4.1.7. Monitoring
With all the information collected about the Visibility module, the Analytics component generates dashboards providing users with quick and comprehensive insights.
The dashboards utilize graphs and tables to organize the diverse and substantial volume of data collected from various sources. Users can apply filters and time periods to customize the displayed parameters. Please note that devices without recent updates won’t be included in the displayed events.
For access to these dashboards, navigate to Administration Portal > Analytics > Visibility.
4.1.7.1. Visibility Overview
The “Visibility Overview” dashboard provides an overview of all the user devices connected to the network. It categorizes them based on their endpoint type and displays the characteristics associated with them.
We can see the following views on this dashboard, starting from the header:
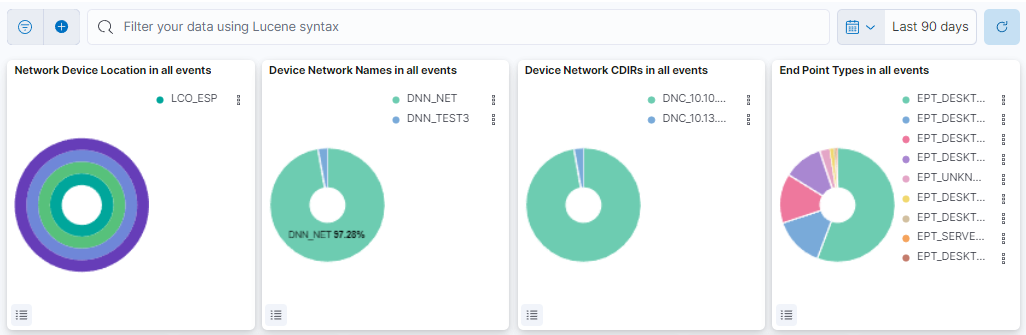
This header composed of four dashboards allows filtering by Network Device Location, Device Network Name, Device Network CDIRs, Endpoint Types. It will always look for the temporary index that is regenerated every day. In this toolbar, filter your data using Lucene syntax.
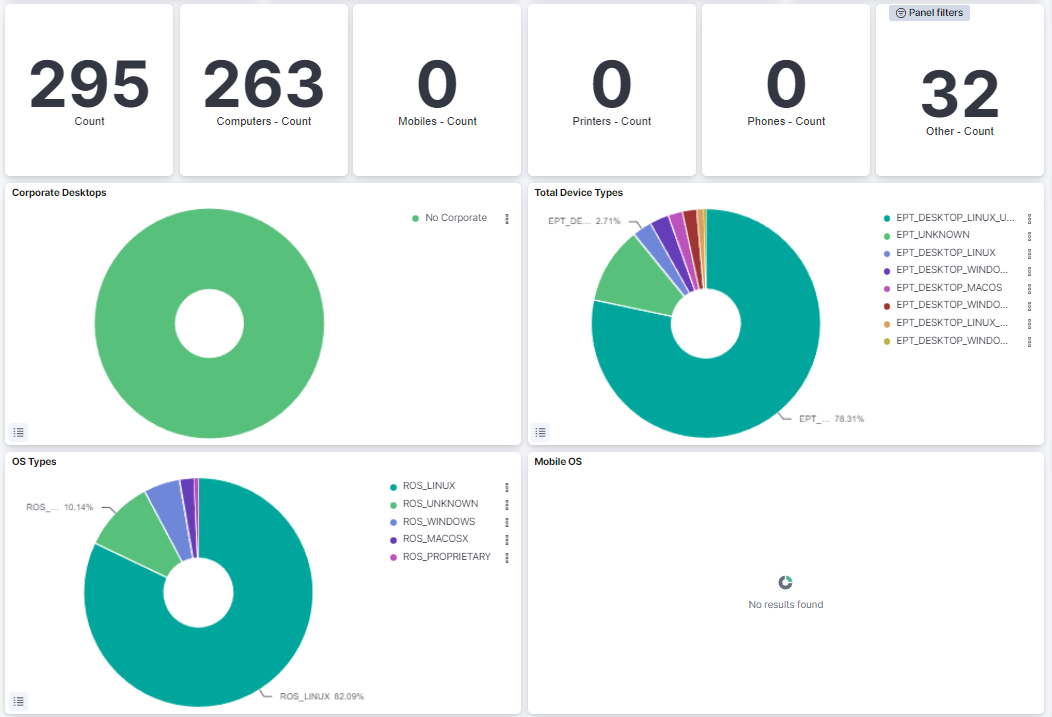
Total Devices: Shows the number of total devices in the network.
Computers: Shows the number of total computers in the network.
Mobiles: Shows the number of total mobiles in the network.
Printers: Shows the number of total printers in the network.
Phones: Shows the number of total phones in the network.
Other: Shows the number of the other devices in the network.
Corporate Desktops: Represents the percentage of corporate devices and no corporate devices.
Total Device Types: Represents the percentage of EPT (Endpoint Type) tags.
OS Types: Represents the percentage of the operating systems from all the devices in the network.
Mobile OS: Represents the percentage of the operating systems from the mobiles in the network.
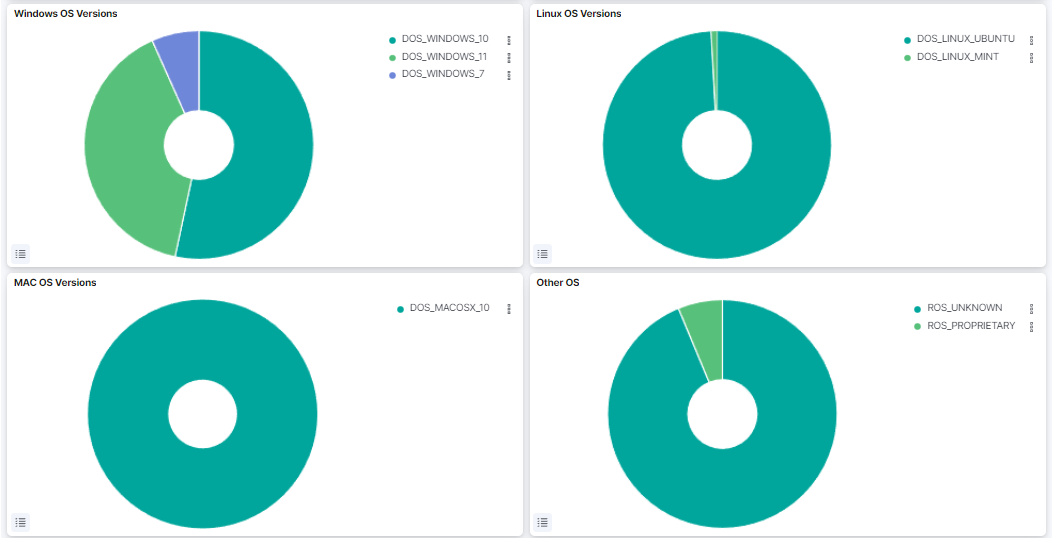
Windows OS Versions: Represents the percentage of the Windows versions found in the network.
Linux OS Versions: Represents the percentage of the Linux versions found in the network.
MAC OS Versions: Represents the percentage of the MAC OS versions found in the network.
Other OS: Represents the percentage of the other operating systems found in the network.
4.1.7.2. CMDB Metrics
The CMDB metrics dashboard display various metrics and insights related to Network Devices and Enpoint Devices and their tags.
We can see the following views on this dashboard, starting from the header:
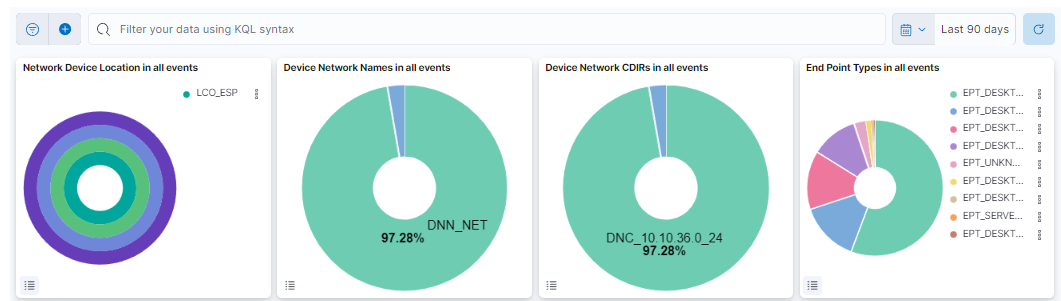
This header composed of four dashboards allows filtering by Network Device Location, Device Network Name, Device Network CDIRs, Endpoint Types. It will always look for the temporary index that is regenerated every day. In this toolbar, filter your data using KQL syntax.
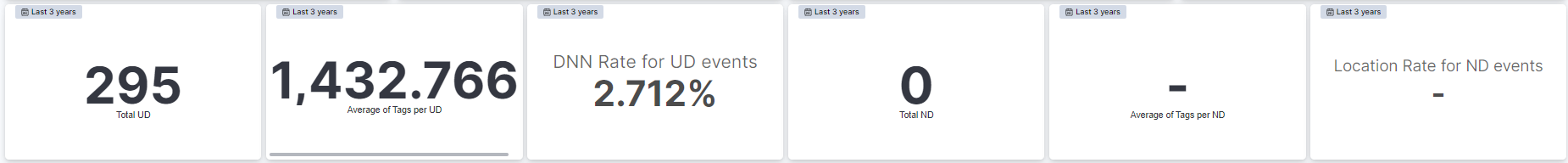
Total UD: Displays the count of total User Devices.
Average of Tags per UD: Displays the average count of tags per User Device.
DNN Rate for UD events: Displays the rate of predicting events related to User Devices.
Total ND: Displays the count of total Network Devices.
Average of Tags per ND: Displays the average count of tags per Network Device.
Location rate for ND events: Displays the rate of predicting events related to Network Devices.
Note
By default, these modules display data by the last 3 years time range.
To change the time range, click on the time displayed and a configuration window will pop-up.
Choose the time range that better suit your needs and click on Update to save your preferences.
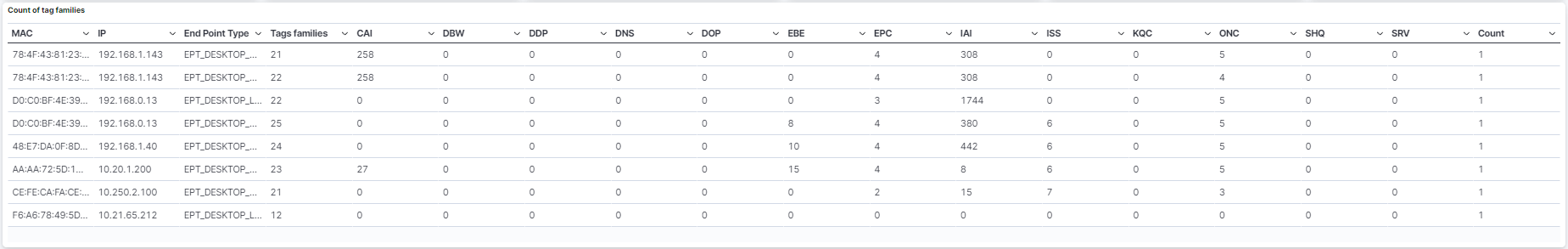
Count of tag families: Table that features the tags associated to a specific device and its count of tag families. See the Tags Table section for detailed information about the tags displayed in this view.
