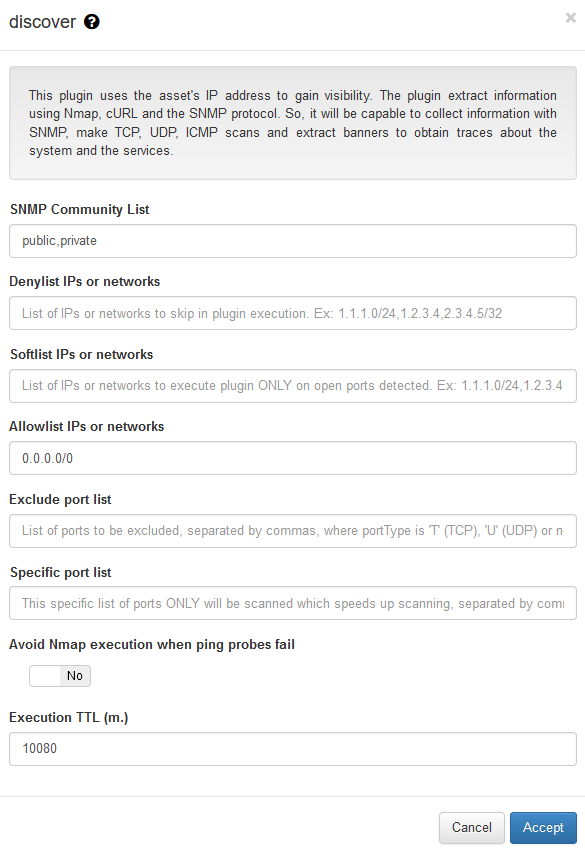
SNMP Community List: An IP range, or a set of comma-separated IP ranges that should be scanned by the plugin, if the received IP is included in the network lists, the plugin will execute. In case CIDR doesn’t appear will consider /32.
Denylist IPs or networks: An IP range, or a set of comma-separated IP ranges that should not be scanned by the plugin, if the received IP is included in the network lists, the plugin will NOT execute.
Softlist IPs or networks: An IP range, or a set of comma-separated IP ranges that should not be scanned by the plugin. If the received IP is included in the network list, the plugin just runs over the defined ports as open ports using Device Open Ports (DOP) and Passive Open Ports (POP) tags . For example using the network performance information collected by the Sensor. This functionality allows discovering “banners” in the known ports through a “soft” scan.
Allowlist IPs or networks: An IP range, or a set of comma-separated IP ranges that should be scanned by the plugin, if the received IP is included in the network lists, the plugin will execute. In case CIDR doesn’t appear will consider /32.
Example of an IP range for the three previous fields:
172.16.1.0/24 , 10.10.36.113/32, 1.2.3.4
Exclude Port List: ROS_LINUXist of ports to be excluded, separated by commas, where portType is ‘T’ (TCP), ‘U’ (UDP) o no portType for both.
Example of a port list:
-100,200-1024,T:3000-4000,U:60000-
Specific port list: This field allows for faster scanning by specifying a predefined list of ports to be scanned. If the user’s device IP address is defined in Softlist IPs or networks, the specific port list will not be executed. In such cases, the Exclude port list can still be executed if any ports are defined. In scenarios where Softlist IPs or networks, Exclude port list, and Specific port list options are empty, the plugin will perform scanning on the top 1000 TCP ports.
Example of port list ranges:
0-100, 200-1024, T:3000-4000, U:60000-
Invalid examples, including invalid ranges:
't' or 'u' values, or values greater than 65535 (e.g., t:22, T:80-22, U:65536).
Avoid NMAP execution when ping probes fail: If it is not marked, and there is no ping response, the NMAP is used with the -Pn option, to avoid NMAP execution if the ping fails.
Execution TTL (m.): During this period, indicated in minutes, no more executions are done over the same client.
Note
These fields can be empty. In this case, they don’t apply.
