3.1.8.1. Agent Profiles
A table with a list of agent objects is defined. These objects are defined with agent properties, and they are executed by the policies with postconditions. When a policy is matched and it’s configured with an agent profile as a postcondition, the agent profile inserts to the agent with the respective configuration in it.
If we click on the eye icon located in the Policies column, we will see the policies to which the agent profile applies.
By clicking on Add new, you will see the following properties needed to configure an agent profile:
3.1.8.1.1. General
In the following image we can see the fields displayed in the General module:
Name: Add the identification of the agent profile.
Description: Add a description of the Agent profile
Use as default profile: Set this agent profile as the default profile by enabling this flag.
Enabled: This flag is used to enable or disable the Agent profile.
3.1.8.1.2. Service configuration
In the following image, we can see the fields that we can find in the Service configuration module:
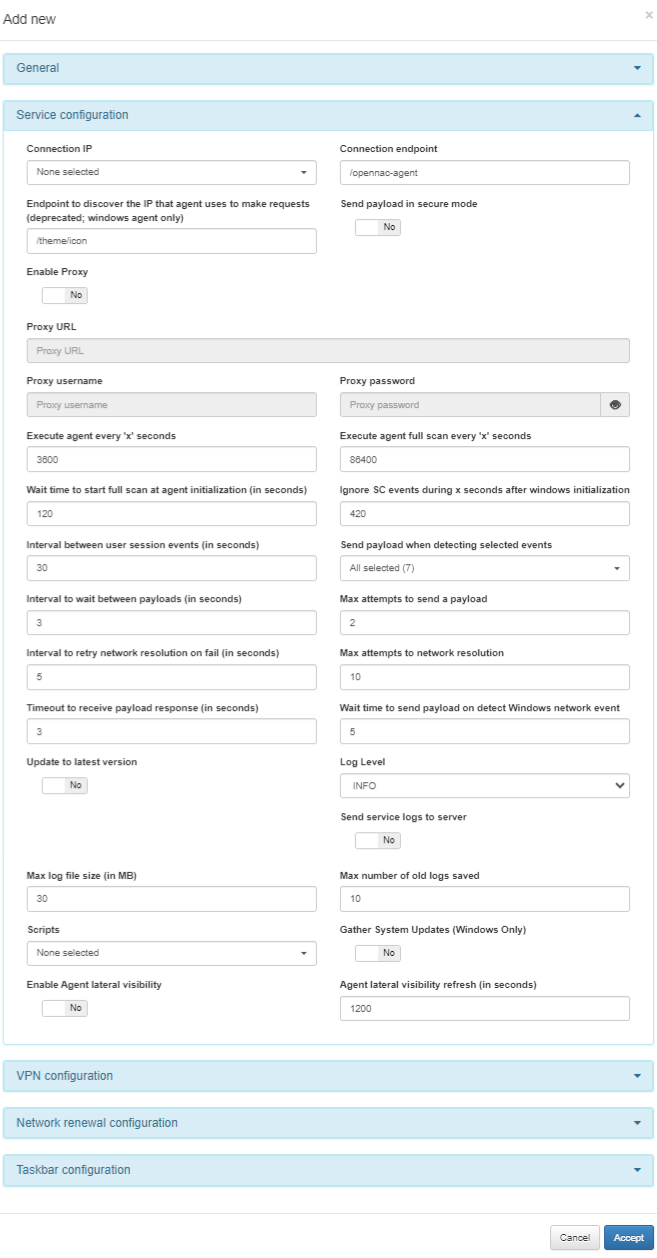
Connection IP: Dropdown menu containing a list of available connection IPs. These IPs should have been configured in the Agent Configuration > Download & Install agent options > Server list section beforehand for selection here.
Connection endpoint: By default, /opennac-agent
Endpoint to discover the IP that agent uses to make requests: By default, /admin/favicon.ico.
Send payload in secure mode: Flag to enable sending payloads in secure mode.
Enable proxy: Flag to enable Proxy.
Execute agent every ‘x’ seconds: You can change the agent execution time. The default time is 3600 seconds.
Execute full agent scan every ‘x’ seconds: You can change the agent scan frequency. By default, a full scan is done every 86400 seconds.
Wait time to start full scan at agent initialization (in seconds): When the Agent initializes, a scan is performed. It is possible to configure the time (in seconds) the scan runs after initializing the agent. The default value is 120 seconds.
Ignore SC events for x seconds after Windows initialization: When Windows starts, SC events are running and are not relevant to our agent. To avoid these events, SC sets a time to start listening to events. The default time is 420 seconds.
Interval between user session events (in seconds): You can change this interval. The default interval is 30 seconds.
