9.2.4.5. Cisco
9.2.4.5.1. Wireless LAN Controller (WLC)
In this section, we cover the basic configuration of the WLC for OpenNAC Enterprise using the web interface.
9.2.4.5.1.1. Wireless LAN Controller (WLC) 802.1X
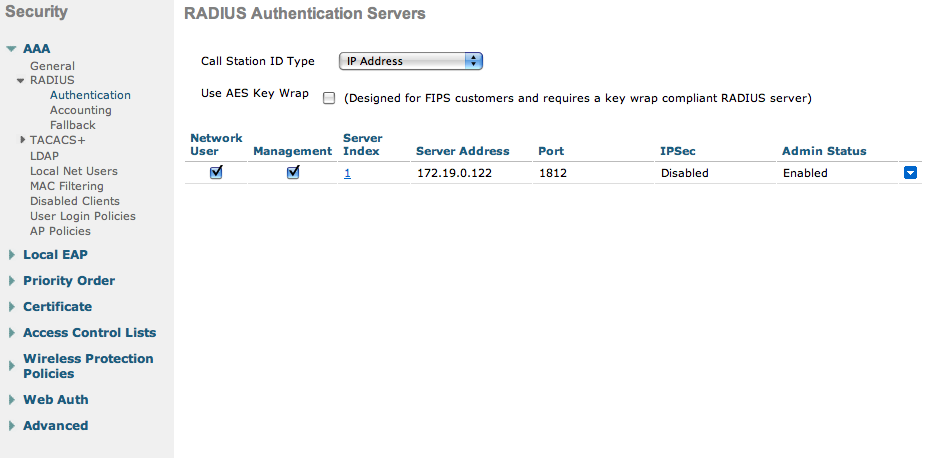
First, globally define the RADIUS server running on OpenNAC Enterprise and make sure “Support for CoA” is enabled (if not displayed, it is enabled by default).
Then, create an SSID:
OpenNAC-Secure: secure with WPA2 Enterprise PEAP/MSCHAPv2.
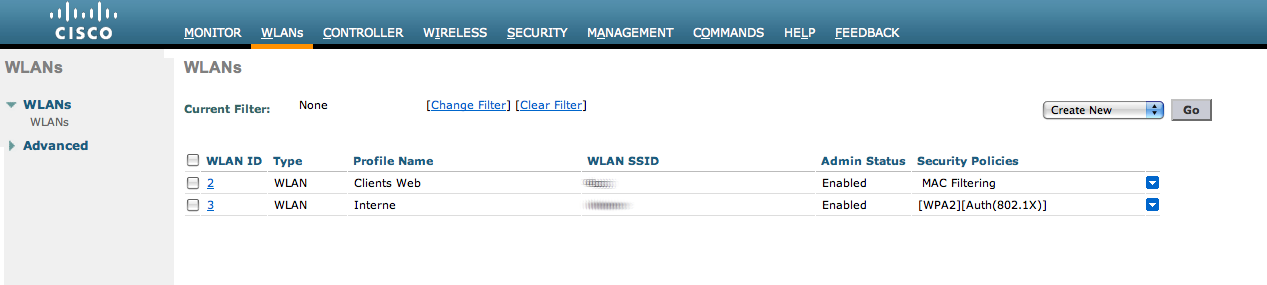
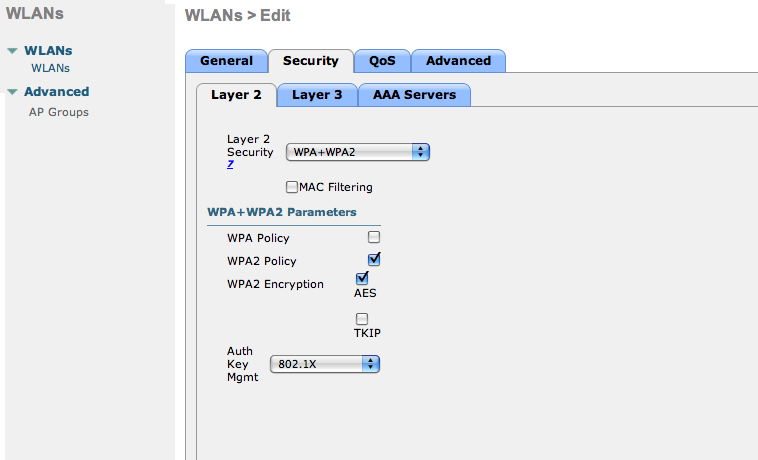
In the secure SSID, make sure 802.1X is enabled and select the appropriate encryption for your needs (recommended: WPA + WPA2).
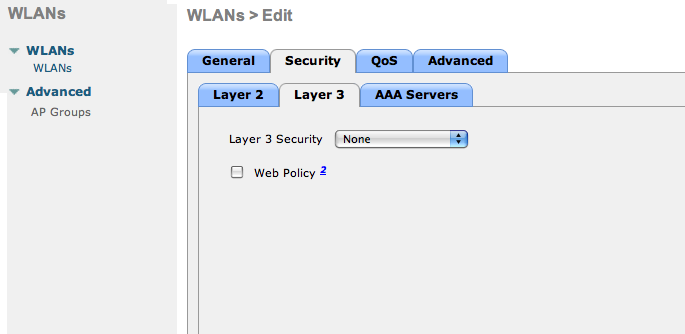
No Layer 3 security.
