4.8.1. Captive Portal with Microsoft 365 Authentication (SAML)
One of the possible use cases within OpenNAC Enterprise is the authentication through Microsoft 365 credentials through the Captive Portal.
For this, we can use the webauth-registered-users flows of the captive portal and, through SAML type authentication, use the Microsoft credentials to access the network.
In this example, we will see the minimum required to access a Wi-Fi network through Microsoft 365 authentication.
Note
By using Microsoft 365 as IdP we can use Microsoft 2FA (Microsoft Authenticator) during authentication if users have it enabled.
4.8.1.1. Minimum requirements for the use case
- OpenNAC Enterprise:
On Principal.
ON Core (external or installed in ON Principal).
Additionally we can deploy the ON Analytics and ON Aggregator machines to maintain use case data.
- Wireless Lan Controller:
Compatible network electronics (approved for OpenNAC Enterprise).
- Microsoft:
Application in Azure to act as IdP of Microsoft 365.
The steps to configure this use case are:
4.8.1.2. Create a new application that acts as an IdP in Azure
To use Microsoft 365 credentials through an Azure IdP we will need to create a new application in Azure.
4.8.1.3. Configuration on OpenNAC Enterprise
4.8.1.3.1. Creation of a new 8021X policy
The policy we need for captive portal flow authorization has the following basic characteristics:
