6.1.4. Data Sent to the OpenNAC Core
The Agent sends information to the OpenNAC Core, either to record actions (logs) or to execute actions such as updating data or issuing warnings for specific events.
This section will list the conditions for the information collection to happen, the queries involved, and all the information gathered from the device once the Agent is installed.
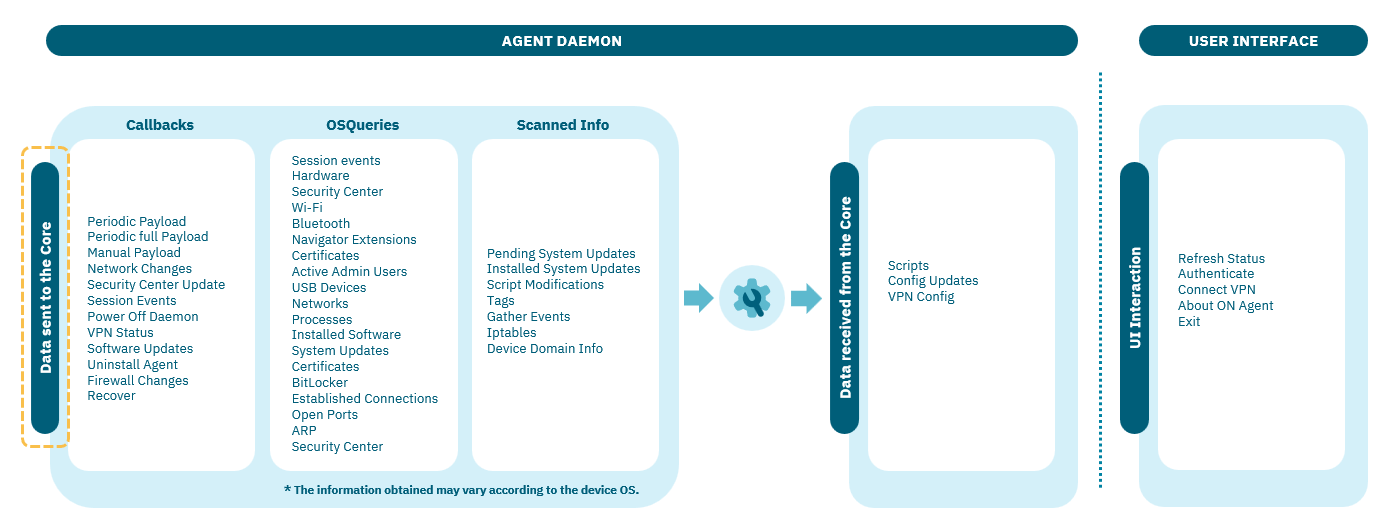
6.1.4.1. Agent callbacks
These are the callbacks that send information to the Core:
Periodic payload: This callback sends all information except the software installed on the device. That information is composed of: session events, active users, USB devices, networks, running processes, certificates, hardware, security center, WIFI, Bluetooth, Google Chrome extensions, Internet Explorer extensions, Firefox extensions, established connections and open ports.
Periodic full payload: The same as the previous case, with the difference that it also sends the device’s software and the processes running in the system. Therefore, it is a full scan that will take longer and should be done less frequently than a normal scan.
Manual payload: In addition to the periodic scans executed by the Agent himself, the user can request a manual scan. In this case all the data also will be sent as a full scan.
Network changes: When a change is detected in the network interfaces, for example, new IP address or new status.
Security Center update: When the security center has been updated (in the case of windows).
Session event: When a user connection or disconnection event has occurred. In some operating systems, also for lock and unlock events.
Software updates: When any changes are made to the software list**: Installation/uninstallation/modification of the current software.
Power Off Daemon: When the Agent is closed by the user or the operating system.
VPN status: The VPN connection status (authenticated,unauthenticated connected, not connected).
Uninstall Agent: The data sent in this event includes information about the uninstallation process.
Firewall changes: When changes are made to the firewall, this event sends data to the Core.
Recover: When the server connection recovers, this event sends data to the Core.
6.1.4.2. Data extracted from devices
This section provides an overview of the different types of information that the Agent extracts from a device on which it is installed and sends to the Core server.
These payloads sent to the Core look similar to the following sample. Since it can be quite long, we have used variables for the Queries to shorten it. These variables, for instance $ACTIVE_ADMIN_USERS, contain a JSON object that we will detail later.
Payload sample
{
"ACCOUNTINFO": {
"KEYNAME": "TAG",
"KEYVALUE": "6141a608712463f232fa9d0d61b2a36c"
},
"OPENNAC": {
"UID": "0a12ea58ba85",
"TIMESTAMP": "1713350096",
"TYPE": "service",
"PLATFORM": "WINDOWS",
"VERSION": "102.04.02005",
"MONITOR_TYPE": "Full",
"USED_INTERFACE_IP": "10.21.33.131",
"TOKEN": null,