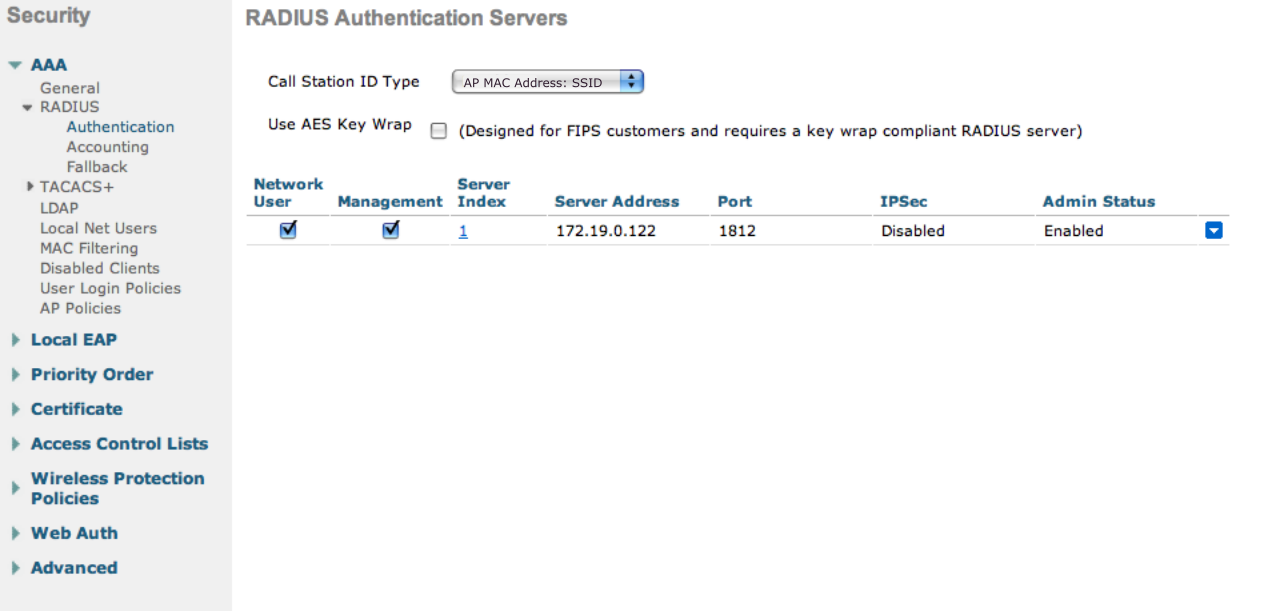
Set the IP of the OpenNAC Enterprise server in the “AAA Servers” tab.
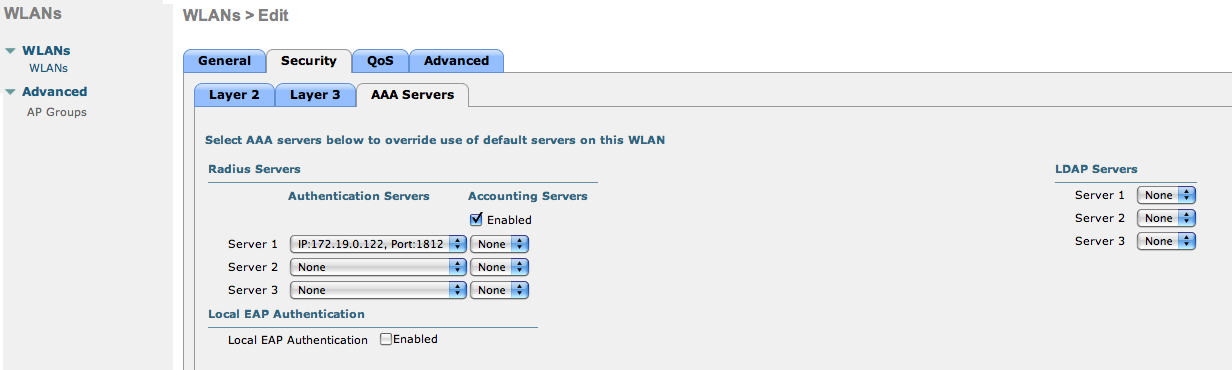
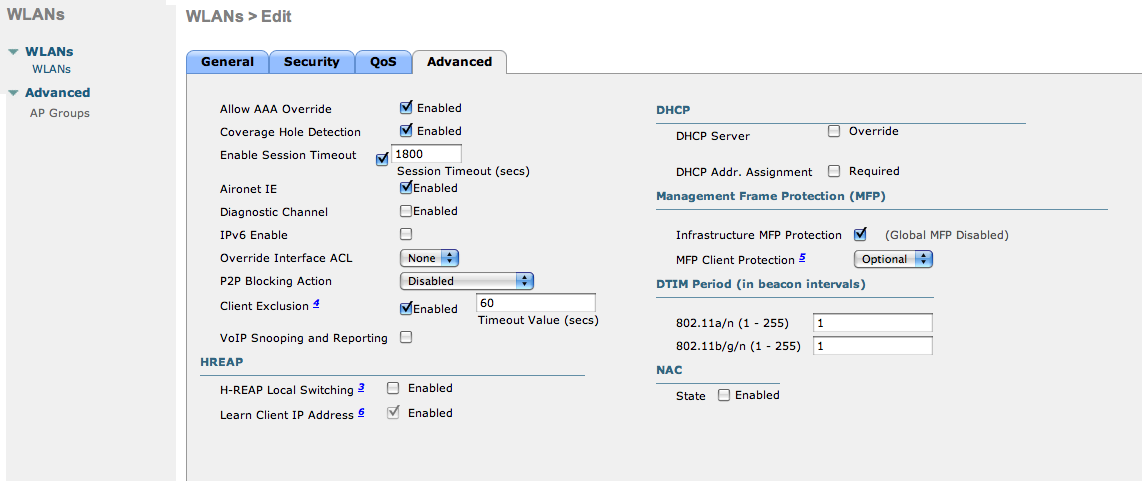
Allow AAA override in the Advanced Tab. This allows VLAN assignment from RADIUS.
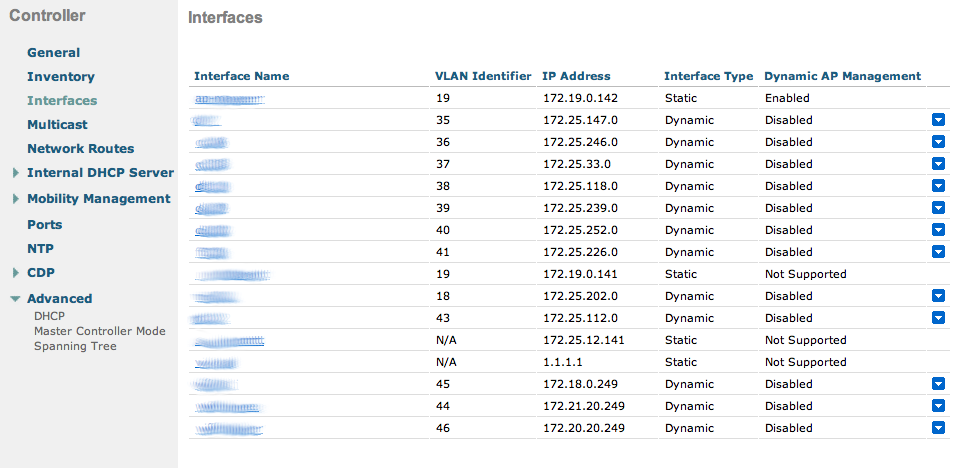
Finally, in Controller > Interfaces tab, create an interface per VLAN that could be assigned.
