5.2.7. Platform Users
On this section, you can define the users that can access OpenNAC Enterprise.
Go to the Configure > System data > Security > Roles section. There, you can generate console profiles (roles) and associate them to the web console users. This functionally allows administrators to provide different console views for particular uses, by customizing the console access and the permissions given to a particular user.
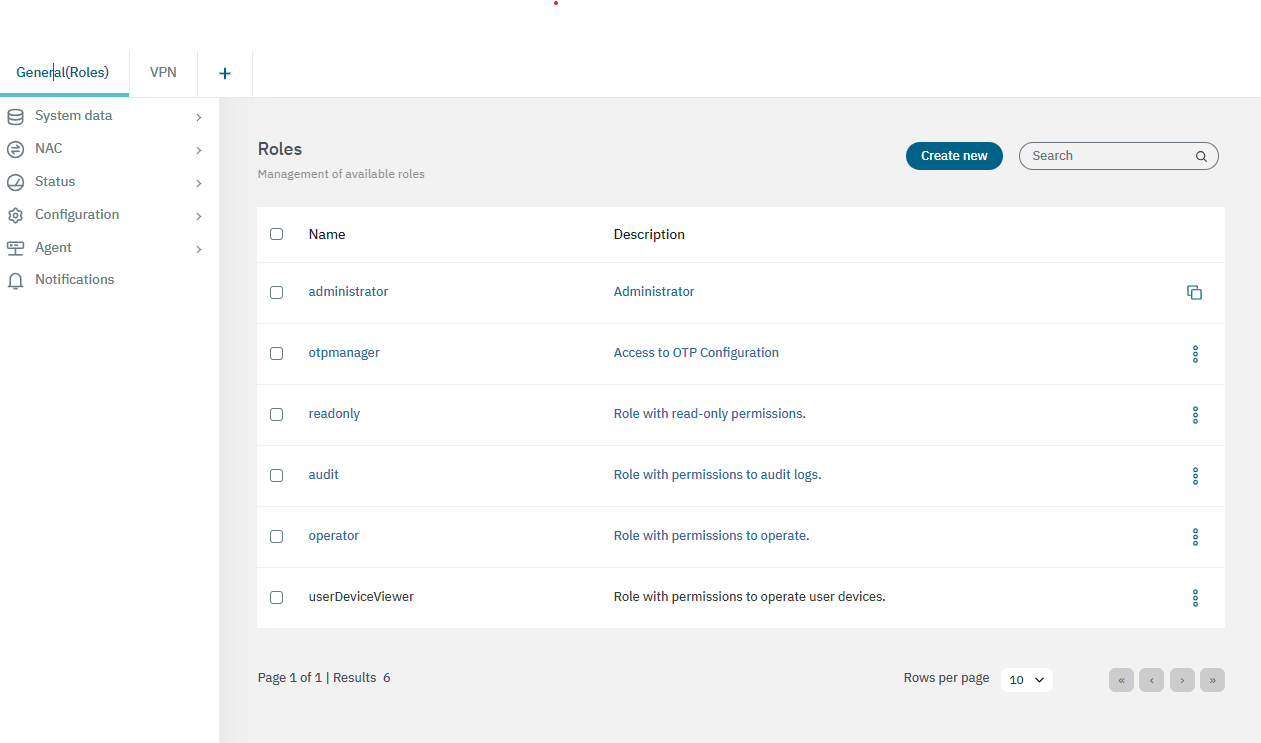
In the Roles section, we can see the default roles with basic permissions. To create a custom role, click the Create new button.
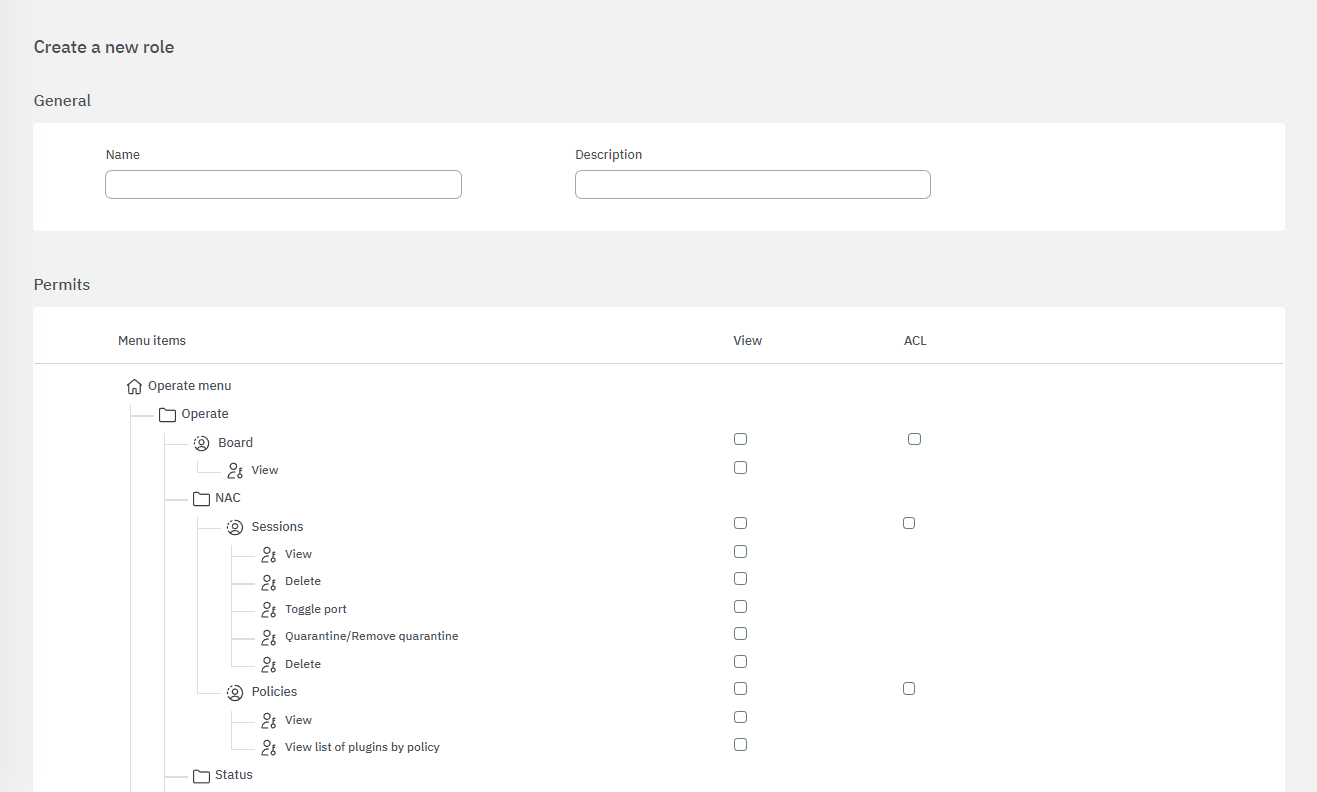
Define the role name and add a description for this role in the General section of this configuration window.
When creating a new role, the minimum permission are assigned through ACLs. To manage those permissions, choose between View or ACL for each web console menu option, by checking the corresponding box in the Permits section. This way, we can manage all the permissions that we want to give to an specific role.
The administrator will be able to enable and disable the different views and menus on the Administration Portal and manage the different ALCs (permissions to edit, add, delete, etc.) and the different sections.
5.2.7.1. Admin Users
From the Configure > System data > Security > Admin users section, you can create and manage administrator users who will have access to the Web Administration Portal. You can create different users and configure parameters such as email, role, phone, etc.
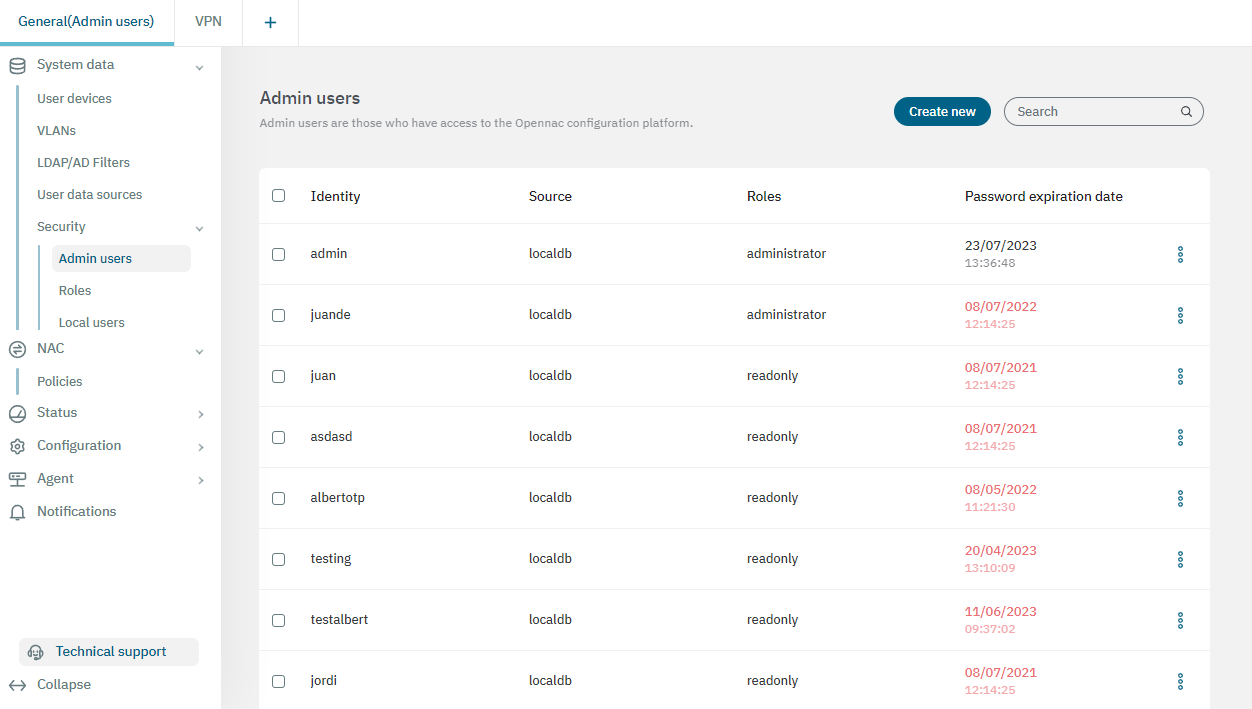
These users can be created from various user data sources, and we have the flexibility to assign them different roles. These roles are utilized to control access to the Web Administration Portal, enabling each user to have distinct permissions when navigating through its different sections. It is necessary to create these roles beforehand.
Note
If a user with a specific role switches to another role, they will automatically be logged out to renew their permissions. The new permissions associated with the assigned role will take effect the next time the user logs in.
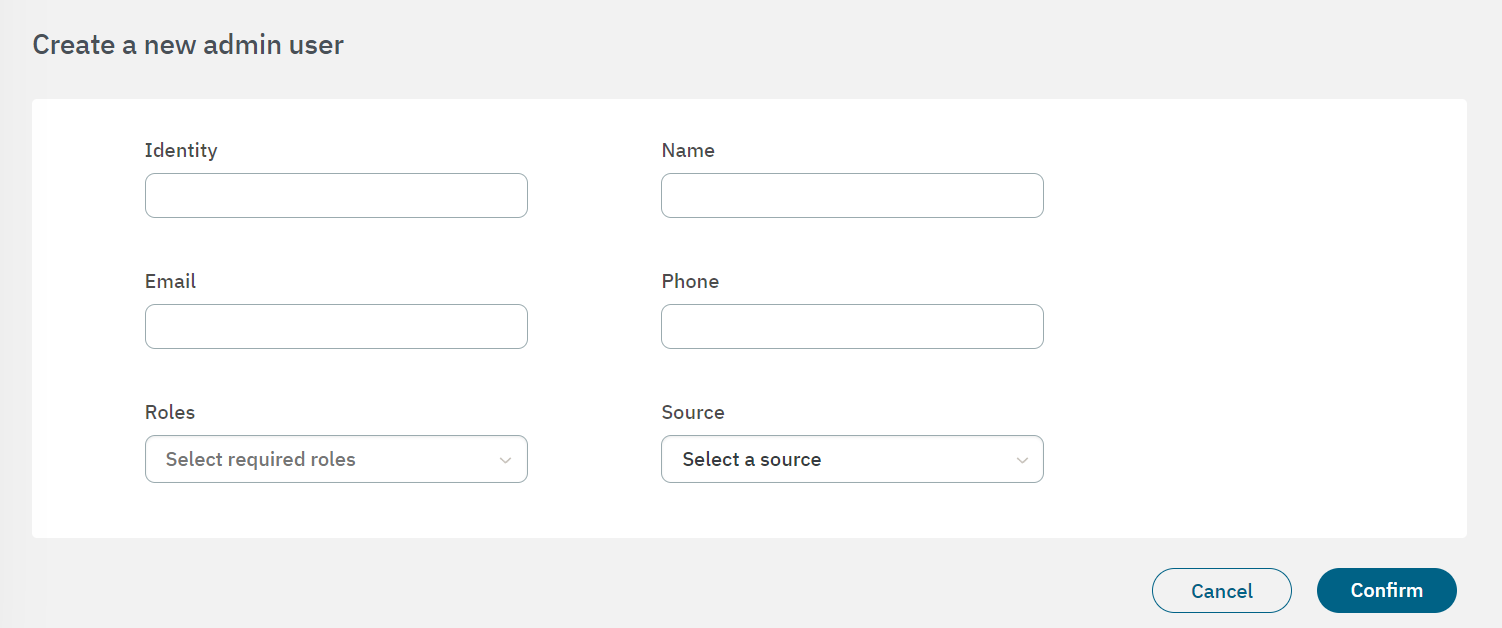
After creating the new user, use the newly configured credentials to log in to the Administration Portal.

5.2.7.2. User Data sources
Multiple user data sources (UDS) can be defined in the OpenNAC Enterprise System data, enabling the system to incorporate different identities in the authorization process. Active Directory attributes are utilized as part of this process. For example, if a user belongs to a specific group in the Active Directory, they can be assigned a different level of access, such as VLANs.
When you have the ON Core added to the domain and a UDS configured, it is possible to define different authorization policies.
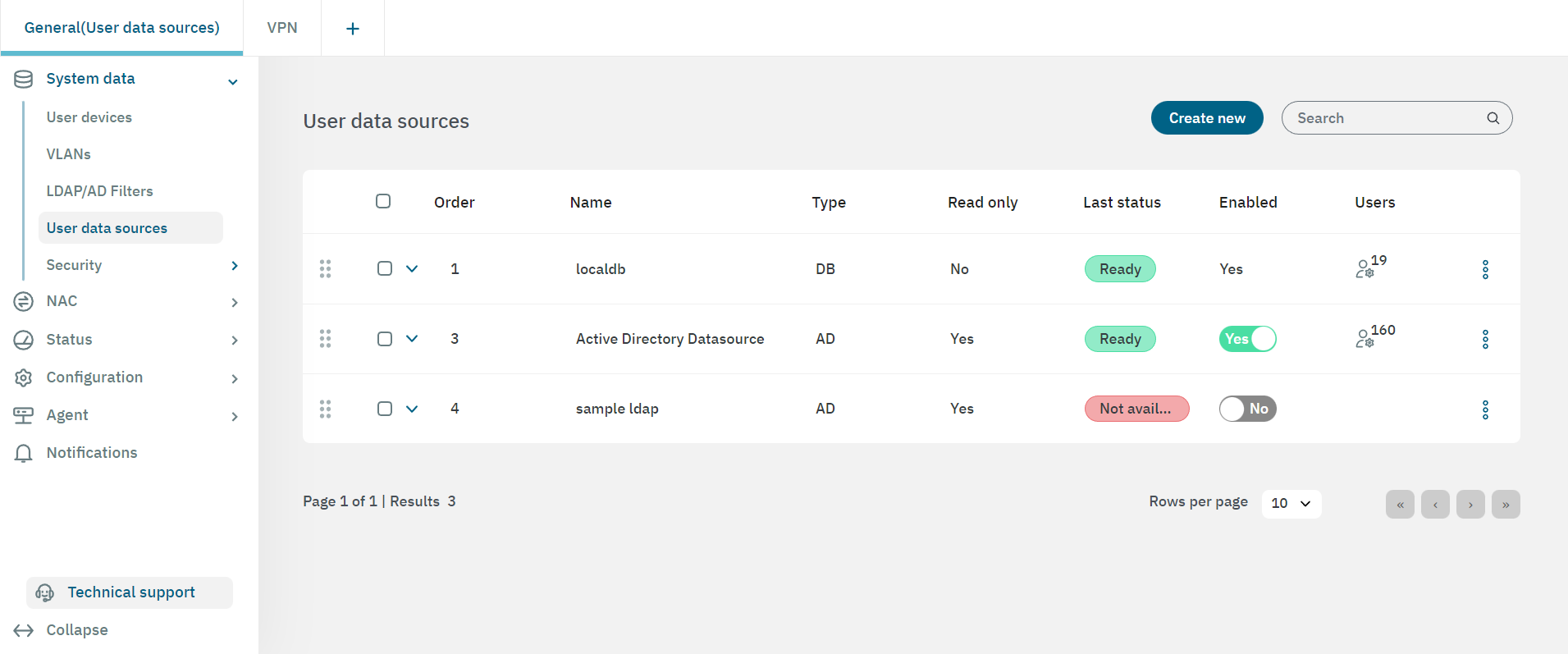
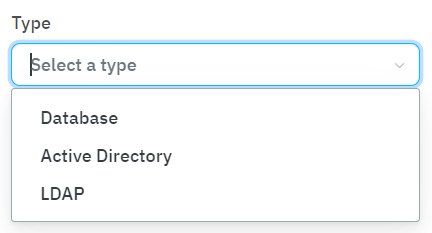
Some of the user data sources that can be defined are:
LocalDB: This is a local database based on MySQL.
Sample ldap: This is a local ldap service that can be used for proof of concepts, is not recommended for productive environments.
Active Directory (optional): This is the connection established with Active Directory.
LDAP Server.
External Database or many others.
To create a new UDS, click on the Create new button. It will display the following window.
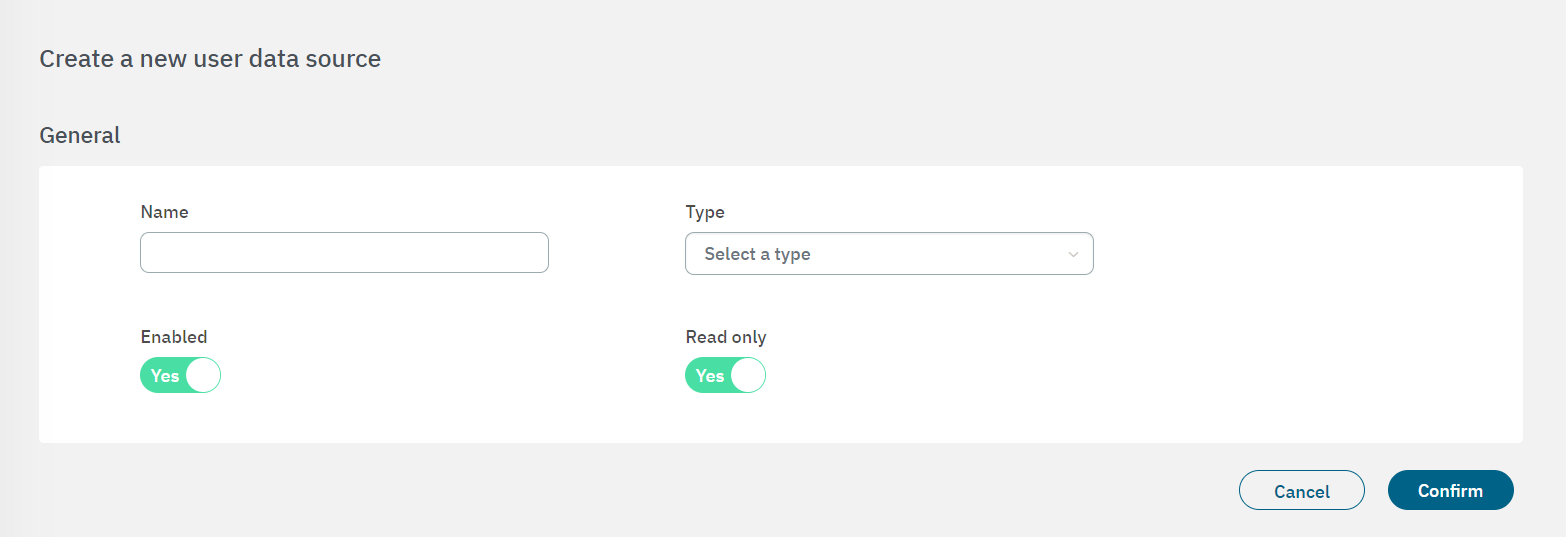
Enter a name for the new UDS and select a type from the three options available:
By selecting the Database type, the following configuration properties will be displayed:
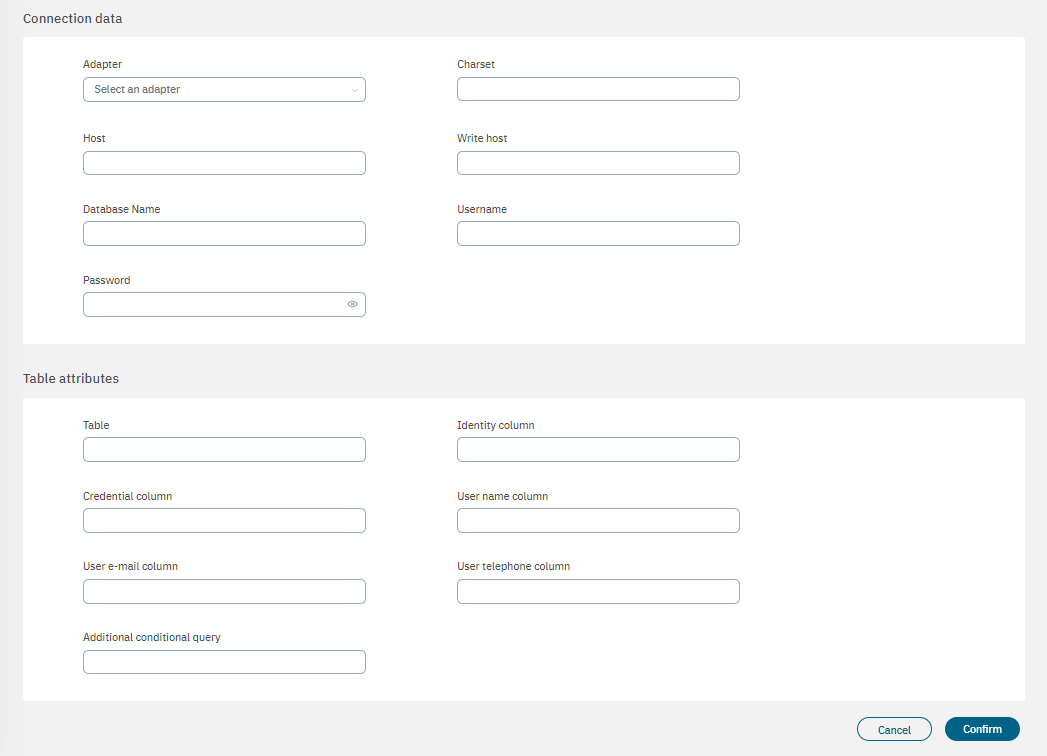
Connection data
Adapter: Select an adapter from MySQL, PostgreSQL, Oracle, or Microsoft SQL server.
Charset: Character encoding format.
Host: Hostname or IP address of the database server.
Write host: Hostname or IP address of the server for write operations.
Database name: Name of the database to connect to.
User name: Name of the user account.
Password: Password for the user account.
Table attributes
Table: Name of the table in the database.
Identity column: Column that represents the identity or unique identifier for records.
Credential column: Column that stores the credential information (if applicable).
User name column: Column that stores the usernames of users.
User e-mail column: Column that stores the email addresses of users.
User telephone column: Column that stores the telephone numbers of users.
Additional conditional query: An optional additional query with specific conditions or criteria for data retrieval.
By selecting a Active Directory or LDAP, the following configuration properties will be displayed:
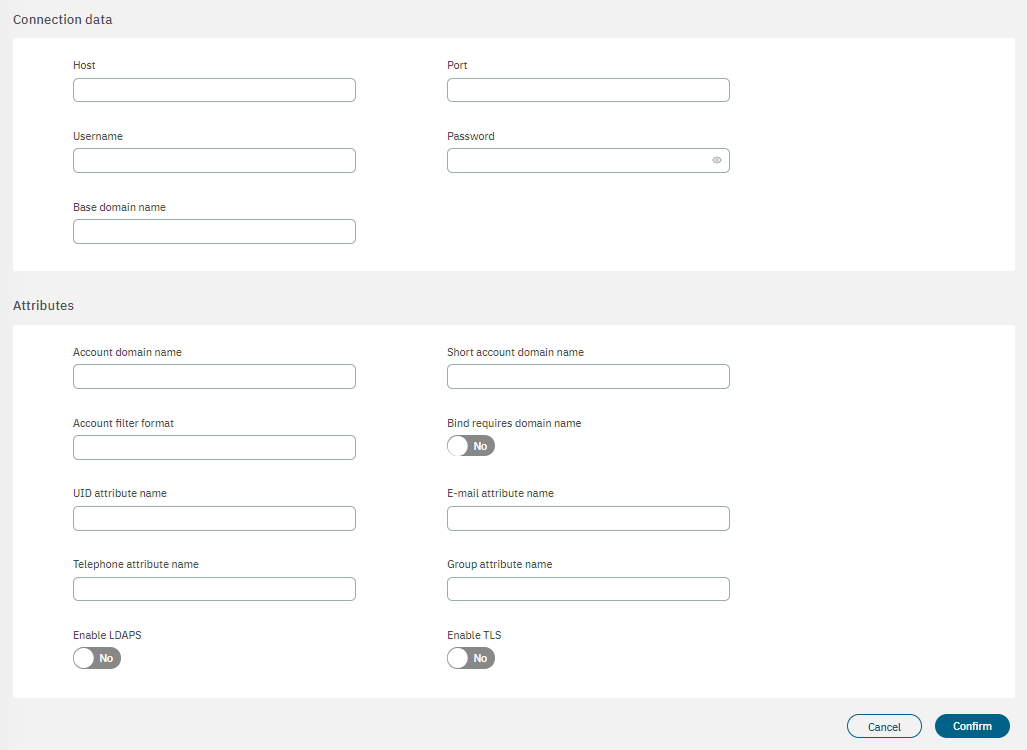
Name: The name used by the UDS. In this case, this is a UDS type LDAP/AD, and for this reason, for instance: AD Mycompany.
