4.4.2.1. Introduction
Network Device Compliance centralizes and automates the audit of electronic configurations with reference configurations, baselines, or Best Practices. It facilitates the adaptation of the organization with standards and frameworks such as ISO2700x, NIST, ENS, etc., and ensures the secure implementation of NAC technology.
The Network Device Compliance module contributes to the following requirements:
Centralize: Checks of all the electronics are carried out from a single solution and interface, simplifying and accelerating the audit work.
Automate: Checks can be launched on-demand or on a scheduled basis to align with audit tasks.
Facilitates compliance with standards and frameworks: It is possible to implement the necessary configuration verification rules for the adequacy of standards and frameworks.
Ensures secure NAC implementation: It can be ensured that the electronics are correctly configured so that NAC works optimally.
4.4.2.1.1. Basic Concepts for NDC
Here are the fundamental concepts for configuration validation in Network Device Compliance (NDC):
ON CMDB: The Configuration Management Database (CMDB) is a centralized repository that contains all relevant information about the hardware and software components used by the system, including the relationships between those components.
Network Devices (CMDB): Network devices listed in the CMDB are those to which users connect, typically found in the access layer. This includes all configurations related to each device, such as IP addresses, MAC addresses, backup configurations, and connection settings.
Configuration file: To determine how a network device is configured, we must access its configuration. There are two ways to obtain this information, through a direct connection with the device in question, where the configuration will be obtained from the response to a given command, or by accessing the repository where network devices store their configuration in plain text files.
Regular expressions: Regular expressions enable the identification of specific patterns within text. They are essential for detecting and validating configurations of network devices based on their configuration files or backups.
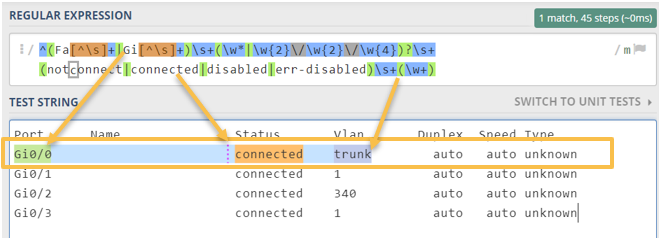
Tags: Tags are labels assigned to network devices in the CMDB that convey important information about each device. In the NDC module, tags are assigned based on the results of evaluated test groups, tests, and rules applicable to the devices.
4.4.2.1.1.1. NDC modes
Network Device Compliance (NDC) operates in two modes:
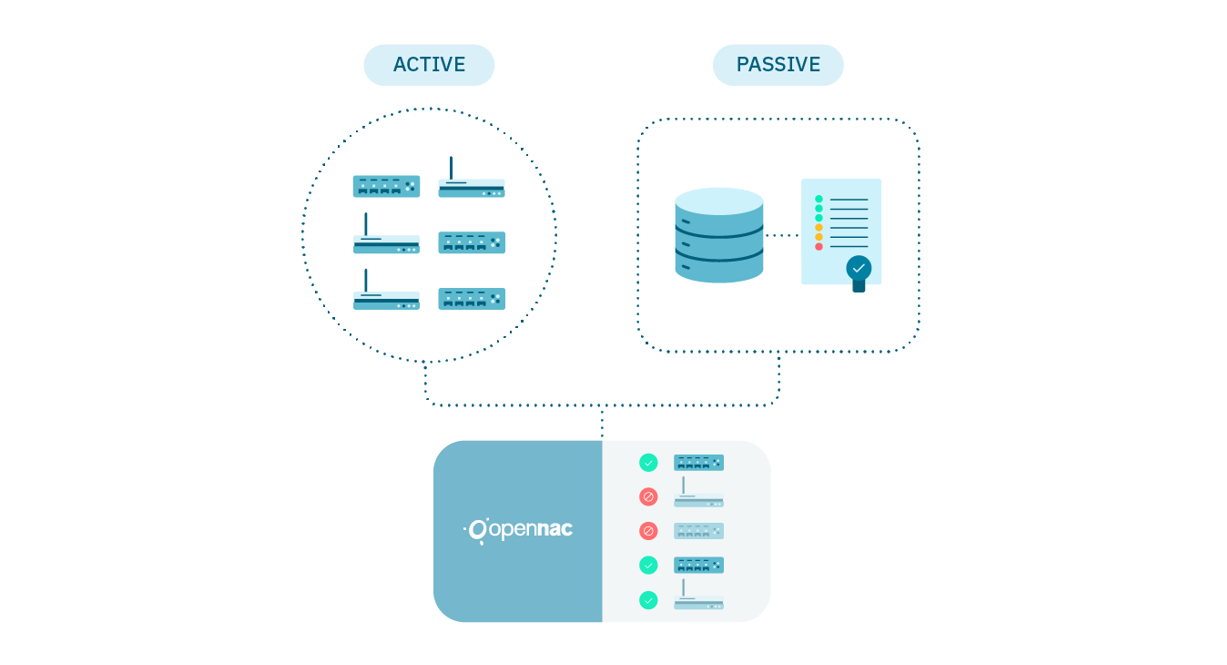
Active Mode: In this mode, NDC can dynamically launch active check rules directly against network devices or statically by first generating a backlog of the configurations to perform the checks later.
Passive Mode: Alternatively, NDC can perform the same compliance checks passively against a configuration repository, without the need to reference the devices in real-time.
4.4.2.1.1.2. Audit in three steps
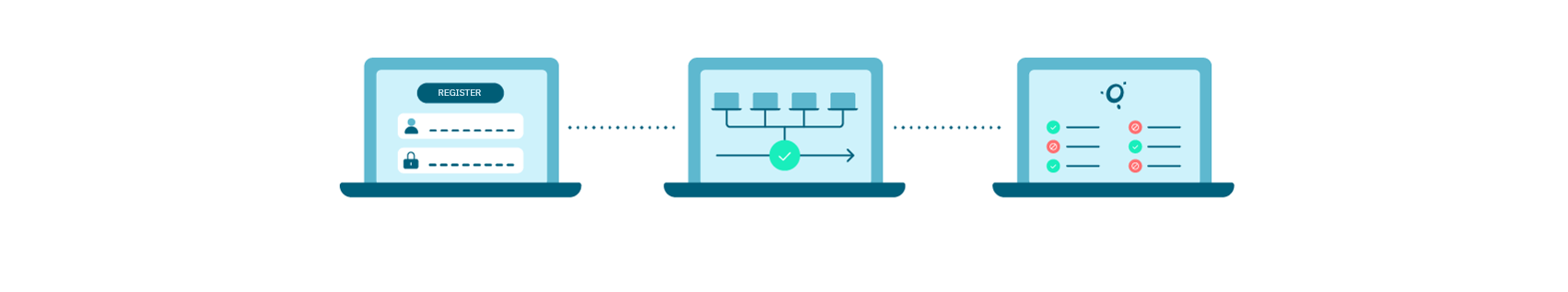
Register: Register a network device using SSH or, in the case of a passive check, establish a repository of configurations via SCP.
Define Rules and Launch: Set the rules and create the corresponding rule groups for individual devices or device groups. You can choose to launch the checks immediately or schedule them for a later time.
Review Results: The results are displayed on centralized dashboards, providing insights into successful checks, failures, findings, and more.