9.2.4.5.1.2. Wireless LAN Controller (WLC) MAC-Auth
First, globally define the RADIUS server running on OpenNAC Enterprise and make sure “Support for CoA” is enabled (if not displayed, it is enabled by default).

Then, create an SSIDs:
OpenNAC-Public: non-secure with MAC authentication only.

Edit the non-secure SSID: Enable MAC authentication at Layer 2.
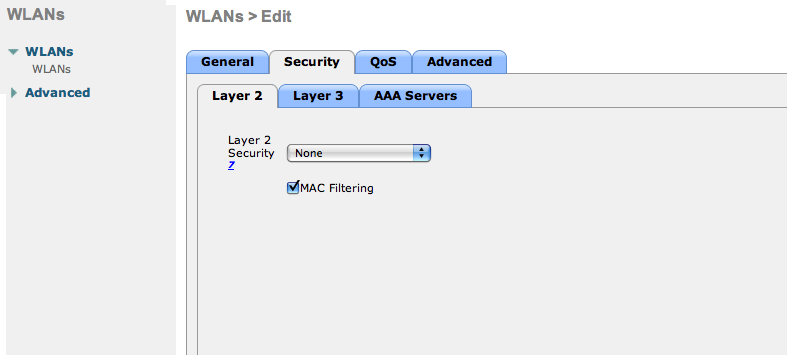
No Layer 3 security
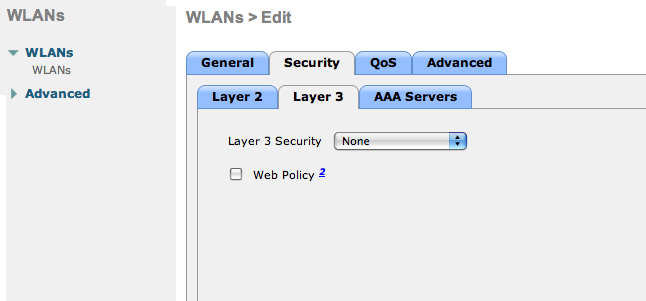
Set the IP of the OpenNAC Enterprise server in the “AAA Servers” tab.

Allow AAA override in the Advanced tab. This allows VLAN assignment from RADIUS.

Finally, in the Controller > Interfaces tab, create an interface per VLAN that could be assigned.

9.2.4.5.1.3. Wireless LAN Controller (WLC) Web Auth
In this section, we cover the basic configuration of the WLC Web Auth for OpenNAC Enterprise using the web interface. The idea is to forward the device to the Captive Portal with an ACL if the device is in an unreg state and allow the device to reach Internet (or the normal network) by changing the ACL once registered.
In the unreg state, the WLC will intercept the HTTP traffic and forward the device to the captive portal.
First, globally define the RADIUS server running on OpenNAC Enterprise and make sure “Support for CoA” is enabled (if not present, it is enabled by default).
Then, you have to create two ACLs - one to deny all traffic except the required one to hit the portal (Pre-Auth-For-WebRedirect) and the another one to allow anything (Authorize_any).
Create a new SSID:
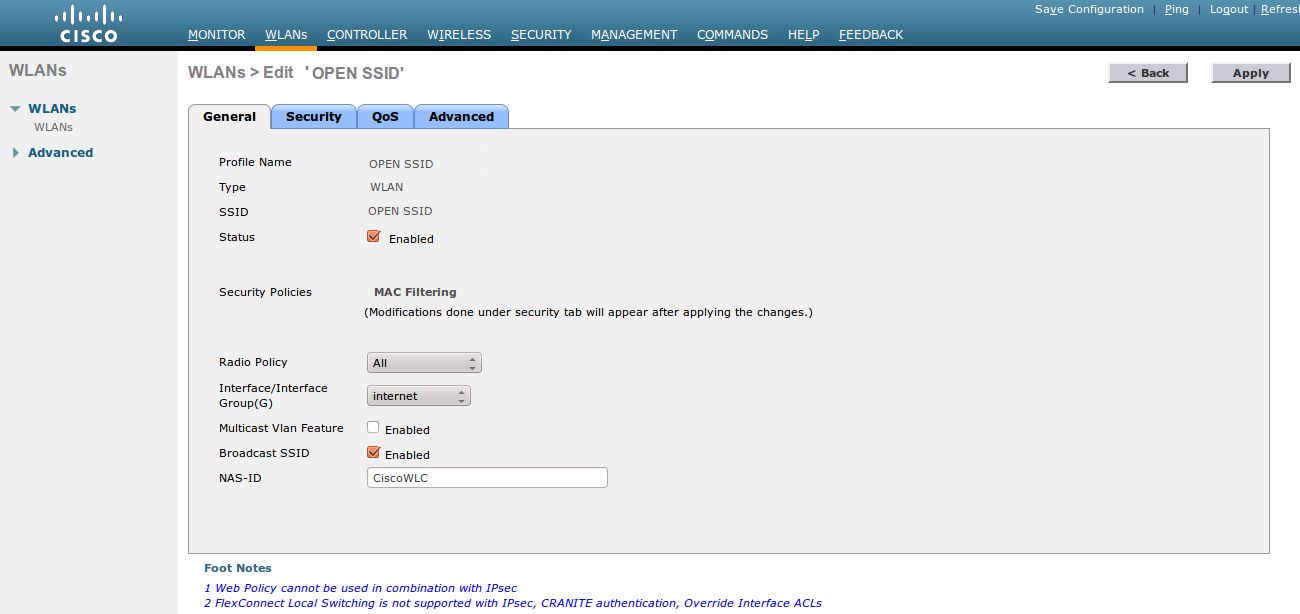
Security > Layer 2: Enable MAC authentication at Layer 2 (optional).
