1.4.6. Guest Management
The Guest module enables external users to authenticate into the corporate network using their own devices.
This setup allows third parties to connect efficiently while keeping the corporate network secure. It ensures that all devices meet security requirements and regulations.
1.4.6.1. Guest in 4 Steps
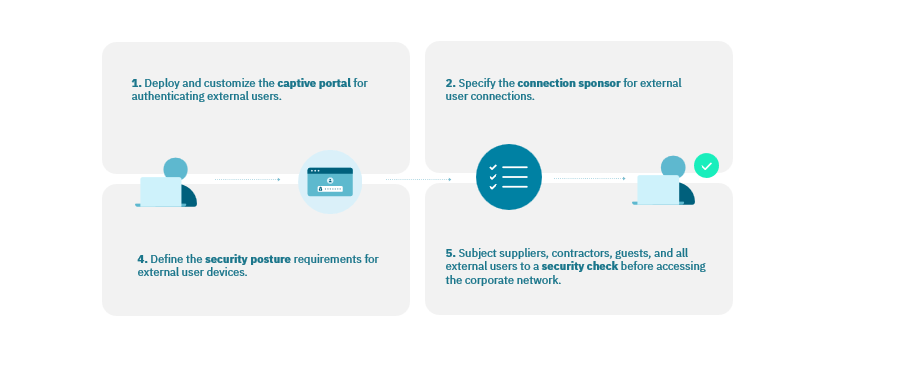
1.4.6.2. Guest Features
Adaptive security: Dynamically adapts your network to changing demands and the access permissions of numerous guest users. This way you can modify the access rights of multiple guest users.
Regulatory compliance (GDPR): Defines the security baseline required for access to the corporate network from any device (AV, FW, OS, etc.). Guaranteeing that partners and contractors comply with security criteria.
Customized workflow: Add other steps to the sign-in process (internal sponsor, IT personnel confirmation …) and customize the captive portal for authentication.
Reduced workload: Free up the IT department by automating the sign-in process with a customizable captive portal.
1.4.6.3. Guest Scenarios
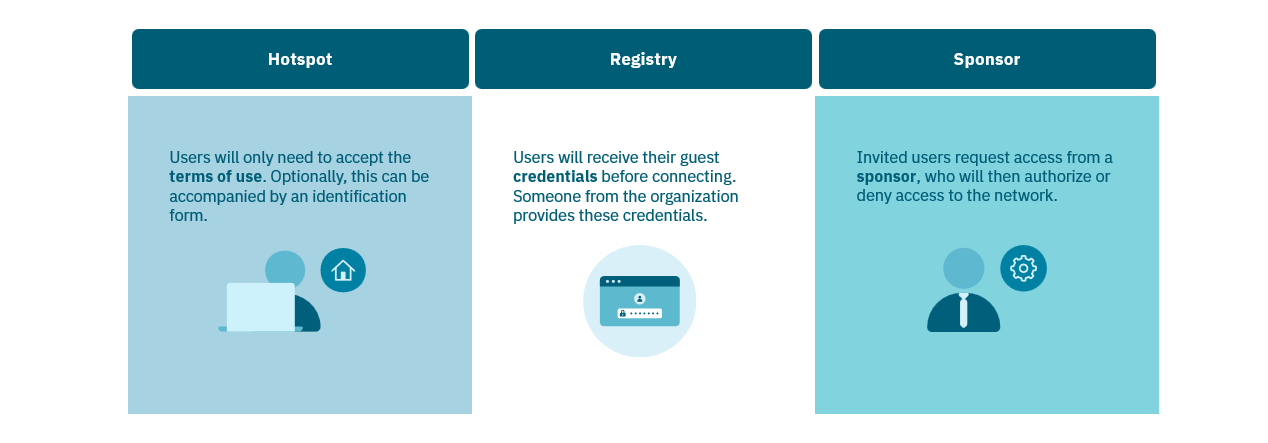
1.4.6.3.1. Hotspot
The user enters the Captive Portal and connects to an “open” network, where the only requirement for access is the acceptance of the terms of use.
Optionally, guests must fill out an access form, providing minimum identification data such as name, position, company, etc.
This option offers very open access, providing quick connectivity without identity control. The form data is not subject to validation and can be customized.
Requirements
Guest network propagation
Flow configuration
Identification form definition
Terms of Use
1.4.6.3.2. Registry
The guest user enters the Captive Portal and logs in with a username and password that were previously provided.
The provisioner in the organization is responsible for creating these identities in the Administration Portal. It is possible to send the credentials directly to the guest’s external email and auto-generate the password.
Requirements
Guest network propagation
Flow configuration
Identity provisioning and distribution mechanism definition
terms of Use
1.4.6.3.3. Sponsor
The guest user enters the Captive Portal and fills out an identification form, which is then sent to a sponsor.
Although the identification form does not perform authentication, the sponsor receives the guest’s access request via email and decides whether to allow or deny access to the network.
Requirements
Guest network propagation
Flow configuration
Identification form definition
Terms of Use
Sponsor definition
Additionally, the Sponsor scenario can add another layer to its authentication, to establish a compliant connection by adding the Soluble Agent download to the connection flow.
The Agent will provide full visibility by scanning the device and sending a payload to OpenNAC Enterprise.