3.2.2.8.3.5. WireGuard
From this section you can define the VPN configurations for WireGuard.
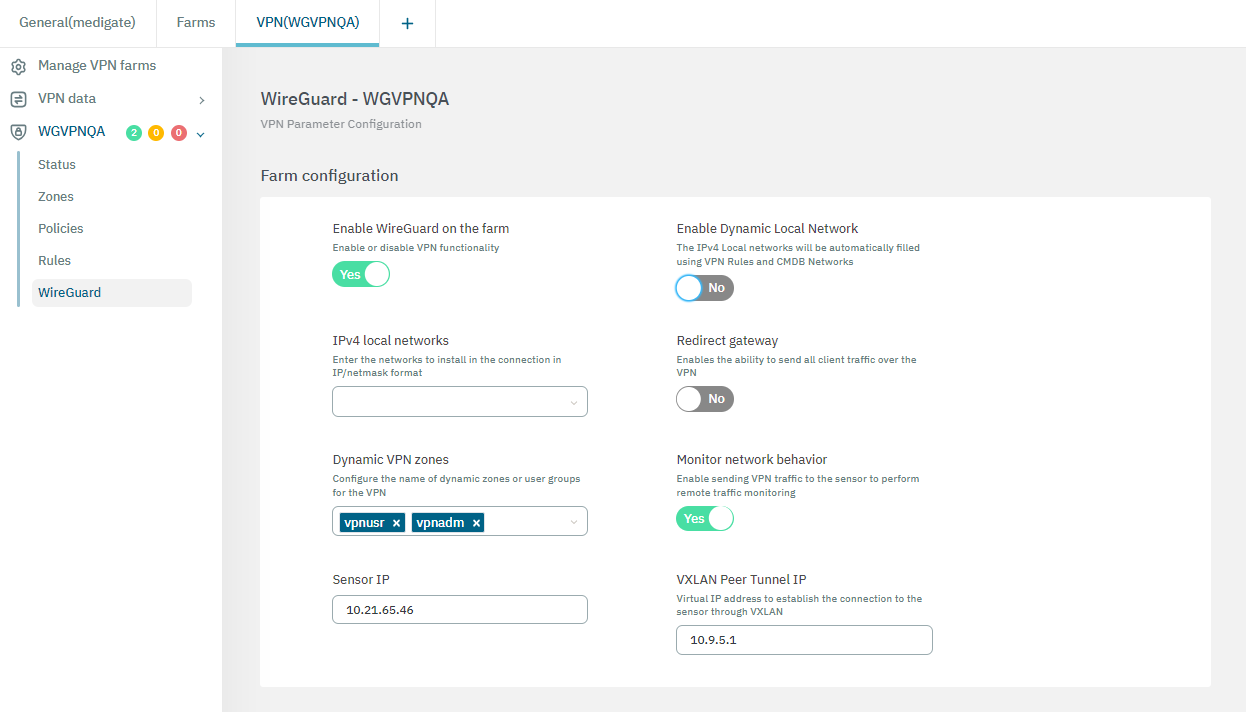
This view features Farm configurations and Node configurations. Let’s explore each of them in the following topics.
3.2.2.8.3.5.1. Farm configuration
The Farm configuration properties allows you to configure tunnel settings and Dynamic VPN zones for the Wireguard service. This configuration will synchronize with all nodes under this farm.
Enable the flag Enable WireGuard on the farm to see the following configuration options available:
Enable Wireguard on the farm: Flag to enable the service.
Enable Dynamic Local Network: If the flag is enabled, VPN rules will be applied to route traffic.
Note
Enabling the Dynamic Local Network requires a VPN rule configuration. Refer to the Dynamic Route Configuration section below for more information.
