3.1.10.4. OTP
A One-Time Password or OTP is an authorization code or dynamic password that can only be used one time. It is often used on login and it prevents several deficiencies associated with the traditional static login methods.
OpenNAC Enterprise offers the possibility to configure and manage OTPs to use this second authentication password when accessing to the VPN or the Administration portal itself.
You can manage all tasks related to OTP Network Access from the OTP section, which is divided into tabs:
OTP Admin Users
OTP Local Users
OTP External Users
OTP Policies
OTP configuration
This section allows the creation of OTPs using the same user ID but distinct repositories. Additionally, during user authentication, the system utilizes both the user ID and repository ID of the authenticated repository to verify OTPs.
3.1.10.4.1. OTP Admin Users
From the OTP Admin Users tab, you can manage the OTP configuration for admin role users:
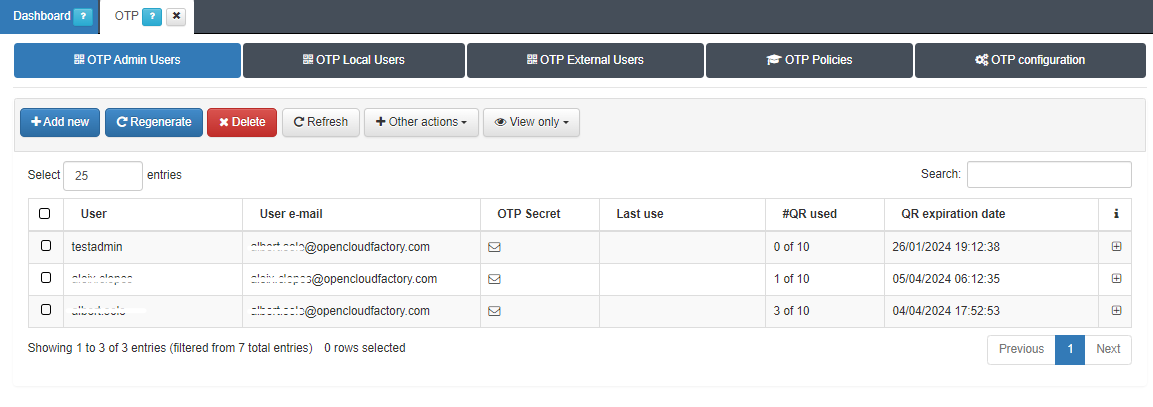
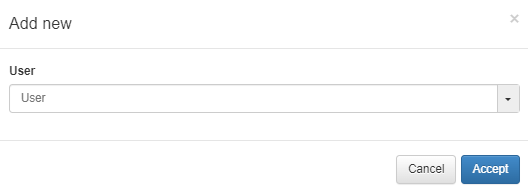
You can add new users by clicking on the Add new button and selecting the desired admin user.
3.1.10.4.2. OTP Local Users
From the OTP Local Users tab, you can manage the OTP configuration for local users:
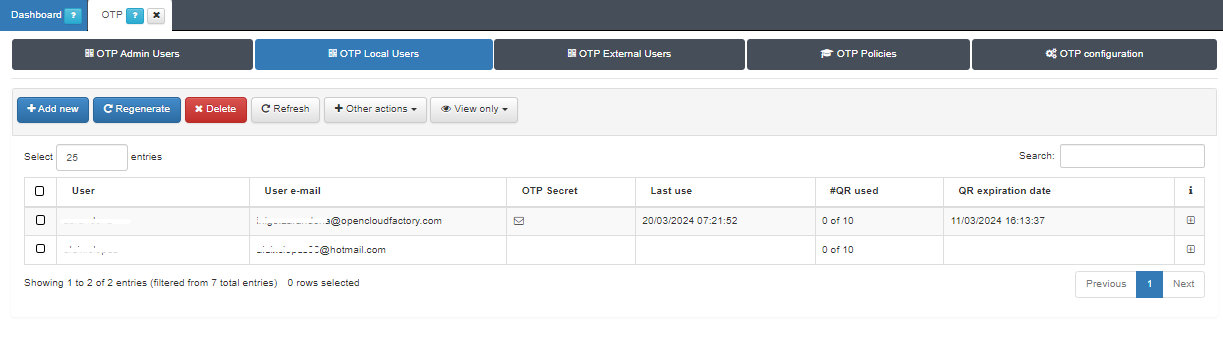
You can add new users by clicking on the Add new button and selecting the desired local user.