The following diagram shows the execution flow of the plugin:
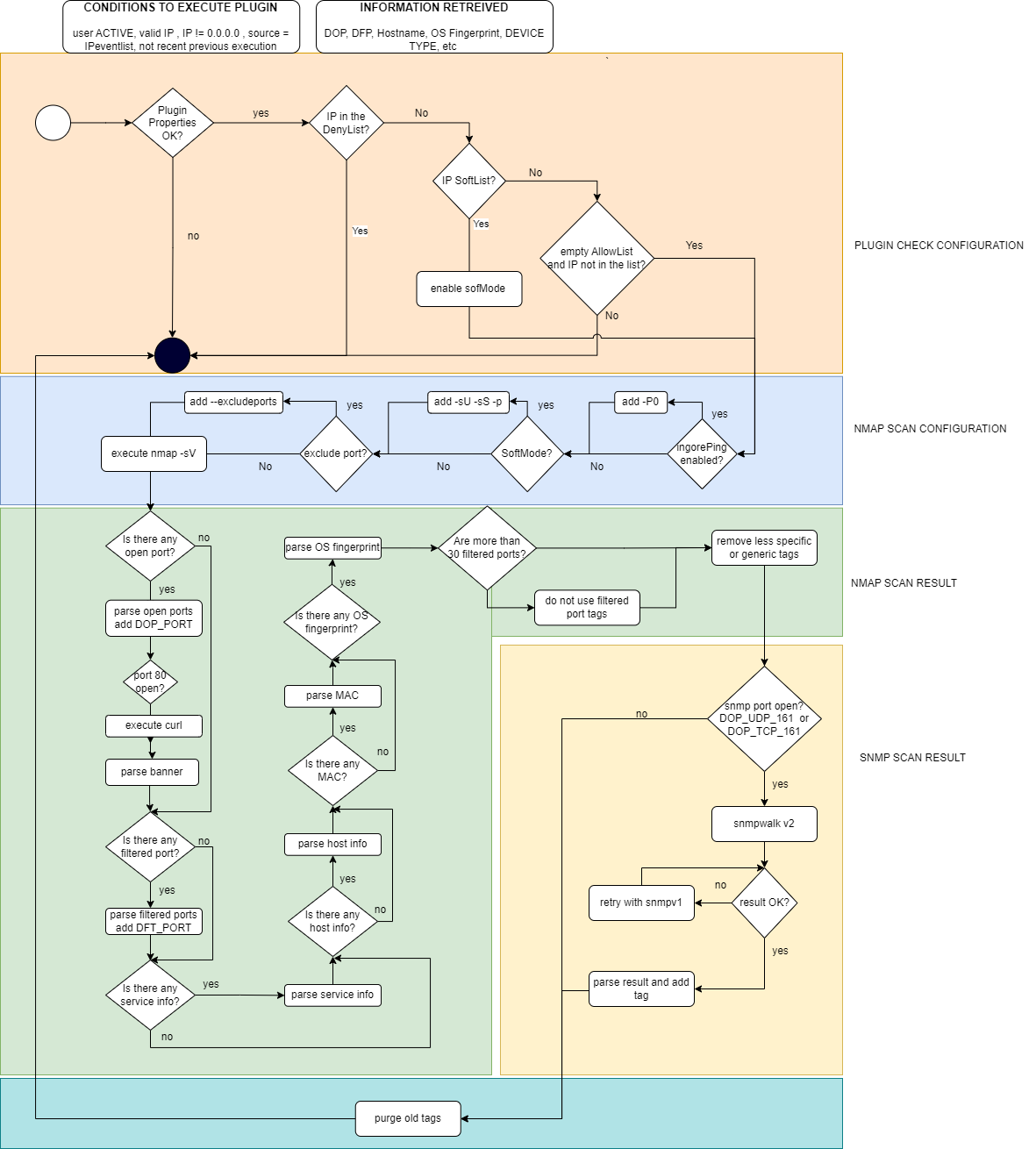
If the scanned output matches a defined encoded information (Banners, HTTP parsing and SNMP OID) and the tag to be added has parent tags in the profile tree, those parent tags will also be added. For instance, if the output matches “NETWORK_DEVICE_AP_CISCO,” it will automatically add “NETWORK_DEVICE_AP” and “NETWORK_DEVICE” tags as well.