General - Name: Name of the policy.
Preconditions - Network Devices: Here we can filter by network device (WLC) and even by the SSID of the network to which the client connects.
Preconditions - Sources: The authentication source in this use case will be “Supplicant User”
Postconditions - VLAN: VLAN to be assigned, 0 if it is the default.
It is possible to add configurations to the policy in case you want to give more flexibility to the use case.
4.8.1.3.2. Creation of a new Workflow of type webaut-registered-users
In the ON Captive -> Captive workflows section, we must add a new workflow:
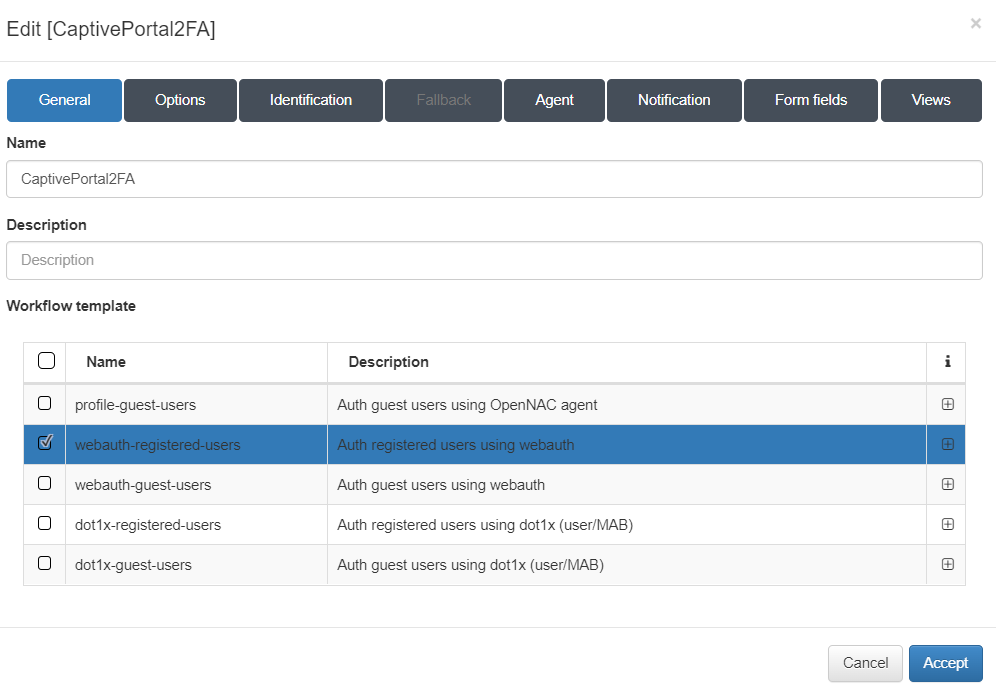
General:
Name: Name of the new workflow. Description (optional): Description of the new workflow. Workflow template: This new workflow should be of type “webauth-registered-users”
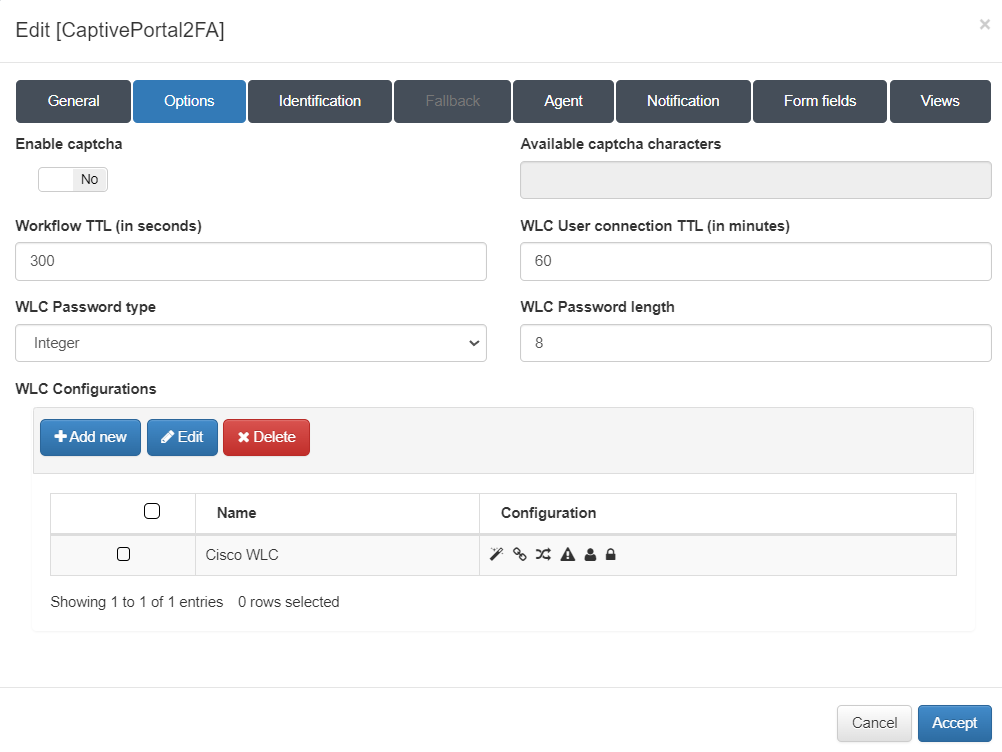
Options:
Here we must configure the workflow options. These must be correlated with the configurations of the WLC to be used. In the “WLC Configurations” section we must add all those WLCs that are going to be used (Cisco, Aruba…)
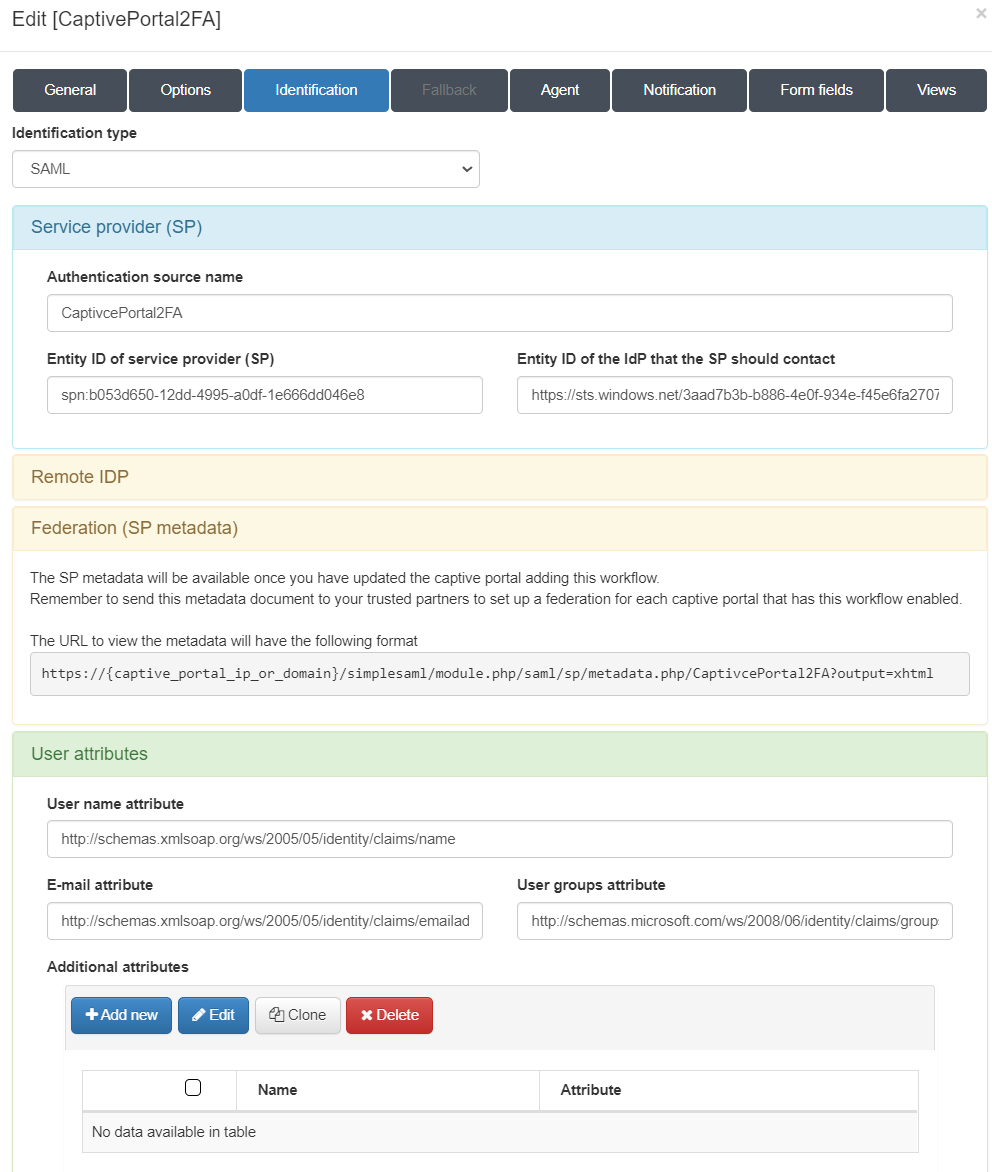
Identification:
Here we must configure the authentication method that will be used in the workflow, in this case, when using Microsoft 365 we will do it through SAML.
Service provider (SP) - Authentication source name: Name of the new SP. - Entity ID of service provider (SP): Entity ID that will be assigned to the SP. For it to work correctly, it must have the following format: spn:<Application (client) ID>
<Application (client) ID> corresponds to the name of the application (IdP) created in the Microsoft Azure portal.
Entity ID of the IdP that the SP should contact: EntityID of IdP (we can find this information in the metadata of the IdP)
Remote IDP: - Here we must add the metadata for the federation (in PHP format) of the IdP.
Federation (SP metadata) - This field will be updated with the URL where we will find the metadata of the SP once we have saved this flow.
User attributes - These are the names of the attributes that will be sent to us from the IdP.
4.8.1.3.3. Captive Portal configuration
Once the workflow is configured, you must add it to the instance of the captive portal when configuring the captive portal instance.
4.8.1.4. Configuration on the WLC (Cisco example)
The last point to configure is the WLC with the new network and the authentication configuration through OpenNAC Enterprise.
We can see an example with a Cisco WLC here.
Important
It is very important that the preauth-ACLs are well configured. They must allow traffic to both the OpenNAC Enterprise captive portal and Microsoft 365 authentication portal URLs (or IPs).