Send payload when detecting selected events: You can enable or disable a type of payload generated automatically after an event. The types are: Software changed, Firewall changed, Security Center changed, Network changed, User session, Agent service stopped and Agent uninstalled.
Interval to wait between payloads (in seconds): You can change this interval value. The default interval is 3 seconds.
Max attempts to send a payload: You can change the max attempt value. By default, the number of attempts is 2.
Interval to retry network resolution on fail (in seconds): You can change the interval. The default interval is 5 seconds.
Max attempts to network resolution: You can change the max attempts value. The default number of attempts is 10.
Timeout to receive payload response (in seconds): You can change the timeout value. The default timeout is 3 seconds.
Wait time to send payload on detect Windows network event: You can change this wait time. The default time is 5 seconds.
Update to latest version: Allows the agent to update automatically.
Log level: Flag to change the service log level (TRACE, DEBUG, INFO, WARN,ERROR, FATAL, OFF). Its default value is INFO.
Max log file size (in MB): You can change the maximum size of the logs. The default max size is 30 MB.
Max number of old logs saved:You can change the number of days the logs will be stored. The default value is 10 days.
Scripts: Here you can see the objects created in ON Agent > Agent Scripts
Gather System Updates (Windows Only): Enables the execution of the System Updates Script, which gathers information about pending and installed updates on Windows operating systems. When the flag is enabled it will display the options: System Updates Check URL, System Updates Check URL Timeout, and System Updates Script Execution Timeout.
System Updates Check URL: URL to check if system updates information is available on the device. The agent has the URL configured in app settings, so the default value can be empty.
System Updates Check URL Timeout: Check URL timeout in seconds. The default value is 15.
System Updates Script Execution Timeout: Script execution timeout in seconds. The default value is 60.
Enable Agent lateral visibility: Enables/disables scanning of the network to which the device belongs. For this function to work, the network must be registered in the ON CMDB > Networks.
Agent lateral visibility refresh: Time interval between one scan of the network and the next scan of the network.
For more information about Agent functions, refer to:
Agent VPN
3.1.8.1.3. VPN configuration
In the following image, you can see the fields displayed in the VPN configuration module:
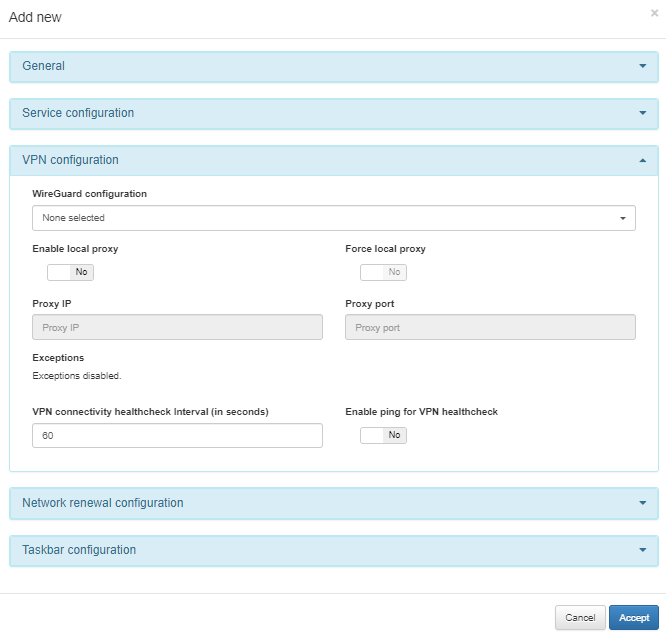
Within this module you can configure the following fields:
WireGuard configuration: You can create an WireGuard configuration file in ON Agent > Agent VPN > WireGuard.
Enable local proxy: Flag to enable local proxy, which will be applied when the agent connects to the VPN.
Force proxy: This flag enables the force proxy feature, which prevents the user from disabling the local proxy through the operating system configuration.
Proxy IP: You can change the Proxy IP in this field.
Proxy port: You can change the Proxy port in this field.
VPN connectivity healthcheck Interval (in seconds): Specifies the interval the system will check the WireGuard status and verify if it aligns with the VPN Agent’s reported status. Additionally, it checks for an active handshake between the client and the WireGuard server.
Note
Before enabling the following flag, ICMP packets must be allowed through the network.
Enable ping for VPN healthcheck: When enabled, this flag adds a ping test to the VPN connectivity healthcheck process, providing an additional layer of verification for the connection status.
3.1.8.1.4. Network renewal configuration
In the following image, we can see the fields displayed in the Network renewal configuration module:
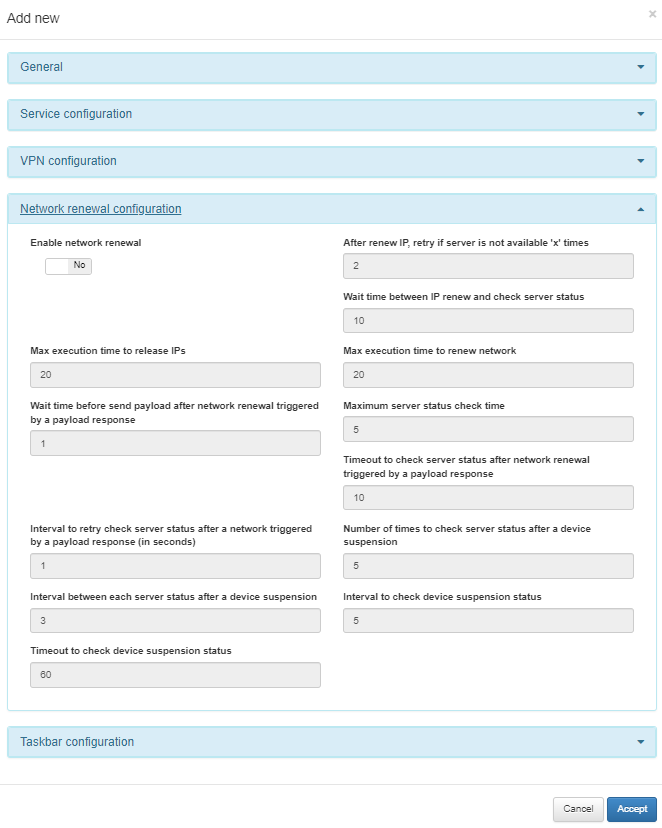
In this configuration section, we will define the behavior of the IP renewal service forced by the agent.
This service will force the IP renewal after OpenNAC Enterprise applies a VLAN change to the client that will be notified that it must make a new DHCP request.
This happens in environments where the Windows client does not detect that a VLAN change has been made at the switch layer, and therefore it no longer has connectivity.
The options available for configuring this service are:
Enable network renewal: This flag enables or disables the IP renewal service.
After renew IP, retry if server is not available ‘x’ times: When the service has been executed, the agent will try to reach the server X times to determine if it has obtained an IP from the new network.
Wait time between IP renew and check server status: Time that the agent will wait after the renewal of the IP to verify connectivity.
Max execution time to release IPs: Maximum execution time for the release of the previous IP.
Max execution time to renew network: Maximum execution time of the request for the new IP.
Wait time before send payload after network renewal triggered by a payload response: Time the agent will wait before sending a payload to the core after an IP renewal.
Maximum server status check time: Maximum time, measured in seconds, for checking the server status.
Timeout to check server status after network renewal triggered by a payload response: Maximum time to wait for server verification after an IP renewal.
Interval to retry check server status after a network triggered by a payload response (in seconds): Time interval to make the multiple checks of connectivity status with the server.
Number of times to check server status after a device suspension: Number of times to check connectivity with the ON Core server.
Interval between each server status after a device suspension: Time interval to make the multiple connectivity status checks with the server when a client suspension has occurred.
Interval to check device suspension status: Interval for checking a device in suspension (watchdog timer).
Timeout to check device suspension status: Maximum time to check the device’s suspension status.
3.1.8.1.5. Taskbar configuration
In the following image we can see the fields displayed in the Taskbar configuration module:
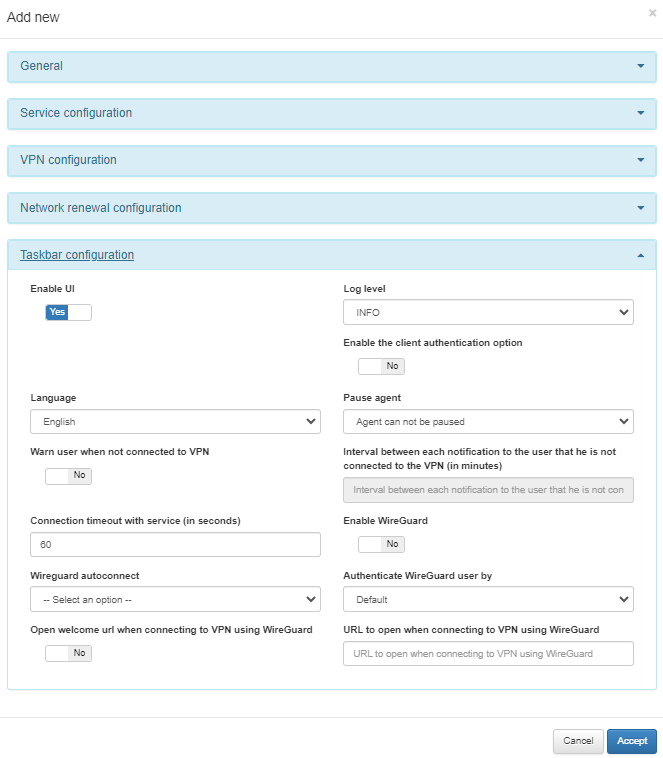
Enable UI: You can enable the User Interface of the agent.