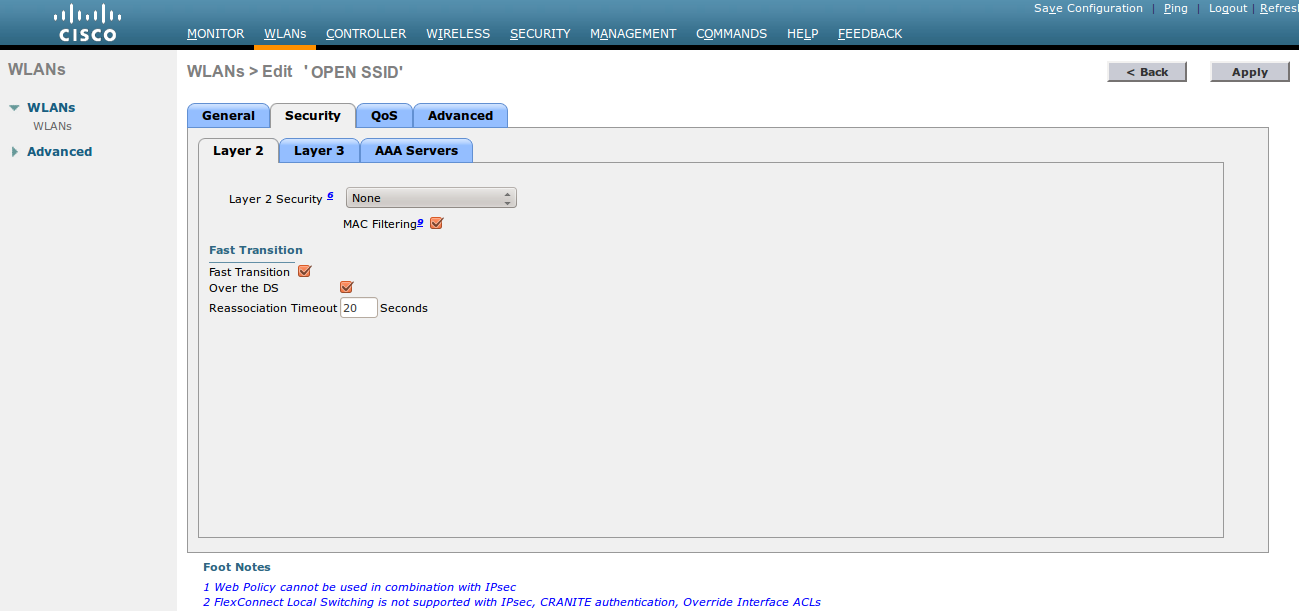
Security > Layer 3:
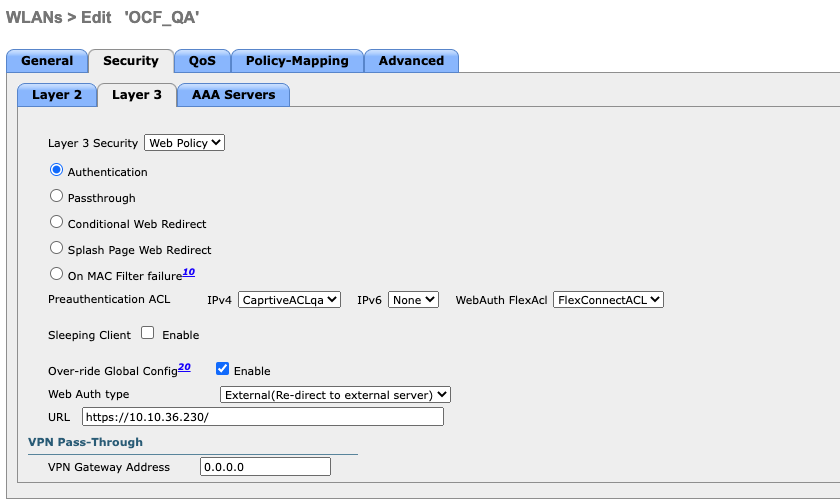
Layer 3 Security: Web Policy with Authentication mode
Preauthentication ACL: The ACL that will be assigned to user sessions prior to a valid authentication in the captive portal. It is important that the applied ACL allows users access to the captive portal so that they can authenticate.
Web Auth type: External
URL: The URL of the OpenNAC Enterprise captive portal to which the user will be redirected once connected to the network.
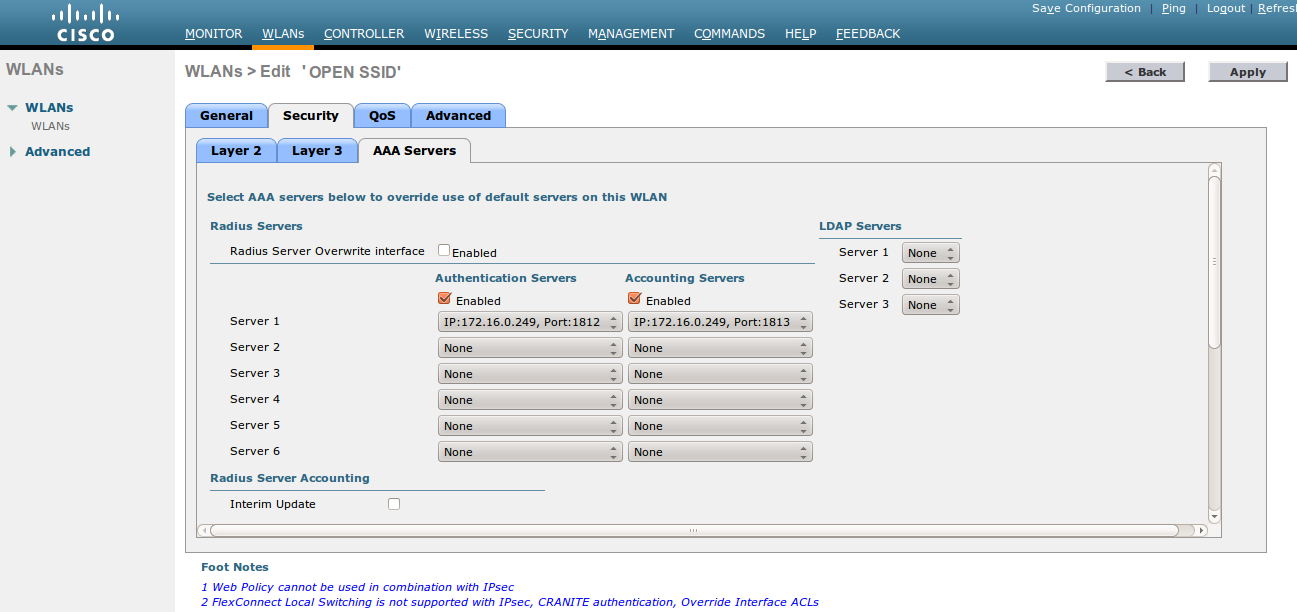
Security > AAA Servers: Set the IP of the OpenNAC Enterprise server.
