1.4.4. Compliance
Establishing a baseline security posture for your organization’s infrastructure end-to-end.
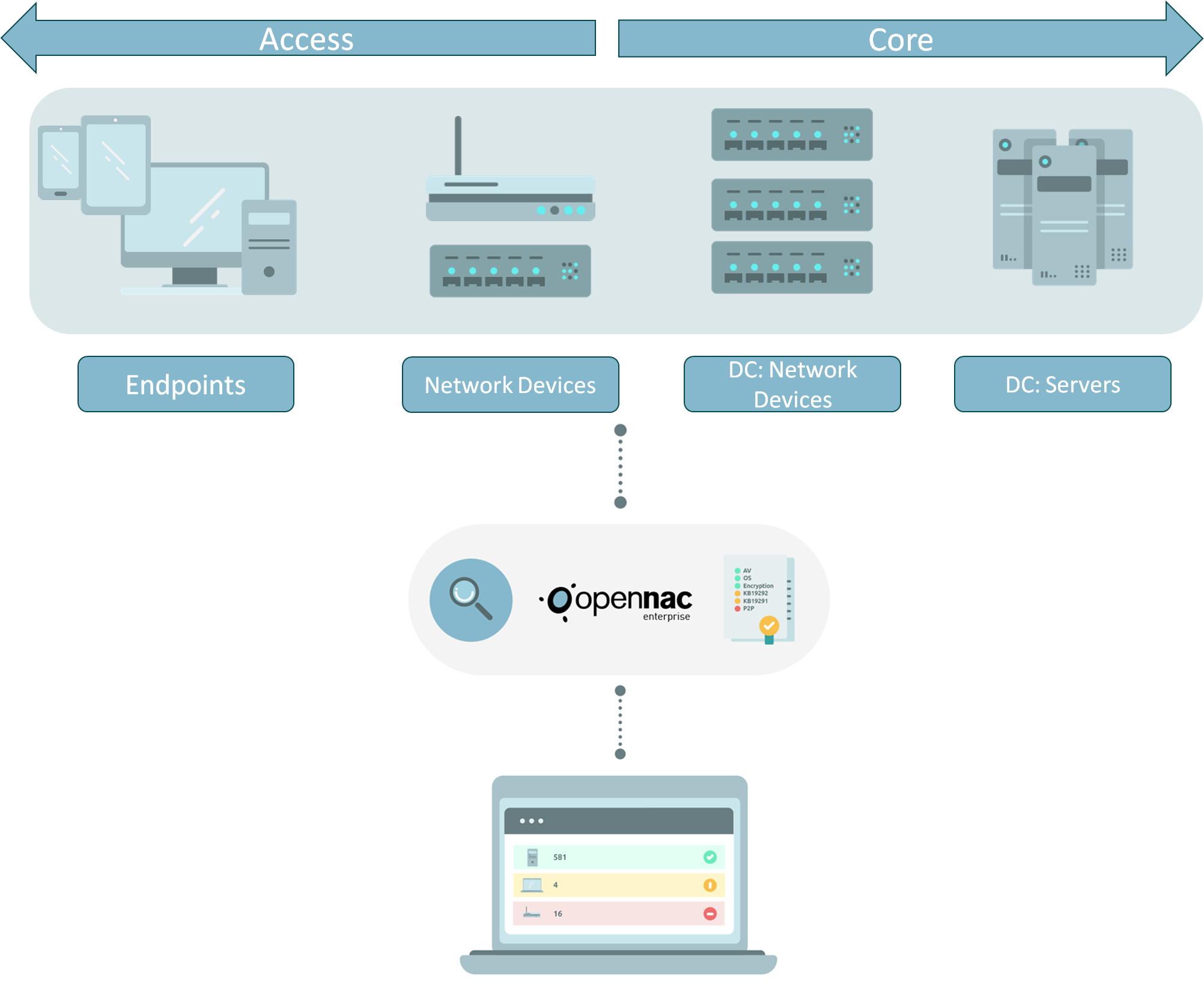
Guarantee infrastructure security compliance with corporate policies/regulatory mandates end to end.
- DEFINE A GLOBAL BASELINE
Define the necessary security baselines for your infrastructure end to end. From endpoints on the network to core switches on the Data Center.
- RESPOND TO AUDITS
Demonstrate the security posture of your infrastructure at any given time. Create reports to show compliance in a certain time period, etc.
- ADDRESS ROUGUE DEVICES
By hardening network devices configurations, rogue network devices will not have any gaps to exist.
Rogue Endpoints can be automatically discovered.