4.7.2.3. Architecture
This section outlines the necessary nodes for the use case, offering essential information on its architecture, including components, simplified architecture, and recommended sizing.
4.7.2.3.1. Components
2SRA module deployment requires a Backend composed of additional components; the integration and users authentication with the corporate identity manager, the management of the GAuth OTP, the centralization of logs, traffic monitoring, among others.
4.7.2.4. ON Core
ON Core provides the centralized management console of the solution. It is where the Visibility policy engine for discovery resides. This device runs the logic that processes and validates asset profiling based on multiple conditions and characteristics. It also runs plugins to enrich profiling in a active or passive way.
It is a mandatory component of the solution and includes critical components such as:
Policy Engine: It is the solution’s brain. All modules are implemented using this component.
CMDB: It is the memory of the solution where all the configuration, assets and its features are saved.
VPNGW: Allows the remote centralized management of the VPN Gateway nodes and its configuration.
The administration portal is the control panel for the solution.
Note
The ON Core is a critical component of the solution. The implementation of one or more nodes to ensure high availability will depend on the deployment requirements and the final architecture design.
If this component goes offline, the solution will lose the ability to authenticate requests.
4.7.2.5. ON Analytics
ON Analytics is based on the ELK Stack, receives the platform logs, structures, metadata and builds the datalake to show dashboards and reports in real time to allows the specific searches.
It is a mandatory component of the solution that includes non-critical components such as:
Aggregator: an enrichment of all the information generated by any component of OpenNAC Enterprise.
Search Engine: based on an elastic search engine that allows you to easily search the information generated and collected by the OpenNAC Enterprise components.
Dashboards and reports: The solution includes a set of dashboards and reports based on common technical information gathered. You can create and generate your own custom dashboards.
Note
ON Analytics is a non-critical component of the solution and therefore does not require high availability. The decision to implement one or more nodes will depend on the specific deployment requirements and the final architecture design.
If this component is taken offline, the main functionality of the OpenNAC Enterprise modules will remain operational. However, during this downtime, the system will not be able to process or display solution-related data.
In deployments where large volumes of data are generated, it may be necessary to deploy multiple Analytics nodes to balance the storage load.
The Analytics component has two roles, typically running on the same node:
Aggregator: This role receives information via Filebeat and processes logs using Logstash.
Analytics: This role handles data management through Elasticsearch and provides data
4.7.2.6. ON Agent
The Agent is a software that is installed in the end for VPN connection establishment, monitoring and the hardware/software posture of the device. It is required for the Secure Remote Access (2SRA) module.
Allows you to manage and perform a detailed analysis of the device inventory (for example, OS patches, health and security features, deployed applications, etc.)
Establishment of the VPN tunnel, and validation of credentials using 2FA. 3. ON Agent
4.7.2.7. ON Sensor
ON Sensor is based on IDS technology, it processes the traffic generated in the network. Performs a deep analysis of network protocols that are being used by ingesting the traffic through a port-mirror (SPAN, RSPAN or ERSPAN).
It is an optional component that provides:
Network Behavior Monitoring. Provides metadata of network traffic that is captured by copying the traffic through the port-mirror configured on the network device. It is capable of decoding multiple standard protocols and applications, providing information from layer 2 to layer 7.
Note
ON Sensor is is a non-critical component for the solution, therefore, it does NOT require high availability. If this component is outlined, the main functionality of OpenNAC Enterprise modules would continue working, with the exception that during the outlined period we would no longer have the ability to have advanced visibility, analysis and monitoring of network behavior.
4.7.2.8. ON VPNGW
The VPN Gateway provides the ability to establish the VPN from a remote location to the corporate network. It maintains the system update packages and the object base (networks, hosts, protocols, means of authentication, etc.) to distribute among the different VPN Gateways.
The Administration Portal VPNGW module provides the centralized management of all the VPNGW nodes.
It is a mandatory component for the Secure Remote Access (2SRA) module, which includes critical features such as:
Manage VPNGW: This section allows you to manage the VPN Gateway nodes, configure workers and also manage the WireGuard and Shorewall protocols.
