2.9.2.21. paloAlto
The Palo Alto plugin allows sending information related to a username and IP along with a PA Dynamic Address Group Tag. An internal OpenNAC Tag can be assigned to the device.
To start, you notify to the firewall the username associated with an specific IP address, and this relationship is active until a logout is received or the User Session Timeout (min.) indicated in plugin properties is exceeded( after that time, without a new notify, the relationship expires). A part from that, you associate the IP address with a Palo Alto dynamic tag, so in Palo Alto firewall you can define a Dynamic Address Group and use it in Palo Alto policies.
To configure the plugin, the next fields must be configured:
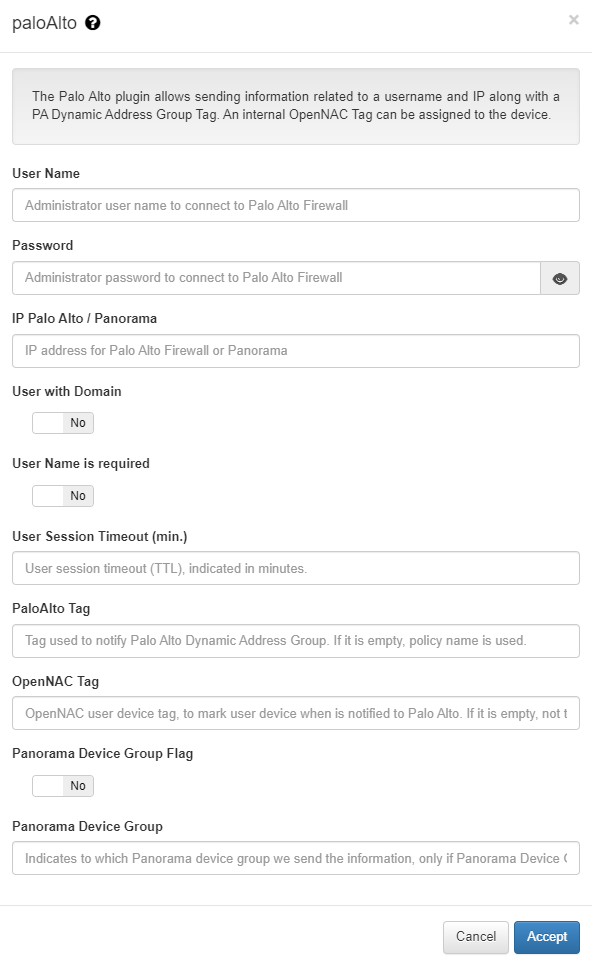
User Name: Administrator user name to connect to Palo Alto Firewall.
Password: Administrator password to connect to Palo Alto Firewall.
IP Palo Alto / Panorama: IP address for Palo Alto Firewall.
User with Domain: It indicates if user name sent to Palo Alto has to include the domain name in case it is included in user request.
User Name is required: It indicates if user name is required to send information to Palo Alto. If it’s required, when a MAB authentication is produced, there could not be a notification to Palo Alto.
User Session Timeout (min.): User session timeout (TTL), indicated in minutes.
PaloAlto Tag: Tag used to notify Palo Alto Dynamic Address Group. If it is empty, policy name is used.
openNAC Tag: openNAC user device tag, to mark user device when is notified to Palo Alto. If it is empty, not tag is used.
Panorama Device Group Flag: It indicates that we have to send the information to an specific Panorama device group.
Panorama Device Group: Indicates to which Panorama device group we send the information, only if Panorama Device Group Flag is active.
Note
To connect to Palo Alto, only a user with “XML API – User-ID Agent” rights is required, so “Web UI” and “Command Line” rights can be disabled.
PaloAlto NGFW technologies includes an API that needs to have a credentials to be accessed.
In case that Palo Alto is integrated with Active Directory or LDAP servers is required, in case other types of users are used this must be indicated, this means that user session information is exchange between PaloAlto and openNAC allowing to define sessions timeout to force to be authenticated and also use the User Device tags when Palo Alto is notified.