"SERVICE_STOPPED": false,
"SERVICE_INSTALLED": true,
"AGENT_UPDATE_FAILED": false,
"USER_ACCOUNT":"my-account@opencloudfactory.com"
"CHOSEN_SERVER": "dc-sta-qa.opencloudfactory.com",
"SYSTEM_UPDATES_ACTIVE": true,
"SYSTEM_UPDATED": false,
"SYSTEM_BUILD_NUMBER": "19045.3930",
"SCRIPTS_MODIFICATIONS": true
},
"QueryResults": {
$ACTIVE_ADMIN_USERS,
$OPEN_PORTS,
$SOFTWARES,
$USER_ACTIVE,
$USER_ACTIVE,
$IE_EXT,
$FIREFOX_EXT,
$ESTABLISHED_CONNECTIONS,
$BITLOCKER,
$CHROME_EXT,
$PROCESSES,
$NETWORKS,
$SECURITY_CENTER
$HARDWARE
$NETWORKS
$CERTIFICATE
},
"GATHEREVENTS": {
"GATHER_EVENT_ID": "cd79775d-059d-4f24-a21a-265e9d77fbc5",
"GATHER_START_DATE_TIME": "2024-04-17T10:34:27.2529249Z",
"GATHER_END_DATE_TIME": "2024-04-17T10:34:36.5884993Z",
"GATHER_CPU_PERCENTAGE": 0.96,
"GATHER_MEMORY_CONSUMPTION": 1875184
},
"TRIGGERTYPE": 3,
"TRIGGERDATETIME": "2024-04-17T10:34:54.950368Z",
"SCRIPTEXECUTIONRESULTS": {
"INIGO_WIN_1": {
"SCRIPT": "descripcion1 modificado",
"RESULT": false,
"STDOUT": "",
"STDERR": "descripcion1 : The term 'descripcion1' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.At C:\\WINDOWS\\TEMP\\8b817d92169543e2b2397615a15c8735.ps1:1 char:1+ descripcion1 modificado+ ~~~~~~~~~~~~ + CategoryInfo : ObjectNotFound: (descripcion1:String) [], CommandNotFoundException + FullyQualifiedErrorId : CommandNotFoundException ",
"START_TIME": "2024-04-17T10:34:54.95379Z",
"END_TIME": "2024-04-17T10:34:56.2197323Z"
}
},
"TAGS": [...
],
"SCANNED_NETWORKS": null,
"PENDING_SYSTEM_UPDATES": [...
],
"INSTALLED_SYSTEM_UPDATES": [...
],
"SCRIPTS_MODIFICATIONS": {...
},
"IPTABLES": null
}
OPENNAC
This JSON object provides useful information to OpenNAC Enterprise about the Agent and the device on which it is running.
UID: Unique identifier of the agent.
TIMESTAMP: Timestamp in which the agent payload is generated.
TYPE: The type of VLAN associated with the agent’s connection to the server.
PLATFORM: Platform running the Agent.
VERSION: Agent version.
MONITOR_TYPE: Monitor type.
USED_INTERFACE_IP: IP address of the interface used by the agent.
TOKEN: Token generated to verify if the agent comes from a trusted source (registered agent) or not. If the agent is not registered yet, then this parameter will not exist in the payload.
SERVICE_STOPPED: Whether the Agent service has stopped or not.
SERVICE_INSTALLED: Whether the Agent service is installed or not.
AGENT_UPDATE_FAILED: Whether the Agent update has failed or not.
CHOSEN_SERVER: The server from where the Agent was downloaded.
SYSTEM_UPDATES_ACTIVE: Whether the Agent update is active or not.
SYSTEM_UPDATED: Whether the Agent has been updated.
SYSTEM_BUILD_NUMBER: The Agent build number.
SCRIPTS_MODIFICATIONS: Whether there was a script modification or not.
6.1.4.2.1. Query Results
This QueryResults object within the payload contains all the OSQuery executed by the Agent. Each query will result in objects containing information about the network interfaces, information regarding the hardware of the device, etc.
6.1.4.2.1.1. User active

This entity is very simple; it only contains the name of the domain and the user who is currently logged into the device. In this way, we can identify in the Core which user is using that device with a specific MAC and IP interface.
},
"USER_ACTIVE": {
"Results": [
{
"DOMAIN": "STD2-V07",
"NAME": "ocf"
}
],
"GATHER_EVENT_ID": "cd79775d-059d-4f24-a21a-265e9d77fbc5",
"GATHER_START_DATE_TIME": "2024-04-17T10:34:27.2609363Z",
"GATHER_END_DATE_TIME": "2024-04-17T10:34:30.2873639Z",
"GATHER_CPU_PERCENTAGE": 1.15,
"GATHER_MEMORY_CONSUMPTION": 959024
},
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
NAME |
User login name |
juan |
DOMAIN |
Remote hostname |
DESKTOP-77FMN5B |
6.1.4.2.1.2. Active admin user

This entity is also simple; it only contains the name of the group which the user belongs and the user who is currently logged into the device. In this way, we can identify in the Core if the user has the administrator role.
},
"QueryResults": {
"ACTIVE_ADMIN_USERS": {
"Results": [
{
"GROUPNAME": "Administrators",
"NAME": "ocf"
}
],
"GATHER_EVENT_ID": "cd79775d-059d-4f24-a21a-265e9d77fbc5",
"GATHER_START_DATE_TIME": "2024-04-17T10:34:27.2684474Z",
"GATHER_END_DATE_TIME": "2024-04-17T10:34:29.9913556Z",
"GATHER_CPU_PERCENTAGE": 1.0,
"GATHER_MEMORY_CONSUMPTION": 919528
},
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
GROUP NAME |
The name of the administrator group which identifies this user as an admin user. |
administrators |
NAME |
User login name. |
Juan |
6.1.4.2.1.3. Open ports

This entity is formed by a list of open network sockets in the system. Those are only LISTEN state connections.
"OPEN_PORTS": {
"Results": [
{
"FAMILY": "2",
"LOCAL_ADDRESS": "0.0.0.0",
"LOCAL_PORT": "22",
"PID": "3004",
"PROTOCOL": "6",
"REMOTE_ADDRESS": "0.0.0.0",
"REMOTE_PORT": "0",
"STATE": "LISTEN"
},
...
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
PID |
Process ID |
1716 |
FAMILY |
Network protocol (IPv4, IPv6) |
2 |
PROTOCOL |
Transport protocol (TCP/UDP) |
6 |
LOCAL_ADDRESS |
Socket local address |
0.0.0.0 |
REMOTE_ADDRESS |
Socket remote address |
0.0.0.0 |
LOCAL_PORT |
Socket local port |
135 |
REMOTE_PORT |
Socket remote port |
0 |
STATE |
TCP state |
LISTEN |
6.1.4.2.1.4. ARP

This entity is formed by the association between IP addresses and their corresponding MAC addresses.
"ARP": {
"Results": [
{
"ADDRESS": "10.21.156.1",
"INTERFACE": "00:ff:37:fd:47:6f",
"MAC": "00:FF:38:FD:47:6F",
"PERMANENT": "0"
},
{
"ADDRESS": "192.168.1.1",
"INTERFACE": "88:78:73:fc:3a:82",
"MAC": "E0:19:54:BD:DA:8F",
"PERMANENT": "0"
}
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
ADDRESS |
IP address of the device |
192.168.1.1 |
INTERFACE |
MAC address of the device’s network interface. |
88:78:73:fc:3a:82 |
MAC |
Unique identifier for the network interface. |
E0:19:54:BD:DA:8F |
PERMANENT |
Indicates if the ARP entry is static (1) or dynamic (0). |
0 |
6.1.4.2.1.5. Softwares

The software or applications installed on a device provide valuable information that can be extracted for various purposes. Knowing the applications and their versions enables the generation of tags and facilitates device compliance assessment. If an application on a device has a version lower than the minimum expected, it will be classified as non-compliant. Additionally, these applications assist in identifying pending operating systems updates that the user needs to install.
"SOFTWARES": {
"Results": [
{
"INSTALLDATE": "UNKNOWN",
"ISUPDATE": "0",
"NAME": "",
"PUBLISHER": "Microsoft Corporation",
"VERSION": ""
},
{
"INSTALLDATE": "UNKNOWN",
"ISUPDATE": "0",
"NAME": "Notepad++ (64-bit x64)",
"PUBLISHER": "Notepad++ Team",
"VERSION": "8.5.8"
},
...
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
ISUPDATE |
If it is a Windows Update (1) or not (0) |
0 |
NAME |
Application name |
Microsoft Visual C 2005 Redistributable |
VERSION |
Application version |
8.0.61001 |
PUBLISHER |
Application manufacturer |
Microsoft Corporation |
INSTALLDATE |
Installation date |
11/17/2017 |
6.1.4.2.1.6. Bitlocker

This entity contains information about the execution of this disk encryption (BitLocker) feature when enabled in Windows operating systems.
"BITLOCKER": {
"Results": [
{
"CONVERSION_STATUS": "0",
"DEVICE_ID": "\\\\?\\Volume{fa9100bc-0000-0000-0000-501f00000000}\\",
"DRIVE_LETTER": "C:",
"ENCRYPTION_METHOD": "None",
"LOCK_STATUS": "0",
"PERCENTAGE_ENCRYPTED": "0",
"PERSISTENT_VOLUME_ID": "",
"PROTECTION_STATUS": "0",
"VERSION": "0"
}
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
CONVERSION_STATUS |
The bitlocker conversion status of the drive |
0 |
DEVICE_ID |
ID of the encrypted drive. |
\\?\Volume{eeebe104-4340-4d0a-9342-75f95cf75a77}\ |
DRIVE_LETTER |
Drive letter of the encrypted drive. |
C |
ENCRYPTION_METHOD |
The encryption type of the device. |
None |
LOCK_STATUS |
The accessibility status of the drive from Windows |
0 |
PERCENTAGE_ENCRYPTED |
The percentage of the driver that is encrypted. |
0 |
PERSISTENT_VOLUME_ID |
Persistent ID of the device. |
11/17/2017 |
PROTECTION_STATUS |
The bitlocker protection status of the device. |
0 |
VERSION |
The FVE metadata version of the drive. |
0 |
6.1.4.2.1.7. Internet Explorer extensions

