4.7.1.7. Operation
This section provides an overview of the key operational aspects related to the 2SRA use case using the Default Portal.
Note
Before proceeding with the operation section, make sure you have completed the administration configurations to prepare the system for basic operations.
4.7.1.7.1. Checking the status of VPN connections
This section shows how to use the system’s Business Profiles to view active connections, and how to get more information about a device. The Business Profiles are groups of connections based on the associated policies, they are customizable and we can create as many as we want, simply giving a name and selecting the policy or policies we want to be included. Go to the ON NAC -> Business Profiles in the Default View.
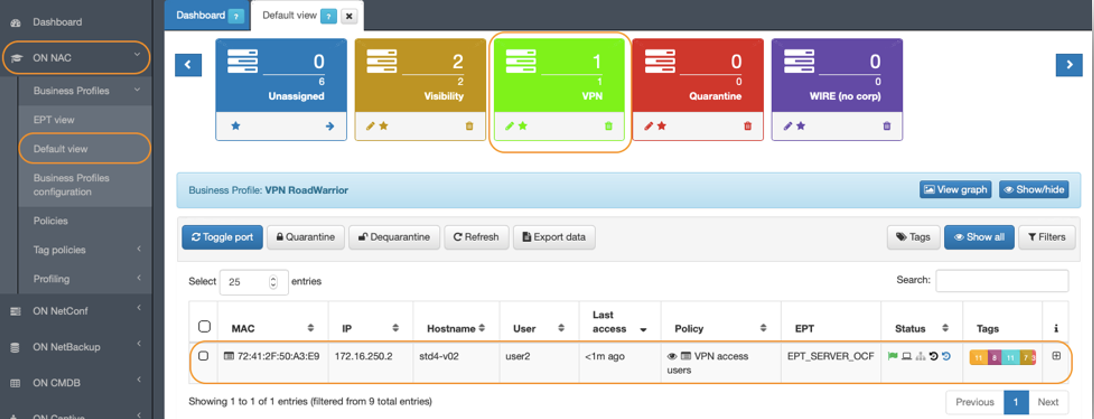
Let’s focus on the VPN Business Profile (green box) from our example. At the bottom you can see the total number of devices you have registered with the VPN TAG. At the top, we have another counter, which indicates the total number of devices that are connected. In each connection, horizontal line, if we go to the Status column we can see that there is a flag, which helps us identify the current connection status of the selected device.
Green flag indicates that the device is connected (login)
Red flag indicates a problem and that could not connect
Black flag indicates that the device is not connected (logout)
If we click on the icon that appears in the Policy column, we are able to obtain more information about the selected connection.
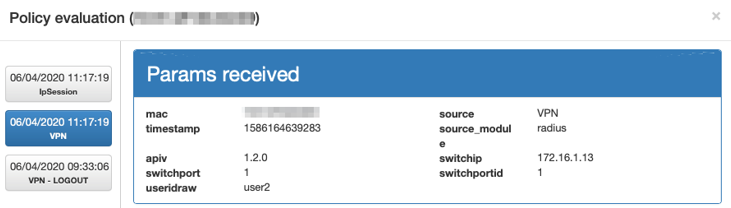
Another way to view more information about the connection, is to use the + icon on the right end, which will display all the information from the different sources of information related to the device.
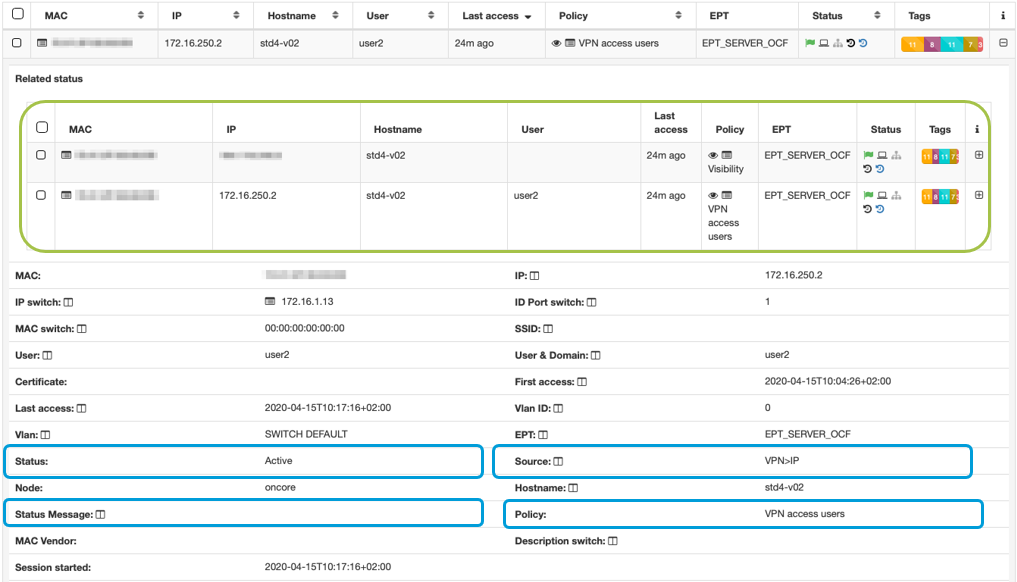
In the green box, you can see that there are two sources of information and two connections. The first refers to the data of the device through the public IP, information received through the internet and sent by the agent. The second source is from the VPN connection itself since its IP is a private address that matches the pool of IPs configured in the RoadWarrior VPN tunnel.