We can find the URL for the Microsoft authentication in https://learn.microsoft.com/en-us/azure/azure-portal/azure-portal-safelist-urls?tabs=public-cloud
4.8.1.5. Workflow example
When accessing the captive portal, the OpenNAC Enterprise portal will appear for us to accept the terms and conditions:
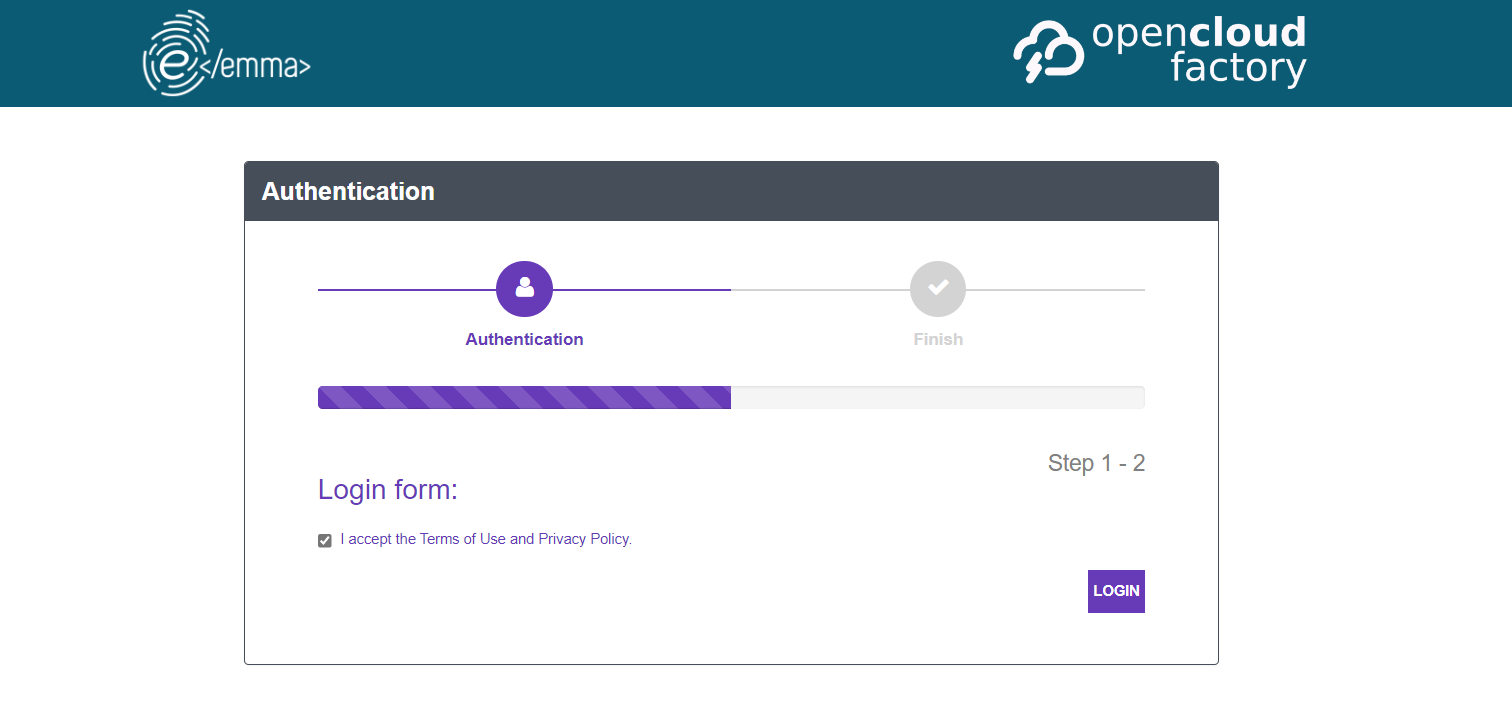
After clicking on Accept, the portal will redirect us to the IdP (Microsoft 365) so that we can authenticate ourselves.
Once authenticated in Microsoft 365, we will return to the Captive Portal and access the network.