3.1.9.3.1. Zones
The VPN Gateway serves as both a Layer 3 Firewall and a means to manage traffic flows within the VPN tunnel. The initial step involves identifying and configuring different zones within your network, which facilitates effective traffic management for the VPN. An example of network segmentation could be, Servers Zone, Servers DMZ, Corporate Firewall, and Frontend Firewall. include CMI architecture image updated
To ensure communication between the frontend and the zones of standard and critical servers, the traffic passes through the Corporate Firewall. As a result, these zones will be considered subzones of the previous zone. To achieve this configuration, you need to create these zones and subzones within the zone management section
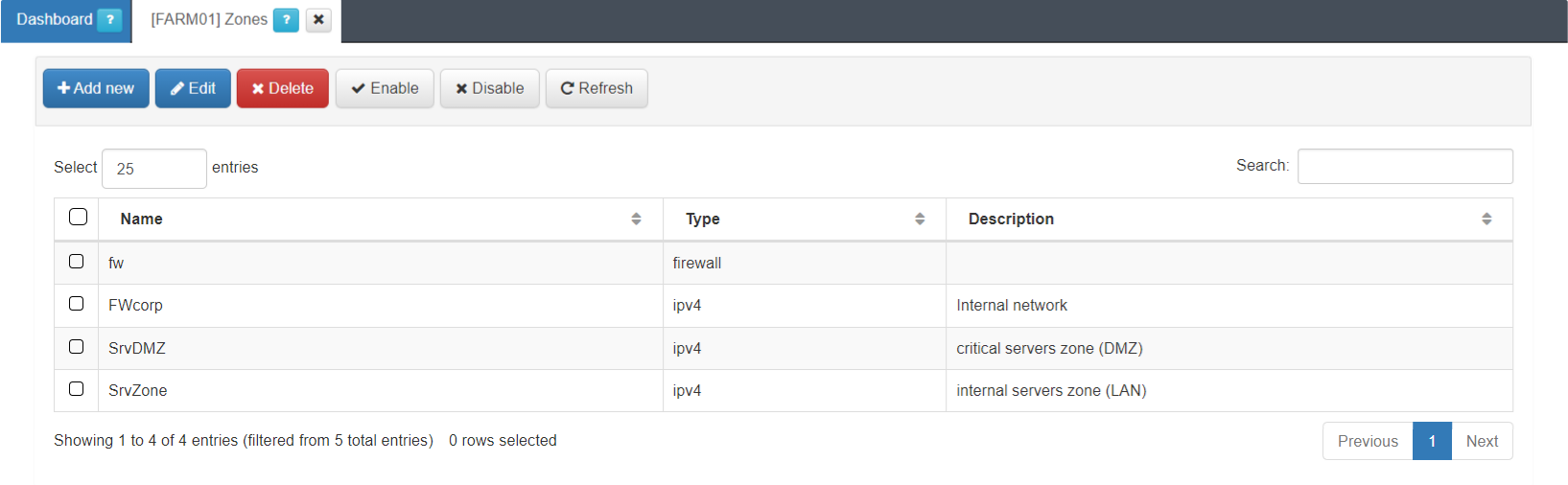
This view displays the zone name, its type and description.
The firewall (fw) zone itself is already created by default.
You can create the rest of zones by clicking on the Add new button. It will display the following configuration window:
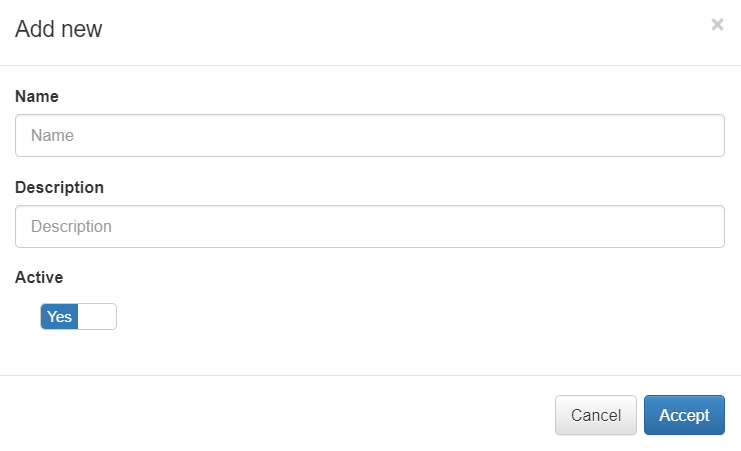
Name: The zone identification name must start with a letter followed by alphanumerical characters or underscore. It must have a maximum of 8 characters. Example: “FWCorp”
Description: Here you can add a Zone description.
Active: Flag to enable or disable the zone.
From this section, you can Enable and Disable a zone.
Note
By disabling a zone, all of its related objects and the related objects of its subzones will be disabled.
Similarly, enabling a zone will also enable its associated objects and those of its subzones.
After creating the zones, you need to assign them to a network interface (except for the default fw zone). See the next section for interface configuration.