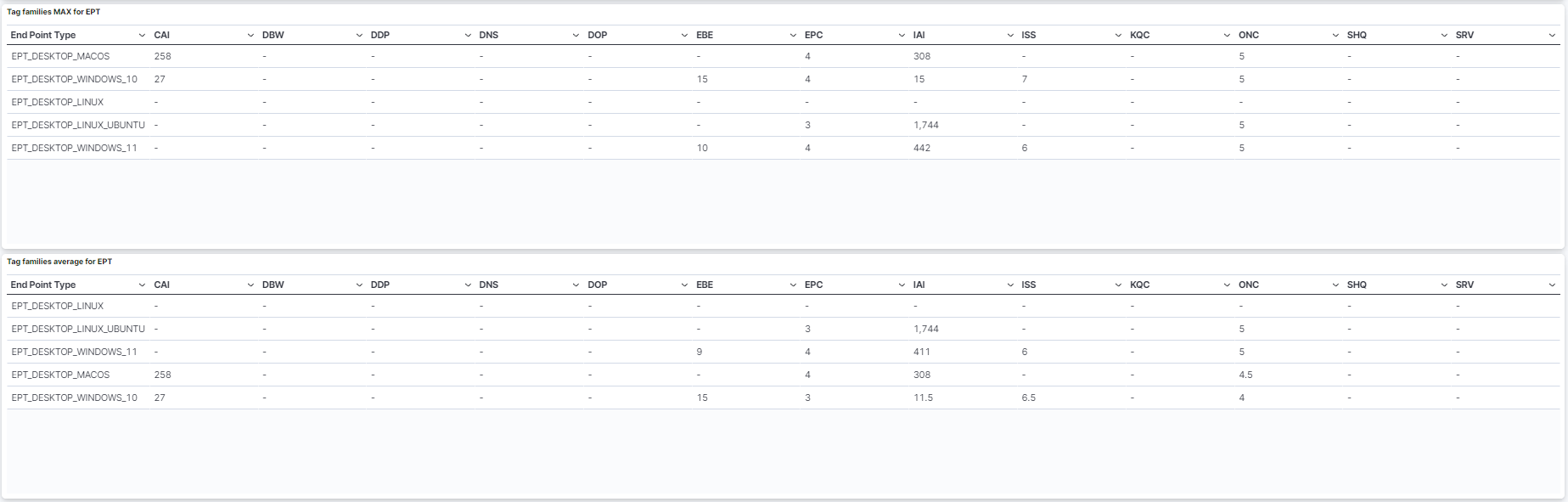
Tag families MAX for EPT: Table that features the MAX tag families associated to an Endpoint Type.
Tag families average for EPT: Table that features the average tag families associated to an Endpoint Type.
4.1.7.3. Network Behaviour
The Network Behaviour Dashboard displays all the information captured from the ON Sensor that is stored in the index of “bro-”.
4.1.7.3.1. Header
The three available views in the Network Behaviour section show different information captured by the sensor. However, they have a common header, which refers to a consistent section at the top of each view that contains shared information.
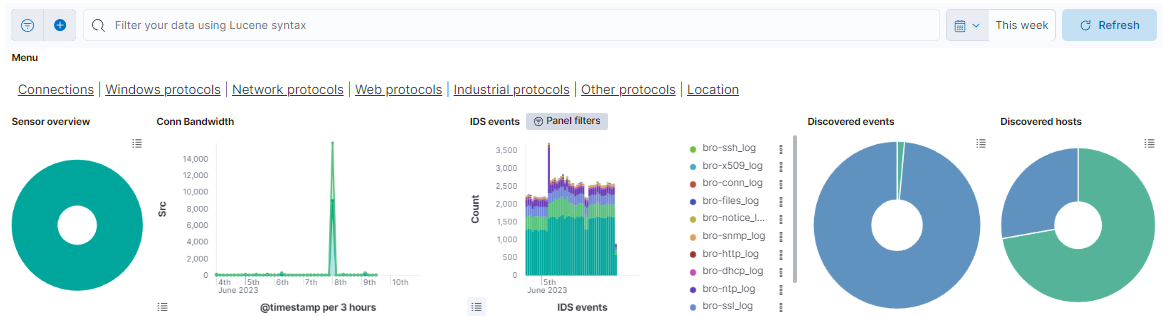
Menu
The menu features different windows, such as Connections, Windows protocols, Network protocols, Web protocols, Industrial protocols, Other protocols, and Location. Each window offers distinct dashboard views, allowing you to navigate between these sections. The following topics will explore these menu options in detail.
Sensor overview: Represents the percentage of the different ON Sensor that are generating the events.
Conn Bandwidth: Shows the total bandwidth of requests and responses to see the traffic that the bro index is generating on a timeline.
IDS events: Shows the total of events of bro separated by the event type on a timeline. The different event types are: bro-conn_log, bro-dns_log, bro-http_log, bro-files_log, bro-dhcp_log, bro-notice_log, bro-ssl_log, bro-x509_log, bro-kerberos_log, bro-radius_log, bro-ssh_log, bro-snmp_log, bro-sip_log, bro-dpd_log, bro-smtp_log, bro-arp_log, bro-modbus_log, bro-rfb_log, bro-rdp_log, bro-ntlm_log, bro-socks_log, bro-tunnel_log, bro-rpc_log, bro-pe_log, bro-smb_files_log, bro-smb_mapping_log, bro-s7comm_log, bro-profinet_log, bro-bacnet_log, bro-enip_log, bro-dnp3_log and bro-syslog_log.
Discovered events: Represents the total of events discovered by OpenNAC Enterprise versus the events that can’t be discovered and represent unknown devices. One device can generate many events.
Discovered hosts: Represents the total of devices discovered by OpenNAC Enterprise versus the devices that can’t be discovered and represent unknown devices.
4.1.7.3.2. Connections
This window displays the connections logs captured by the ON Sensor.
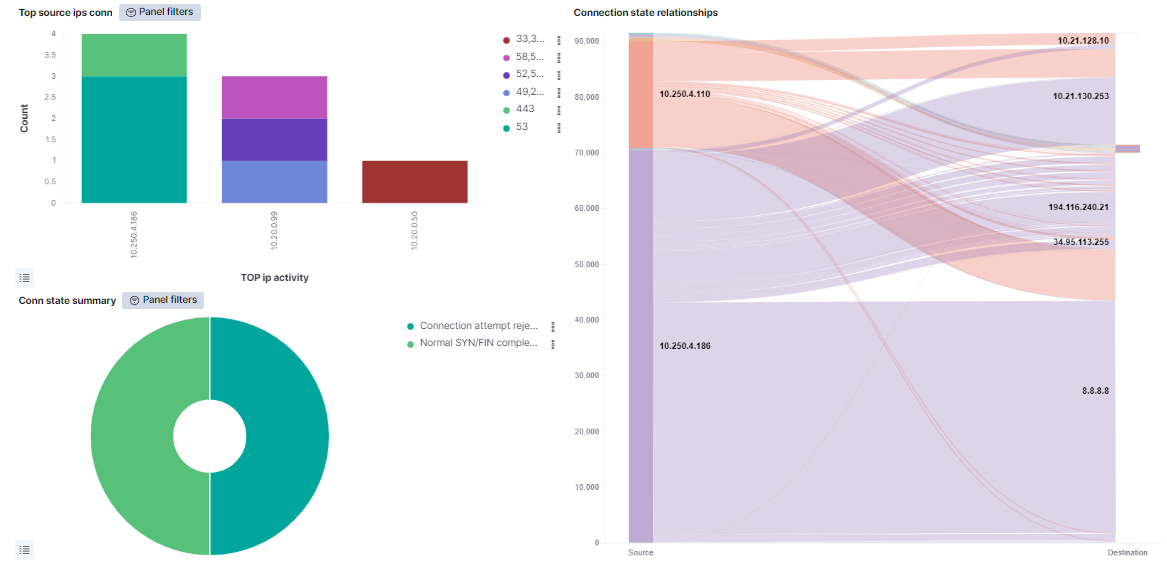
Top source ips conn: Shows the top 10 IPs with more connections indicating in the Y axis the total of connections. The connections are divided by the destination port of the connection
Conn state summary: Represents the percentage of the top 10 most found connection states.
Connection state relationship: Shows the connection relationship between the different IPs separating in the left the source IPs and in the right the destination IPs.
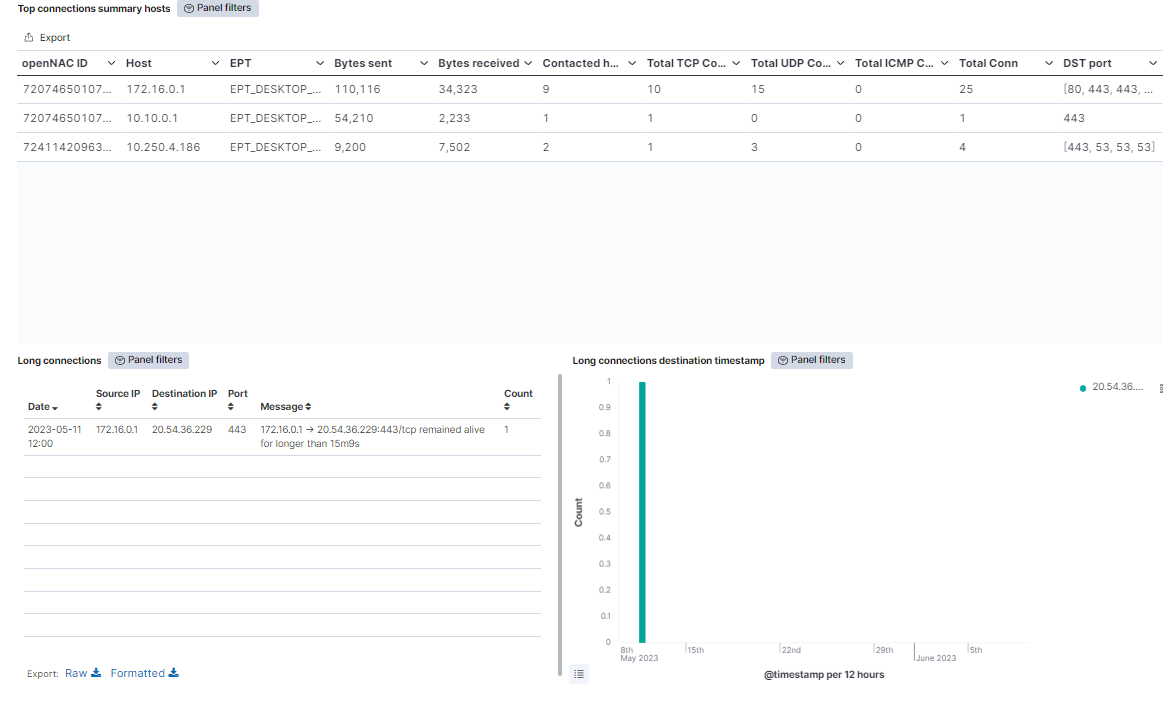
Top connections summary hosts: Shows a table of the top 100 connections showing the OpenNAC Enterprise ID, the host IP, the EPT type, the bytes send and received, the contacted host, the total TCP connections, the total UDP connections, the total ICMP connections, the total connections (the summarization of TCP, UDP and ICMP connections), and the last five destination port.