3.1.10.4.3. OTP External Users
From the OTP External Users tab, you can manage the OTP configuration for external users:
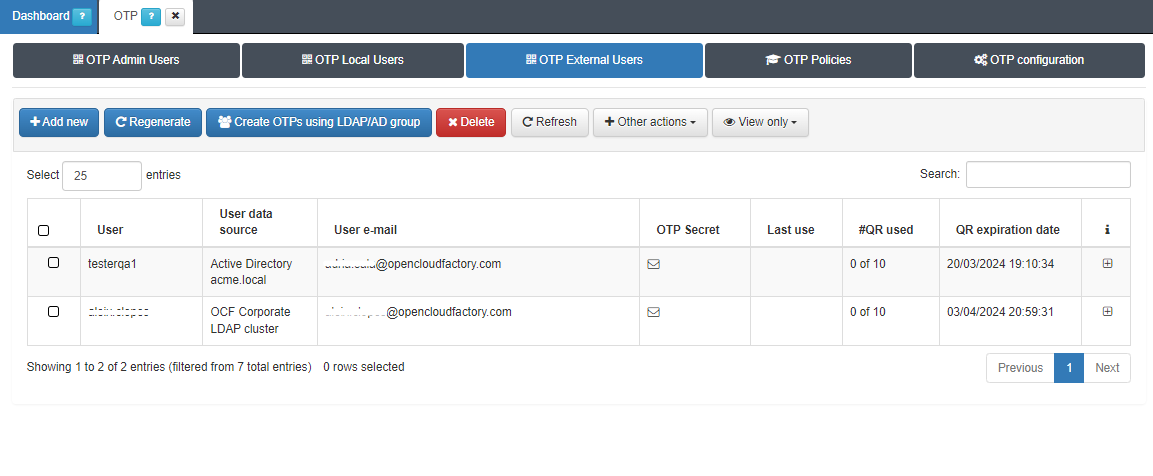
To add new users through the OTP Eternal Users tab, click the Add new button and enter the the desired username for the QR owner and select its User data source:

You can create a OTP for a user by selecting a group from an LDAP or AD by clicking on Create OTP using LDAP/AD group:
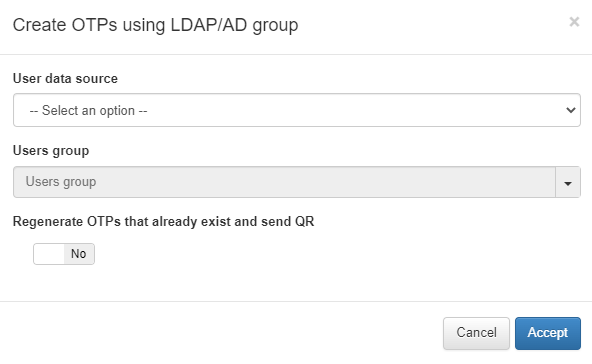
User data source: The LDAP or AD source we want to use.
Users group: The group of users that will be using the OTP.
Regenerate OTPs that already exist and send QR: Flag that allows to enable or disable the OTP regeneration if it already existed.
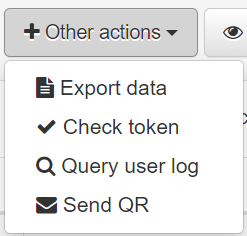
Contextual menu capabilities
You can Delete the selected OTP or Refresh the page.
When clicking on Other actions it will display the following drop-down menu:
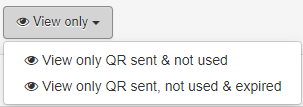
It is also possible to filter the entries by the QR that have been sent and not used, or sent not used and expired by clicking on View Only.
It is also possible to Search for a user and review its OTP parameters by clicking on the + icon.
