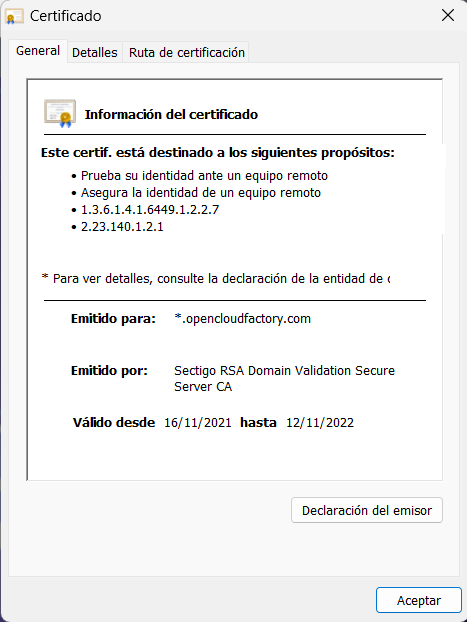
5.2.10.2. HTTPD Certificates Configuration
For web browsers to recognize OpenNAC Enterprise portals as trusted HTTPS sites, it is necessary to load trusted certificates in the web server configuration.
In the Administration Portal, we can upload public or private trust certificates to the organization if they are installed on the computers that access the portal.
In the case of the Captive Portal, it is recommended to install public trust certificates, because devices whose certificates we do not control, are more likely to access it.
The main purpose of this section is to explain how to enable SSL in order to use HTTPS to connect the OpenNAC Enterprise web server.
5.2.10.2.1. Certificate Installation
If we have a valid certificate for this server, we can use it by entering the CRT and KEY files in /etc/httpd/ssl directory:
/etc/httpd/ssl/server.crt
/etc/httpd/ssl/server.key
For testing purposes, we can generate a selfsigned certificate, indicating the days and subject for this certificate. The most important, is the Common Name in the subject; it should match the internet name FQDN:
openssl req -x509 -nodes -days 11499 -subj '/C=ES/ST=Madrid/L=Madrid/CN=opennac.test' -newkey rsa:2048 -keyout /etc/httpd/ssl/server.key -out /etc/httpd/ssl/server.crt
Generate CSR
We can generate a CSR to be signed for a trusted CA, again we have to enter the information.
openssl req -new -newkey rsa:2048 -nodes -keyout opennac.key -out opennac.csr
Generating a 2048 bit RSA private key
..........................................+++
.............+++
writing new private key to 'opennac.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:ES
State or Province Name (full name) []:Madrid
Locality Name (eg, city) [Default City]:Madrid
Organization Name (eg, company) [Default Company Ltd]:OpenCloudFactory
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:LAB0oncore
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
After that, we can export the .csr file or copy and paste the contents of the file.
5.2.10.2.2. Restarting HTTPD
Finally, we have to restart the service:
systemctl restart httpd
5.2.10.2.3. Check Installed Certificate
To verify that the certificate is installed for the HTTPD service, we can access the server’s web portal and check if the installed certificate is displayed:
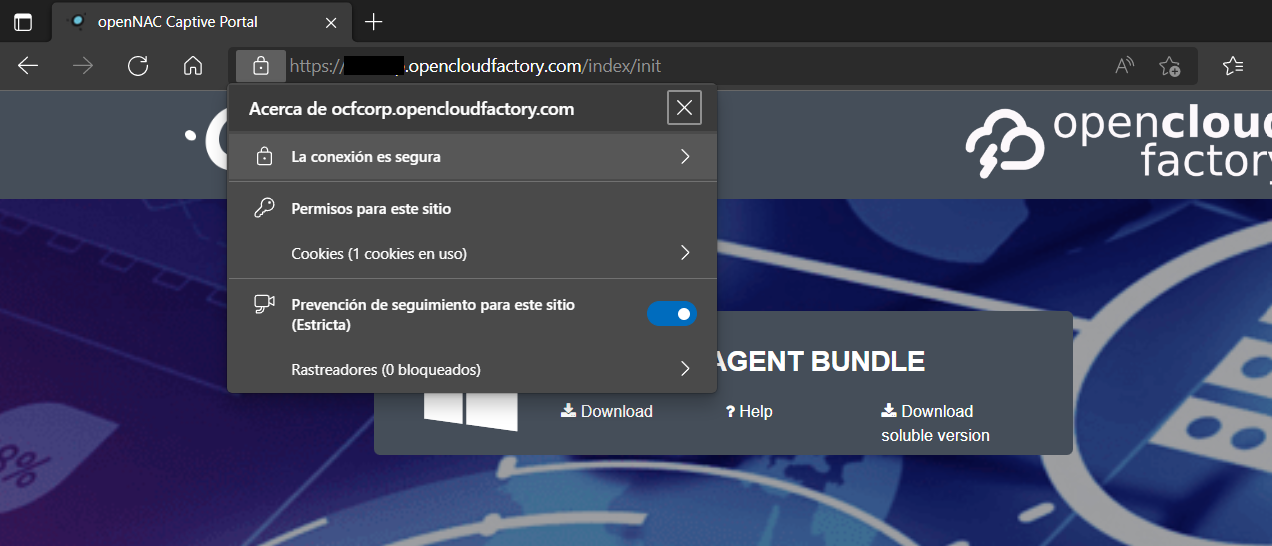
Information about the certificate: