4.4.1.1. Introduction
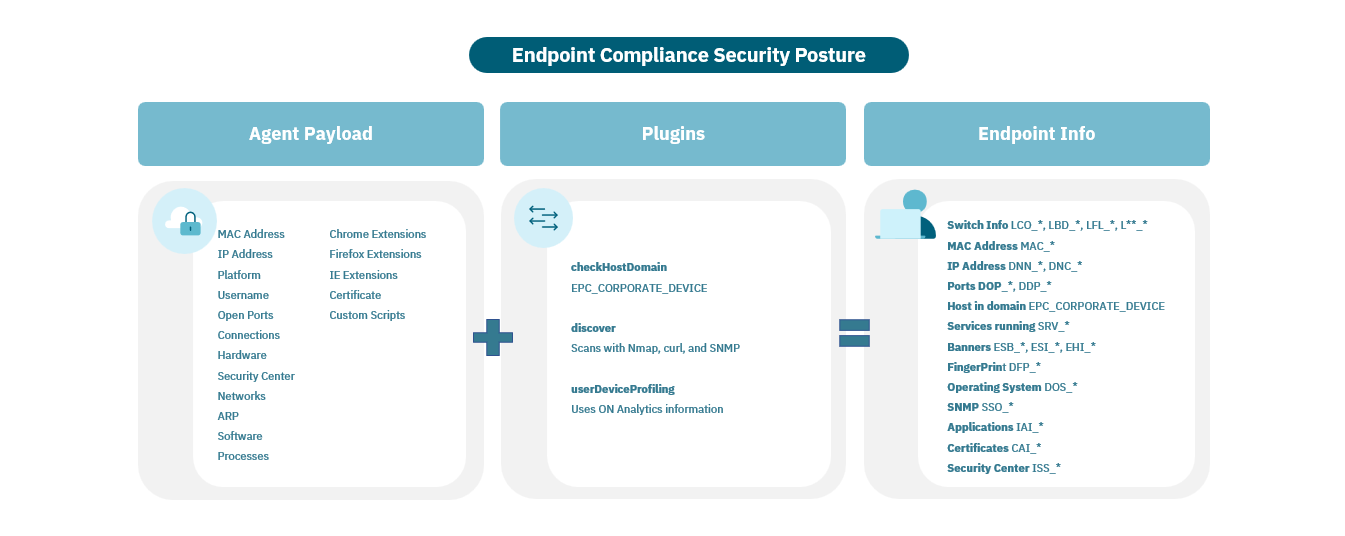
This EndPoint Compliance use case allows you to check on each endpoint device and the different parameters it has installed such as software, ON Agent, versions and updates, antivirus, specific software versions, etc. After identifying the value of a specific setting, users can create a tag and then use the tag as a precondition in the policy details.
Note
The Endpoint Compliance module relies on the UNAC module, meaning its functionality may depend on the configuration and performance of UNAC. The following section outlines the processes for implementing EndPoint Compliance. Therefore, it is essential to configure UNAC properly beforehand.
4.4.1.1.1. What does the Endpoint Compliance module provide?
Defining Security Requirements: Security requirements must be met to access the corporate network from any endpoint (EP). These include the presence of antivirus (AV), firewall (FW), specific operating systems (OS), and related software applications, among others.
Discover and Verify Compliance: Automatically discover EPs and ensure their compliance. Keep in mind that 99% of vulnerabilities exploited have been known for more than a year.
Respond and Enforce Security Measures: Having visibility into the network and a centralized decision point for enforcement is critical. This enables a global response to attacks, addressing issues immediately, automatically, and continuously. This includes actions such as isolation and remediation to effectively mitigate threats.
Response and Auditing: Demonstrate responses to security incidents and measure the effectiveness of security controls. This is essential for showing compliance with regulatory requirements and internal policies.
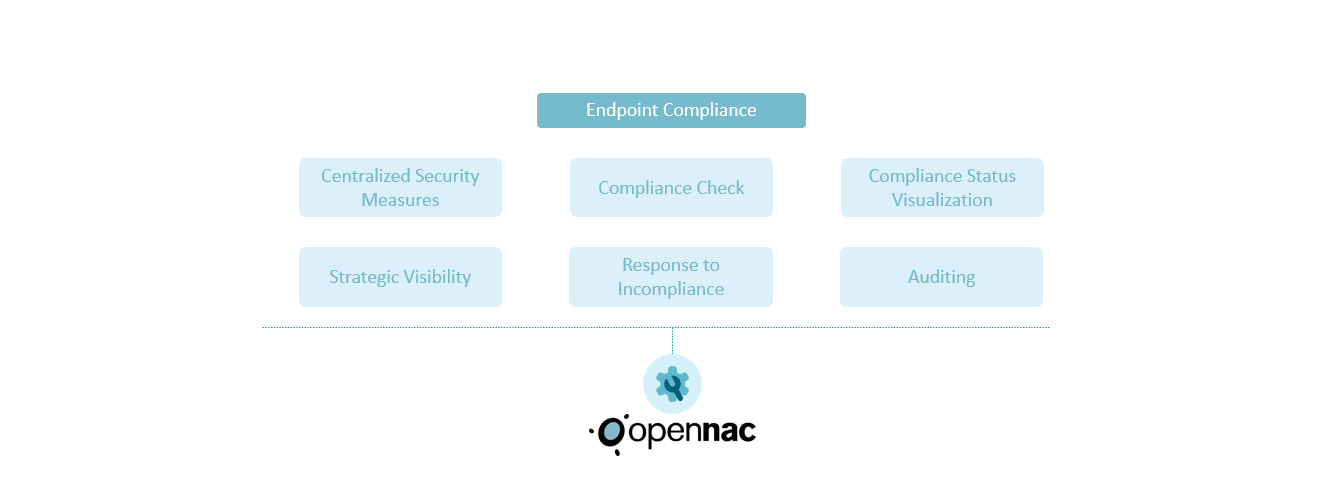
Strategic Visibility
When dealing with data centers and switches, gaining visibility into non-compliance is crucial for establishing an action plan regarding your equipment. Once a policy is defined, it undergoes verification against the infrastructure, encompassing endpoints, data centers, and network devices.
99% of the of exploited vulnerabilities have been known for over a year. By implementing a well-defined compliance policy, you can significantly reduce the risk of exposure and enhance the overall security posture of your system.
Response to incompliance
OpenNAC Enterprise centrally enables you to respond to any incompliance by establishing multiple enforcements, such as:
Blocking the endpoint
Isolating it to a remediation VLAN
Automatically sending automated self-help instructions to the end user to remediate the issues.
Downloading a patch, etc.
Visualize compliance status
You can access policies and compliance status reports through the respective dashboards. Additionally, you have the capability to generate reports that display the endpoint posture of your entire organization or drill down to specific criteria based on your requirements.
4.4.1.1.2. Security posture