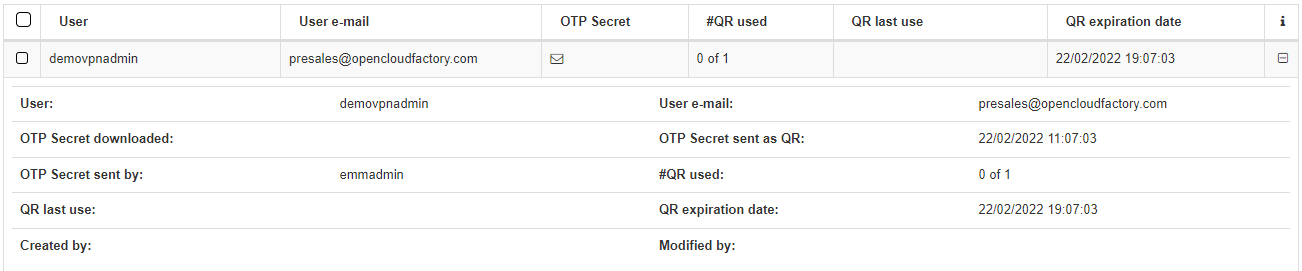
User: The owner of the QR.
User e-mail: The email where the QR has been sent.
OTP Secret downloaded: Boolean indicating whether the OTP has been downloaded or not.
OTP Secret sent as QR: Date and time indicating when the QR was sent.
OTP Secret sent by: The user that sent the QR.
#QR used: Number of times the QR was used.
QR last use: Date of the last use of the QR.
QR expiration date: Expiration date of the sent QR (in red if the QR has expired).
Created by: User who created the OTP.
Modified by: User who modified the OTP.
After creating a user or group OTP and sending the QR code, users can scan it with any authenticator app, such as Google Authenticator, which will generate a dynamic PIN for about 30 seconds.
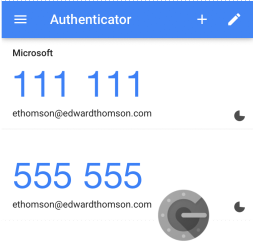
Users can then connect to the VPN by selecting 2FA in the authentication window, entering their username, password, and OTP PIN.
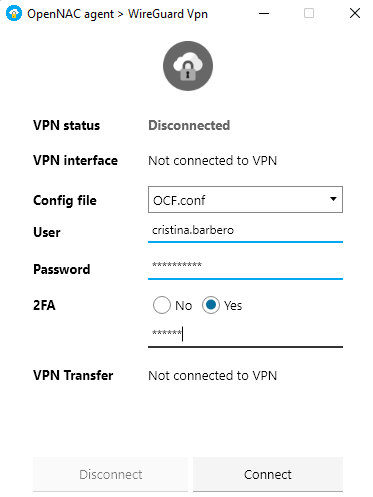
3.1.10.4.4. OTP Policies
From the OTP Policies tab, you can manage policies that must be met to request OTPs upon user authentication:
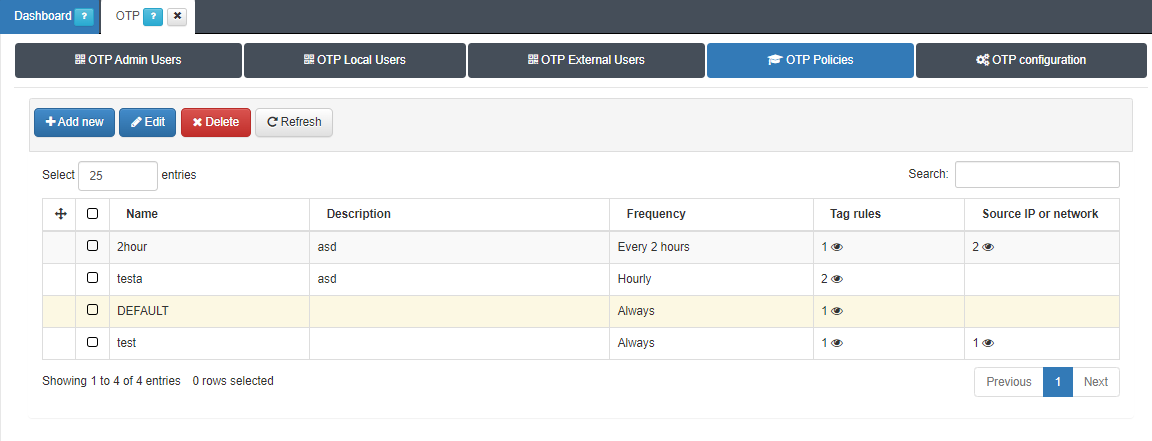