In this same view, we can see more information about the VPN connection. We can highlight the information inside the orange boxes, which provide useful information about the status of the connection. For example, the current status of the connection is indicated, the source from which it comes (in this case VPN and IP are assigned), the policy accessed by the device, and a message regarding the status.
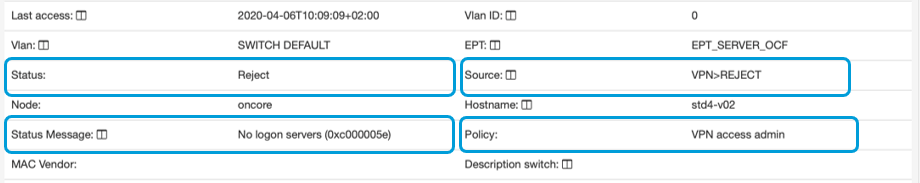
The image shows a case where the connection was rejected. Its status is Reject, there is a message of the cause of the error No logon servers, the source becomes VPN and reject, and the policy is maintained.
4.7.1.7.1.1. VPN Gateway status
You can check the VPN Gateway status from the Manage VPNGW view:
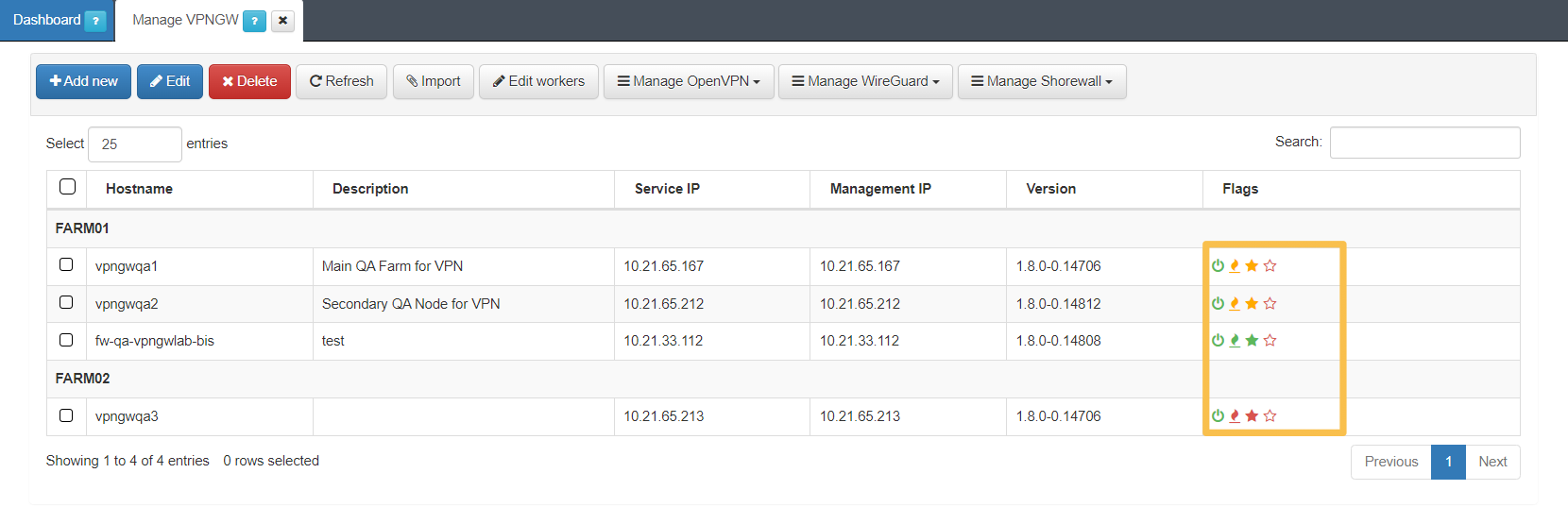
Hovering over the icons, you can read the status of the following components:
They will be displayed in red, yellow and green according to their status that can be up & running, started & updated, started but not updated, and status unknown.
4.7.1.7.2. Checking a connected client in the VPNGW
We can check if the client is connected using either Wireguard or OpenVPN.