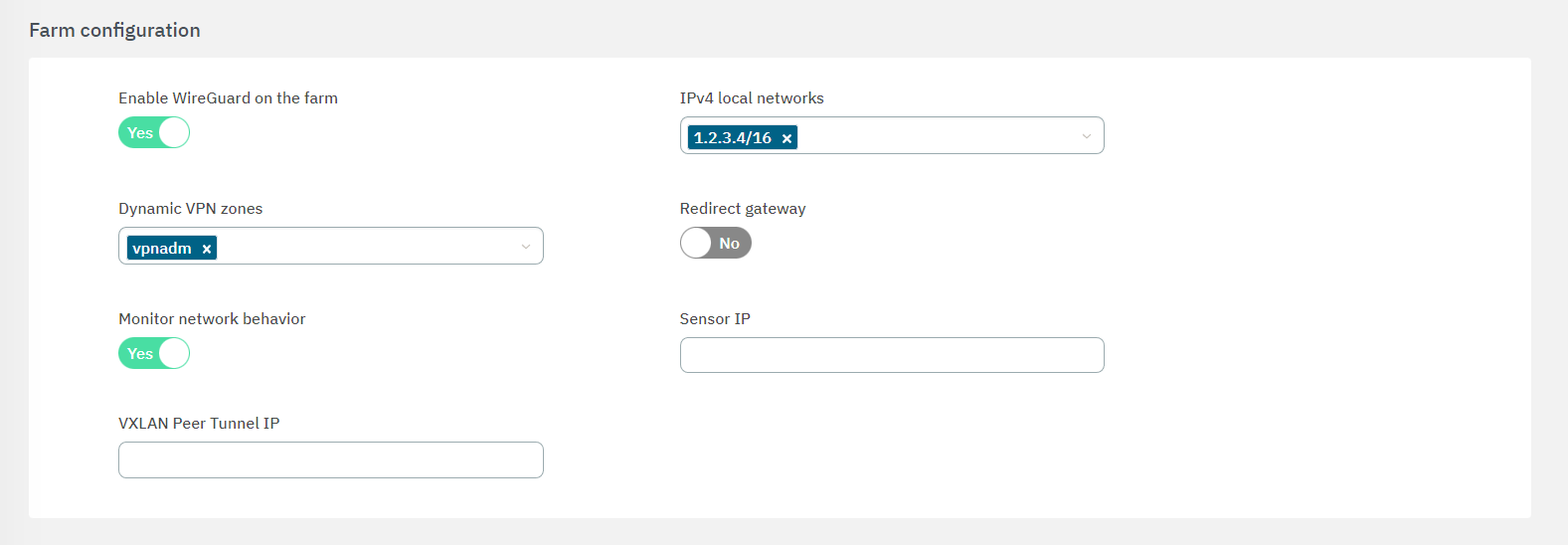
IPv4 Local Networks: Local networks in CIDR IPv4 format that can be accessed through the VPN. When the connection is established, the client receives the connection routes, enabling it to know which networks are accessible. It refers to the IP range that will be configured in the WireGuard configuration file (AllowedIps). This range determines the set of IP addresses that clients connecting to the VPN can access.
Redirect gateway: Flag to enable Gateway redirection. Enabling it changes the the IPv4 Local Networks to 0.0.0.0/0.
Dynamic VPN zones: Zones that will be dynamically associated to the VPN access groups. They will be used in the access policies.
- Monitor Network Behavior: If enabled, the traffic that is passing through the VPN connection will be monitored. Enabling it displays the following fields:
Sensor IP: : IP address for the ON Sensor BackEnd (the sensor external IP).
VXLAN Peer Tunnel IP: Remote IP address for the ON Sensor BackEnd inside the VXLAN tunnel for traffic monitoring. It is recommended to use the 192.168.70.1, but other IP addresses could also be used. Note that the Peer VXLAN Tunnel IP must match the IP address assigned to the sensor’s VXLAN-TAP interface.
3.2.2.8.3.5.1.1. Dynamic Route Configuration
Enabling the Dynamic Local Network requires a VPN rule configuration. Follow the steps described in this section for configuring it:
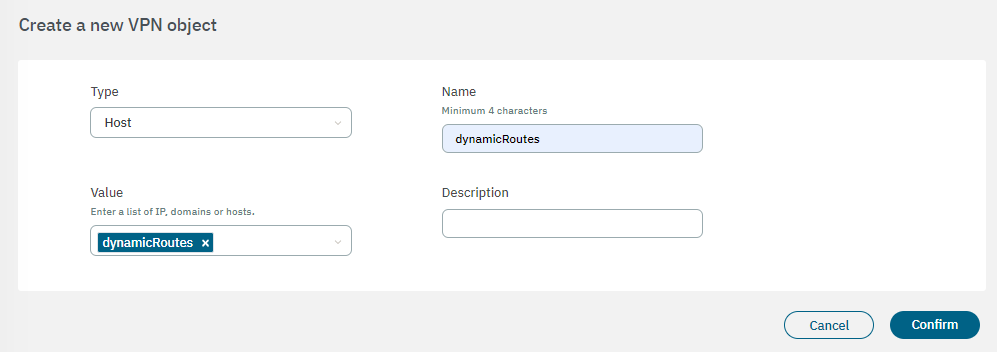
Define a network for the dynamic routes.
Define a host object for the dynamic route under the network you have previously defined in the VPNGW > VPN data > Objects.
Create a VPNGW Rule allowing connections from a dynamic zone to the specified destination.
