9.11. BlastRADIUS Mitigation Fix
9.11.1. What is the BlastRADIUS (CVE-2024-3596)?
The BlastRADIUS CVE is a vulnerability affecting FreeRADIUS. The BlastRADIUS vulnerability allows an attacker to exploit a flaw in the RADIUS software. The Blast-RADIUS attack allows a man-in-the-middle attacker between the RADIUS client and server to forge a valid protocol accept message in response to a failed authentication request. This forgery could give the attacker access to network devices and services without the attacker guessing or brute forcing passwords or shared secrets. The attacker does not learn user credentials.
Note
This vulnerability affects all authentication protocols that do not use EAP (such as PAP, CHAP or MS-CHAP) over UDP. EAP protocols are not affected by this vulnerability.
For more details on the BlastRADIUS, you can visit the Blastradius documentation, which provides comprehensive information about the vulnerability.
9.11.2. Mitigate the vulnerability
In version 1.2.5, we have introduced the necessary changes to mitigate the BlastRADIUS vulnerability. Although these changes are automatically applied in the RADIUS configuration, administrators may need to take additional actions to fully secure the system.
The changes introduced in this version include:
9.11.2.1. Global configuration (/etc/raddb/radius.conf)
In the “security { … }” block, the following variables have been defined:
require_message_authenticator = auto
limit_proxy_state = auto
These two variables affect all clients that do not have them specifically defined in the /etc/raddb/clients.conf file.
require_message_authenticator
Global configuration for requiring Message-Authenticator in all Access-* packets sent over UDP or TCP.
The only way to protect yourself from the BlastRADIUS attack is to update all RADIUS servers, and then set this flag to “yes”. If all RADIUS servers are updated, and if all of them have this flag set to “yes” for all clients, then your network is safe. You can then upgrade the clients when it is convenient, instead of rushing the upgrades.
(Default) “auto” - Automatically determine the value of the flag, based on the first packet received from that client or home_server.
limit_proxy_state: Global configuration for limiting the combination of Proxy-State and Message-Authenticator. This flag only applies to packets sent over UDP or TCP. This flag is ignored for TLS.
(Default) “auto” - Automatically determine the value of the flag, based on the first packet received from that client.
Warning
When these variables are set to “yes” or “auto”, any RADIUS packet that does not meet the defined conditions will be silently discarded.
Review the configuration details in /etc/raddb/radiusd.conf to understand the impact of these settings.
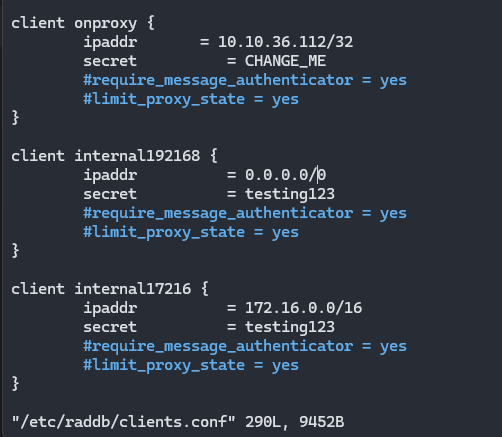
9.11.2.2. RADIUS clients configuration (/etc/raddb/clients.conf)
In the “localhost” client these variables are defined as “yes” to secure the environment in requests coming from the OpenNAC server itself.
In the rest of the clients (devices and networks) these attributes are commented out by default. The global configuration from radius.conf will apply unless you explicitly define behavior for specific networks or devices.
Note
To keep the system secure, it is good practice to always set these attributes to “yes”—especially when handling PAP, CHAP or MS-CHAP requests in the environment (non-EAP requests). This way you can maintain a secure environment.
Only set these attributes to “no” if absolutely necessary, and understand that doing so will make the system insecure.
For more information about the vulnerability and its mitigation, you can consult the official FreeRADIUS security documentation .