Long connections: Shows a table with the connections tagged as long. These connections are those that are running during a large period of time, like hours or days. In this table the Date when an event of long connection is detected is shown, and also the source and the destination IP of the connection, the port and the message, that shows the time the connection has been alive.
Long connections destination timestamp: Show over time when the long connections are noticed, separated by destination IP.
4.1.7.3.3. Windows protocols
This window displays windows protocols logs captured by the ON Sensor. These protocols are NTLM (windows New Technology Local area network Manager), SMB (Server Message Block), DCE RPC (Data Circuit-terminating Equipment Remote Procedure Call), RDP (Remote Desktop Protocol), RFB (Remote Frame Buffer) and PE (Portable Executable).

Top services: The internal pie represents the percentage of the events that exist from each service. Some of these services are dns, ssl, nto, krb, http, dce_rpc, dhcp, ssh. The external pie represents the percentage of messages of every event.
NTLM Overview: The internal pie represents the percentage of the top 10 NTLM hostnames, and the external pie, the username of the NTLM host.
SMB mapping: Shows a table with the SMB mapping events. This table has the source IP and the destination IP, the path, the share type, and the count each event has been repeated.
SMB mapping timestamp: Shows all the SMB mapping events, separated by destination IP on a timeline.

SMB files: Shows a table with the SMB files events. This table represents the source IP and the destination IP of each connection, the name of the file, the action of SMB over the file, the path, the size, and the amount of times this event is repeated.
SMB files timestamp: Shows all the SMB file events, separated by destination IP on a timeline.
DCE RPC: Shows a table with DCE RPC events. In this table the source IP and the destination IP of each connection is represented, as well as the endpoint, the operation, the named pipe, and the amount of times this event is repeated.
DCE RPC authentication timestamp: Shows all the DCE RPC events, separated by destination IP on a timeline.

RDP connections: Shows a table with RDP events. In this table the source IP and the destination IP of each connection is represented, as well as the hostname, the result, the security protocol, the certificate count, and the amount of times this event is repeated.
RDP authentication timestamp: Shows all the RDP events, separated by destination IP on a timeline.
RFB connections: Shows a table with RDP events. This table represents the source IP and the destination IP of each connection, as well as the authentication method, the desktop, and the amount of times this event is repeated.
RFB authentication timestamp: Shows all the RFB events, separated by destination IP on a timeline.
PE: Shows a table with RDP events. In this table there are values for each source machine that generates this event, their operating system, if the portable executable is executable, if its size is 64b, its code integrity, if it has cert table, if it has debug data, and the amount of times this event is repeated.
PE summary: The internal pie represents the percentage of the PE machines subsystem. The middle pie represents the percentage of operating systems for every subsystem. And the external pie represents the percentage of the PE machines for every operating system.
4.1.7.3.4. Network protocols
The Network protocols displays views of network protocols logs captured by the ON Sensor. These protocols are VLAN (Virtual Local Area Network), DHCP (Dynamic Host Configuration Protocol), RADIUS (Remote Authentication Dial-In User Service), Kerberos, SNMP (Simple Network Management Protocol) and VXLAN (Virtual Extensible Local Area Network).
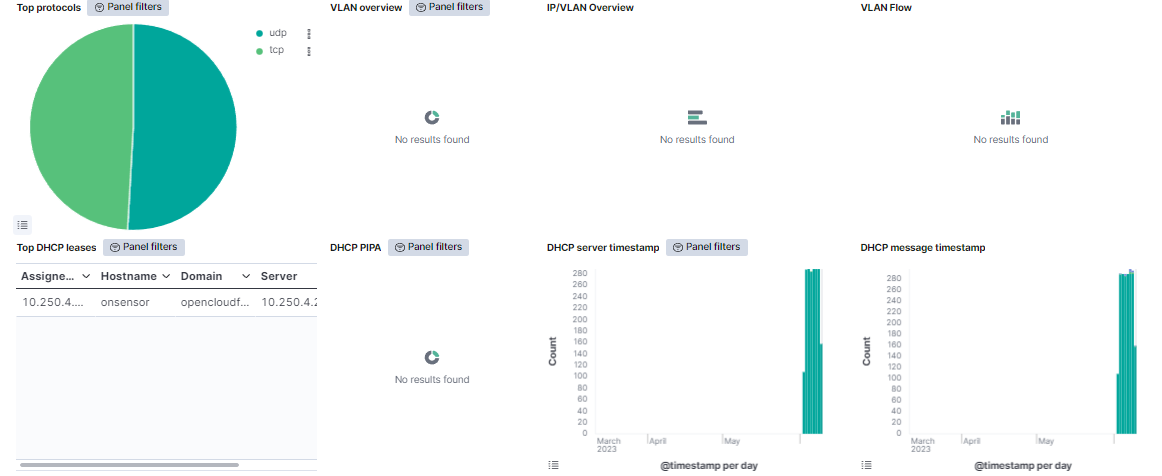
Top protocols: Represents the percentage of the events from protocols TCP, UDP and ICMP.
IP/VLAN Overview: Shows the number of IP detected in each VLAN.
VLAN overview: Represents the percentage of events per VLAN.
VLAN Flow: Shows the data bytes of the VLAN traffic, separated by VLAN on a timeline.
Top DHCP leases: Shows a table with DHCP leases events. This table represetns the assigned IP, as well as the hostname, the domain, the DHCP server, and the amount of times this event is repeated.
DHCP PIPA: The internal pie represents the percentage of the DHCP PIPA IP ranges. These are the IPs that are assigned when a DHCP server is not in range. The external pie represents the percentage of VLANs where the DHCP PIPA has been assigned.
DHCP server timestamp: Shows all the DHCP events, separated by destination IP on a timeline.
DHCP message timestamp: Shows all the DHCP events, separated by DHCP message on a timeline.
Top radius auth: Shows a table with Radius authorization events. In this table it’s represented the username, the result, the client IP, the server IP, and the amount of times this event is repeated.
Radius result: Represents the percentage of success and failed Radius authentications.
Number of Radius request: Shows the Radius events, separated by success or failed on a timeline.
Radius devices: Shows a table with Radius devices. This table displays the MAC, the username, the IP, and the amount of times this event is repeated.
Kerberos host: Shows a table with Kerberos hosts. This table displays the Kerberos host and the hosts event counts.
Kerberos success: Represents the percentage of success and failed Kerberos events.
Kerberos error timestamp: Shows the Kerberos events, separated by Kerberos error message on a timeline.
Kerberos user: Shows a table with Kerberos users. This table displays the Kerberos host and the users event counts.
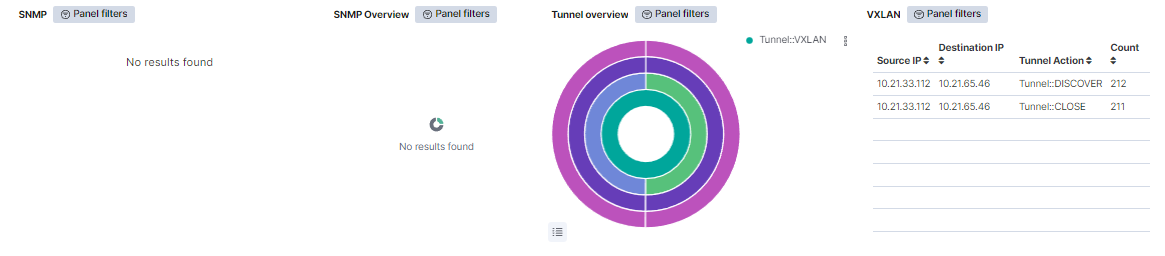
SNMP: Shows a table with SNMP events. This table represents the source IP, the destination IP, and the amount of times this event is repeated.
SNMP Overview: The internal pie represents the percentage of SNMP versions. The middle pie represents the percentage of SNMP community for every SNMP version. The external pie represents the percentage of source IP for every SNMP community..
Tunnel overview: The internal pie represents the percentage of the Tunnel type. The second pie represents the percentage of the Tunnel actions for every Tunnel type. The third pie, the percentage of the destination IPs actions for every Tunnel action. In the external pie, the percentage of source IPs for every destination IP is shown.
VXLAN: Shows a table with VXLAN events. This table displays the source IP, the destination IP, the Tunnel action, and the count of each event.
4.1.7.3.5. Web protocols
This window displays views of web protocols logs captured by the ON Sensor. These protocols are DNS (Domain Name System), HTTP (HyperText Transfer Protocol), SSH (Secure SHell), SSL (Secure Sockets Layer), and Certificate.
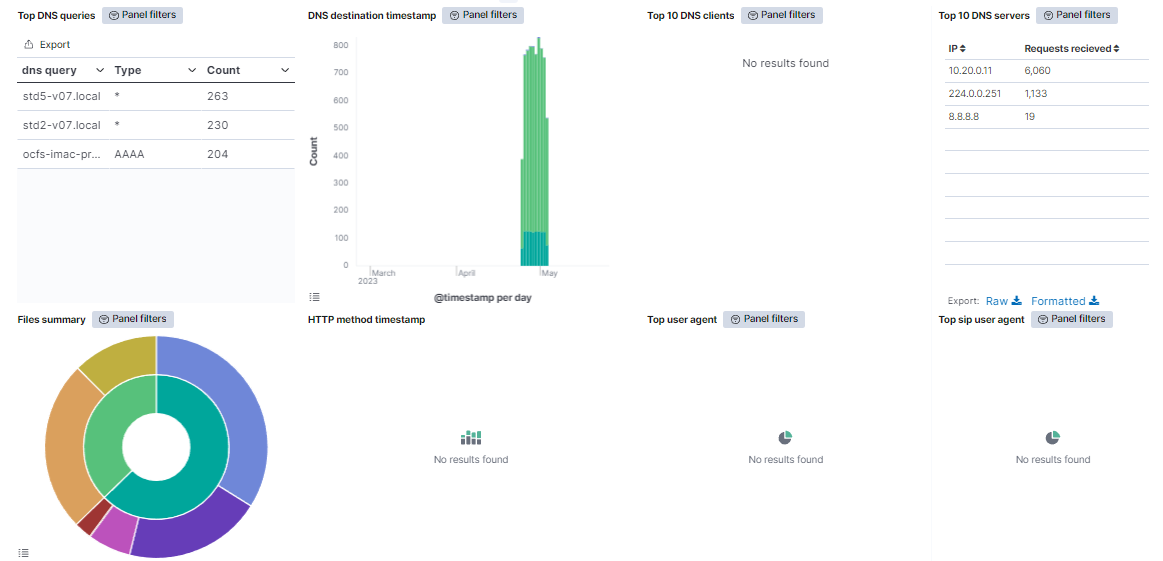
Top DNS queries: Shows a table with DNS events. The table, for each event, includes the dns query, the type, and the amount of times this event is repeated.
