1.4.4.1. User Device Compliance
This module is applied based on the UNAC module, so the operation of compliance may be conditioned by the configuration and operation of the UNAC module. This section only details the processes for implementing the EPC module, so previously it will be necessary to perform the UNAC module.
This use case allows you to check on each endpoint device and the different parameters it has installed such as software, ON Agent, versions and updates, antivirus, specific software versions, etc. After identifying the value of a specific setting, users can create a tag and then use the tag as a precondition in the policy details.
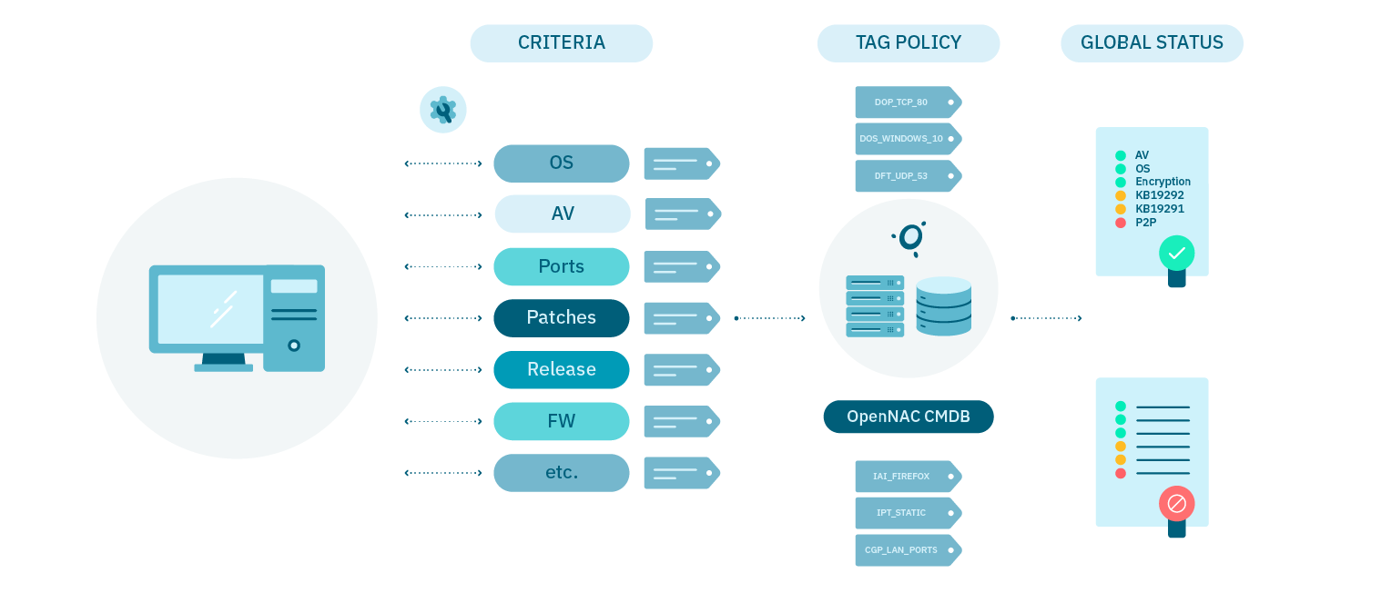
With OpenNAC Enterprise you can define your security baseline for endpoints. This can be as granular as your organization needs. You could also guarantee that no problematic shadow IT is on the endpoint “Torrent” solutions. Switches and APs are a huge vulnerability for organizations and because they are generally managed one by one, there is little control over their status.
Once the policy has been defined, it will be checked against the infrastructure (EP/data centers, network devices). Remember that 99% of the vulnerabilities that are exploited have already been known for more than a year. With a well-defined compliance policy, you can radically reduce your risk of exposure.
OpenNAC Enterprise centrally enables you to respond to any incompliance by establishing multiple enforcements, such as blocking the endpoint, isolating it to a remediation VLAN, automatically sending automated self-help instructions to the end user to remediate the issues, downloading a patch, etc.
When it comes to data centers and switches, you may just want visibility into what is non-compliant to establish an action plan for your equipment.
Policies and compliance status reports can be viewed from the dashboard and reports can be created to show the endpoint posture of your entire organization or drilled down to whatever logic you need.