4.2.1. Introduction
This section will introduce the UNAC use case, going through its main concepts, capabilities, and different authentication scenarios.
4.2.1.1. What is UNAC?
UNAC is a module designed for authenticating all users and devices across a corporate network, including wired, wireless, and VPN connections.
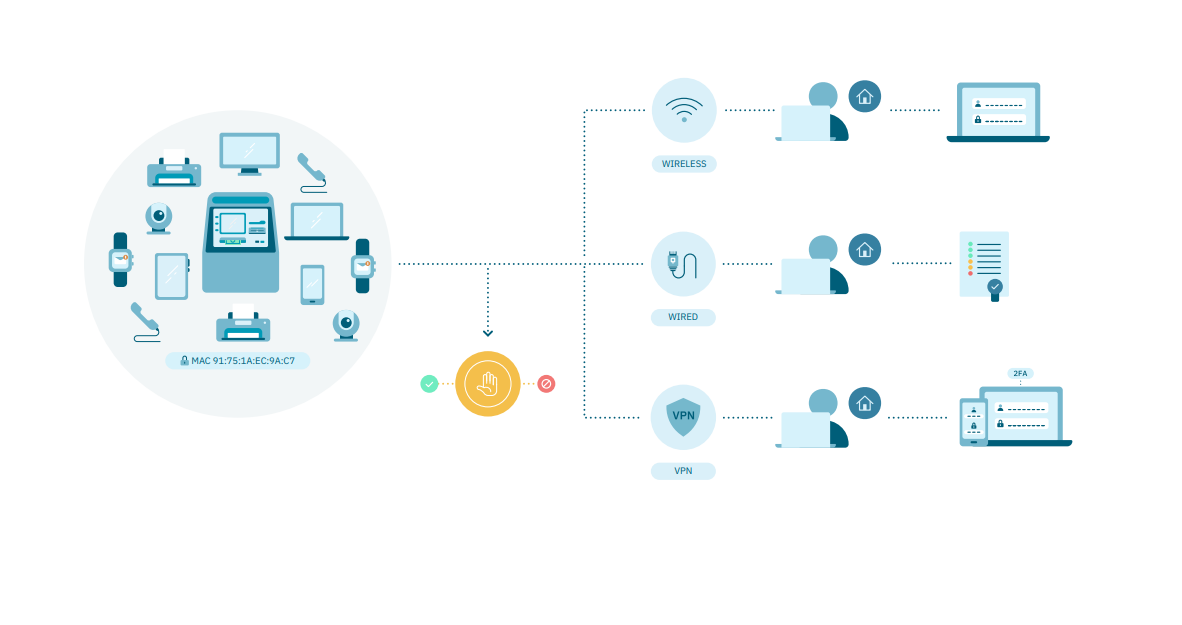
It provides the foundation for implementing a Zero Trust security strategy and adheres to security principles such as the least privilege principle.
Users and devices can be authenticated using various methods within the UNAC module:
Corporate user credentials
Corporate credentials + OTP (2FA)
Certificates with internal CA
MAB for non-supplicant devices
4.2.1.2. 802.1x
UNAC relies on the 802.1x protocol for establishing authentication policies.
8021x is a network access control protocol that permits or denies device access to the network by using authentication. Ethernet switch ports can be enabled dynamically based on the identity of the device that connects to it. Devices that are not authenticated cannot gain access to the network.
802.1x Authentication Components
A supplicant: a client device (such as a laptop or endpoint device) that attempts to access a LAN/Wireless LAN (WLAN), or the software that runs on this device and provides credentials to the authenticator.
An authenticator: a network device (such as an Ethernet switch or wireless access point) that acts as an access point to a protected network. For 802.1X authentication, the supplicant provides network credentials, such as username, password, digital security certificate, or a combination of these, to the authenticator. The authenticator then forwards the credentials to the authentication server for verification.
An authentication server: a server (such as ON Core) that guards the protected network. For 802.1X authentication, the authentication server receives the supplicant’s network credentials from the authenticator and verifies the supplicant’s identity so the supplicant can access the resources located on the network.
The figure below illustrates the fundamentals of the 802.1x protocol:
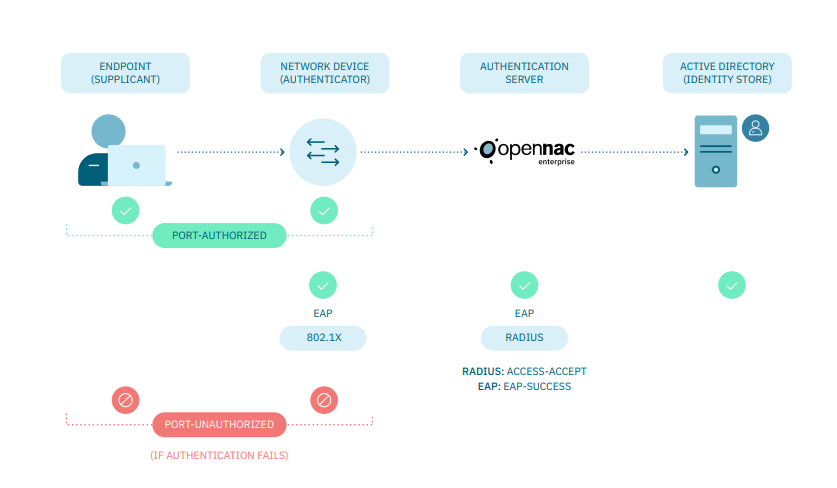
Supplicant: Software running on the client that provides credentials to the authentication (Network Device).
EAP: Extensible Authentication Protocol.
802.1x is based on RADIUS (Remote Authentication Dial In User Service) protocol which consist in a standardized method of information exchange between a device that provides network access to users called RADIUS client and a device that contains authentication information for those users called RADIUS server.
See the 802.1x Concept section for further details about this protocol.
4.2.1.3. Authentication Scenarios
Understand the different scenarios and authentication methods enabled by the UNAC module.
4.2.1.3.1. User and Password
User identity will be validated based on information that users know, such as their username and password. In this case, the user’s corporate credentials will be utilized for the validation process.
Requirements
Integration with User Database (LDAP, AD).
Enable 802.1x supplicant in user device.
Enable 802.1X protocol settings in network devices.
Access rules in OpenNAC Enterprise.
Outputs
Authentication metrics
Control Dashboards
Connected devices information: Connected devices information: IP, MAC, Switch Interface, VLAN, Hostname, User, and last access.
4.2.1.3.2. Host
Host identity will be validated based on information stored locally on the device, such as a digital certificate or device-specific credentials. In this case, the device’s credentials or certificate will be utilized for the validation process.
Requirements
CA Settings
Certificates generation
Certificates Deployment
Enable 802.1X protocol settings in network devices
Access rules in OpenNAC Enterprise
Outputs
Authentication metrics
Control Dashboards
Connected devices information: Connected devices information: IP, MAC, Switch Interface, VLAN, Hostname, User, and last access.
4.2.1.3.3. Certificate
Every user and/or device will possess a unique certificate generated by a Certificate Authority (CA). These certificates can be issued for either devices or individual users.
Requirements
CA Settings
Certificates generation
Certificates Deployment
Enable 802.1X protocol settings in network devices
Access rules in OpenNAC Enterprise
Outputs
Authentication metrics
Control Dashboards
Connected devices information: IP, MAC, Switch Interface, VLAN, Hostname, User, and last access.
4.2.1.3.4. MAB
In a MAB scenario, devices are allowed to connect to the network based on the MAC address without requiring any user credentials. This method accommodates devices that do not support 802.1x authentication, such as printers, IP phones, or legacy devices.
Requirements
Enable MAB as authentication method
Access rules in OpenNAC Enterprise
Outputs
Authentication metrics
Control Dashboards
Connected devices information: IP, MAC, Switch Interface, VLAN, Hostname, User, and last access.