DNS destination timestamp: Shows the DNS events, separated by the destination IP on a timeline.
Top 10 DNS clients: Shows a table with the top 10 DNS clients. The table, for each event, includes the dns client IP, the hostname, and the requests send.
Top 10 DNS servers: Shows a table with the top 10 DNS servers. The table, for each event, includes the dns server IP, and the requests received.
Files summary: In the internal pie, it is represented the percentage of the file sources. In the external pie, the percentage of MIME types for every file source is shown.
HTTP method timestamp: Shows over time the HTTP events, separated by the HTTP method.
Top user agent: In the internal pie, the percentage of HTTP user agents is shown. In the external pie, the percentage of http response MIME types for every HTTP user agent is represented.
Top SIP user agent: Represents the percentage of SIP user agents types.
Top ssh servers: Shows a table with the top SSH servers. The table, for each event, includes the destination IP, the server banner, the client banner, and the amount of times this event is repeated.
SSH servers timestamp: Shows over time the SSH events, separated by the SSH server.
Top SSL server name: Shows a table with the top SSL servers subjects. The table, for each event, includes the SSL subject, the SSL version, the status, and the amount of times this event is repeated.
SSL version timestamp: Shows over time the SSL events, separated by the SSL version.
Top 10 SSL clients: Shows a table with the top 10 SSL clients. The table, for each event, includes the client IP, the ja3 (client fingerprint), the MAC, the EPT type, and the amount of times this event is repeated.
Top 10 SSL servers: Shows a table with the top SSL servers. The table, for each event, includes the server IP, the ja3s (server fingerprint), and the amount of times this event is repeated.
Certificate: Shows a table with the top certificate issuers. The table, for each event, includes the certificate issuer name, the key length, the key type, the key algorithm, the signature algorithm, and the amount of times this event is repeated.
Certificate issuer timestamp: Shows when the certificates are used, separated by the certificate issuer on a timeline.
4.1.7.3.6. Industrial protocols
The Industrial Potocols window displays views of the industrial protocol logs captured by the ON Sensors. These protocols are Bacnet (Building Automation and Control NETworks), ENIP (EtherNet/IP), Profinet (PROcess FIeld NETwork), Modbus, S7comm (Siemens S7 communication), DNP3 (Distribution Network Protocol version 3).
Bacnet: Shows a table with the Bacnet events. The table, for each event, includes the source IP, the destination IP, the abdu type, the bvlc function, the service, and the amount of times this event is repeated.
Top 10 Bacnet clients: Shows a table with the top 10 Bacnet clients. The table, for each event, includes the client IP and the amount of times this event is repeated.
Bacnet timestamp: Shows over time the Bacnet event, separated by destination IP.
Top 10 Bacnet servers: Shows a table with the top 10 Bacnet servers. The table, for each event, includes the server IP and the amount of times this event is repeated.

ENIP: Shows a table with the ENIP events. The table, for each event, includes the source IP, the destination IP, the command, the session ID, and the amount of times this event is repeated.
Top 10 ENIP clients: Shows a table with the top 10 ENIP clients. The table, for each event, includes the client IP and the amount of times this event is repeated.
ENIP timestamp: Shows over time the ENIP event, separated by destination IP.
Top 10 ENIP servers: Shows a table with the top 10 ENIP servers. The table, for each event, includes the server IP and the amount of times this event is repeated.

Profinet: Shows a table with the Profinet events. The table, for each event, includes the source IP, the destination IP, the index, the operation, the slot, the subslot, and the amount of times this event is repeated.
Top 10 Profinet clients: Shows a table with the top 10 Profinet clients. The table, for each event, includes the client IP and the amount of times this event is repeated.
Profinet timestamp: Shows over time the Profinet event, separated by destination IP.
Top 10 Profinet servers: Shows a table with the top 10 Profinet servers. The table, for each event, includes the server IP and the amount of times this event is repeated.

Modbus: Shows a table with the Modbus events. The table, for each event, includes the source IP, the destination IP, the modbus function, and the amount of times this event is repeated.
Top 10 Modbus clients: Shows a table with the top 10 Modbus clients. The table, for each event, includes the client IP and the amount of times this event is repeated.
Modbus timestamp: Shows over time the Modbus event, separated by destination IP.
Top 10 Modbus servers: Shows a table with the top 10 Modbus servers. The table, for each event, includes the server IP and the amount of times this event is repeated.

S7comm: Shows a table with the s7comm events. The table, for each event, includes the source IP, the destination IP, and the amount of times this event is repeated.
Top 10 S7comm clients: Shows a table with the top 10 s7comm clients. The table, for each event, includes the client IP and the amount of times this event is repeated.
S7comm timestamp: Shows over time the s7comm event, separated by destination IP.
Top 10 S7comm servers: Shows a table with the top 10 s7comm servers. The table, for each event, includes the server IP and the amount of times this event is repeated.

DNP3: Shows a table with the DNP3 events. The table, for each event, includes the source IP, the destination IP, the fc request, the fc reply, the IIN, and the amount of times this event is repeated.
Top DNP3 clients table: Shows a table with the top 10 DNP3 clients. The table, for each event, includes the client IP and the amount of times this event is repeated.
DNP3 timestamp: Shows over time the DNP3 event, separated by destination IP.
Top DNP3 servers table: Shows a table with the top 10 DNP3 servers. The table, for each event, includes the server IP and the amount of times this event is repeated.
4.1.7.3.7. Other protocols
The Other protocols window displays other protocol logs captured by the ON Sensor that do not match in the other windows. These protocols are DPD (Dynamic Protocol Detection), Syslog (System Logging Protocol) and FTP (File Transfer Protocol).
DPD: Shows a table with the DPD events. The table, for each event, includes the source IP, the destination IP, the analyzer, the protocol type, the failure reason, and the amount of times this event is repeated.
DPD Analyzer: Represents the percentage of the DPD analyzers detected.
DPD failures: Shows over time the DPD event, separated by the failure reason.
Syslog: Shows a table with the syslog events. The table, for each event, includes the source IP, the destination IP, the facility, the severity, the message, and the amount of times this event is repeated.
Syslog timestamp: Shows over time the syslog events, separated by destination severity.

FTP: Shows a table with the FTP events. The table, for each event, includes the source IP, the destination IP, the source host, and the amount of times this event is repeated.
FTP flow timestamp: Shows over time the data bytes of the FTP traffic, separated by destination IP.
4.1.7.3.8. Location
The Location window displays views about the location of the logs captured by the ON Sensor.
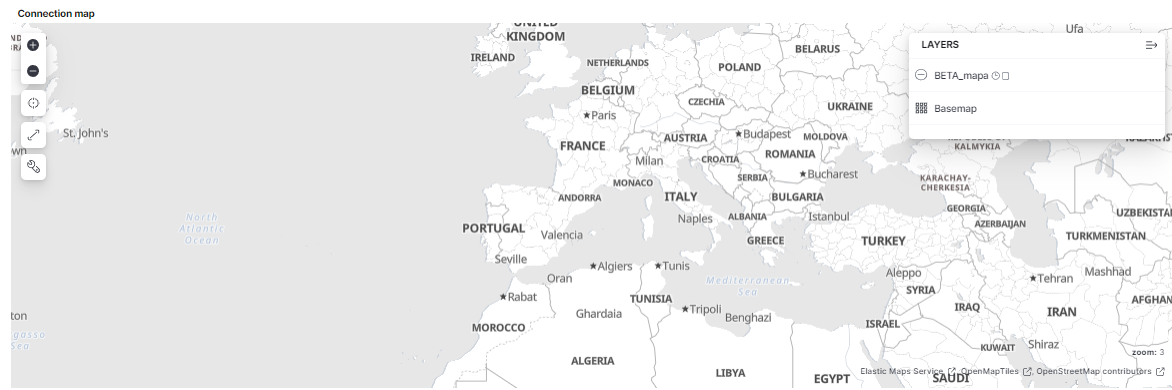
Connection map: Shows in a map from what part of the world is the traffic coming, and depending of the traffic density, the circle is bigger or smaller.
4.1.7.4. Profiling Metrics
The Profiling Metrics dashboard presents device tag metrics to enhance device profiling capabilities.
We can see the following views on this dashboard, starting from the header:
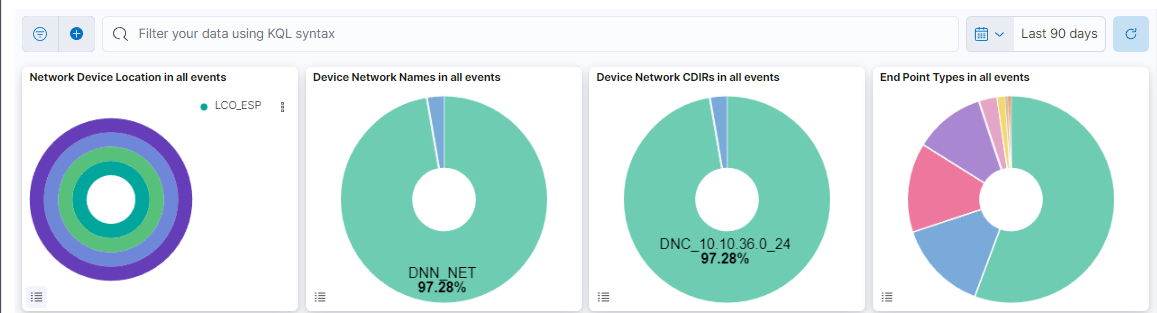
This header composed of four dashboards allows filtering by Network Device Location, Device Network Name, Device Network CDIRs, Endpoint Types. It will always look for the temporary index that is regenerated every day. In this toolbar, filter your data using KQL syntax.
