1.4.5. BYOD
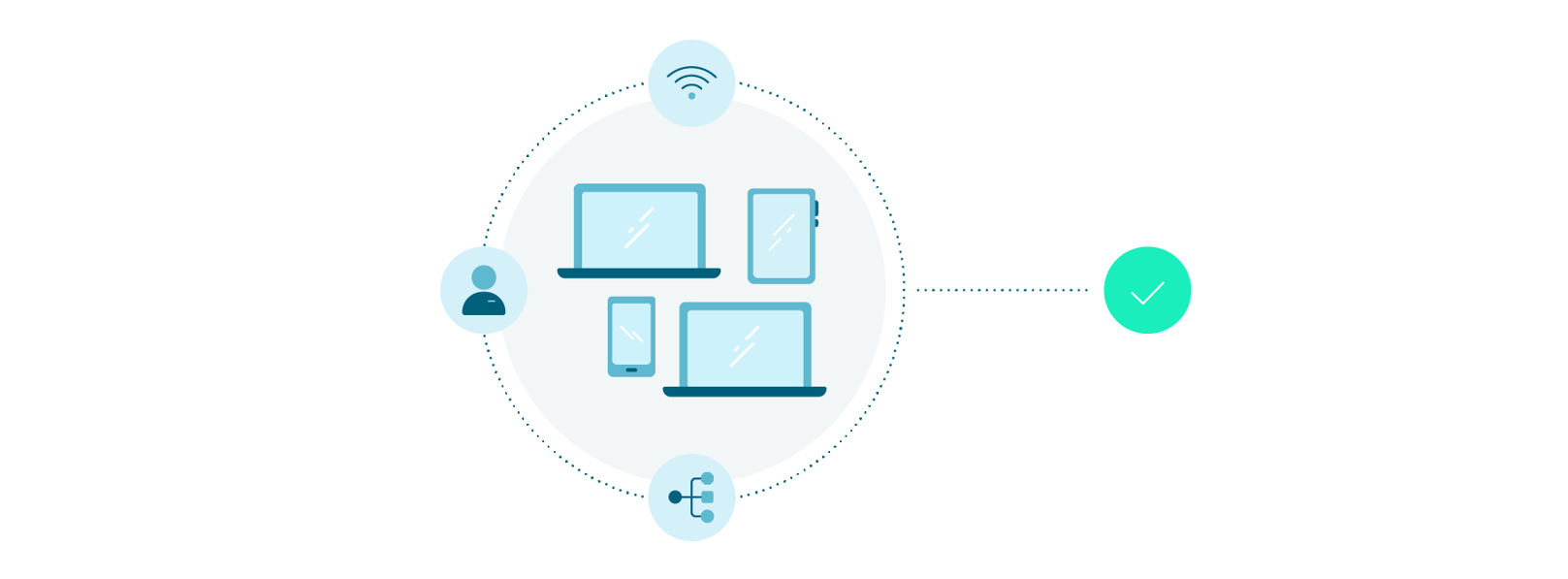
Through BYOD, corporate users will be able to access the network regardless of the device they use through an authentication process.
1.4.5.1. What is BYOD?
BYOD is the module that allows the authentication process of corporate users to be carried out from any device, inheriting all the permissions and access associated with the user’s identity.
Once the network authentication process has been validated, the accesses associated with the identity of corporate users will remain, regardless of the device used. Ensures infrastructure security compliance with corporate policies.
1.4.5.2. BYOD benefits
Discover, monitor, and manage: Discover and manage unexpected BYOD behaviors (postures) for a given entity (profiling) without the need to install an agent.
Ensure compliance and access requirements: Defines the security requirements needed to access the corporate network (such as OS version, etc.).
Optimize team resources: Reduce IT department workload by automating the user registration process with a captive portal.
Authenticate users from any device: It facilitates mobility through the authentication of corporate users from any device, inheriting those permissions and access associated with their identity.
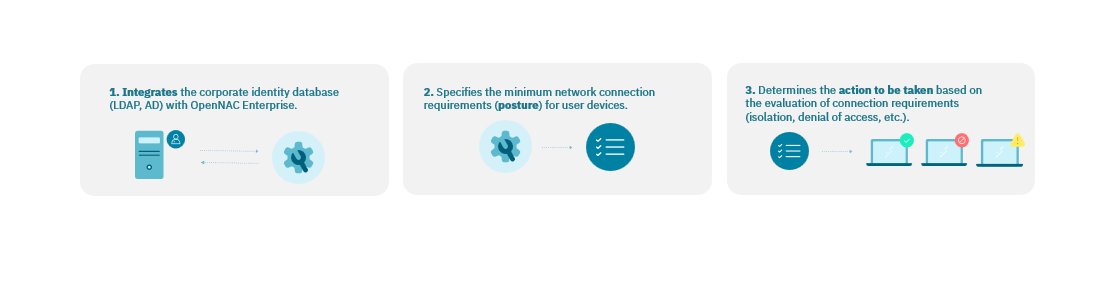
1.4.5.3. BYOD in 3 Steps