4.2.1.4. UNAC in 4 Steps
The UNAC configuration and operation process involve the following 4 steps:
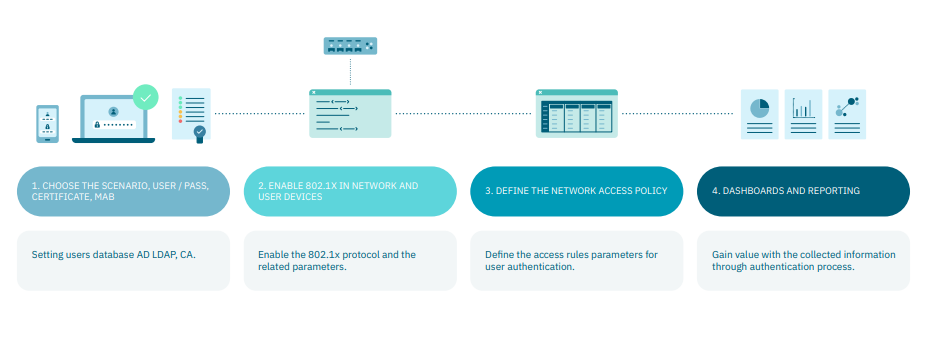
The first two steps are explained in the Configuration documentation and the last two are in the UNAC operation.
4.2.1.5. Host Modes
Host Modes define the different levels of access control that can be applied to network resources. It is based on the host that is trying to access them and can enforce different levels of security and restrictions for different types of devices.
There are several Host Modes that can be used in network authentication.
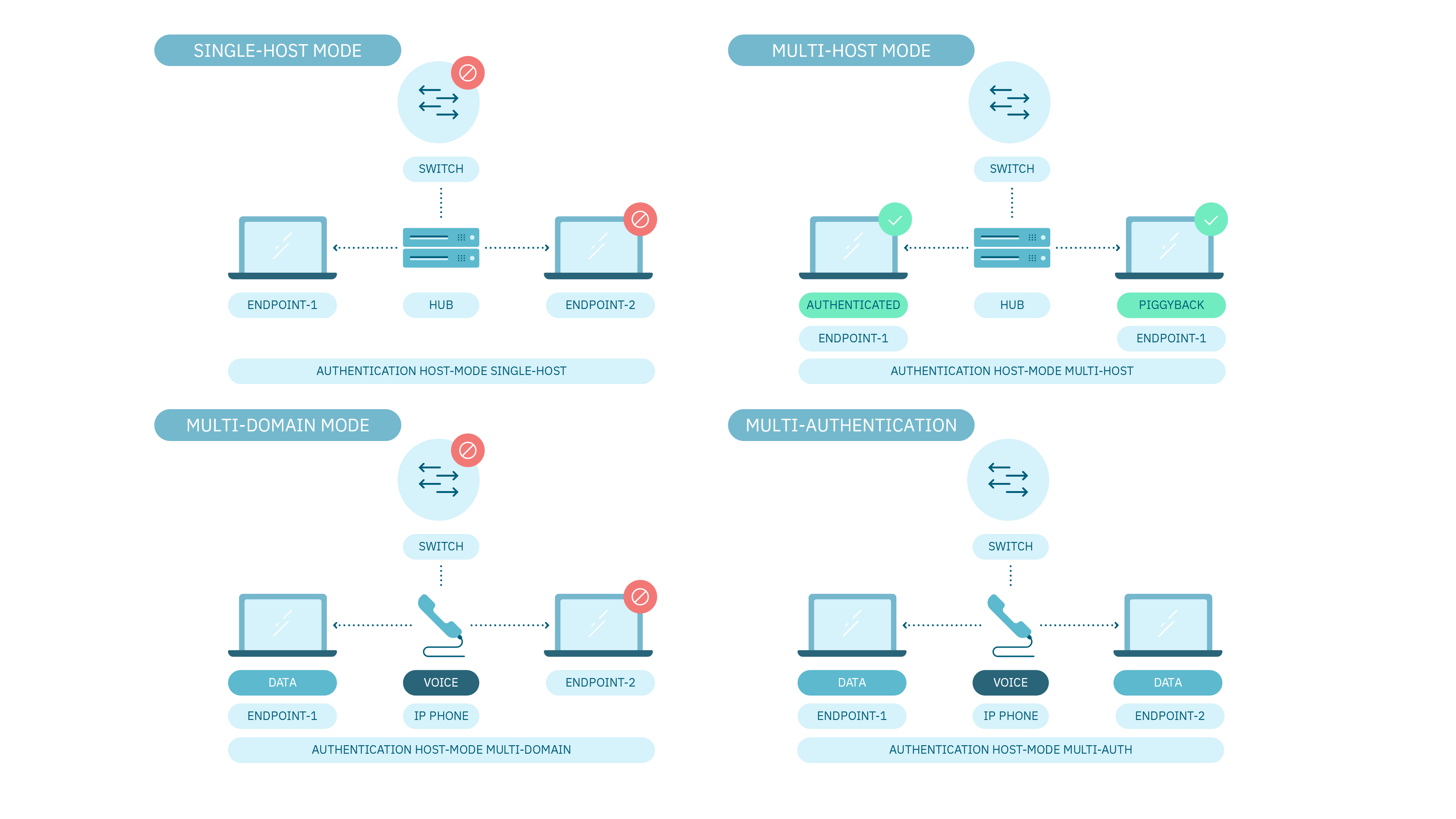