By clicking on Add new, you create create new policies:
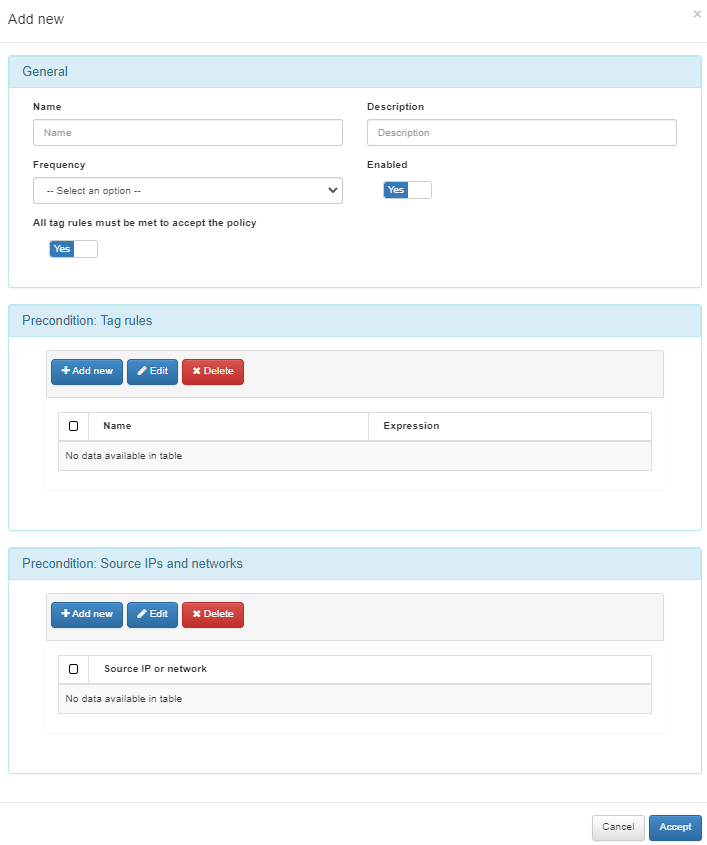
General
Name: Name of the new OTP policy.
Description: Description of the new policy for ease of identification.
Frequency: Frequency with which the OTP will be requested during a user’s authentication: always, hourly, every 2 hours, every 3 hours, every 4 hours, every 6 hours, every 8 hours, every 12 hours, daily, weekly, monthly, quarterly.
Enabled: Flag to enable the policy.
All tag rules must be met to accept the policy: If not enabled, only a single rule must be met to apply the policy.
Precondition: Tag rules
Click on Add new o add a new tag rule by configuring:
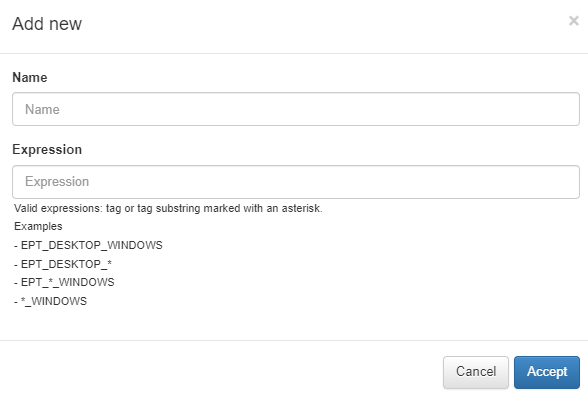
Rule name: Tag rule name.
Expression: Tag or tag substring marked with an asterisk. Examples: EPT_DESKTOP_WINDOWS, EPT_DESKTOP_*, EPT_*_WINDOWS, *_WINDOWS.
Precondition: Source IPs and networks
Click on Add new to add a source IP or network for the precondition:

3.1.10.4.4.1. OTP Policy Evaluation
Once the policy is created, if you want to check the policy evaluation, execute the following steps:
Connect to VPN using the Agent.
