2.6.5. Security Profiles
We can create Security profiles (access lists) objects that can be used from the policy engine as a postcondition parameter, to use it as a RADIUS parameter to communicate with a network device. Security profiles can be assigned to any user ingress port during its network access. This allows us to define an access list that allows or denies access for the ingress traffic at end users’ access ports.
We have two types of Security profiles:
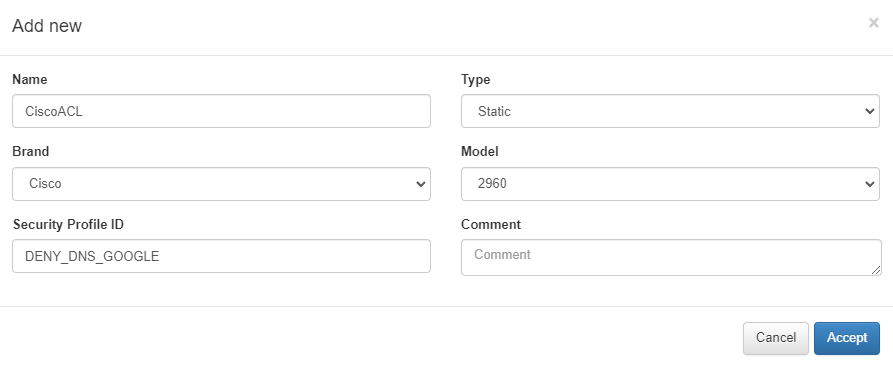
Static: The access list must be previously defined in the network device so we can use and call it from the policy engine. For static security profiles, we define just the name or ID of the security profile, this must match the ACLs defined in the network devices. As soon as the user devices or the user access the network and the security policy is triggered this Security profile is sent via RADIUS.
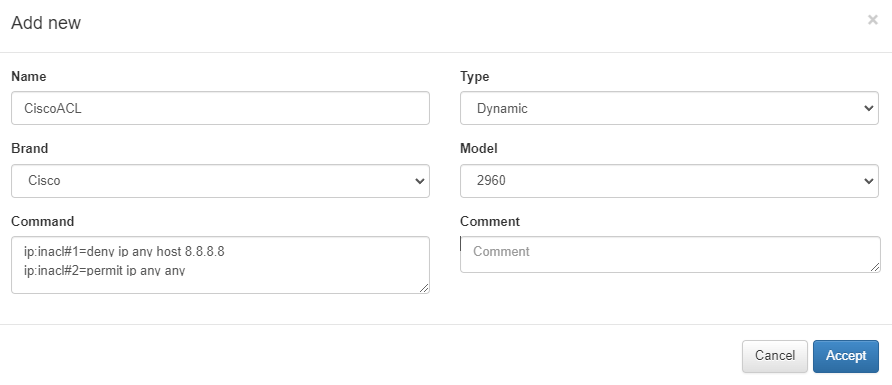
Dynamic: In this case, we can run a security profile command directly to the network devices from OpenNAC Enterprise without any previous definition on the network device, so it will be applied “remotely”. A dynamic security profile IS where you define which command should be sent to the network device. in this case the ACLs sent to the network devices allow specific traffic in the user port.
Static configuration:
First, we will need to apply a specific ACL configuration on the network device so we can refer to them from the OpenNAC Enterprise system.
For example, configuring a Cisco 2920:
ip device tracking
ip access-list extended DENY_DNS_GOOGLE
deny ip any host 8.8.8.8
permit ip any any
To refer to the configured ACL, we have define the security profile ID in the OpenNAC Enterprise :
Dynamic configuration:
It is only required to execute the configuration bellow on OpenNAC Enterprise using the “Command” field.
ip:inacl#1=deny ip any host 8.8.8.8
ip:inacl#2=permit ip any any