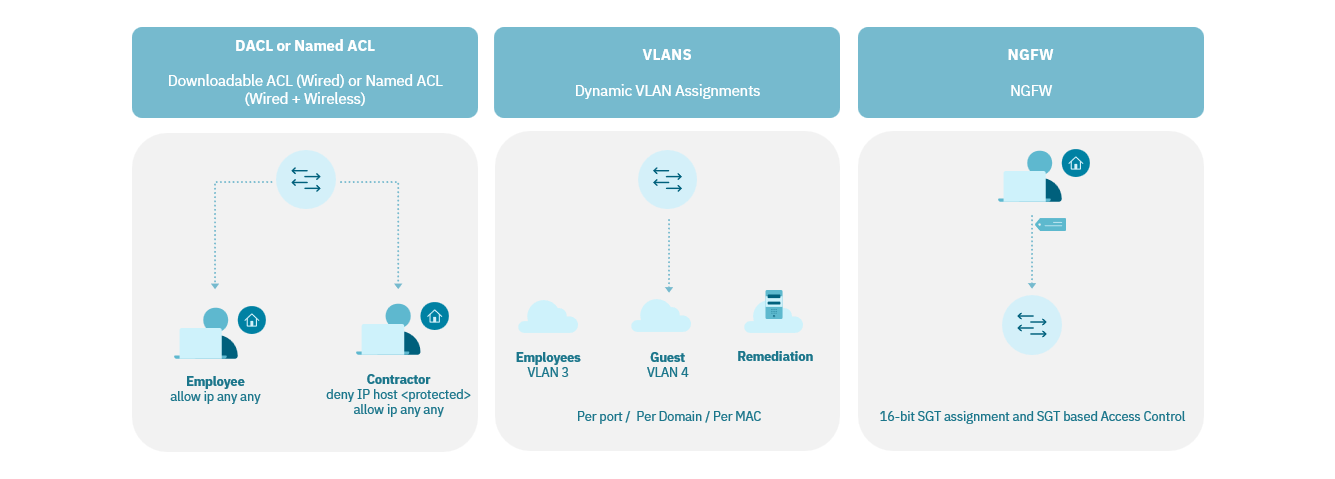
Single-Host Mode: Only “a” MAC address is allowed. A second MAC address causes a security violation.
Multi-Host Mode: The first MAC address is authenticated. The second endpoint piggybacks on the first MAC address authentication and bypasses authentication.
Multi-Domain Host Mode: Each domain (voice or data) authenticates one MAC address. The second MAC address in each domain causes a security violation.
Multi-Authentication: The voice domain authenticates one MAC address. The data domain authenticates multiple MAC addresses. dACL or single VLAN Assignment for all devices is supported.