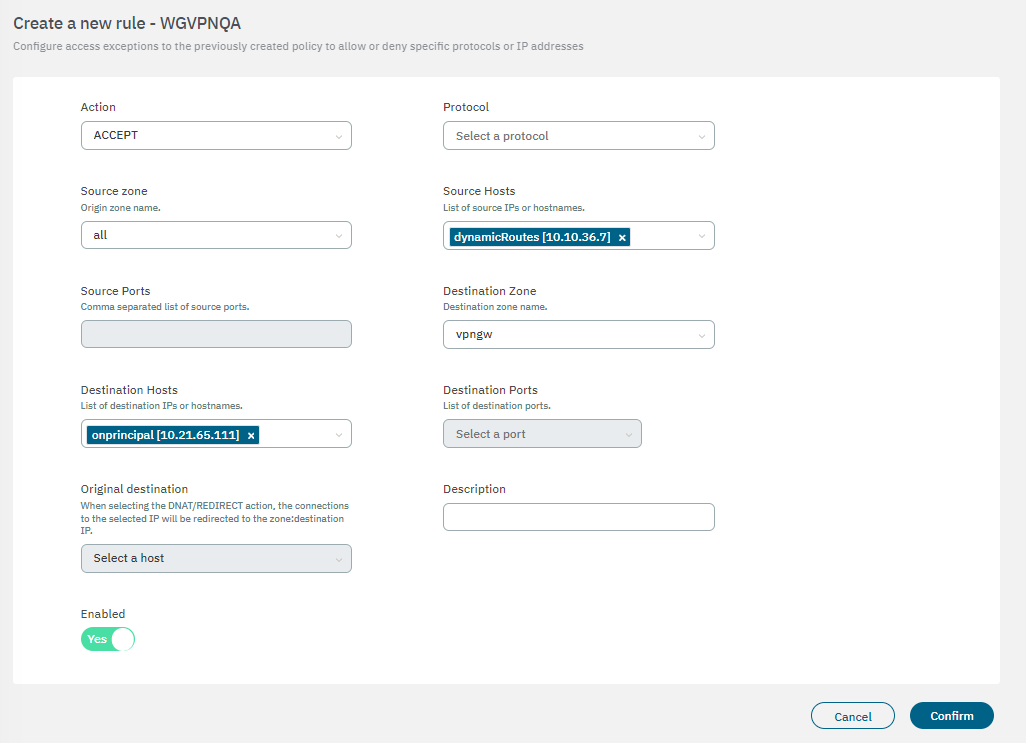
This rule will be applied when you use the Enable Dynamic Local Network flag.
3.2.2.8.3.5.2. Node configuration
The Node configuration properties allows you to apply configurations to a specific node instead of using its farm configuration.
By clicking on the icons highlighted in the following image, all fields become editable.
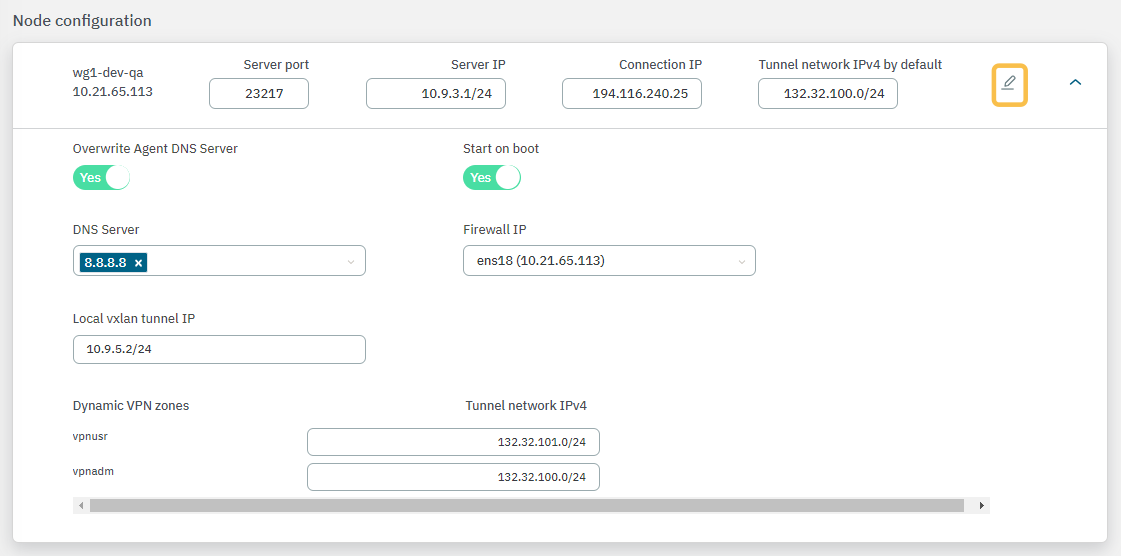
Server Port: Port that is listening inside the Firewall to receive new connections.
Server IP: The IP to use on the WireGuard network interface on the VPN Gateway server. It is recommended to use the 192.168.71.1/24, but other IP addresses could also be used.
Connection IP: VPNGW node public IP (ON VPNGW node external IP).
Tunnel network IPv4 by default: Network in IPv4 CIDR format for remote users. Pool of IP addresses to be offered from the VPN Gateway. This network must be unique in your organization.
Overwrite Agent DNS Server: By enabling the flag, the new DNS servers will replace the current ones. If disabled (default), the new DNS servers will be appended to the existing ones.
Start On Boot: Enable this flag if you want the VPN Gateway to start when the machine reboots. If it is disabled, you have to manually start the VPN after rebooting.
DNS Server: DNS server IP.
Firewall IP: The IP that has communication with the sensor.
Local VXLAN Tunnel IP: This has to be an IP address from the network of the VXLAN-TAP interface of the sensor.
To understand the configuration of the Sensor interface, refer to the ON Sensor Node configuration for the 2SRA use case.
Once you have finished, click on Confirm to save your configurations.
The service is now ready for deployment and can be initiated from the Manage VPN farms section.