4.7.1.7.2.1. Wireguard
You can check which clients are connected to a Wireguard VPN will through the Administration Portal VPNGW section or via SSH.
4.7.1.7.2.1.1. Administration Portal - VPNGW
In the Administration Portal main menu, click on VPNGW and click on the corresponded Farm section from where you want to consult clients.
Select on the Wireguard section and once there, click on Manage users to display the following window:
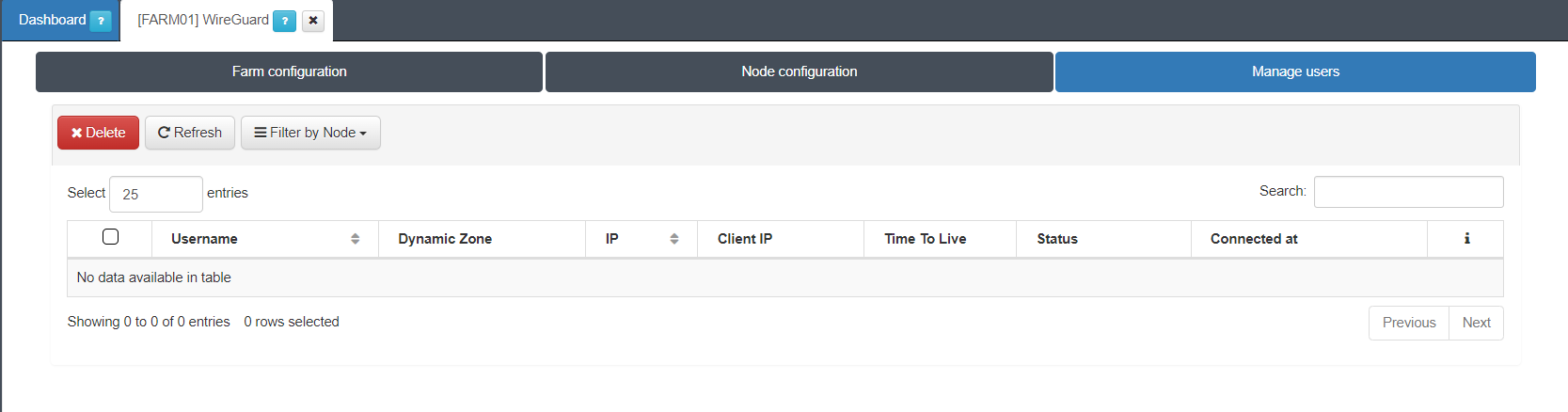
This view displays information of all connected users. This includes username, dynamic zone, IP, TTL, status icons (connected, standalone, dynamic/static), and the date the connection was established. If you click the + button, it will display detailed information abut this specific user.
The Search box allows you to search for any user data. For example, you can filter by the username user_test and as a result, a single row will appear with the user user_test.
Note
A standalone user is one that can connect from an openNAC agent or from a native WireGuard agent. A user NOT standalone can only connect from an openNAC agent.
See the VPNGW WireGuard section for more information.
4.7.1.7.2.1.2. Via SSH
From the command line of the VPN gateway we can also observe information about the users.
SSH into the CMI.
Note: Remember that there is NOT a rule that allows traffic to access the VPN gateway via SSH from any source. However, it can only be accessed from the CMI.
SSH into the VPN gateway.
In the VPN gateway run the following command:
wg show <VPN_name>
This command will show us the connected users and the standalone users (whether they are connected or not).
Example of the user with IP 172.16.250.5 connected to the VPN. The information under interface pertains to the VPN configuration while the information under “peer” will give us user information:
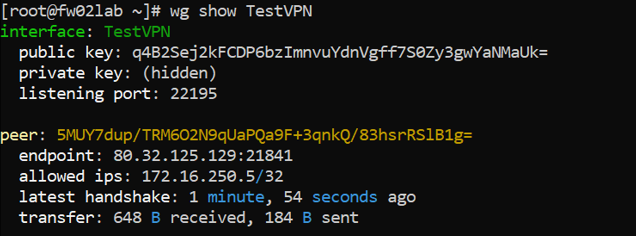
In the VPN gateway, run the following command:
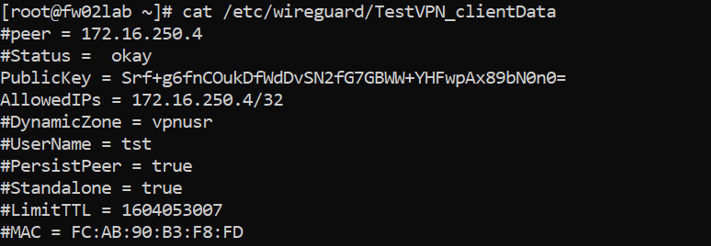
cat /etc/wireguard/<VPN_name>_clientData
This command will show us the static users and the standalone users.