The IE_EXT entity retrieves the services that have been given permissions in you Internet Explorer browser.
"IE_EXT": {
"Results": [
{
"EXTENSION_ID": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Browser Helper Objects\\{1FD49718-1D00-4B19-AF5F-070AF6D5D54C}",
"NAME": "IEToEdge BHO",
"PATH": "C:\\Program Files (x86)\\Microsoft\\Edge\\Application\\121.0.2277.106\\BHO\\ie_to_edge_bho_64.dll",
"VERSION": "121.0.2277.106"
},
{
"EXTENSION_ID": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Browser Helper Objects\\{1FD49718-1D00-4B19-AF5F-070AF6D5D54C}",
"NAME": "",
"PATH": "",
"VERSION": ""
},
...
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
EXTENSION_ID |
Extension identifier (folder name) |
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionExplorerBrowser Helper Objects{1FD49718-1D00-4B19-AF5F-070AF6D5D54C} |
NAME |
Extension name |
Slides |
PATH |
Path of the extension |
C:Program Files (x86)MicrosoftEdgeApplication123.0.2420.97BHOie_to_edge_bho_64.dll |
VERSION |
Extension version |
0.10 |
6.1.4.2.1.8. Firefox extensions

The FIREFOX_EXT entity retrieves the services that have been given permissions in you Firefox browser.
"FIREFOX_EXT": {
"Results": [
{
"ACTIVE": "1",
"EXTENSION_ID": "jid1-FkPKYIvh3ElkQO@jetpack",
"INSTALLATION_URL": "https://addons.mozilla.org/firefox/downloads/file/3654313/signtextjs_plus-0.9.6.xpi",
"NAME": "signTextJS plus",
"PATH": "C:\\Users\\inigo\\AppData\\Roaming\\Mozilla\\Firefox\\Profiles\\lotmkc2g.default-release-1675862288206\\extensions\\jid1-FkPKYIvh3ElkQO@jetpack.xpi",
"PUBLISHER": "null",
"USERNAME": "inigo",
"USER_ID": "1001",
"VERSION": "0.9.6",
"description": "window.crypto.signText support and enhancements"
},
...
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
ACTIVE |
Extension status |
1 |
ID |
Extension identifier |
|
INSTALLATION_URL |
URL from where the extension was installed |
https://addons.mozilla.org/firefox/downloads/file/1167275/google_translator_for_firefox-3.0.3.3.xpi |
NAME |
Extension name |
Google Translator for Firefox |
PATH |
Path of the extension |
C:UsersinigoAppDataRoamingMozillaFirefoxProfileslotmkc2g.default-release-1675862288206extensionstranslator@zoli.bod.xpi |
PUBLISHER |
Extension publisher |
null |
USER_NAME |
name of the user |
juan |
USER_ID |
ID of the user |
1001 |
VERSION |
Extension version |
3.0.3.3 |
DESCRIPTION |
Description of the extension |
Translate the selected text and the full page with Google Translate. |
6.1.4.2.1.9. Chrome extensions

The CHROME_EXT entity retrieves the services that have been given permissions in you Google Chrome browser.
"CHROME_EXT": {
"Results": [
{
"EXTENSION_ID": "ghbmnnjooekpmoecnnnilnnbdlolhkhi",
"NAME": "Google Docs Offline",
"PATH": "C:\\Users\\ocf\\AppData\\Local\\Google\\Chrome\\User Data\\Default\\Extensions\\ghbmnnjooekpmoecnnnilnnbdlolhkhi\\1.62.0_0",
"USERNAME": "ocf",
"USER_ID": "1001",
"VERSION": "1.62.0",
"description": "Edit, create, and view your documents, spreadsheets, and presentations — all without internet access."
},
...
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
ID |
Extension identifier |
ghbmnnjooekpmoecnnnilnnbdlolhkhi |
NAME |
Extension name |
Google Docs Offline |
PATH |
Path of the extension |
C:UsersgaraziAppDataLocalGoogleChromeUser DataDefaultExtensionsghbmnnjooekpmoecnnnilnnbdlolhkhi1.73.6_0 |
USER_NAME |
name of the user |
juan |
USER_ID |
ID of the user |
1001 |
VERSION |
Extension version |
1.73.6 |
DESCRIPTION |
Description of the extension |
Edit, create, and view your documents, spreadsheets, and presentations — all without internet access. |
6.1.4.2.1.10. Established connections

This entity is formed by a list of open network sockets in the system. Those are, for example, ESTABLISHED state connections, but not as LISTEN.
"ESTABLISHED_CONNECTIONS": {
"Results": [
{
"FAMILY": "2",
"LOCAL_ADDRESS": "10.21.33.131",
"LOCAL_PORT": "50681",
"PID": "3064",
"PROTOCOL": "6",
"REMOTE_ADDRESS": "20.54.36.229",
"REMOTE_PORT": "443",
"STATE": "ESTABLISHED"
},
...
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
PID |
Process ID |
10660 |
FAMILY |
Network protocol (IPv4, IPv6) |
2 |
PROTOCOL |
Transport protocol (TCP/UDP) |
6 |
LOCAL_ADDRESS |
Socket local address |
127.0.0.1 |
REMOTE_ADDRESS |
Socket remote address |
127.0.0.1 |
LOCAL_PORT |
Socket local port |
19001 |
REMOTE_PORT |
Socket remote port |
57833 |
STATE |
TCP socket state |
ESTABLISHED |
6.1.4.2.1.11. Processes

The process entity informs about the active tasks in the machine. Every program or script that the processor is executing at the time of a payload will be included in this list.
"PROCESSES": {
"Results": [
{
"CMDLINE": "",
"NAME": "osqueryi.exe",
"PARENT": "10384",
"PATH": "\\Device\\HarddiskVolume2\\Program Files\\osquery\\osqueryi.exe",
"PID": "8604",
"START_TIME": "1713350067",
"THREADS": "7",
"TOTAL_SIZE": "77824",
"USERNAME": "SYSTEM"
},
{
"CMDLINE": "\"C:\\Program Files\\osquery\\osqueryi.exe\" --S --json \"SELECT pid AS PID, name AS NAME, username AS USERNAME, parent AS PARENT, threads AS THREADS, total_size AS TOTAL_SIZE, path AS PATH, cmdline AS CMDLINE, start_time AS START_TIME FROM processes AS p JOIN users AS u ON u.uid = p.uid ORDER BY start_time DESC\"",
"NAME": "osqueryi.exe",
"PARENT": "10384",
"PATH": "C:\\Program Files\\osquery\\osqueryi.exe",
"PID": "6356",
"START_TIME": "1713350067",
"THREADS": "8",
"TOTAL_SIZE": "8171520",
"USERNAME": "SYSTEM"
},
...
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
PID |
Process ID |
28396 |
NAME |
Process name |
chrome.exe |
PARENT |
Parent process ID |
2004 |
THREADS |
Number of threads used by this process |
11 |
TOTAL_SIZE |
Virtual memory used in Bytes |
19714048 |
PATH |
Path to executed binary |
C:Program FilesGoogleChromeApplicationchrome.exe |
CMDLINE |
Complete arguments for the executed binary |
C:Program FilesGoogleChromeApplicationchrome.exe –type=renderer –display-capture-permissions-policy-allowed –lang=es –device-scale-factor=1.5 –num-raster-threads=4 –enable-main-frame-before-activation –renderer-client-d=172 –time-ticks-at-unix-epoch=-1666270068927136 –launch-time-ticks=359313593197 –mojo-platform-channel-handle=9276 –field-trial-handle=1852,i,11565825169520171724,8185573417412930569,131072/prefetch:1 |
START_TIME |
Process start time in seconds since Epoch |
1666629383 |
USERNAME |
User executing the process |
JuanPerez |
6.1.4.2.1.12. Security center

This is a Window only entity and is especially useful to know the current state of security on a device. In this way, you can know the health of the antivirus/firewall, if it is connected or disconnected, what product it is, etc.
"SECURITY_CENTER": {
"Results": [
{
"CATEGORY": "Firewall",
"COMPANY": "Windows Firewall",
"ENABLED": "1",
"PRODUCT": "Windows Firewall",
"SC_ENABLED": "1",
"UPTODATE": "1"
},
{
"CATEGORY": "Antivirus",
"COMPANY": "Microsoft Defender Antivirus",
"ENABLED": "1",
"PRODUCT": "Microsoft Defender Antivirus",
"SC_ENABLED": "1",
"UPTODATE": "1"
}
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
CATEGORY |
Type of security product |
Firewall |
SC_ENABLED |
Security center enabled (1 if the SC health is good or better) |
1 |
COMPANY |
Product company |
Firewall de Windows |
PRODUCT |
Name of product |
Firewall de Windows |
ENABLED |
State of protection |
1 |
UPTODATE |
1 if the product signatures are up to date, else 0 |
01/01/2001 0:00 |
6.1.4.2.1.13. Hardware

Collecting data related to the device’s hardware provides valuable information about its operating system, version, virtual machine status, architecture, serial identifiers, and more. While not all the information would be about the hardware itself, certain details like the machine’s name are assigned by the user during installation.
"HARDWARE": {
"Results": [
{
"ARCH": "x86_64",
"CORES": "4",
"HARDWARE_MODEL": "Standard PC (i440FX + PIIX, 1996)",
"HARDWARE_VENDOR": "QEMU",
"LOGICAL_CORES": "8",
"NAME": "STD2-V07",
"OSNAME": "Microsoft Windows 10 Pro N",
"OSVERSION": "10.0.19045",
"OS_VM": "1",
"OS_VOLUME": "C:",
"PROCESSOR_MODEL": "Common KVM processor",
"PROCESSOR_TYPE": "x86_64",
"RAM_MEMORY_IN_BYTES": "8589934592",
"SERIAL_NUMBER": "",
"UNIQUE_ID": "1F803876-DEFA-42E0-83EC-3B2BF6B0DF11",
"RANDOM_MAC_SWITCH": "0"
}
],
"GATHER_EVENT_ID": "cd79775d-059d-4f24-a21a-265e9d77fbc5",
"GATHER_START_DATE_TIME": "2024-04-17T10:34:27.3565144Z",
"GATHER_END_DATE_TIME": "2024-04-17T10:34:32.614753Z",
"GATHER_CPU_PERCENTAGE": 0.99,
"GATHER_MEMORY_CONSUMPTION": 1387832
},
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
UNIQUE_ID |
Unique ID provided by the system |
b56cef33-5ff1-4205-a6df-Ob6a54624f07 |
NAME |
Friendly computer name |
std3-v02 |
OSNAME |
Distribution or product name |
Windows 10 Pro N |
OSVERSION |
OS Version |
10 |
ARCH |
CPU type |
x64 |
OS_VOLUME |
The drive id, usually the drive name |
C: |
SERIAL_NUMBER |
Device serial number |
1754283681 |
OS_VM |
If it is a virtual machine or not |
1 |
6.1.4.2.1.14. Certificates
The certificates available to the user on their device.
"CERTIFICATE": {
"Results": [
{
"END_DATE": "1620602893",
"ISSUER": "com, microsoft, Microsoft Root Certificate Authority",
"START_DATE": "989450362",
"SUBJECT": "com, microsoft, Microsoft Root Certificate Authority"
},
{
"END_DATE": "1609459199",
"ISSUER": "ZA, Western Cape, Durbanville, Thawte, Thawte Certification, Thawte Timestamping CA",
"START_DATE": "852076800",
"SUBJECT": "ZA, Western Cape, Durbanville, Thawte, Thawte Certification, Thawte Timestamping CA"
},
...
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
ISSUER |
Certificate issuer name |
Microsoft Root Certificate Authority |
START DATE |
Lower bound of valid date |
10/05/2001 1:19 |
END DATE |
Certificate expiration date |
10/05/2021 1:28 |
SUBJECT |
Certificate name |
Microsoft Root Certificate Authority |
6.1.4.2.1.15. Networks

Knowing the status of the user’s networks is essential for identifying their current connections, determining the status of the connection (whether it is active or not), and determining if it is a VPN connection or any other type of connection.
The following attributes represent the Network entity.
"NETWORKS": {
"Results": [
{
"DESCRIPTION": "Intel(R) PRO/1000 MT Network Connection #4",
"DHCP_ENABLED": "0",
"GATEWAY": "10.21.33.254",
"INTERFACE_TYPE": "Physical",
"IPADDRESS": "10.21.33.131",
"MACADDR": "0a:12:ea:58:ba:85",
"NAME": "Ethernet Instance 0 2",
"OPER_STATUS": "2",
"RANDOM_MAC": "TRUE",
"TYPE": "6"
},
...
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
NAME |
Interface name |
Ethernet |
DESCRIPTION |
Description of the network |
Intel(R) PRO/1000 MT Network Connection |
DHCP_ENABLED |
DHCP is enabled or not |
0 |
GATEWAY |
Gateway interface |
10.21.2.254 |
TYPE |
Interface type |
6 |
OPER_STATUS |
State of the network adapter connection to the network. |
1 |
MACADDR |
MAC of interface |
|
IPADDRESS |
IP address of interface |
10.21.2.245 |
6.1.4.2.1.16. Session events

With this entity, we can have a record of the session events on a device. In this way, any session start, close, lock, or unlock will be sent to the Core.
"SESSION_EVENTS": {
"Results": [
{
"DOMAINNAME": "login screen",
"EVENT": "LOGON",
"TIMESTAMP": "1713332279",
"TYPE": "LOGIN",
"USERNAME": "ocf"
},
{
"DOMAINNAME": "tty2",
"EVENT": "LOGON",
"TIMESTAMP": "1713332279",
"TYPE": "LOGIN",
"USERNAME": "ocf"
}
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
TYPE |
General type of the session event. There will be a login if the user starts a session or a logout if the user closes the session. |
LOGIN |
EVENT |
The specific type of the event: logon, logoff, lock and unlock. |
LOGON |
USERNAME |
User name |
juan |
DOMAINNAME |
Domain name |
DESKTOP-77FMN5B |
TIMESTAMP |
Date the event occurred |
1595238650 |
6.1.4.2.1.17. USB devices

This entity collects information about USB devices connected to a device.
"USB_DEVICE": {
"Results": [
{
"DEVICE_ID": "AppleUSBEHCI Root Hub Simulation",
"HARDWARE_ID": "8006",
"MANUFACTURER": "Apple Inc."
},
{
"DEVICE_ID": "QEMU USB Keyboard",
"HARDWARE_ID": "0001",
"MANUFACTURER": "QEMU"
},
...
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
DEVICE ID |
USB Device model |
Realtek USB GbE Family Controller |
MANUFACTURER |
USB Device vendor |
Realtek |
HARDWARE ID |
Hex-encoded USB Device model identifier |
USBVID_OBDAPID_8153REV_3000 |
6.1.4.2.1.18. WiFi

The available WiFi networks in the range of the device. From them, we want to know its SSID, its current status, the type of security and the quality of the signal.
"WIFI": {
"Results": [
{
"Error": "A problem occurred when obtaining information about this entity."
}
],
"GATHER_EVENT_ID": "d372f3d6-c295-4fef-bd23-8815d89d765c",
"GATHER_CPU_PERCENTAGE": 10.69,
"GATHER_MEMORY_CONSUMPTION": 573848
},
DATA KEY NAME |
DESCRIPTION |
EXAMPLE |
|---|---|---|
INTERFACE_GUID |
SSID octets of the network |
4E5538F9-13FE-45AD-8682-77797A5AB319 |
SSID |
Name of the network |
MOVISTAR_PLUS_4C1A |
SIGNAL_QUALITY |
The current received signal strength indication (dbm) |
03/04/1900 0:00 |
SECURITY_ENABLED |
If the network has a password, then security is enabled and the value is 1 |
1 |
SECURITY |
Type of security on this network |
WPA2-PSK |
CONNECTABLE |
1 if this network is disabled, otherwise 0 |
1 |
IS_CONNECTED |
1 if the user is connected to this network, otherwise 0 |
1 |
6.1.4.2.2. Scanned info
Finally, at the end of the payload, you will find additional information collected by the Agent that will give you information about system updates, script modifications, Iptables, and the complete list of tags that the Agent assigned to the device.
6.1.4.2.2.1. Gather events
"GATHEREVENTS": {
"GATHER_EVENT_ID": "cd79775d-059d-4f24-a21a-265e9d77fbc5",
"GATHER_START_DATE_TIME": "2024-04-17T10:34:27.2529249Z",
"GATHER_END_DATE_TIME": "2024-04-17T10:34:36.5884993Z",
"GATHER_CPU_PERCENTAGE": 0.96,
"GATHER_MEMORY_CONSUMPTION": 1875184
},
"TRIGGERTYPE": 3,
"TRIGGERDATETIME": "2024-04-17T10:34:54.950368Z",
6.1.4.2.2.2. Script execution results
"SCRIPTEXECUTIONRESULTS": {
"INIGO_WIN_1": {
"SCRIPT": "descripcion1 modificado",
"RESULT": false,
"STDOUT": "",
"STDERR": "descripcion1 : The term 'descripcion1' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.At C:\\WINDOWS\\TEMP\\8b817d92169543e2b2397615a15c8735.ps1:1 char:1+ descripcion1 modificado+ ~~~~~~~~~~~~ + CategoryInfo : ObjectNotFound: (descripcion1:String) [], CommandNotFoundException + FullyQualifiedErrorId : CommandNotFoundException ",
"START_TIME": "2024-04-17T10:34:54.95379Z",
"END_TIME": "2024-04-17T10:34:56.2197323Z"
}
},
6.1.4.2.2.4. Scanned Networks
"SCANNED_NETWORKS": [
{
"BROADCAST_ADDRESS": "192.168.1.255",
"NETMASK": "255.255.255.0",
"NETWORK_ADDRESSES": [
{
"IP_ADDRESS": "192.168.1.1",
"OPEN_PORTS": {
"TCP": [
53,
80,
8080
],
"UDP": []
},
"TAGS": [
"DOP_TCP_53",
"DOP_TCP_80",
"DOP_TCP_8080"
],
"HOSTNAME": "www.routerlogin.net"
},
{
"IP_ADDRESS": "192.168.1.12",
"OPEN_PORTS": {
"TCP": [
22,
53,
80,
443,
3306,
8080,
8081,
8443
],
"UDP": []
},
"TAGS": [
"DOP_TCP_22",
"DOP_TCP_53",
"DOP_TCP_80",
"DOP_TCP_443",
"DOP_TCP_3306",
"DOP_TCP_8080",
"DOP_TCP_8081",
"DOP_TCP_8443"
],
"HOSTNAME": null
},
{
"IP_ADDRESS": "192.168.1.148",
"OPEN_PORTS": {
"TCP": [],
"UDP": []
},
"TAGS": [],
"HOSTNAME": null
},
{
"IP_ADDRESS": "192.168.1.221",
"OPEN_PORTS": {
"TCP": [
80
],
"UDP": []
},
"TAGS": [
"DOP_TCP_80"
],
"HOSTNAME": null
}
]
}
],
6.1.4.2.2.5. Pending System updates (Windows only)
"PENDING_SYSTEM_UPDATES": [
{
"DAYS_PENDING": 99,
"DRIVER": false,
"KB_ARTICLE_ID": "5034441",
"TITLE": "2024-01 Security Update for Windows 10 Version 22H2 for x64-based Systems (KB5034441)",
"MSRC_SEVERITY": "IMPORTANT"
},
{
"DAYS_PENDING": 43,
"DRIVER": false,
"KB_ARTICLE_ID": "5001716",
"TITLE": "2024-03 Update for Windows 10 Version 22H2 for x64-based Systems (KB5001716)",
"MSRC_SEVERITY": null
},
6.1.4.2.2.6. Installed system updates
"INSTALLED_SYSTEM_UPDATES": [
{
"UPDATE_ID": "4f646943-c20c-44e7-ae95-ddffb5eb9c15",
"TITLE": "Security Intelligence Update for Microsoft Defender Antivirus - KB2267602 (Version 1.409.332.0) - Current Channel (Broad)",
"DESCRIPTION": "Install this update to revise the files that are used to detect viruses, spyware, and other potentially unwanted software. Once you have installed this item, it cannot be removed.",
"DATE": "2024/04/17",
"CLIENT_APPLICATION_ID": "Windows Defender"
},
{
"UPDATE_ID": "87ee6d89-5b34-47ba-8d5c-5e6aac6aaf89",
"TITLE": "Update for Microsoft Defender Antivirus antimalware platform - KB4052623 (Version 4.18.24030.9) - Current Channel (Broad)",
"DESCRIPTION": "This package will update Microsoft Defender Antivirus antimalware platform's components on the user machine.",
"DATE": "2024/04/17",
"CLIENT_APPLICATION_ID": "Windows Defender"
},
...
6.1.4.2.2.7. Script modifications
"SCRIPTS_MODIFICATIONS": {
"INIGO_WIN_1": "Added"
},
6.1.4.2.2.8. Iptables
"IPTABLES": [
{
"chain": "INPUT",
"pkts": "543K",
"bytes": "586M",
"target": "ufw-before-logging-input",
"prot": "all",
"opt": "--",
"in": "*",
"out": "*",
"source": "0.0.0.0/0",
"destination": "0.0.0.0/0",
"parameter": ""
},
{
"chain": "INPUT",
"pkts": "543K",
"bytes": "586M",
"target": "ufw-before-input",
"prot": "all",
"opt": "--",
"in": "*",
"out": "*",
"source": "0.0.0.0/0",
"destination": "0.0.0.0/0",
"parameter": ""
},
{
"chain": "INPUT",
"pkts": "1100",
"bytes": "209K",
"target": "ufw-after-input",
"prot": "all",
"opt": "--",
"in": "*",
"out": "*",
"source": "0.0.0.0/0",
"destination": "0.0.0.0/0",
"parameter": ""
},
{
"chain": "INPUT",
"pkts": "111",
"bytes": "4373",
"target": "ufw-after-logging-input",
"prot": "all",
"opt": "--",
"in": "*",
"out": "*",
"source": "0.0.0.0/0",
"destination": "0.0.0.0/0",
"parameter": ""
},
{
"chain": "INPUT",
"pkts": "111",
"bytes": "4373",
"target": "ufw-reject-input",
"prot": "all",
"opt": "--",
"in": "*",
"out": "*",
"source": "0.0.0.0/0",
"destination": "0.0.0.0/0",
"parameter": ""
},
{
"chain": "INPUT",
"pkts": "111",
"bytes": "4373",
"target": "ufw-track-input",
"prot": "all",
"opt": "--",
"in": "*",
"out": "*",
"source": "0.0.0.0/0",
"destination": "0.0.0.0/0",
"parameter": ""
},
{
"chain": "FORWARD",
"pkts": "0",
"bytes": "0",
"target": "ufw-before-logging-forward",
"prot": "all",
"opt": "--",
"in": "*",
"out": "*",
"source": "0.0.0.0/0",
"destination": "0.0.0.0/0",
"parameter": ""
},
{
"chain": "ufw-after-logging-input",
"pkts": "111",
"bytes": "4373",
"target": "LOG",
"prot": "all",
"opt": "--",
"in": "*",
"out": "*",
"source": "0.0.0.0/0",
"destination": "0.0.0.0/0",
"parameter": "limit: avg 3/min burst 10 LOG flags 0 level 4 prefix \"[UFW BLOCK] \""
}
]
6.1.4.2.2.9. Device Domain Info
The device domain information is obtained through a poweshell script execution to calculate and directly associate tags with the device. The payload does not include the details of this script execution.
The following tags will be generated through script execution:
Tag |
Example |
|---|---|
DDI_JOINED_* |
DDI_JOINED_AZUREAD, DDI_JOINED_ENTERPRISE, DDI_JOINED_DOMAIN |
DDI_STATE_* |
DDI_STATE_AZUREADJOINED, DDI_STATE_DOMAINJOINED, DDI_STATE_HYBRIDADJOINED, DDI_STATE_ONPREMISEDRSJOINED |
DDI_DOMAIN_NAME_* |
DDI_DOMAIN_NAME_ACME |
DDI_TENANT_NAME_* |
DDI_TENANT_NAME_ACME |