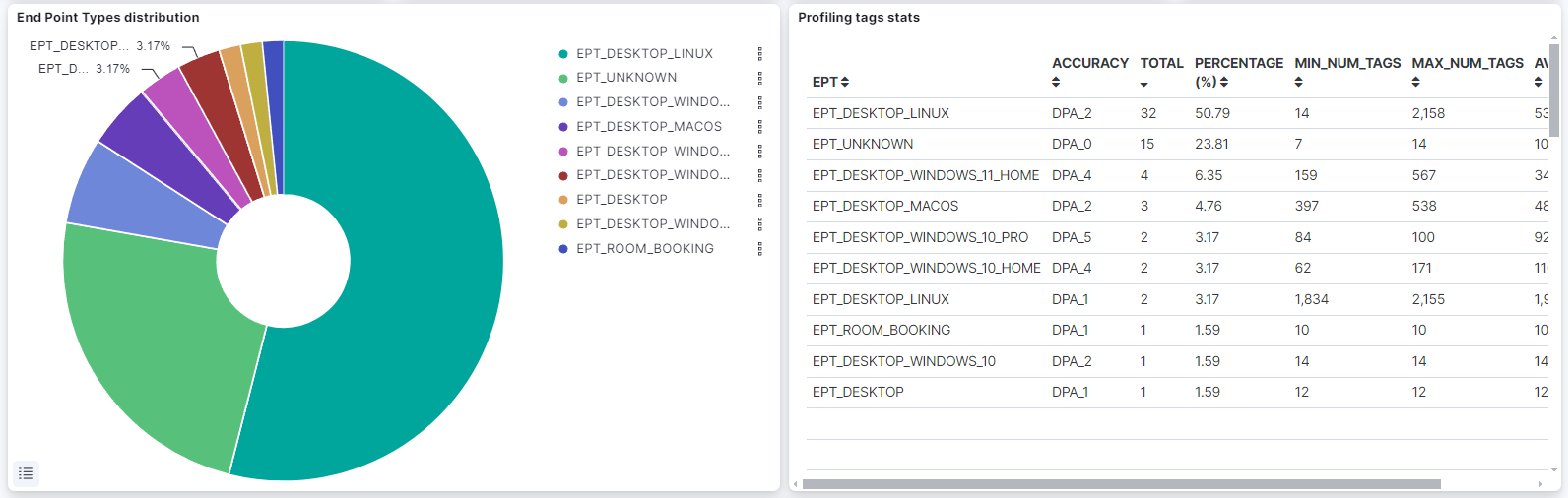
End Point distribution: A pie chart that displays the percentage of each EPT.
Profiling tags stats: A table that shows statistics based on EPT: tag, accuracy (TAG DPA), total, percentage, minimum number of tags, average, and a maximum of TAGs.
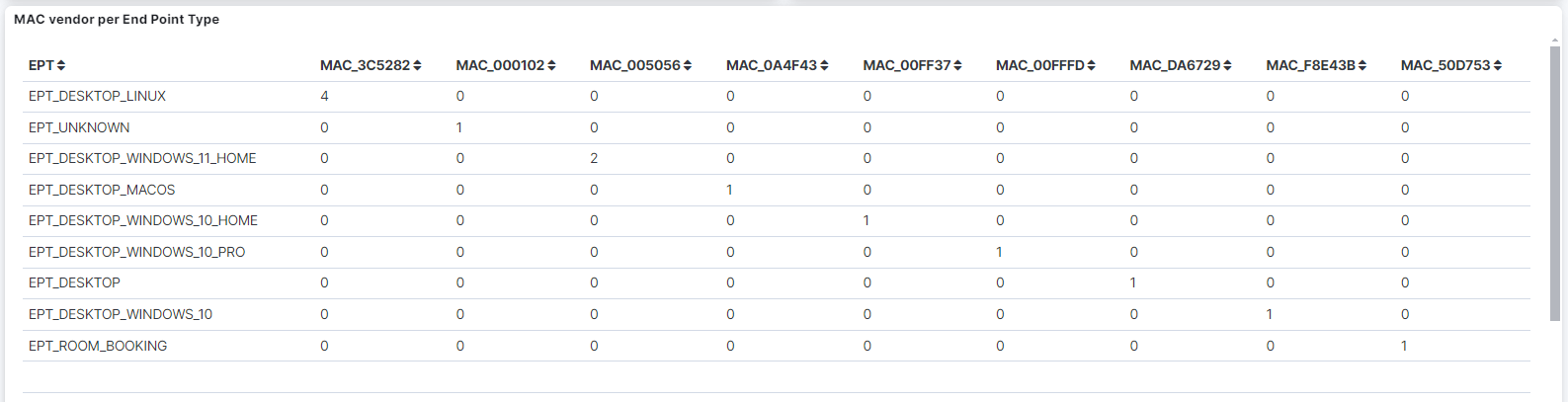
MAC vendor per End Point Type: A table that displays the MAC tags related to vendor per Endpoint Types.
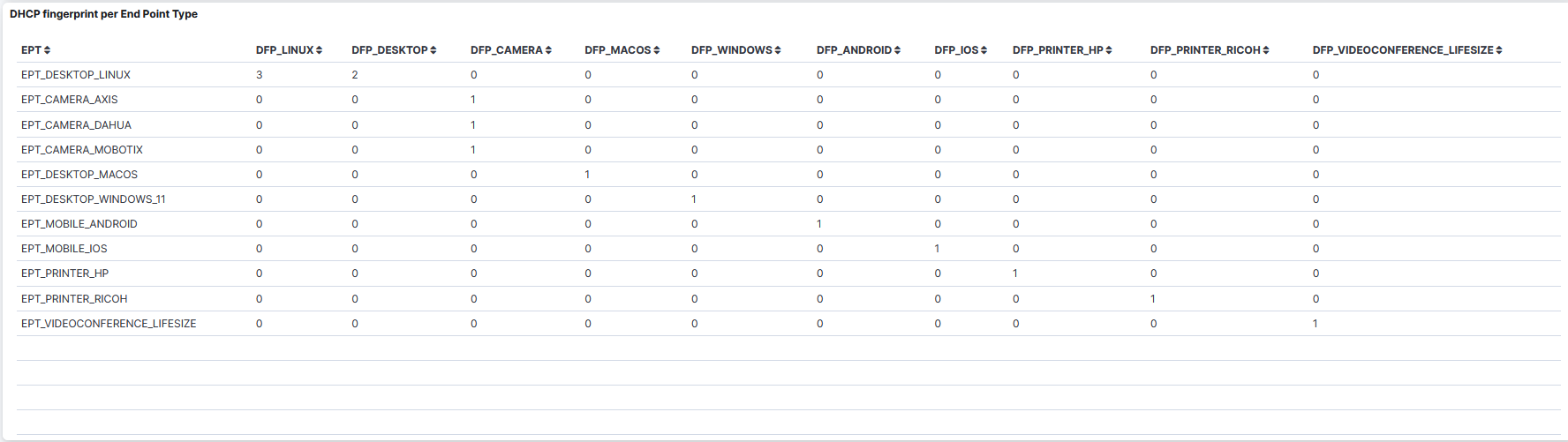
DHCP fingerprint per Endpoint Type: A table that displays the DHCP fingerprint per Endpoint Type.
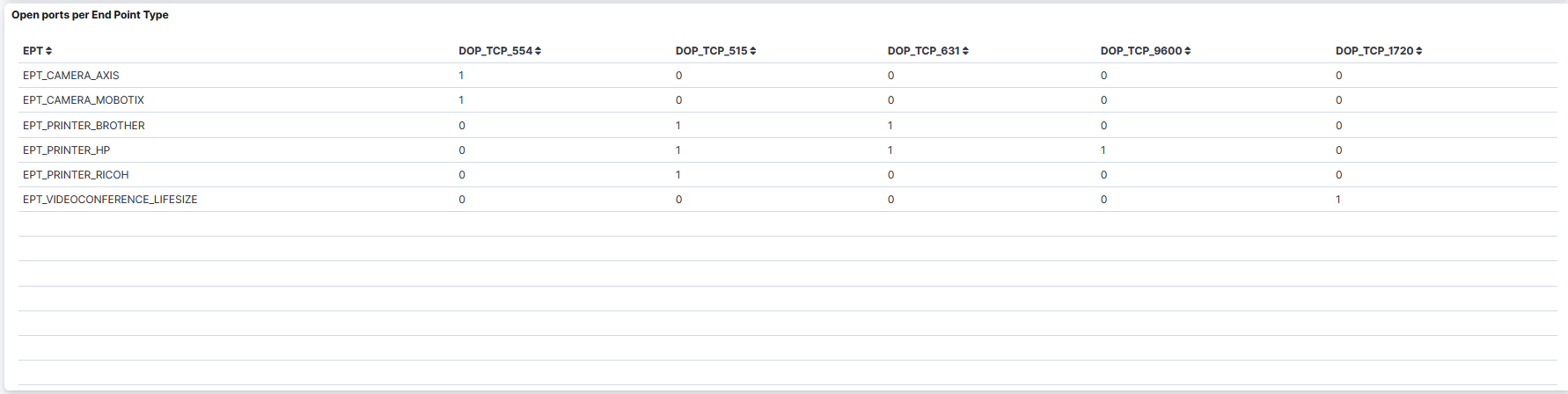
Open ports per End Point Type: A table that displays the open ports per Endpoint Type.
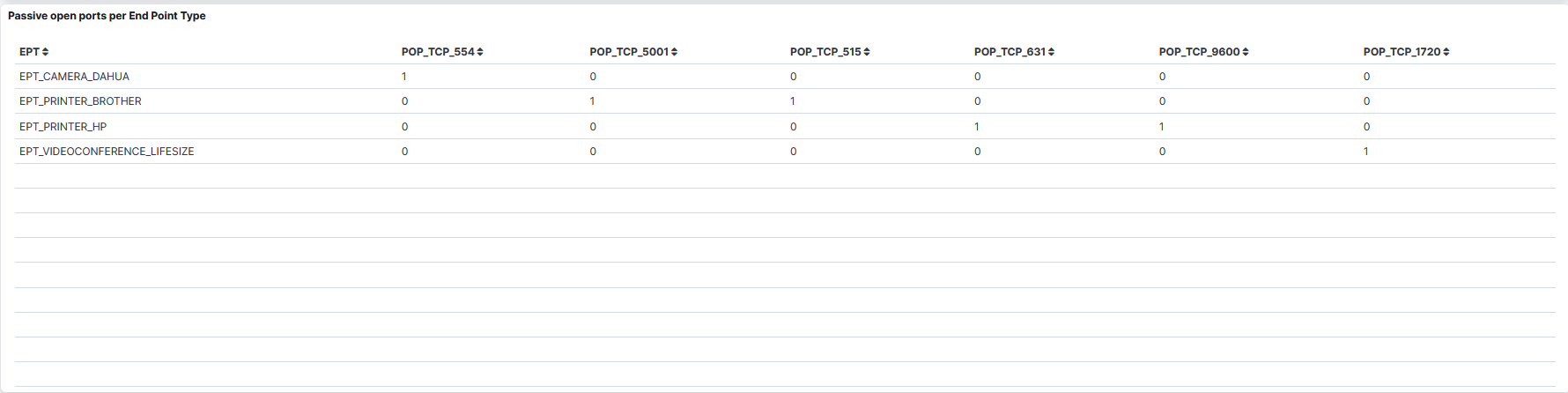
Passive Open ports per End point Type: A table that displays the passive Open ports per Endpoint Type.
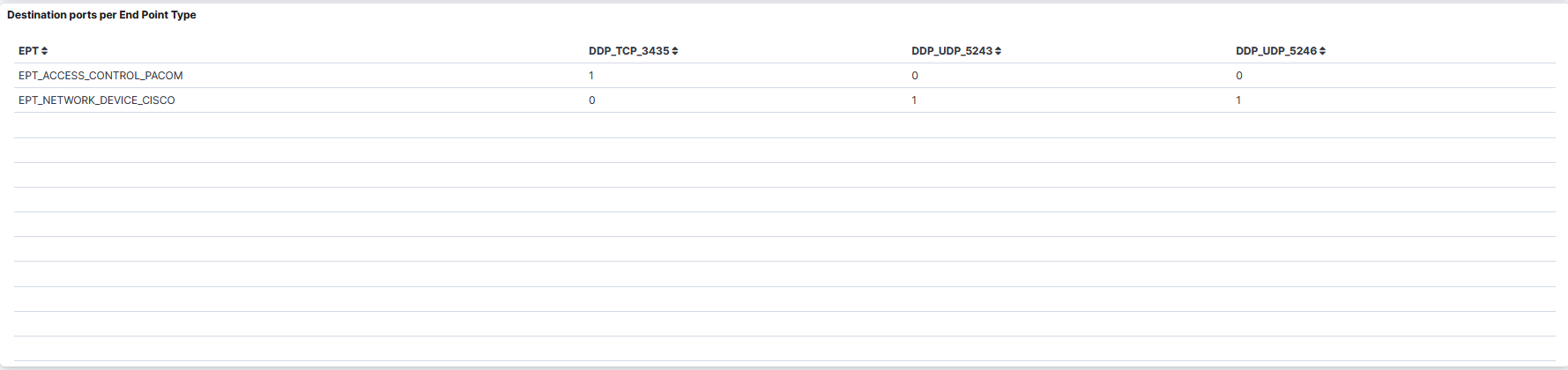
Destination ports per End Point Type: A table that displays the destination ports per Endpoint Type.
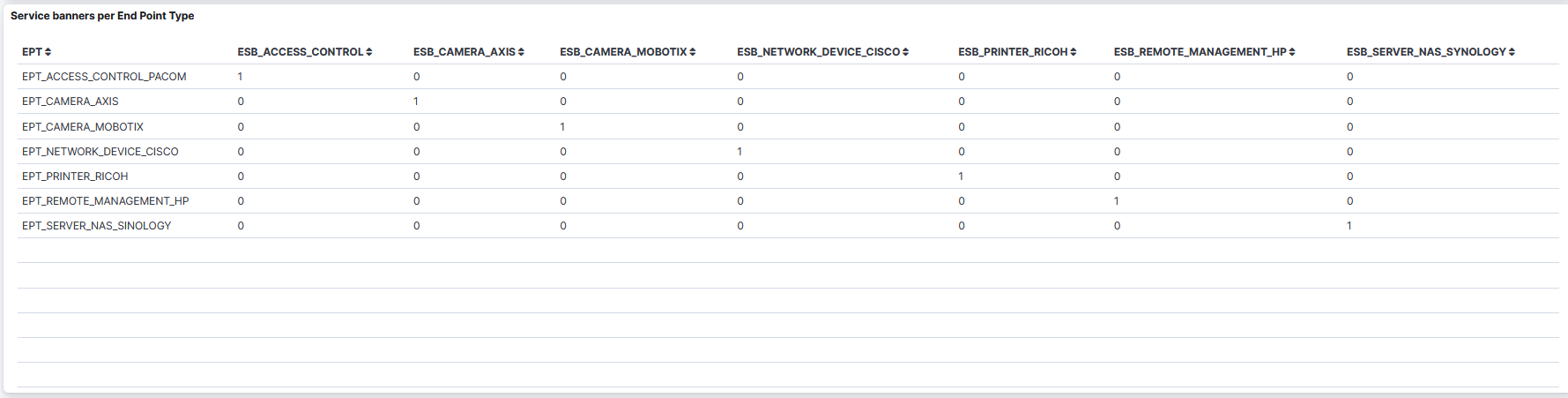
Service banners per End Point Type: A table that displays the service banners per Endpoint Type
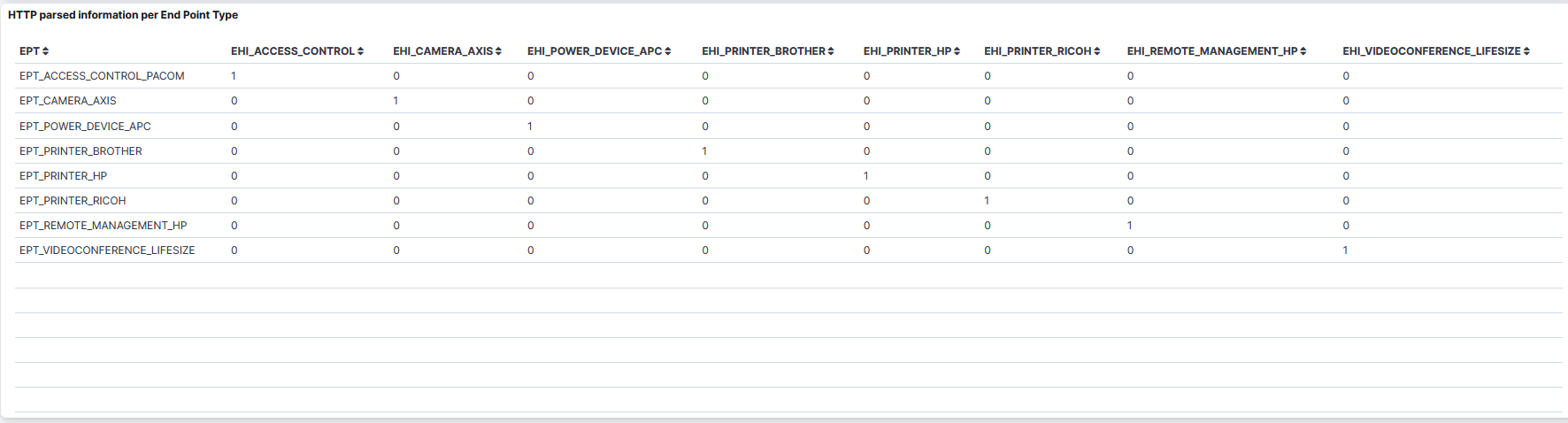
HTTP parsed information per End Point Type: A table that displays the HTTP parsed information per Endpoint Type.
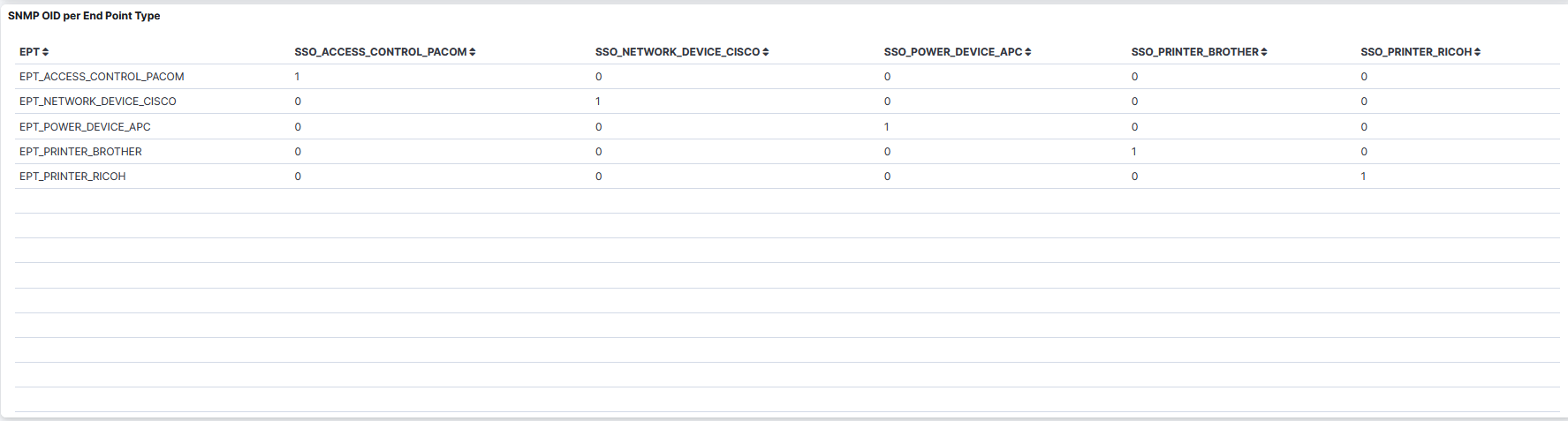
SNMP OID per End Point Type: A table that displays the SNMP OID per Endpoint Type.
Organization Issuer certificates per End Pint Type: A table that displays the Organization Issuer certificates per Endpoint Type.
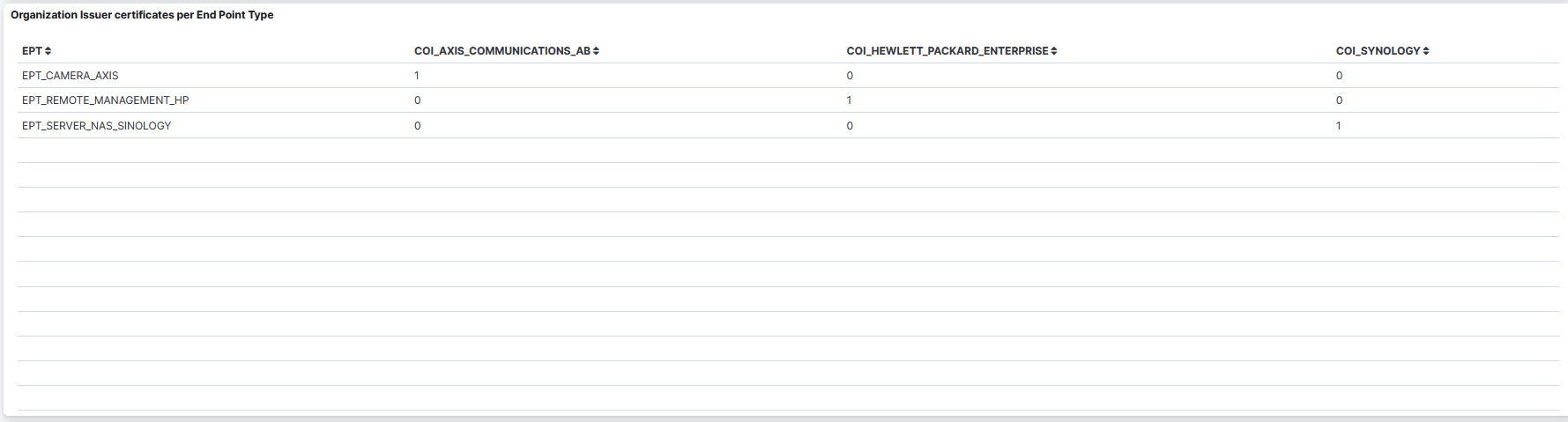
Common Name Subject certificates per End Point Type: A table that displays the Common Name Subject certificates per Endpoint Type.
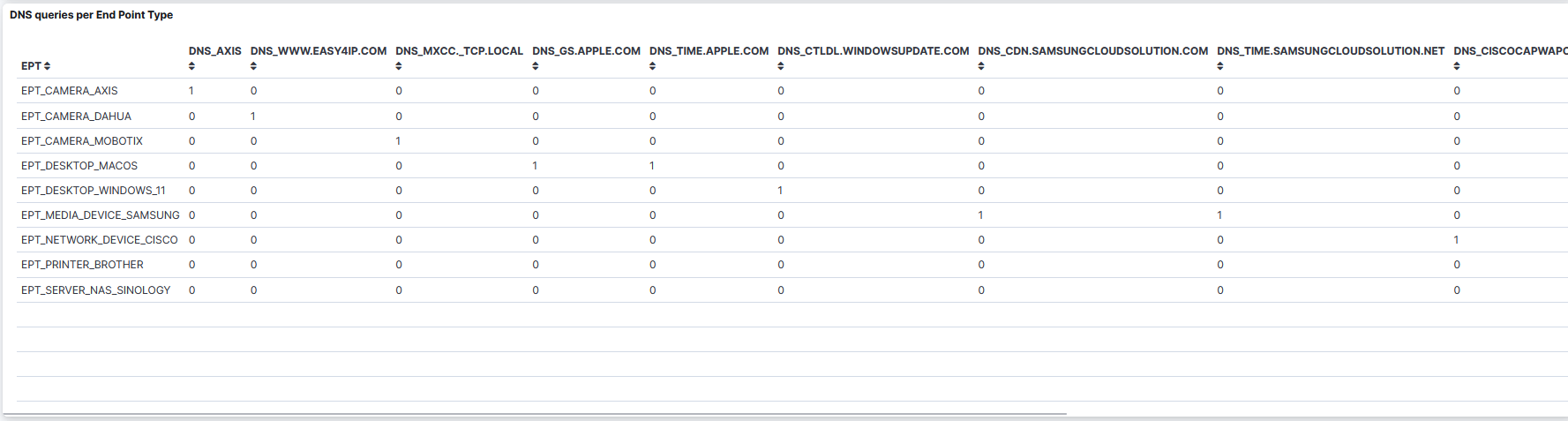
DNS queries per End Point Type: A table that displays the DNS queries per Endpoint Type
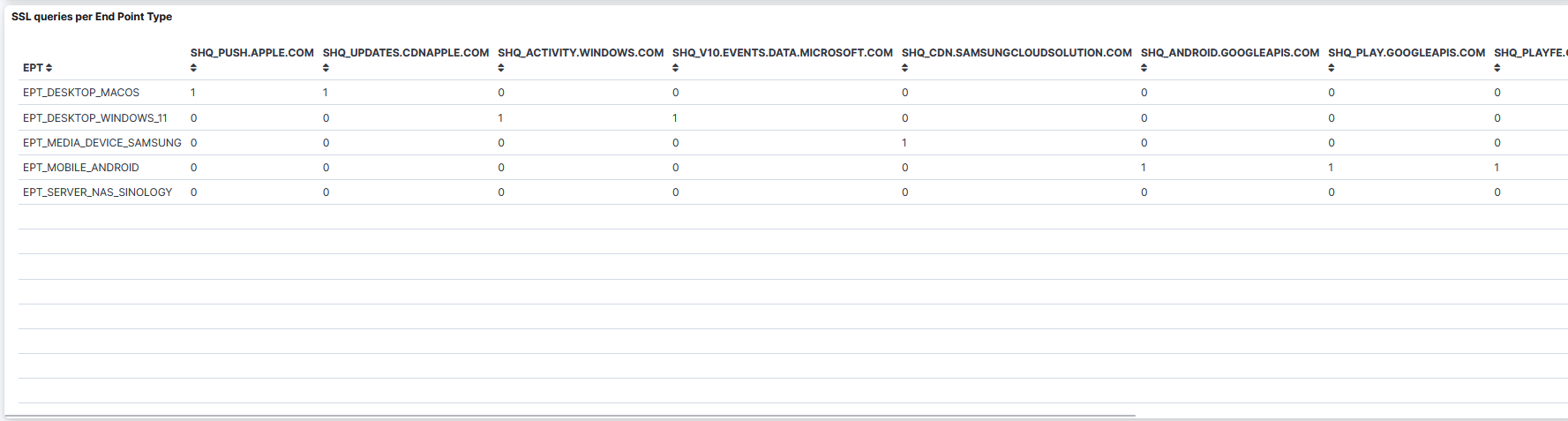
SSL queries per End Point Type: A table that displays the SSL queries per Endpoint Type.
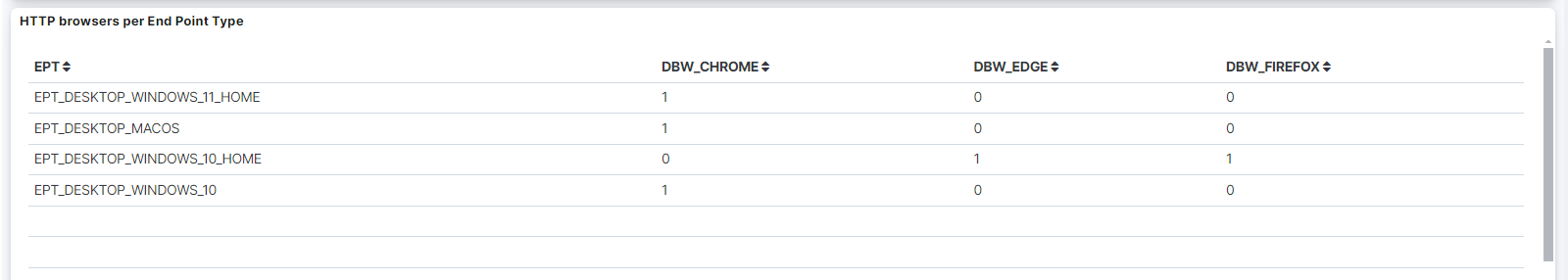
HTTP browsers per End Point Type: A table that displays the HTTP browsers per Endpoint Type.
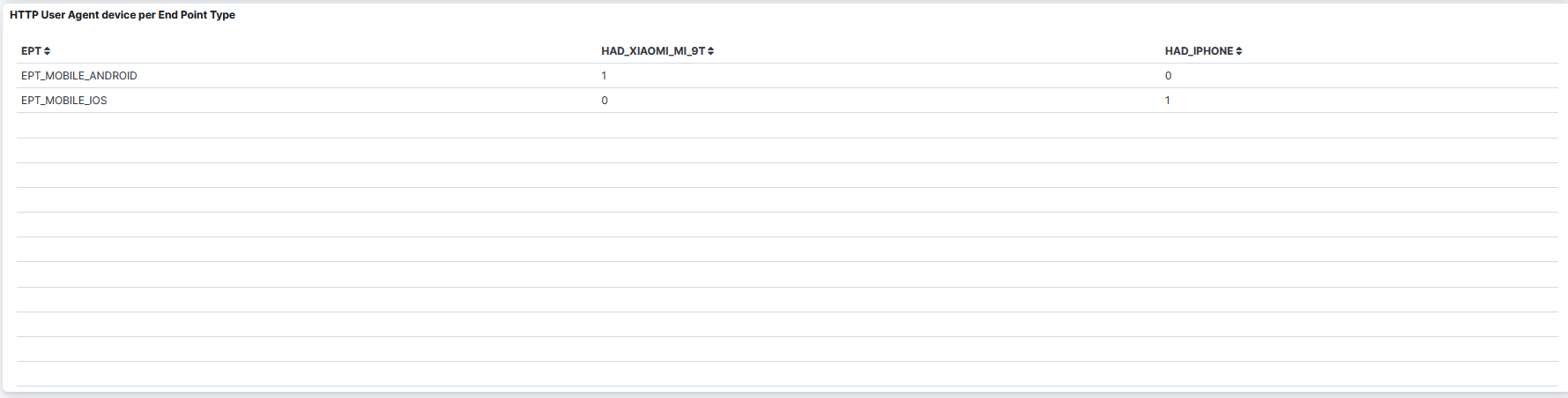
HTTP User Agent Device per End Point Type: A table that displays the HTTP User Agent Device per Endpoint Type.
4.1.7.5. Profiles per VLAN
4.1.7.6. Profiles per VLAN
The Profiles per VLAN dashboard displays the information about User Devices EPT (END POINT TYPE) per VLAN distribution.