Enable the Verbose mode flag in Configuration > Configuration vars > Logs.
See the OTP policy evaluation by inspecting the opennac-api.log:
/var/log/opennac/opennac-api.log
If the user connects to the VPN and no OTP policy matches, the Default policy will be evaluated. If there is no condition configured, the user will always need to introduce the OTP code (Policy frequency applied: CHECK OTP).
Mar 21 13:05:45 onprincipal opennac-api[1209487]: 2024-03-21 13:05:45 DEBUG: [2c4e] [OtpPolicyMapper][user1][testa] Checking OTP policy...
Mar 21 13:05:45 onprincipal opennac-api[1209487]: 2024-03-21 13:05:45 DEBUG: [2c4e] [OtpPolicyMapper][user1][testa] OTP Policy tag rule NOT fullfilled: EPT_*_WINDOWS
Mar 21 13:05:45 onprincipal opennac-api[1209487]: 2024-03-21 13:05:45 DEBUG: [2c4e] [OtpPolicyMapper][user1][testa] OTP Policy tag rule fullfilled: ONC_AGENT
Mar 21 13:05:45 onprincipal opennac-api[1209487]: 2024-03-21 13:05:45 DEBUG: [2c4e] [OtpPolicyMapper][user1][testa] OTP Policy preconditions NOT fullfilled
Mar 21 13:05:45 onprincipal opennac-api[1209487]: 2024-03-21 13:05:45 DEBUG: [2c4e] [OtpPolicyMapper][user1][DEFAULT] Checking OTP policy...
Mar 21 13:05:45 onprincipal opennac-api[1209487]: 2024-03-21 13:05:45 DEBUG: [2c4e] [OtpPolicyMapper][user1][DEFAULT] OTP Policy tag rule NOT fullfilled: EPT_DESKTOP_WINDOWS
Mar 21 13:05:45 onprincipal opennac-api[1209487]: 2024-03-21 13:05:45 DEBUG: [2c4e] [OtpPolicyMapper][user1][DEFAULT] OTP Policy preconditions NOT fullfilled
Mar 21 13:05:45 onprincipal opennac-api[1209487]: 2024-03-21 13:05:45 DEBUG: [2c4e] [OtpPolicyMapper][user1][DEFAULT] OTP Policy frecuency applied: CHECK OTP
If the user connects for the first time and matches with a policy, this policy will evaluate the user device tags (either the last payload tags added or the ones obtained through tag rules, user device profiling, etc.).
At this point, the user will be prompted to enter the OTP (Policy frequency applied: CHECK OTP).
Mar 21 13:19:36 onprincipal opennac-api[1208860]: 2024-03-21 13:19:36 DEBUG: [3958] [OtpPolicyMapper][user1] Evaluating OTP policies...
Mar 21 13:19:36 onprincipal opennac-api[1208860]: 2024-03-21 13:19:36 DEBUG: [3958] [OtpPolicyMapper][user1][2hour] Checking OTP policy...
Mar 21 13:19:36 onprincipal opennac-api[1208860]: 2024-03-21 13:19:36 DEBUG: [3958] [OtpPolicyMapper][user1][2hour] OTP Policy tag rule NOT fullfilled: *_COMPLIANCE
Mar 21 13:19:36 onprincipal opennac-api[1208860]: 2024-03-21 13:19:36 DEBUG: [3958] [OtpPolicyMapper][user1][2hour] OTP Policy preconditions NOT fullfilled
Mar 21 13:19:36 onprincipal opennac-api[1208860]: 2024-03-21 13:19:36 DEBUG: [3958] [OtpPolicyMapper][user1][testa] Checking OTP policy...
Mar 21 13:19:36 onprincipal opennac-api[1208860]: 2024-03-21 13:19:36 DEBUG: [3958] [OtpPolicyMapper][user1][testa] OTP Policy tag rule NOT fullfilled: EPT_*_WINDOWS
Mar 21 13:19:36 onprincipal opennac-api[1208860]: 2024-03-21 13:19:36 DEBUG: [3958] [OtpPolicyMapper][user1][testa] OTP Policy tag rules precondition fullfilled.