Log level: Flag to change the UI log level (TRACE, DEBUG, INFO, WARN,ERROR, FATAL, OFF). Its default value is INFO.
Enable the client authentication option: Flag to enable client authentication.
Language: Select the agent’s language. The available languages are English, Spanish, catalan, French, and Portuguese.
Pause Agent: Select the pause Agent mode from three options:
Agent cannot be paused: Default option.
Pause agent manually: The taskbar will display this option to the user.
Autopause Agent if VPN is down: Pause the Agent while the VPN is down option.
Warn user when not connected to VPN: Flag to enable a VPN disconnection warning.
Interval between each notification to the user that he is not connected to the VPN (in minutes): Define the warning interval in minutes.
Connection timeout with service (in seconds):Field that determines the maximum time (in seconds) the agent UI waits for responses from the agent service.
Enable WireGuard: You can enable WireGuard.
Wireguard autoconnect: You can select different options regarding the VPN connections.
Defined by user: When connecting to the VPN, users will have the option to enable or disable the autoconnect feature according to their preferences.
Enabled by default: Autoconnect is enabled by default in the Agent, but can be disabled by the user when connecting to the VPN.
Disabled by default: Autoconnect is disabled by default in the Agent, but can be disabled by the user when connecting to the VPN.
Force autoconnect: Autoconnect is enabled by default and cannot be disabled by the user. Automatic login is also available when the user recovers from a lost connection, at session start, and when the device recovers from suspension or hibernation.
Authenticate WireGuard user by: depending on the option selected, different fields will be displayed.
SAML: Allow WireGuard authentication using SAML will display the field Timeout to authenticate VPN using SML (in minutes). This timeout represents the maximum time between ‘User click Connect VPN button’ and ‘User click on .nac file downloaded in browser’. If we don’t receive the .nac click action before the timeout configured has passed, the UI should display an error.
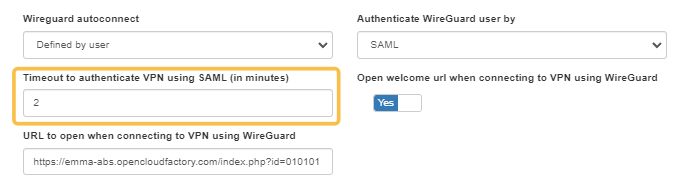
OAuth 2.0: Allow WireGuard authentication using OAuth 2.0 will display the Timeout to authenticate VPN using OAuth 2.0 (in minutes) and OAuth 2.0 configuration fields. The timeout represents the maximum time between ‘User click Connect VPN button’ and ‘User click on .nac file downloaded in browser’. If we don’t receive the .nac click action before the timeout configured has passed, the UI should display an error. See the OAuth 2.0 Integration section for more information about this standard.
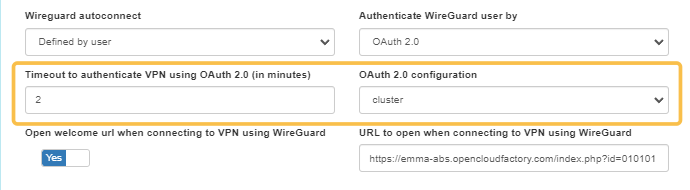
Open welcome url when connecting to VPN using WireGuard option, and the URL can be set in the URL to open when connecting to VPN using WireGuard fields.
1- Defined by user: the autoconnect will be the one that defines the user, so the user will select if they want to enable the autoconnect option when they connect to the VPN.
2- Autoconnect by default: the default autoconnect flag in the agent will always be true, and when connecting the user can disable the flag (if desired).
3- Not autoconnect by default: same as option 2, but with autoconnect flag set to false by default.
4- Force autoconnect option: the autoconnect will always be true by default, the checkbox is disabled, the user will not be able to uncheck it, and will also not be able to disconnect from the VPN, disable/fake the disconnect button.
In addition to the enabled autoconnect functionality, we will be able to login automatically in different scenarios:
When the user recovers after losing connection
When the session starts
When a device recovers after being in a state of suspension or hibernation