Example of the static user with IP 172.16.250.4:
4.7.1.7.2.2. OpenVPN
You can check which clients are connected using OpenVPN through the Administration Portal VPNGW section or via SSH.
4.7.1.7.2.2.1. Administration Portal - VPNGW
In the Administration Portal main menu, click on VPNGW and click on the corresponded Farm section from where you want to consult clients.
Select on the OpenVPN section and once there, click on Node configuration to display the following window:
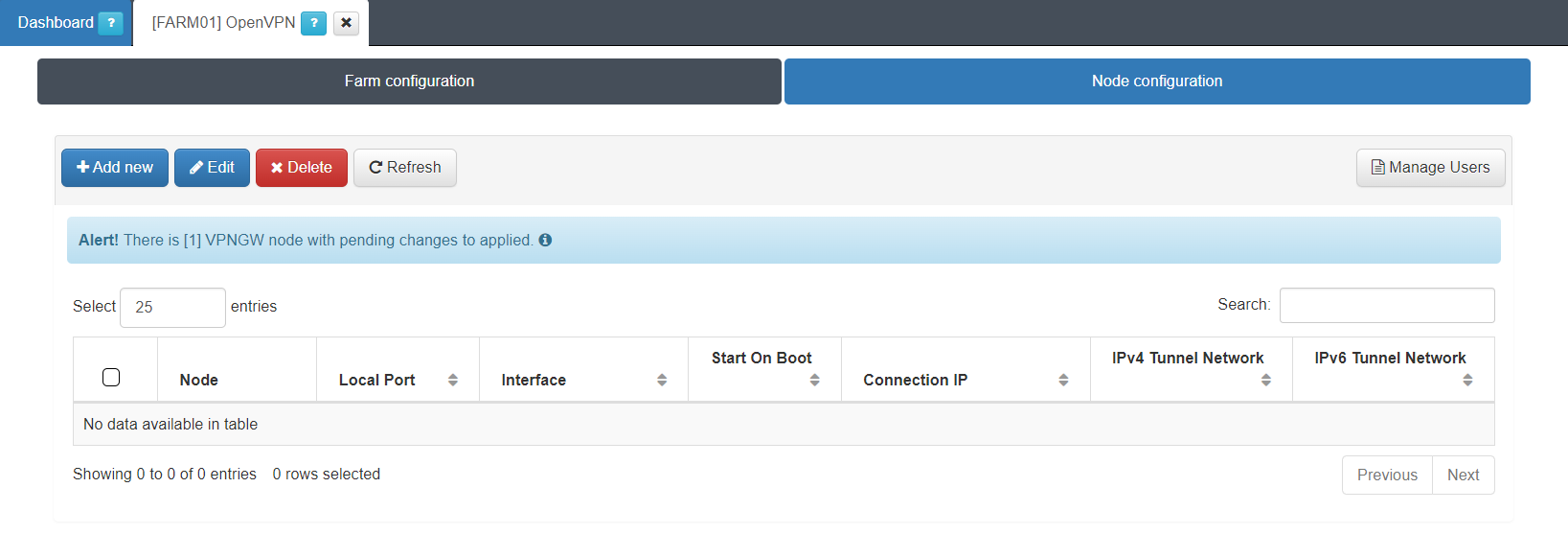
Once there, select a node from the displayed list and click on Manage Users.
EDIT In the table you can see the information of each connected user. This includes the username, Virtual IP, real IP, day and time the connection was established, and the data sent and received.
The Search box will allow you to search for any user data. For example, you can filter by the username user8 and as a result a single row will appear with the user user8.
The actions available on this screen are:
Disconnect: Disconnect the user.
Refresh: Reloads the information of the users in the table.
Export All data: A file in CSV format containing the user data will be downloaded.
4.7.1.7.2.2.2. Via SSH
From the VPN gateway command line we can also see information about connected users.
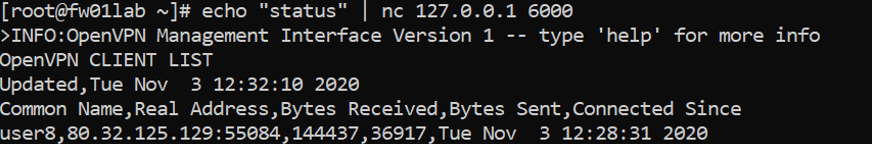
1) SSH into the CMI. Note: Remember that there is NOT a rule that allows traffic to access the VPN gateway via SSH from any source. However, it can only be accessed from the CMI. 2) SSH into the VPN gateway. 3) In the VPN gateway run the following command:
echo "status" | nc 127.0.0.1 6000