Mar 21 13:19:36 onprincipal opennac-api[1208860]: 2024-03-21 13:19:36 DEBUG: [3958] [OtpPolicyMapper][user1][testa] OTP Policy frecuency applied: CHECK OTP
Mar 21 13:19:43 onprincipal opennac-api[1208861]: 2024-03-21 13:19:43 DEBUG: [a62f] [OtpPolicyMapper][user1] Evaluating OTP policies...
Mar 21 13:19:43 onprincipal opennac-api[1208861]: 2024-03-21 13:19:43 DEBUG: [a62f] [OtpPolicyMapper][user1][2hour] Checking OTP policy...
Mar 21 13:19:43 onprincipal opennac-api[1208861]: 2024-03-21 13:19:43 DEBUG: [a62f] [OtpPolicyMapper][user1][2hour] OTP Policy tag rule NOT fullfilled: *_COMPLIANCE
Mar 21 13:19:43 onprincipal opennac-api[1208861]: 2024-03-21 13:19:43 DEBUG: [a62f] [OtpPolicyMapper][user1][2hour] OTP Policy preconditions NOT fullfilled
Mar 21 13:19:43 onprincipal opennac-api[1208861]: 2024-03-21 13:19:43 DEBUG: [a62f] [OtpPolicyMapper][user1][testa] Checking OTP policy...
Mar 21 13:19:43 onprincipal opennac-api[1208861]: 2024-03-21 13:19:43 DEBUG: [a62f] [OtpPolicyMapper][user1][testa] OTP Policy tag rule NOT fullfilled: EPT_*_WINDOWS
Mar 21 13:19:43 onprincipal opennac-api[1208861]: 2024-03-21 13:19:43 DEBUG: [a62f] [OtpPolicyMapper][user1][testa] OTP Policy tag rules precondition fullfilled.
Mar 21 13:19:43 onprincipal opennac-api[1208861]: 2024-03-21 13:19:43 DEBUG: [a62f] [OtpPolicyMapper][user1][testa] OTP Policy frecuency applied: CHECK OTP
If the user have previously matched an OTP policy, the next time they connect to the VPN, the policies will match again. It will indicate that the OTP is not necessary until the frequency time determines that OTP usage is required again. (Policy frequency applied: IGNORE OTP).
Mar 21 13:25:29 onprincipal opennac-api[1208864]: 2024-03-21 13:25:29 DEBUG: [baef] [OtpPolicyMapper][user1] Evaluating OTP policies...
Mar 21 13:25:29 onprincipal opennac-api[1208864]: 2024-03-21 13:25:29 DEBUG: [baef] [OtpPolicyMapper][user1][2hour] Checking OTP policy...
Mar 21 13:25:29 onprincipal opennac-api[1208864]: 2024-03-21 13:25:29 DEBUG: [baef] [OtpPolicyMapper][user1][2hour] OTP Policy tag rule NOT fullfilled: *_COMPLIANCE
Mar 21 13:25:29 onprincipal opennac-api[1208864]: 2024-03-21 13:25:29 DEBUG: [baef] [OtpPolicyMapper][user1][2hour] OTP Policy preconditions NOT fullfilled
Mar 21 13:25:29 onprincipal opennac-api[1208864]: 2024-03-21 13:25:29 DEBUG: [baef] [OtpPolicyMapper][user1][testa] Checking OTP policy...
Mar 21 13:25:29 onprincipal opennac-api[1208864]: 2024-03-21 13:25:29 DEBUG: [baef] [OtpPolicyMapper][user1][testa] OTP Policy tag rule NOT fullfilled: EPT_*_WINDOWS
Mar 21 13:25:29 onprincipal opennac-api[1208864]: 2024-03-21 13:25:29 DEBUG: [baef] [OtpPolicyMapper][user1][testa] OTP Policy tag rules precondition fullfilled.
Mar 21 13:25:29 onprincipal opennac-api[1208864]: 2024-03-21 13:25:29 DEBUG: [baef] [OtpPolicyMapper][user1][testa] OTP Policy frecuency applied: IGNORE OTP
3.1.10.4.5. OTP Configuration
From the OTP Configuration tab, you can enable or disable sending QR One Time Passwords (OTP) Secrets by email:
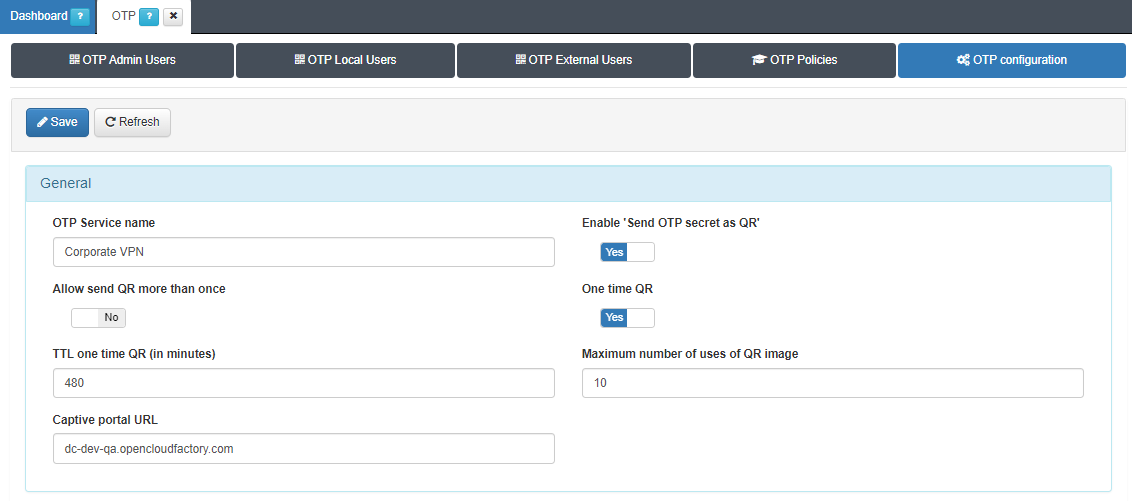
General
OTP Service name: Identification name for the OTP service.
Enable “Send OTP secret as QR”: Select “yes” so that the user will receive a QR code that they will use in Google Authenticator.
Allow to send QR more than once: By default, the QR Code can be sent only once (if you want to send another email you have to generate a new OTP secret). In case you want to reuse the same code, enable this field.
One time QR: If we enable one time QR mode, the QR will adopt the following parameters:
TTL one time QR (in minutes): Defines the time in minutes that it will take for a QR image to expire from when it is sent until it is scanned by the user. By default 480 minutes.
Maximum number of uses of QR image: Set the maximum number of scans of the same QR image.
Captive portal URL: Address for the unique QR.
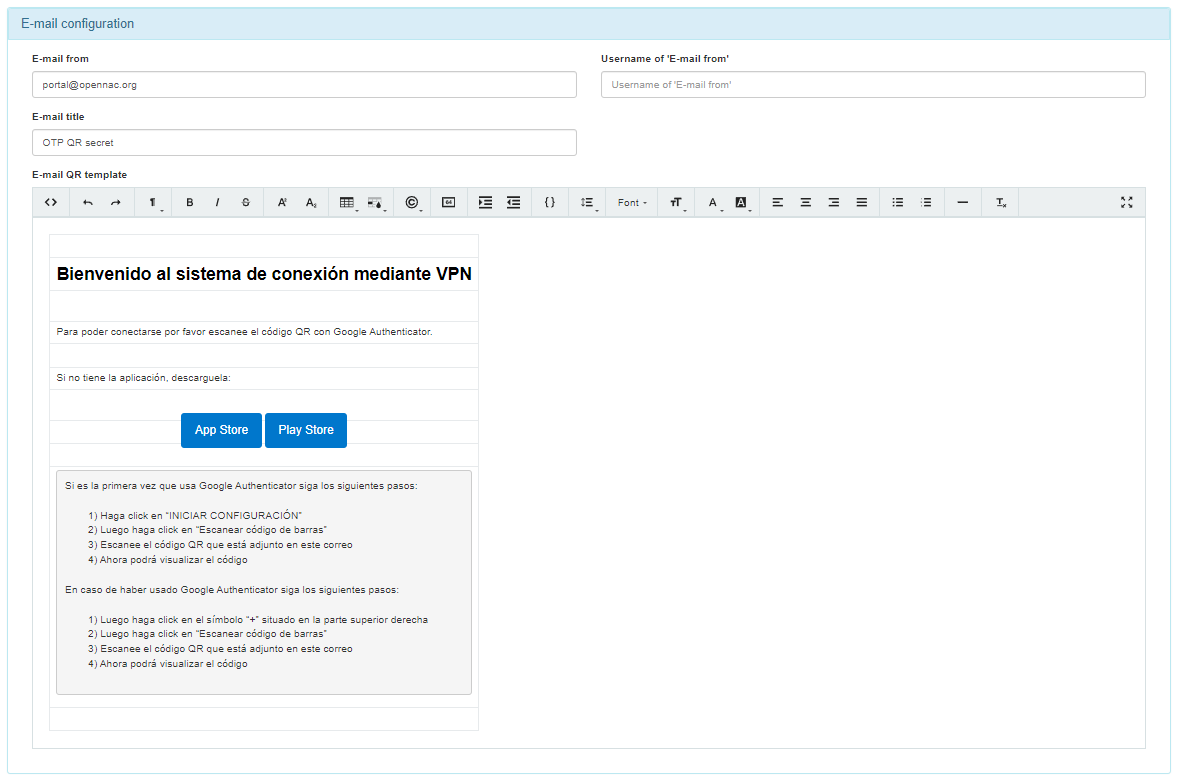
E-mail configuration
Email settings without one-time QR mode enabled.
Email from: Enter the e-mail address of the sender.
Username of ‘E-mail from’: Provide a descriptive name (e.g., the sender’s name or the organization’s name) instead of an email address, especially avoiding the same email address used in the “Email from:” field. This information is crucial to prevent potential rejection by mail relay servers due to anti-spam rules.
E-mail title: Enter subject of the email.
Email QR template: This section includes the HTML code that will be seen in the content of the email sent with the one time QR off mode.
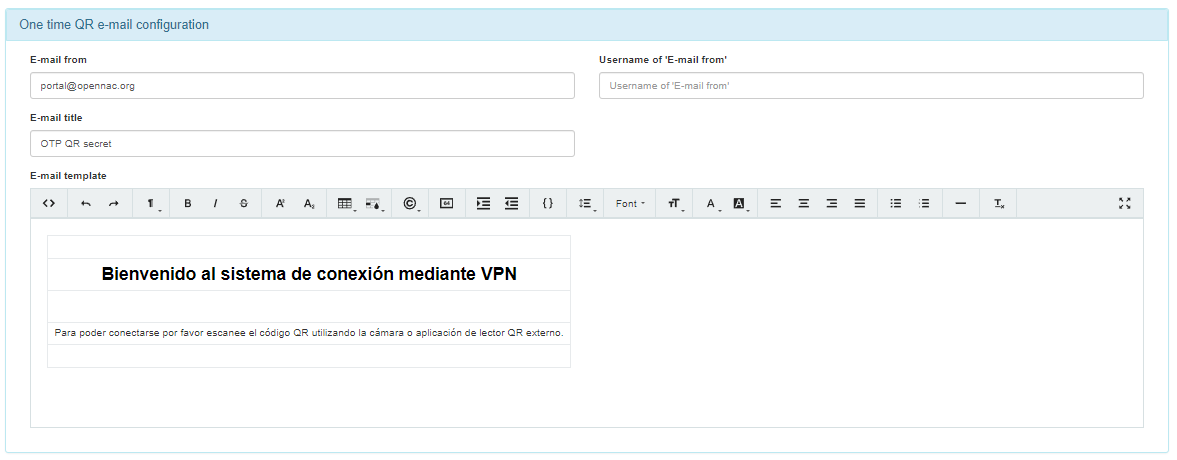
One time QR e-mail configuration
Email settings without the one-time QR mode enabled.
Email from: Enter the e-mail address of the sender.
Username of ‘E-mail from’: Provide a descriptive name (e.g., the sender’s name or the organization’s name) instead of an email address, especially avoiding the same email address used in the “Email from:” field. This information is crucial to prevent potential rejection by mail relay servers due to anti-spam rules.
E-mail title: Enter subject of the email.
Email QR template: This section includes the content that will be seen in the the email sent with the one time QR off mode.
Click on Save to apply the changes.