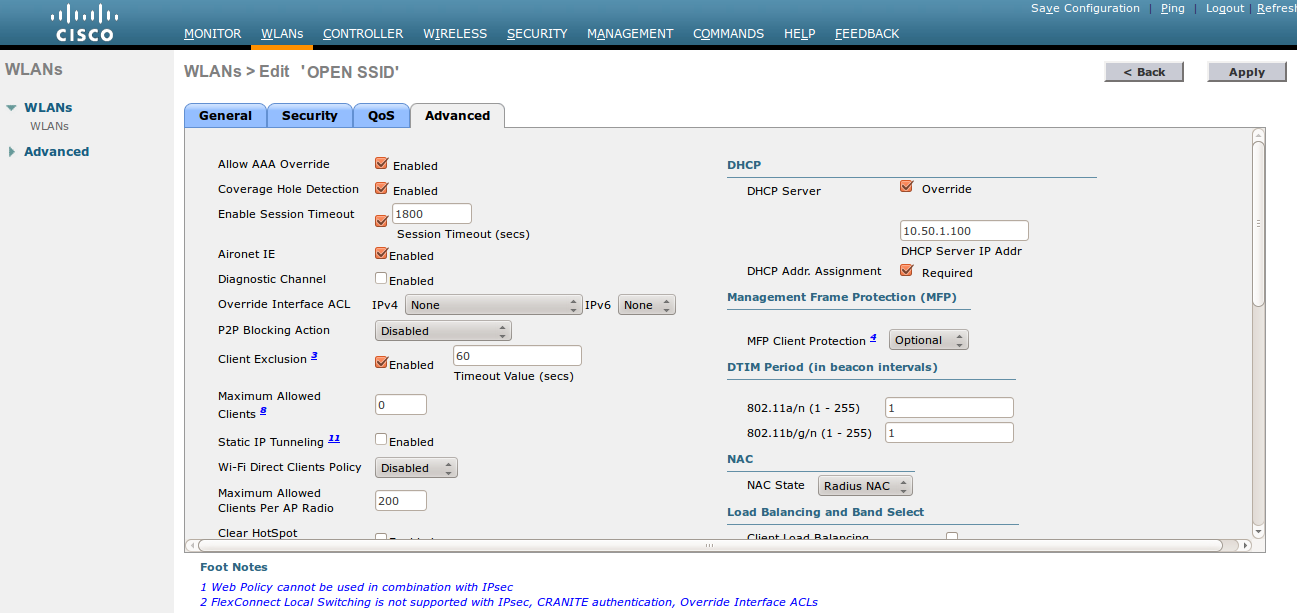
Allow AAA override in the Advanced tab. This allows VLAN assignment from RADIUS.
The last step is to configure the WLC on the OpenNAC Enterprise CMDB.
Note
Troubleshooting ignored RADIUS replies.
In the event that the WLC ignores the RADIUS replies from OpenNAC Enterprise (you receive multiple requests but access is never granted), validate the following elements :
RADIUS secret is properly configured in OpenNAC and the WLC controller.
The SSL certificate used by OpenNAC is not expired.
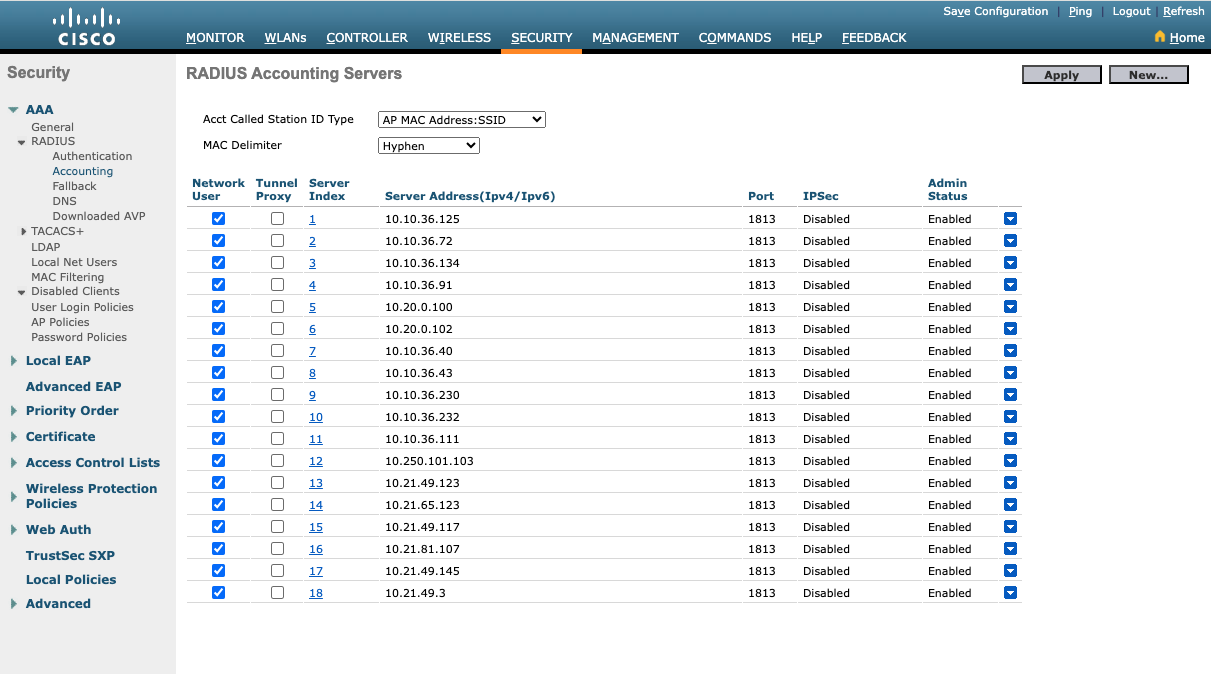
9.2.4.5.1.4. Wireless LAN Controller (WLC) RADIUS Accounting
This configuration allows the WLC to communicate with a RADIUS server to record user authentication and network access details.
9.2.4.5.2. Cisco Catalyst 9800L WCL
This section describes the configuration details of the Cisco Catalyst 9800L Wireless Controller (hereafter WLC) to implement a captive portal for guest user access.
