1.4.7. 2SRA
2SRA **is the solution that **provides secure access to corporate networks, effectively mitigating the risks of identity theft. You can configure up to five security controls for remote access to corporate resources. Furthermore, OpenNAC Enterprise simplifies the adoption of standards and frameworks such as ISO2700x, NIST, ENS, etc.
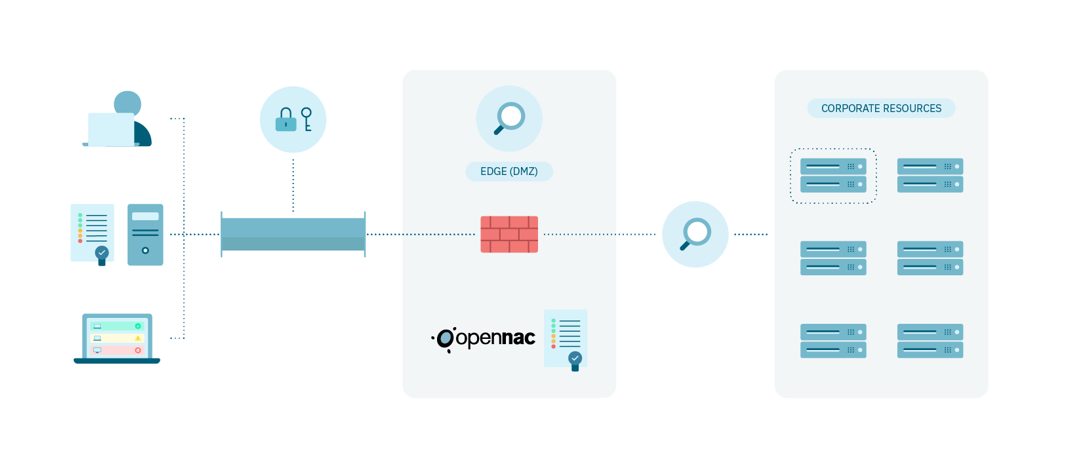
1.4.7.1. 2SRA Benefits
Principle of least privilege: Just users have access to the information and resources essential for the performance of their activity.
Zero Trust approach: Establishes a corporate security framework in which only authenticated and authorized users and devices can access corporate information.
Controls for attack surface: Secures remote connection through encryption and user devices.
Mitigate the risk of identity theft: Adds an extra layer of security by applying two-factor authentication (OTP) to reduce the risk of identity theft.
Reduces the risk associated with the user device: Allows the evaluation of device posture, establishing compliance with the minimum connection requirements when accessing the network.
1.4.7.2. Authentication and Authorization provided by OpenNAC
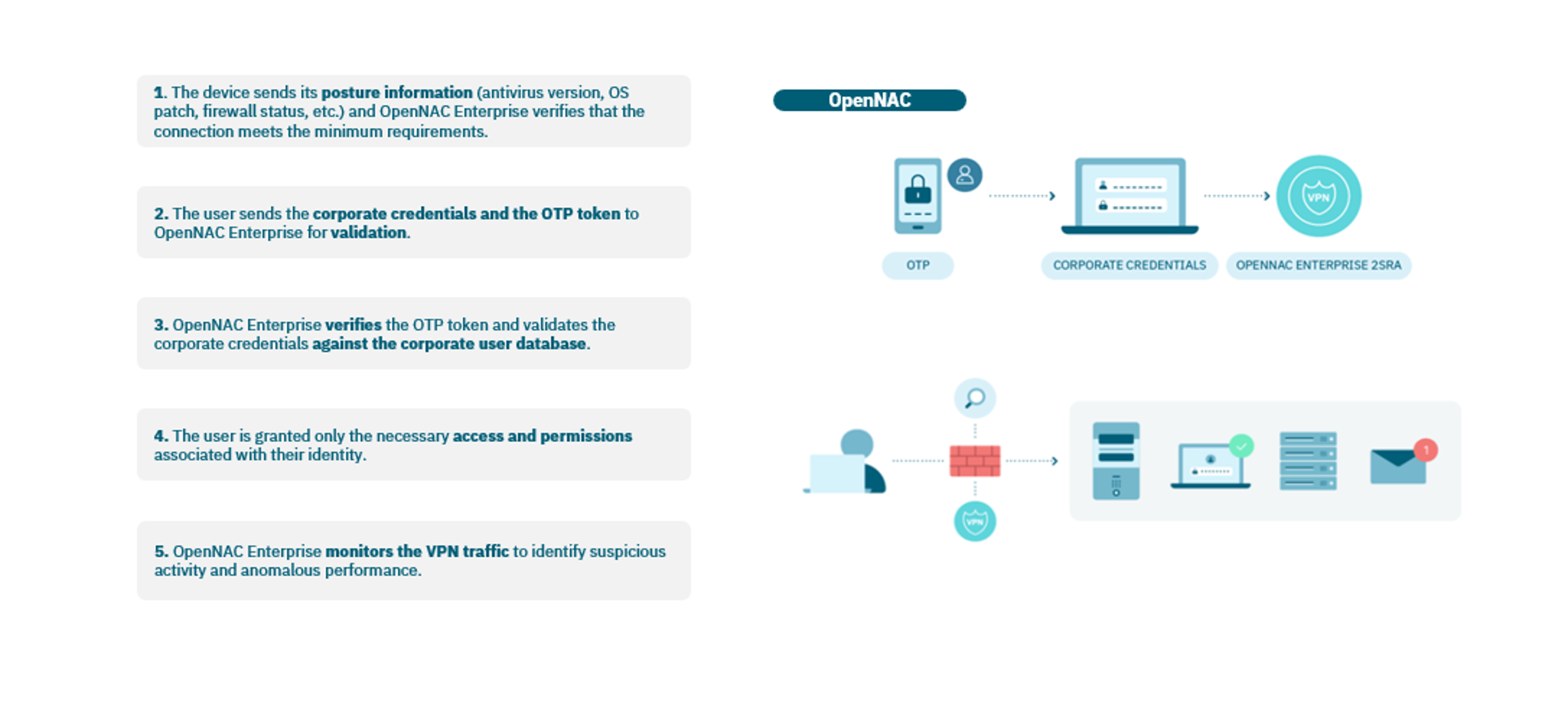
1 |
The device sends its posture information (antivirus version, OS patch, firewall status, etc.) and OpenNAC Enterprise verifies that the connection meets the minimum requirements. |