CMDB: From this section you can manage your Objects, Radius authentications, Certificate authorities, and Server certificates.
FARM: This section allows you to manage and configure the nodes that you have previously created in the “Manage VPNGW” section.
Note
It is a critical node in the solution and high availability deployment is recommended. The deployment of one or more nodes to provide high availability will depend on the deployment requirements, and the final architecture design. With this module offline we would lose the ability to establish VPN connections
4.7.2.8.1. Standard Architecture
A reference architecture requires the components described above and depends on the network architecture available to the customer, as well as the number of end users on the network. Based on the criticality of the components and location in the network, the following should be considered points:
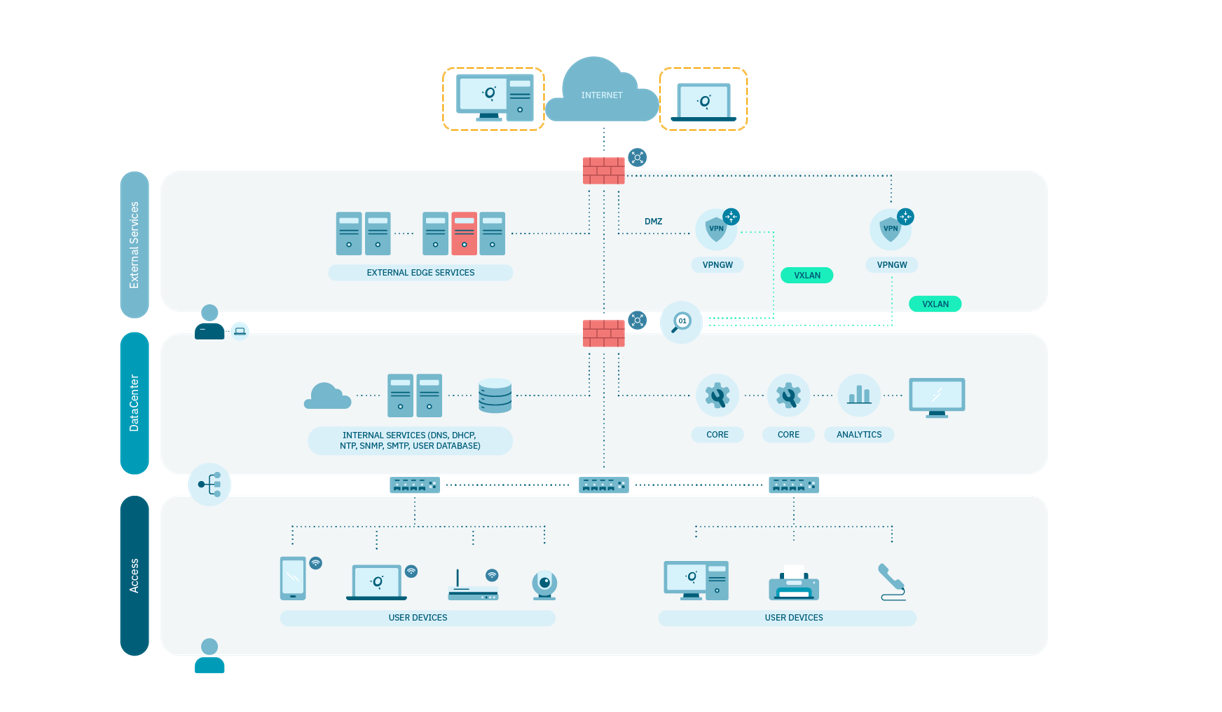
The VPN Gateway needs to have internet access for clients to connect. It is the only component that needs to be exposed to the internet, and it is recommended to install it in a DMZ network separate from the published, internal servers, and the others solution components.
Note
Deployment in high availability will depend on the customer’s requirements. If a HA deployment is required, it will be necessary to add additional components (two or more VPN Gateways).
4.7.2.8.2. Standard Sizing
Based on the reference architecture, the standard sizing of the solution for 2SRA module to support up to 1.500 network users and average traffic of 400kbp.
4.7.2.8.2.1. Sizing
Concurrent user growth is achieved by adding more nodes in an N + 1 scheme through a RADIUS proxy or load balancer.
Component |
Number |
CPU |
Memory |
Disc/Type |
Network Int. |
|---|---|---|---|---|---|
VPN Gateway |
4 Cores |
8 GB |
100 GB/SSD |
2 NIC** |
|
ON Core |
8 Cores |
16 GB |
160 GB/SSD |
2 NIC** |
|
ON Analytics |
8 Cores |
16 GB |
300 GB/SSD |
2 NIC** |
|
ON Sensor |
8 Cores |
16 GB |
100 GB/SSD |
|
|
ON Agent |
N |
Note
** The 2 network interfaces are mainly for service and management (internal communication between the different nodes)
*** In some cases, it is recommended to have at least 2 NICs for active-passive port-span.
4.7.2.8.3. Component flows
The following tables outline the firewall rules for the nodes involved in the 2SRA use case:
ON CORE
Source |
Destination |
Port |
Service |
|---|---|---|---|
Princ/Worker |
All the components |
TCP/22 |
SSH |
Princ/Worker |
NTP Server |
UDP/123 |
NTP |
Princ/Worker |
DNS Server |
UDP/53 |
DNS |
Princ/Worker |
SMTP Server |
TCP/25 |
SMTP |
Princ/Worker |
SMTP Server |
TCP/587 |
SMTPS |
Princ/Worker |
Analytics |
TCP/5601 |
Kibana |
Princ/Worker |
Analytics |
TCP/9200 |
ElasticSearch |
Princ/Worker |
Analytics |
TCP/5000 |
FileBeat |
Princ/Worker |
Analytics |
UDP/161 |
SNMP |
Princ/Worker |
AD/LDAP Server |
UDP/TCP/88 |
KERBEROS |
Princ/Worker |
AD/LDAP Server |
TCP/135 |
DCOM/RPC |
Princ/Worker |
AD/LDAP Server |
UDP/TCP/137 |
NETBIOS |
Princ/Worker |
AD/LDAP Server |
UDP/TCP/138 |
NETBIOS |
Princ/Worker |
AD/LDAP Server |
UDP/TCP/139 |
NETBIOS |
Princ/Worker |
AD/LDAP Server |
TCP/389 |
LDAP |
Princ/Worker |
AD/LDAP Server |
TCP/636 |
LDAPs |
Princ/Worker |
AD/LDAP Server |
TCP/445 |
SMB |
Princ/Worker |
AD/LDAP Server |
TCP/464 |
KPASSWD |
ON ANALYTICS
Source |
Destination |
Port |
Service |
|---|---|---|---|
Analytics |
Princ/Worker |
TCP/80 |
HTTP |
Analytics |
Princ/Worker |
TCP/443 |
HTTPS |
Analytics |
Princ/Worker |
TCP/6379 |
Redis |
Analytics |
Princ/Worker |
UDP/25826 |
Collectd |
Analytics |
NTP Server |
UDP/123 |
NTP |
Analytics |
DNS Server |
UDP/53 |
DNS |
ON SENSOR
Source |
Destination |
Port |
Service |
|---|---|---|---|
Sensor |
Princ/Worker |
TCP/80 |
HTTP |
Sensor |
Princ/Worker |
TCP/443 |
HTTPS |
Sensor |
Princ/Worker |
TCP/6379 |
Redis |
Sensor |
Princ/Worker |
UDP/25826 |
Collectd |
Sensor |
Princ/Worker |
TCP/4730 |
Gearman |
Sensor |
Analytics |
TCP/5601 |
Kibana |
Sensor |
Analytics |
TCP/9200 |
ElasticSearch |
Sensor |
Analytics |
TCP/5001 |
FileBeat |
Sensor |
CMIX (VPN) |
UDP/4789 |
VXLAN |
Sensor |
NTP Server |
UDP/123 |
NTP |
Sensor |
DNS Server |
UDP/53 |
DNS |
ON VPNGW
The following table outlines the firewall rules for the ON VPNGW component: