3.1.9.2.4. Server certificates
This section will show you how to generate a VPN server certificate using the CA.
Once the CA is created, we can use it to create new certificates.
Generate a new CSR (new certificate request) and return to the same directory where the CA was generated and execute the following request:
./easyrsa gen-req VPN_EMMA_RW_SRV nopass
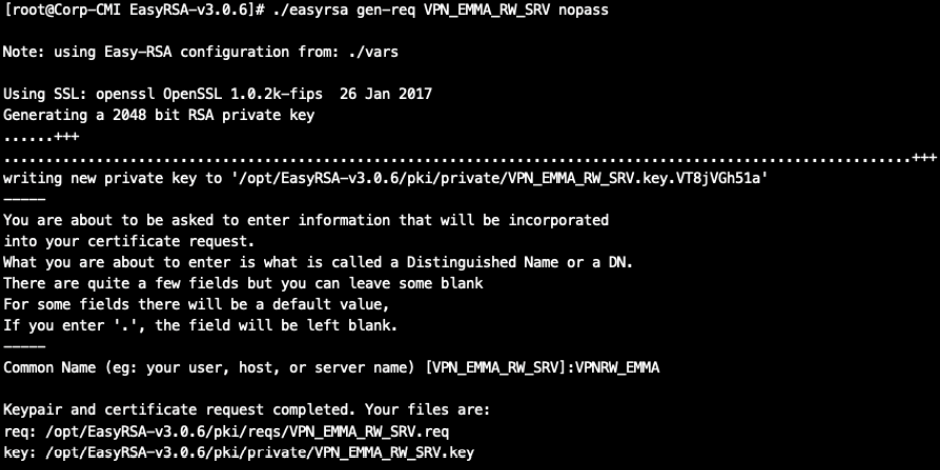
We will sign this request with our CA. For this, we will need the password used in the section “Generating a CA”:
./easyrsa sign-req server VPN_EMMA_RW_SRV
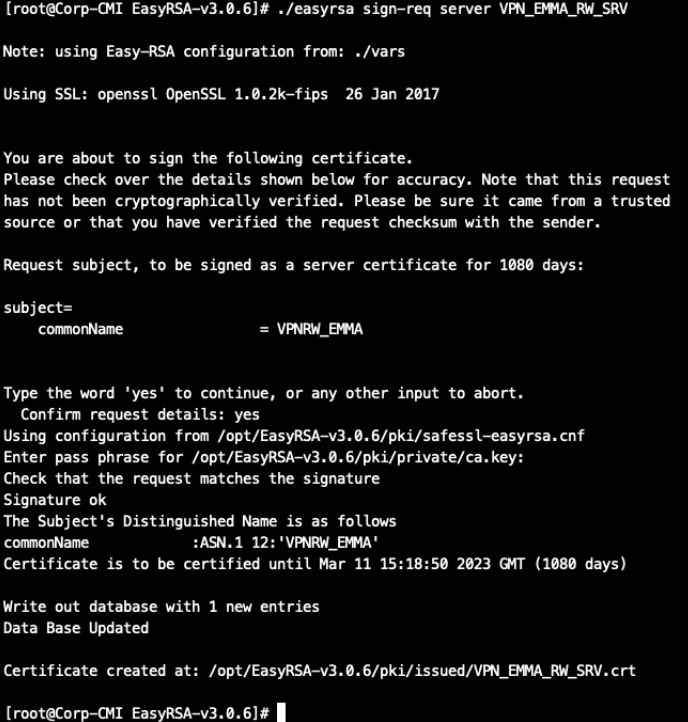
It will generate two files:
The certificate file: /opt/EasyRSA-v3.0.6/pki/issued/VPN_EMMA_RW_SRV.crt
The private key: /opt/EasyRSA-v3.0.6/pki/private/VPN_EMMA_RW_SRV.key
Copy both files to upload them to the Server Certificates section in the VPNG CMDB.
3.1.9.2.4.1. Registering the Server Certificate in the CMDB
Once the server certificate has been created, you must register it in the backend so that it is available and can be used in the VPNGW.
For that, we go back to the Administration Portal > VPNGW > CMDB > Server certificates
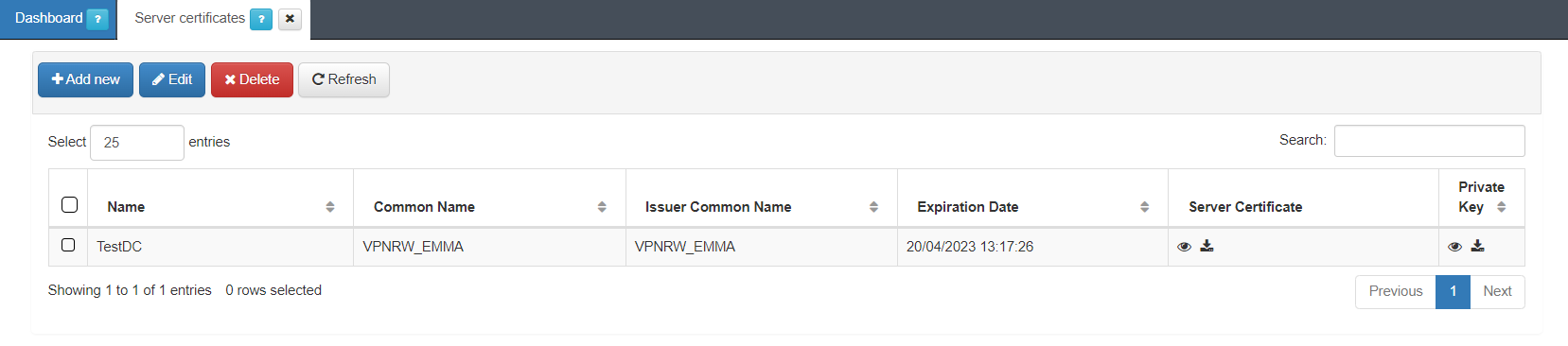
Click on the Add new button, and it will display the following window:
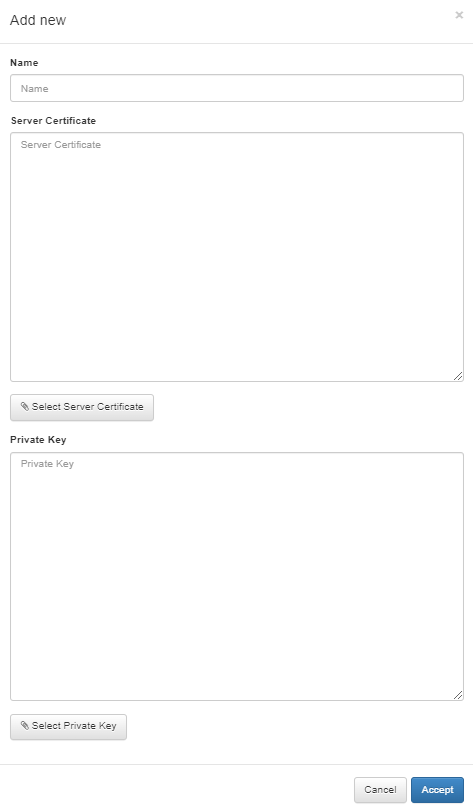
Name: Server certificate name.
Server Certificate: Copy and paste the certificate in this field or click on the Select Server Certificate button to upload the certificate file.
Private Key: Copy and paste the private key in this field or click on the Select Private Key button to upload the private key file.
Click on Accept to load the Server Certificate and the Private Key.