2 |
The user sends the corporate credentials and the OTP token to OpenNAC Enterprise for validation. |
3 |
OpenNAC Enterprise verifies the OTP token and validates the corporate credentials against the corporate user database. |
4 |
The user is granted only the necessary access and permissions associated with their identity. |
5 |
OpenNAC Enterprise monitors the VPN traffic to identify suspicious activity and anomalous performance. |
1.4.7.3. Authentication and Authorization provided by SAML
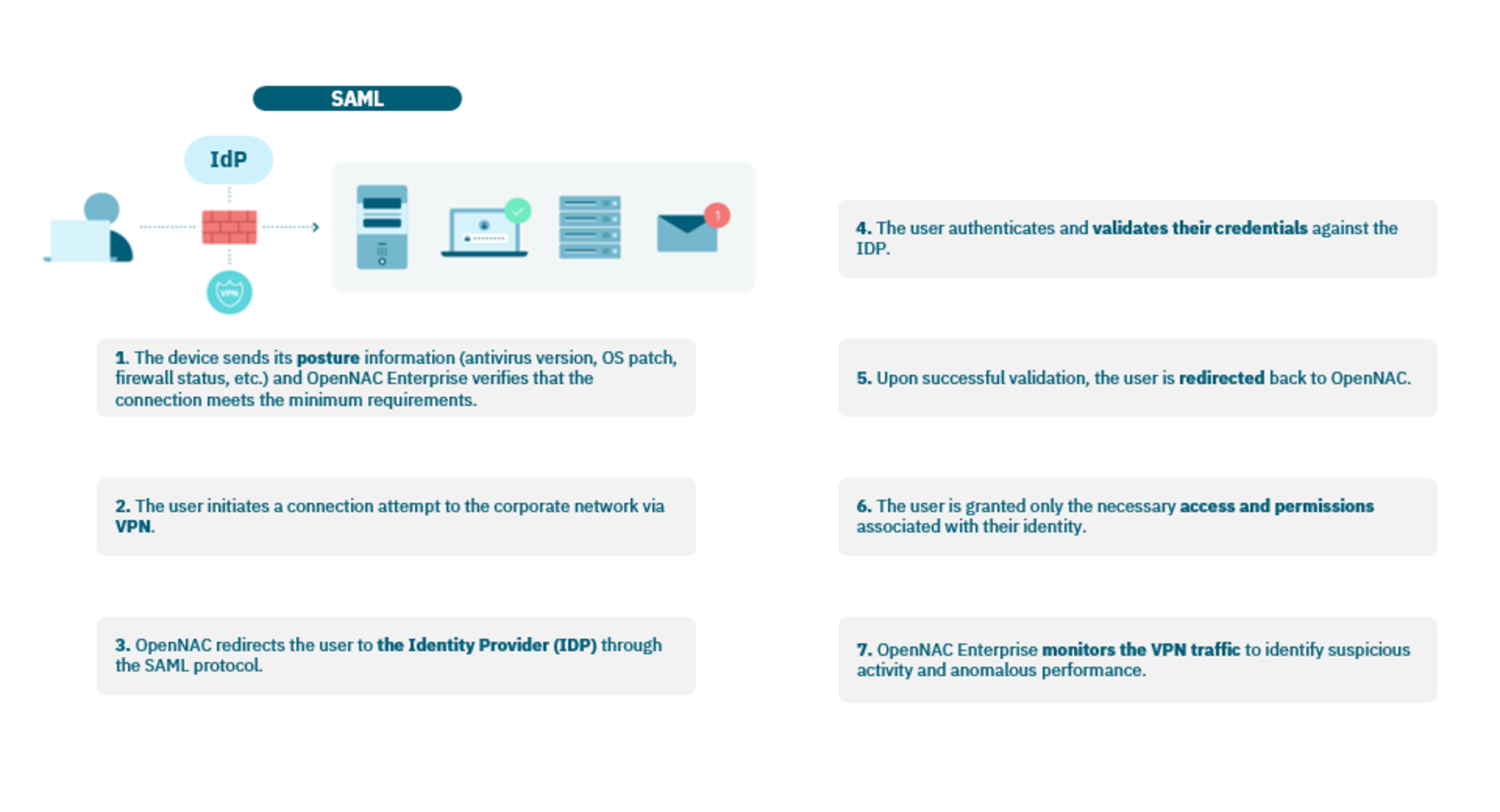
1 |
The device sends its posture information (antivirus version, OS patch, firewall status, etc.) and OpenNAC Enterprise verifies that the connection meets the minimum requirements. |
2 |
The usr initiates a connection attempt to the corporate network via VPN. |
3 |
OpenNAC Enterprise redirects the user to the Identity Provider (IdP) through the SAML protocol. |
4 |
The user authenticates and validates their credentials against the IdP. |
5 |
Upon success validation,the user is redirected back to OpenNAC Enterprise. |
6 |
The user is granted only the necessary access and permissions associated with their identity. |
7 |
OpenNAC Enterprise monitors the VPN traffic to identify suspicious activity and anomalous performance. |