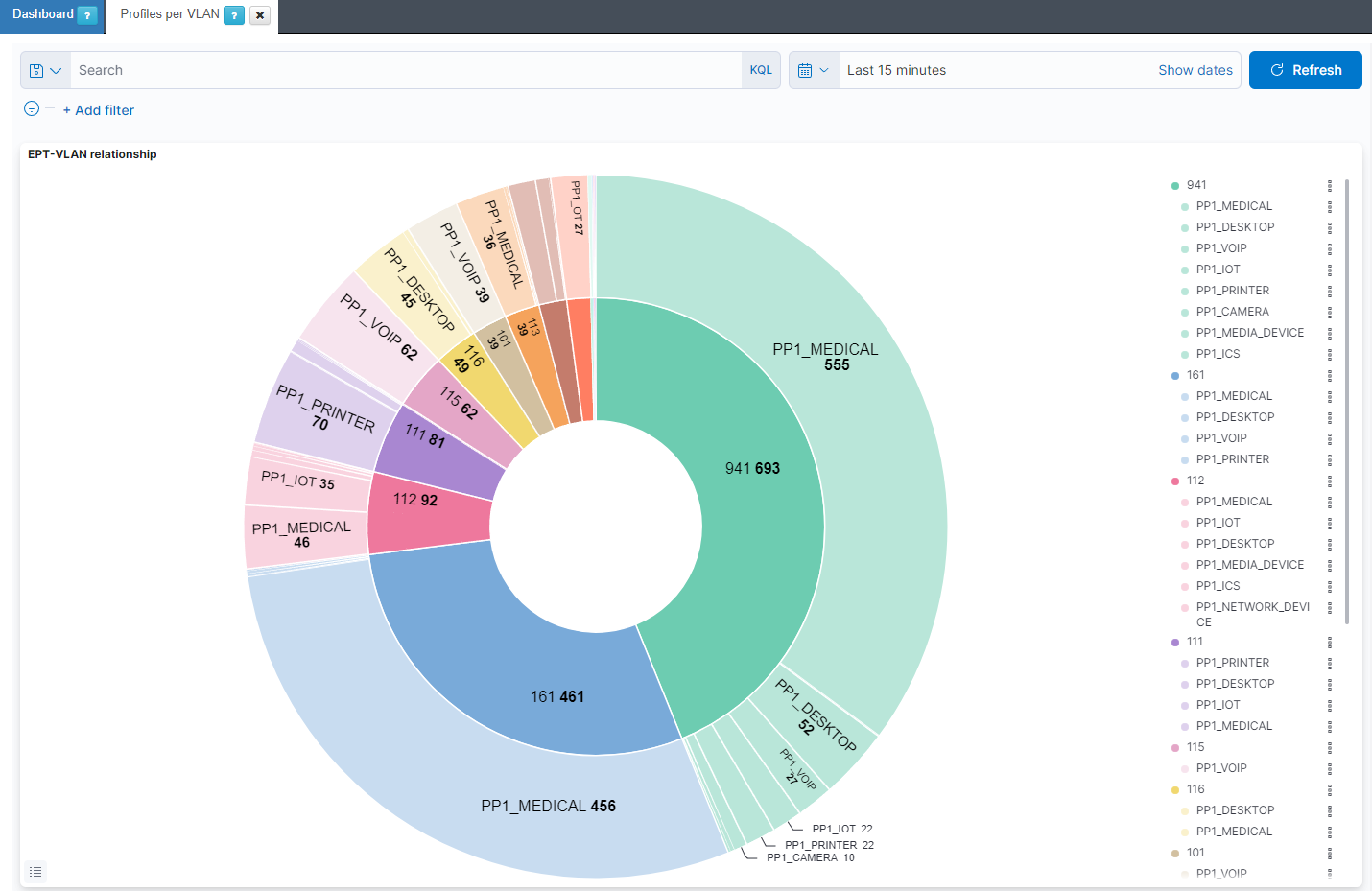
EPT-VLAN relationship: The internal pie represents the number of devices per VLAN. The external pie represents the number of different first profiling hierarchy level PP1 (Parent Profile) for that VLAN.
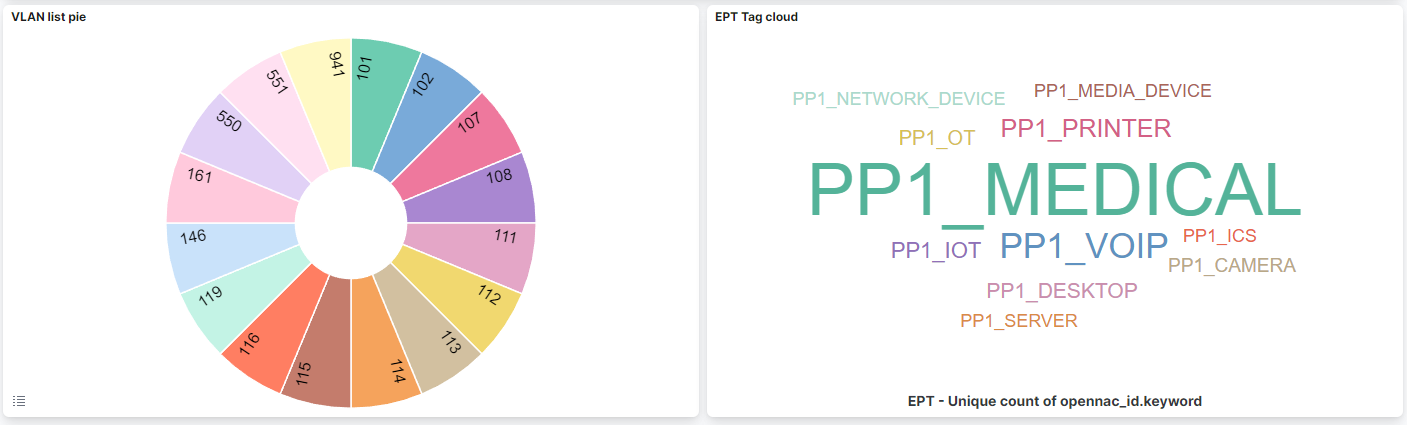
VLAN list pie: The list of VLANs.
EPT Tag cloud: The different level 1 EPTs (PP1 tag), with the largest tags representing the most frequently occurring ones.
4.1.7.7. Profiling Details
4.1.7.8. Profiling Details
Profiling Detail dashboards displays information about devices that have connected to the network and have been profiled.
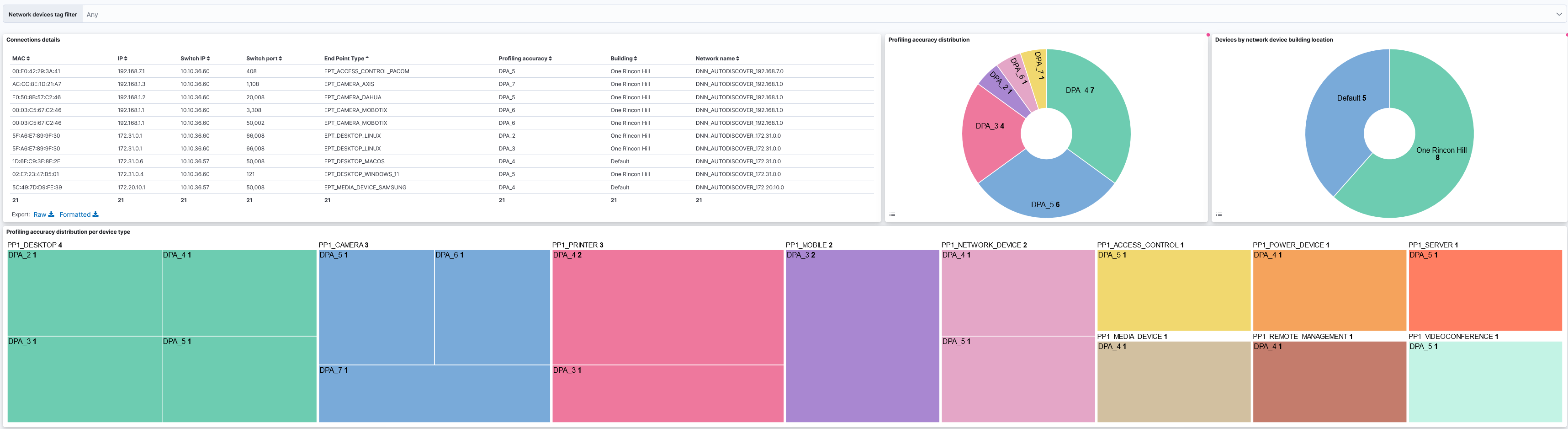
Connections details: Details of the connected devices such as MAC address, IP, Switch IP, Switch port, etc.
Profiling accuracy distribution: Distribution of the profiled devices.
Devices by network device building location: Displays the distribution of connected devices across different buildings within the network.
Profiling accuracy distribution per device type: Profiling accuracy by device type.
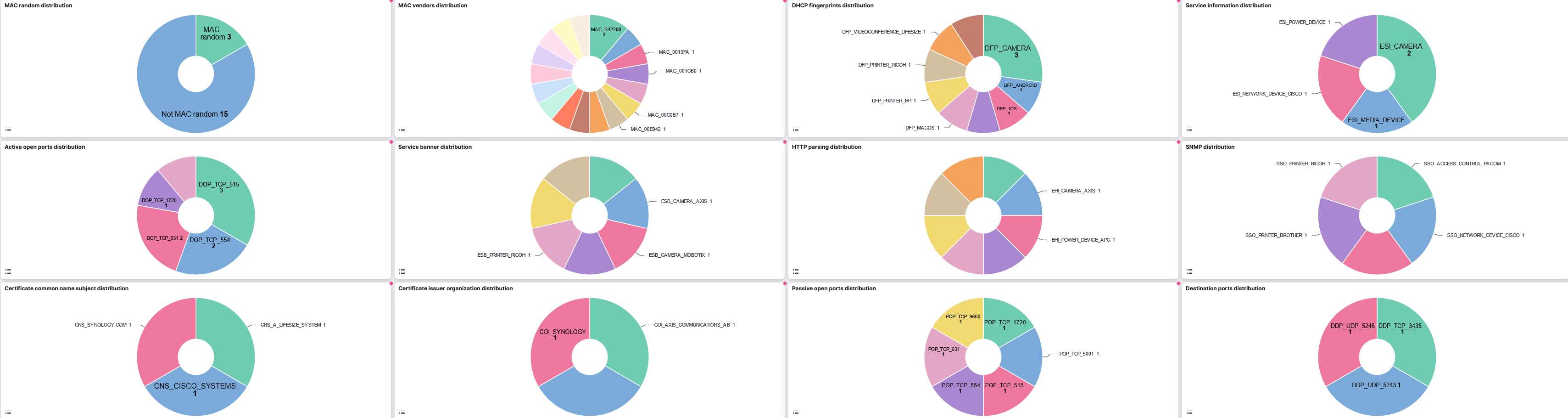
MAC random distribution: Use of randomized vs. static MAC addresses.
MAC vendors distribution: Distribution by MAC address vendor.
DHCP fingerprints distribution: Device distribution based on DHCP fingerprints.
Service information distribution: Breakdown of services used by devices.
Active open ports distribution: Distribution of open ports on active devices.
Service banners distribution: Distribution of service banners.
HTTP parsings distribution: Distribution of parsed HTTP requests.
SNMP distribution: Usage of SNMP across the network
Certificates common name subject distribution: Certificate common names percentage.
Certificates issuer organization distribution: Issuer organization certificates percentage.
Passive open ports distribution: Distribution of open ports on passive devices.
Destination ports distribution: Distribution of destination ports.
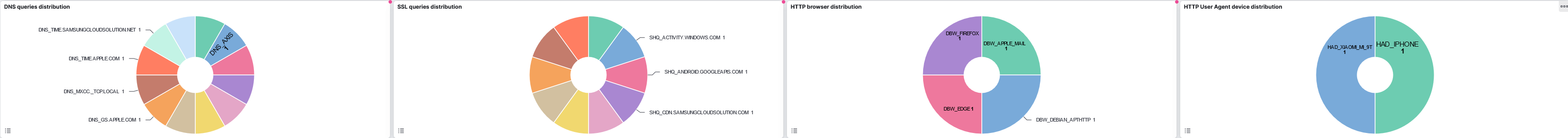
DNS queries distribution: Distribution of DNS queries.
SSL queries distribution: Distribution of SSL queries.
HTTP browsers distribution: Distribution of HTTP browsers.
HTTP User Agent devices distribution: Distribution of HTTP User Agents.