9.2.4.5.2.1. Configuring WLC Web Auth parameters
Go to Menu > Configuration > Security > Web Auth:
In the Web Auth Parameter Map view, select the named parameter you want to edit:
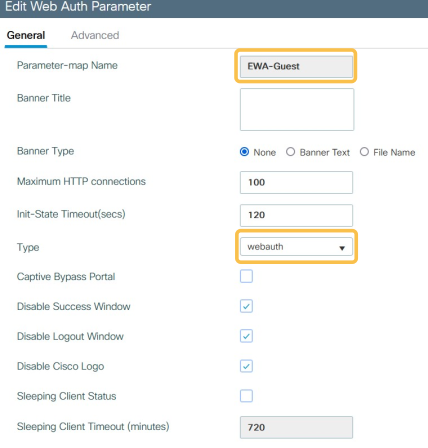
Edit the “General tab” like in the example below:
In the “Advanced” tab, edit the following fields:
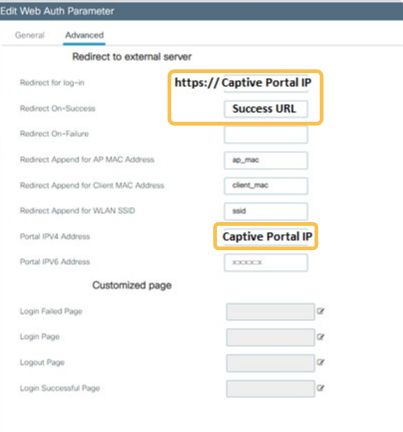
Redirect for log-in: Indicate the Captive Portal URL.
Redirect On-Success: The URL where the guest will be redirected On-Success.
Portal IPV4 Address: Indicate the Captive Portal IP.
You can check how it looks in the “Preview of the Redirect URL” at the top of the view.It could be, for example:
https://fqdn.captive.portal?switch_url=https://192.0.2.1/login.html&redirect=<website-name>&ap_mac=xxxx.xxxx.xxxx&client_mac=xxxx.xxxx.xxxx&ssid=<wlan-name>
Back to the Web Auth Parameter Map view, select the Global parameter:
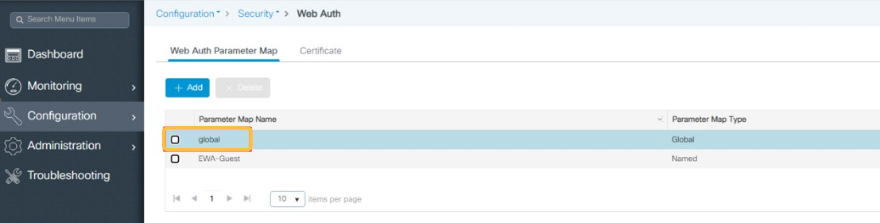
Edit the “General tab” like in the example below:
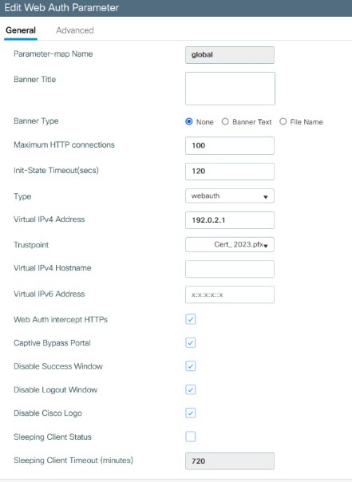
In the “Advanced” tab, edit the same fields as in the named parameter example:

9.2.4.5.2.2. Configuring different WLANs
Go to Menu > Configuration > Tags & Profiles > WLANs:
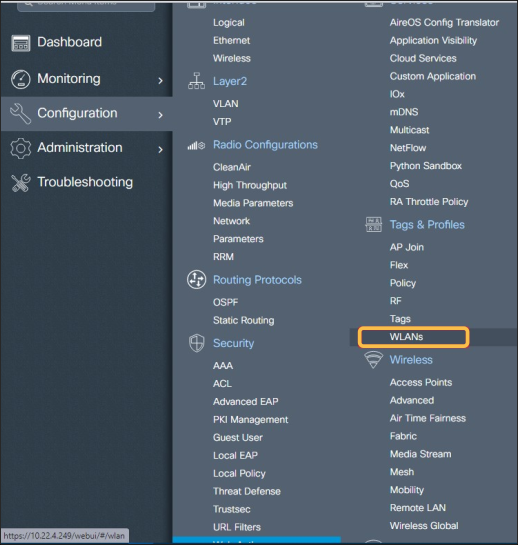
Create a “WLAN_guests”:

Configure the “General” tab:
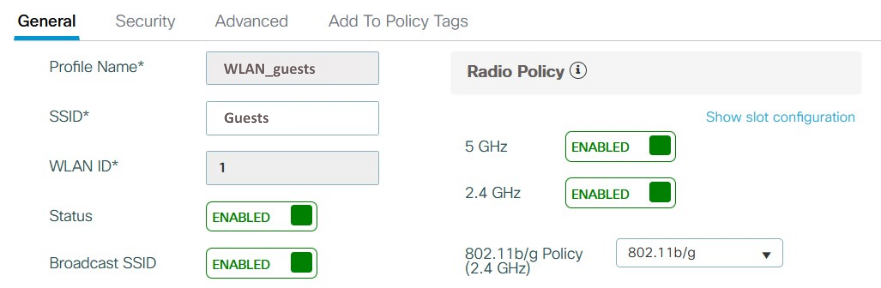
Set the Security > Layer 2 tab like in the example below:
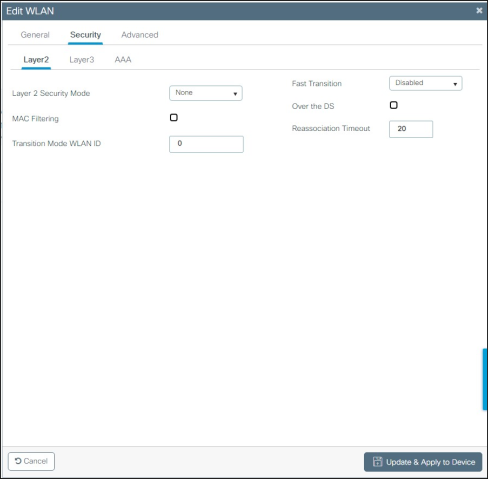
In the Security > Layer 3 tab, click on “Show Advanced Settings”:
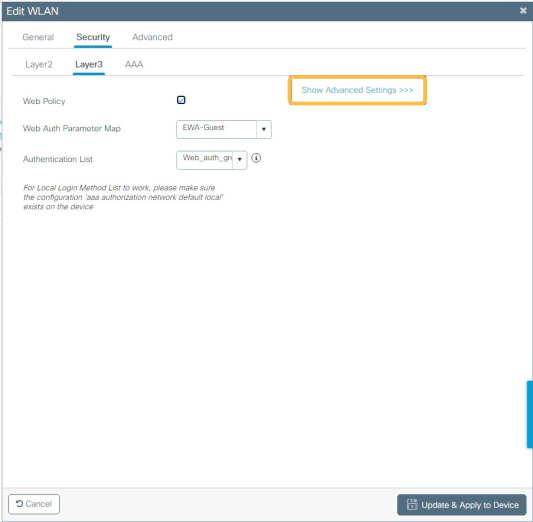
This tab should look like the example below:
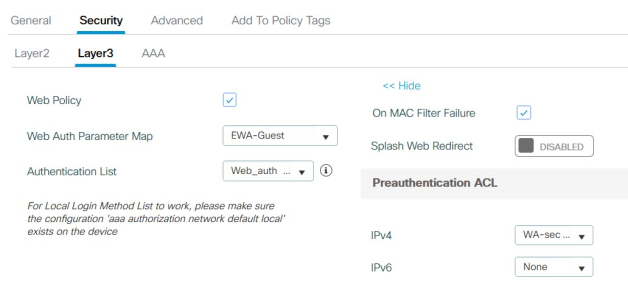
Set the Security > AAA tab like in the example below:
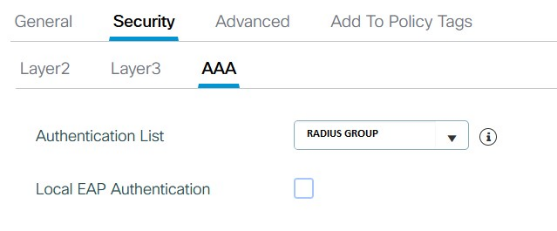
9.2.4.5.2.3. Configuring the AAA security
Go to Menu > Configuration > Security > AAA:
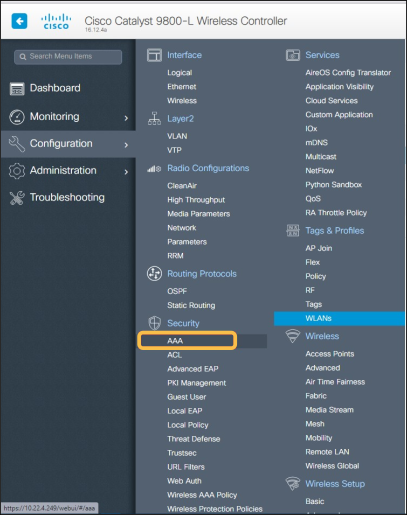
In the Server/Groups > Radius > Servers view:
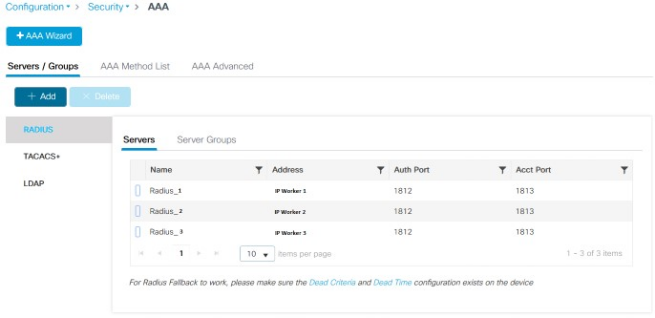
The configuration should look like the example below:
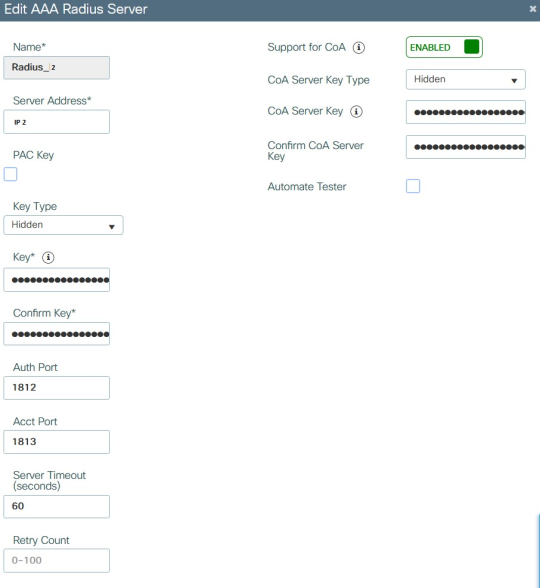
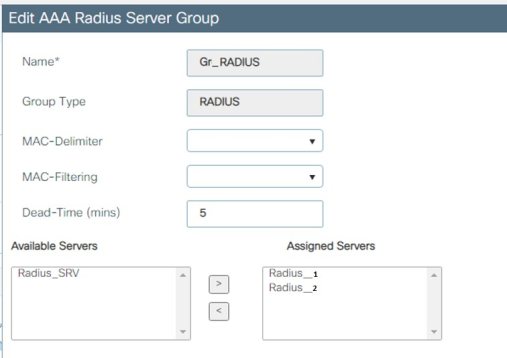
In the Server/Groups > Radius > Server Groups view:
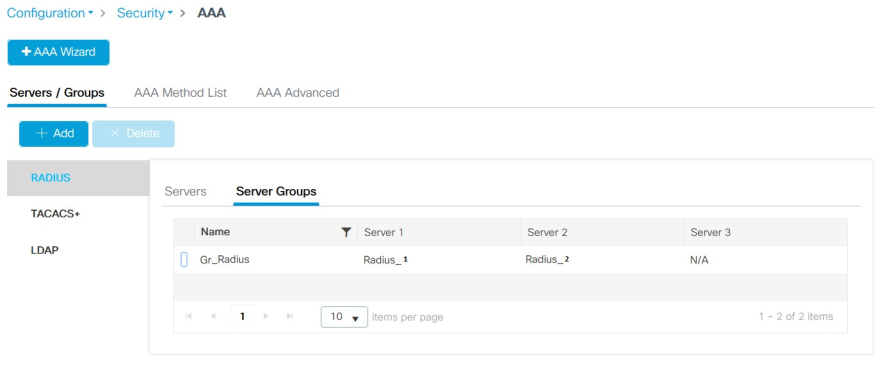
The configuration should look like the example below:
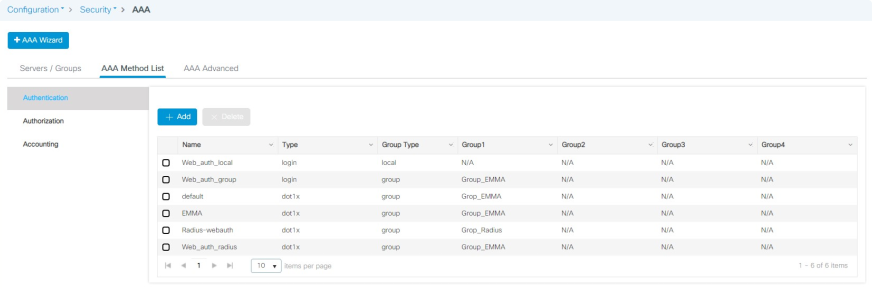
In the AAA Method List > Authentication view:
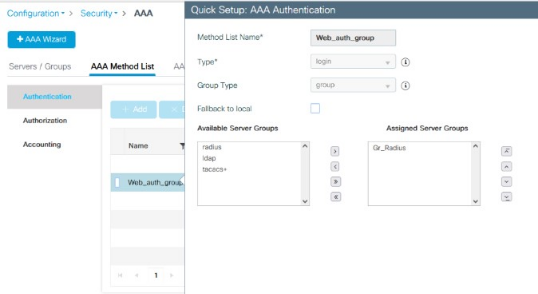
The “Web_auth_group” configuration should look like the example below:
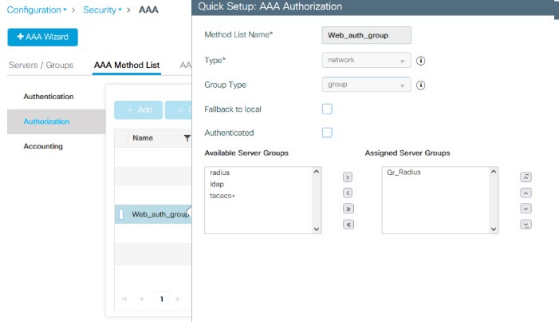
In the AAA Method List > Authorization view, configuration should look like the example below:
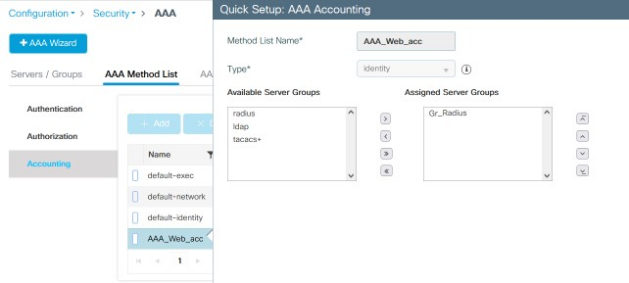
In the AAA Method List > Accounting view, configuration should look like the example below:
In the AAA Advanced tab, the default values of the configuration are supported.
9.2.4.5.3. Aironet 1121, 1130, 1242, 1250, 1600
Note
With this equipment, the same VLAN cannot be shared between two SSIDs. Have this in mind in your design. For example, you need two isolation VLAN if you want to isolate hosts on the public and secure SSIDs. MAC-Authentication + 802.1X configuration
Radio Interfaces:
dot11 vlan-name normal vlan 1
dot11 vlan-name registration vlan 2
dot11 vlan-name isolation vlan 3
dot11 vlan-name guest vlan 5
interface Dot11Radio0
encryption vlan 1 mode ciphers aes-ccm
encryption vlan 2 mode ciphers aes-ccm
ssid OpenNAC-Public
ssid OpenNAC-Secure
interface Dot11Radio0.2
encapsulation dot1Q 2
no ip route-cache
bridge-group 253
bridge-group 253 subscriber-loop-control
bridge-group 253 block-unknown-source
no bridge-group 253 source-learning
no bridge-group 253 unicast-flooding
bridge-group 253 spanning-disabled
interface Dot11Radio0.3
encapsulation dot1Q 3
no ip route-cache
bridge-group 254
bridge-group 254 subscriber-loop-control
bridge-group 254 block-unknown-source
no bridge-group 254 source-learning
no bridge-group 254 unicast-flooding
bridge-group 254 spanning-disabled
interface Dot11Radio0.5
encapsulation dot1Q 5
no ip route-cache
bridge-group 255
bridge-group 255 subscriber-loop-control
bridge-group 255 block-unknown-source
no bridge-group 255 source-learning
no bridge-group 255 unicast-flooding
bridge-group 255 spanning-disabled
LAN interfaces:
interface FastEthernet0.2
encapsulation dot1Q 2
no ip route-cache
bridge-group 253
no bridge-group 253 source-learning
bridge-group 253 spanning-disabled
interface FastEthernet0.3
encapsulation dot1Q 3
no ip route-cache
bridge-group 254
no bridge-group 254 source-learning
bridge-group 254 spanning-disabled
interface FastEthernet0.5
encapsulation dot1Q 5
no ip route-cache
bridge-group 255
no bridge-group 255 source-learning
bridge-group 255 spanning-disabled
Then create the two SSIDs:
dot11 ssid OpenNAC-Secure
vlan 3 backup normal
authentication open eap eap_methods
authentication key-management wpa
dot11 ssid OpenNAC-Public
vlan 2 backup guest
authentication open mac-address mac_methods
mbssid guest-mode
Configure the RADIUS server:
radius-server host 192.168.1.5 auth-port 1812 acct-port 1813 key Testing123
aaa group server radius rad_eap
server 192.168.1.5 auth-port 1812 acct-port 1813
aaa authentication login eap_methods group rad_eap
aaa group server radius rad_mac
server 192.168.1.5 auth-port 1812 acct-port 1813
aaa authentication login mac_methods group rad_mac
5.9.2. Aironet 1600
CoA and radius:
radius-server attribute 32 include-in-access-req format %h
radius-server vsa send accounting
aaa server radius dynamic-author
client 192.168.1.5
server-key 7 Testing123
port 3799
auth-type all
For Aironet 1600
CoA and RADIUS:
radius-server attribute 32 include-in-access-req format %h
radius-server vsa send accounting
aaa server radius dynamic-author
client 192.168.1.5
server-key 7 Testing123
port 3799
auth-type all