Type: Defined as LDAP. The database connection could be used to get user attributes.
Enabled: The UDS can be enabled or disabled.
Read only: If the query is launched with a Read only flag. This will avoid any write action in the commands.
Host: The LDAP/AD IP where the queries are launched. For instance: 172.16.11.5, additional IPs can be added.
Port: The port used for the AD/LDAP Search query, by default, uses an unsecured connection. The default is 389 and if AD/LDAP SSL is enabled is 636.
Username: The user registered in the AD/LDAP server. This allows us to bind and use AD/LDAP information.
Password: The password for the AD/LDAP binding.
Base domain name: BaseDN at the top of the domain name structure. Our domain is named mycompay.local and its BaseDN is DC=mycompany,DC=local.
Account domain name: The DNS name for the domain is in uppercase. In this case MYCOMPANY.LOCAL.
Short account domain name: The short name for the domain or commonly named NETBIOS name. For instance, MYCOMPANY.
Account filter format: The attribute used to select users. We have included two options, but only one must be used. In this example sAMAccountName=%s is defined for Active Directory, and uid=%s for LDAP Servers.
Bind requires domain name: It is basically the credential you are using to authenticate against an LDAP. When using a bindDN, it usually comes with a password associated with it. Sometimes, anonymous binding doesn’t allow certain types of actions.
UID attribute name: The attribute is used to identify users’ IDs. The filter changes depending on if AD or LDAP is used.
E-mail attribute name: The filter is used to identify the email as an attribute of the user.
Telephone attribute name: The filter is used to identify the phone number as an attribute of the user.
Group attribute name: The filter use to identify the groups as an attribute of the user.
Enable LDAPS: For authenticating and authorizing users where LDAP communication is transmitted over an SSL tunnel port 636 TCP.
Enable TLS: For securing communication between LDAP clients and LDAP servers.
5.2.7.3. UDS table
The following fields are displayed in the UDS table:
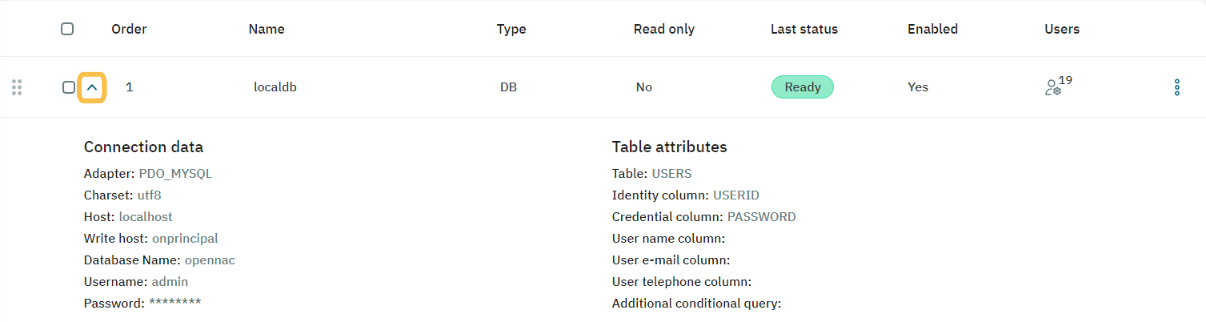
You can check the UDS status, its connection details, and if it is enabled or disabled by clicking on the arrow located at the beginning of each UDS row.
The three-dot icon located at the end of each row, can display the following options:
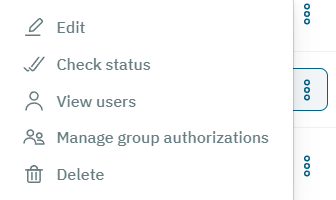
Edit: Edit UDS.
Check status: Check the status of this UDS.
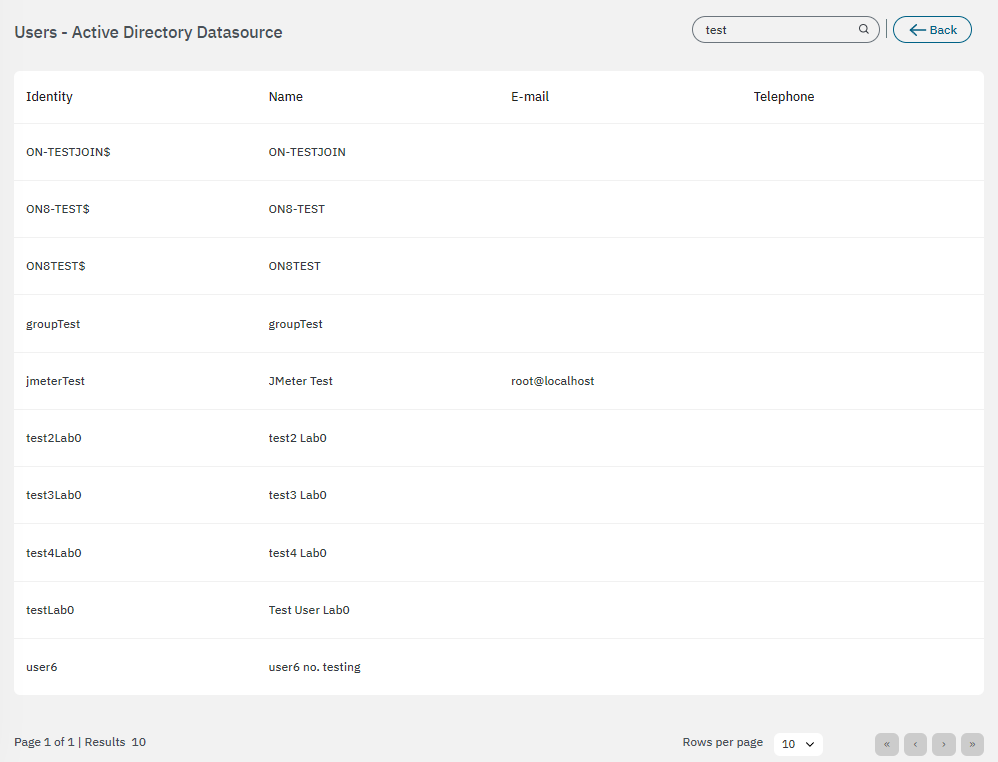
View users: View with a list of users registered in this UDS.
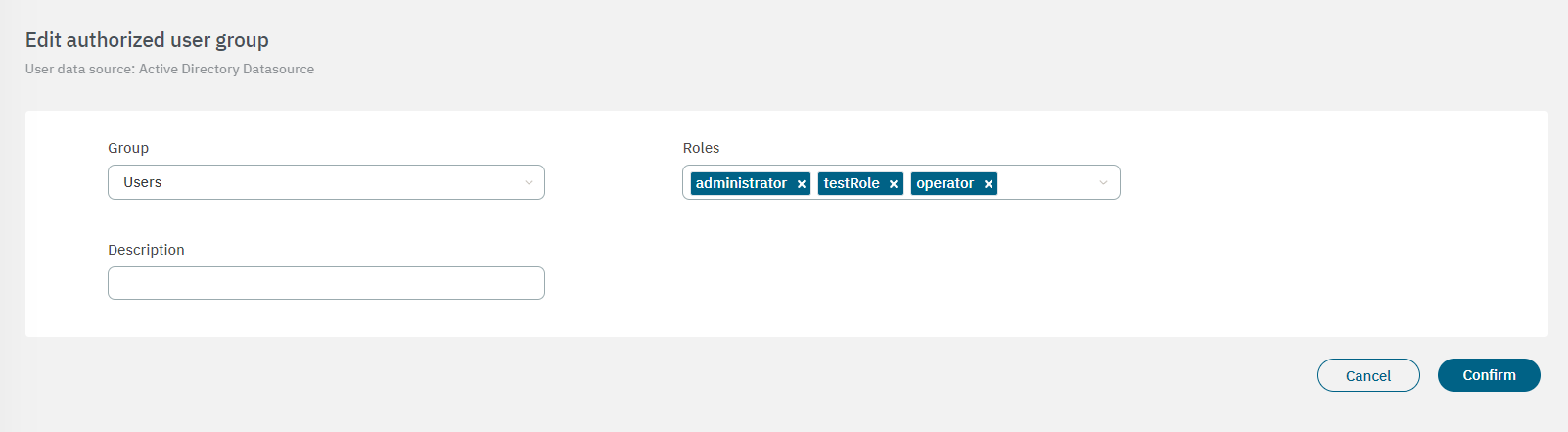
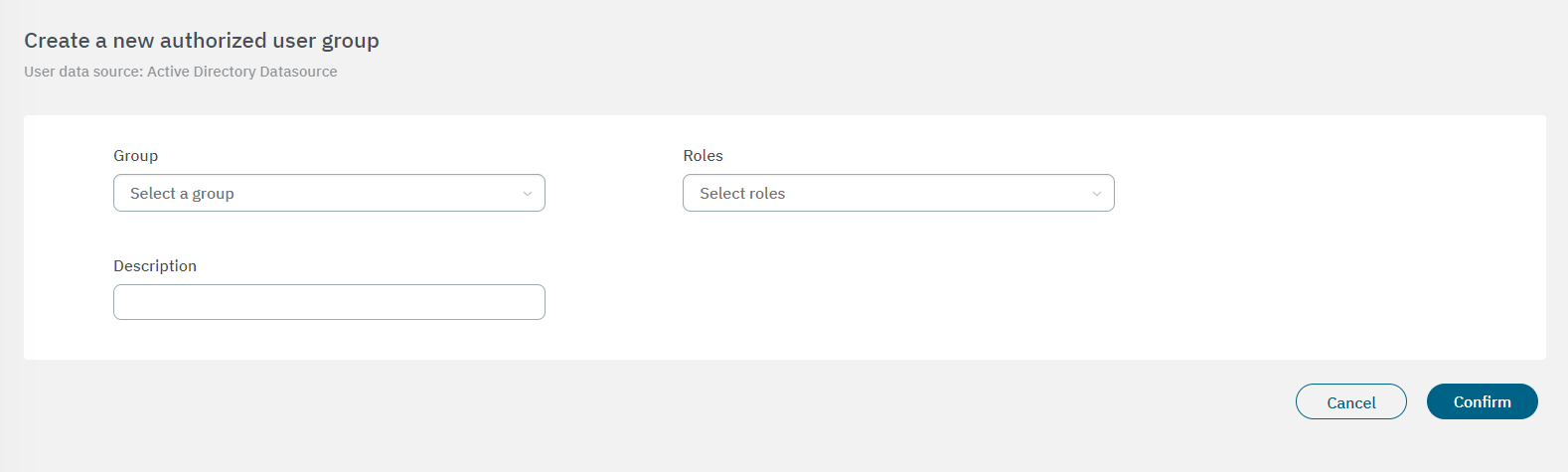
Manage group authorizations: By selecting this option, it will open the Authorized user groups table:
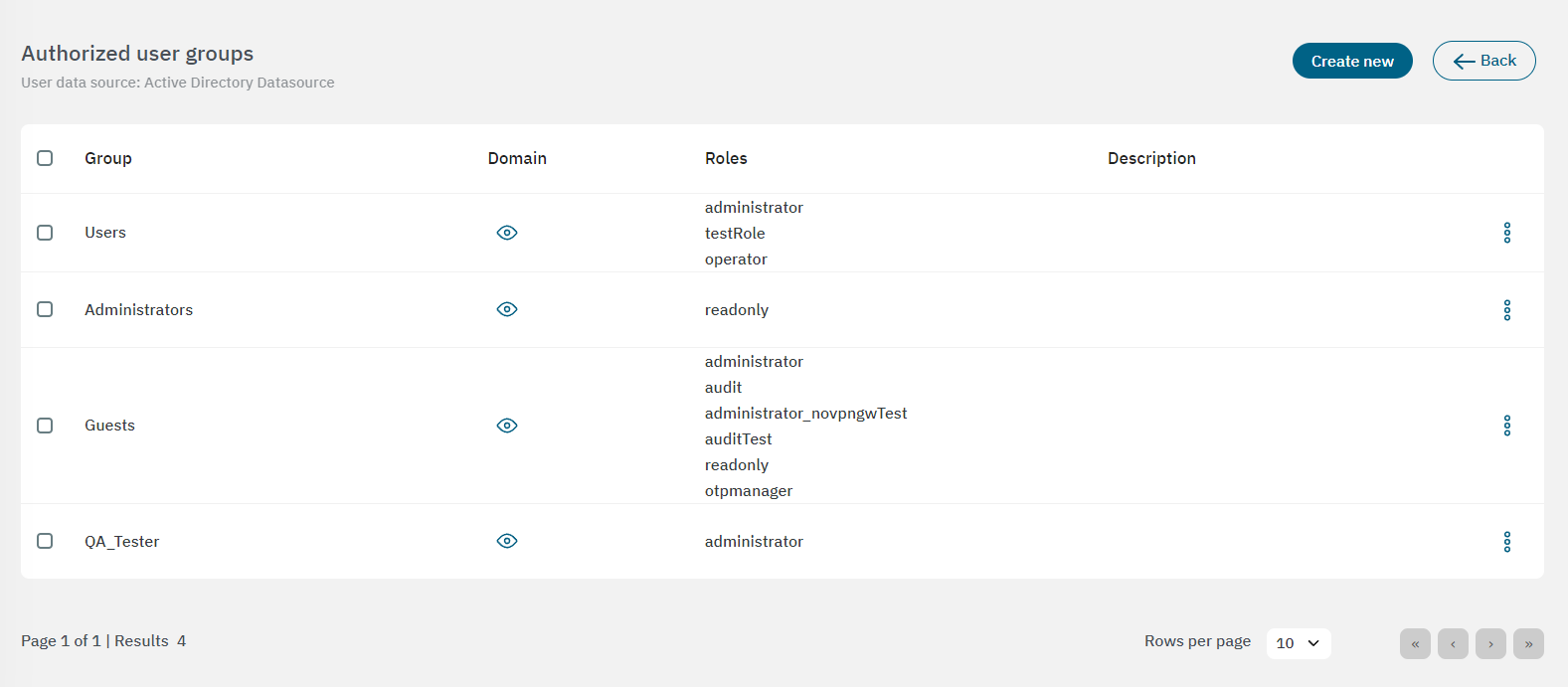
From this view you can edit user groups by selecting the edit option from the three-dot icon dropdown menu.