4.2.8. Troubleshooting
In order to troubleshoot the UNAC use case, we have considered the following sections. Carefully review the topics to see if they can solve your problem.
4.2.8.1. Troubleshooting Process
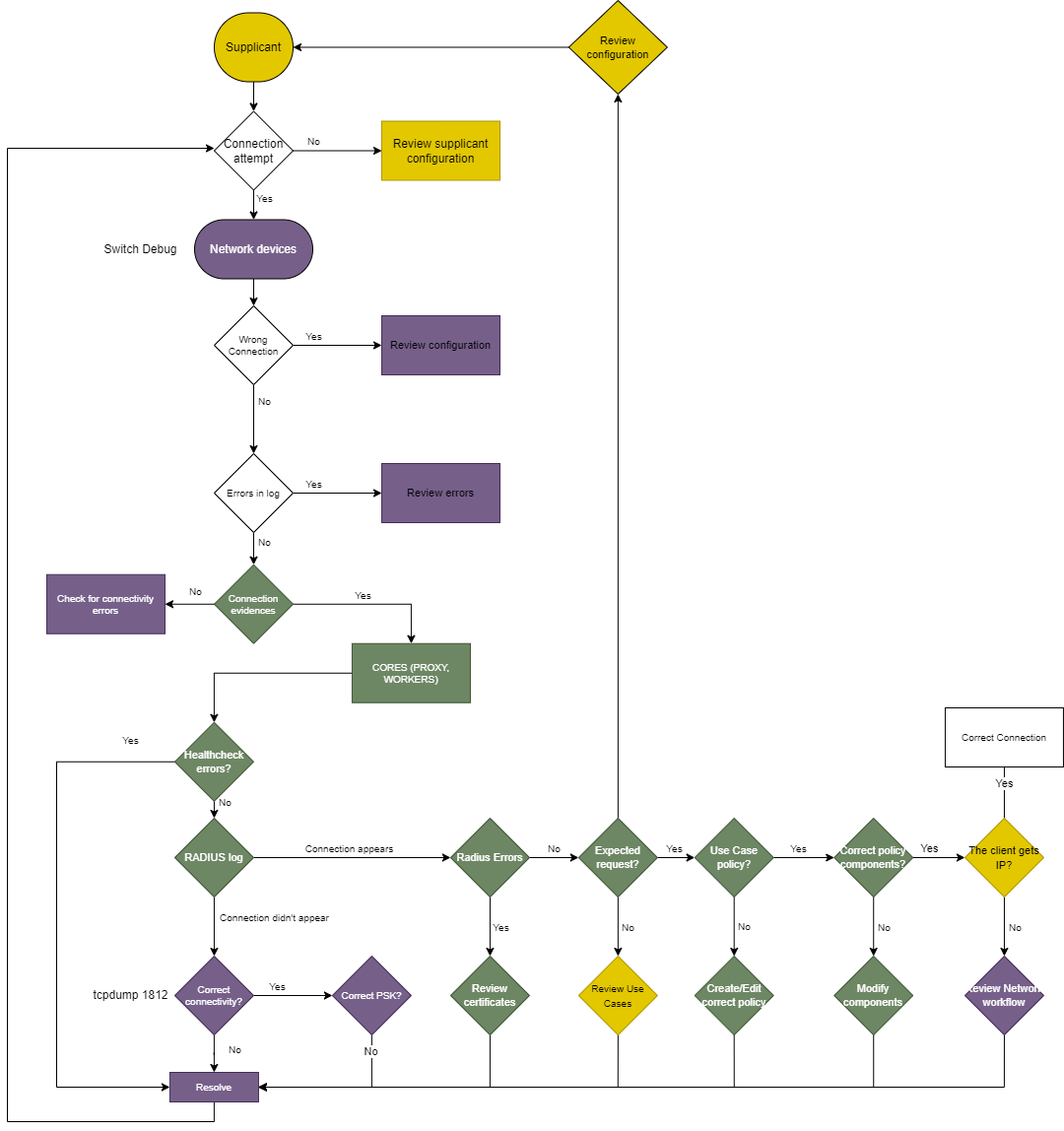
In the following diagram, we can see the flow that we should follow when identifying problems in the use case of UNAC.
At the connectivity level, we can verify that the requests are reaching OpenNAC Enterprise using a tcpdump on the authentication and accounting port:
tcpdump -i any port 1812 or port 1813 -v
When reviewing the flows, it is important to see the system logs to be able to identify where the problem is. Some of these logs are:
RADIUS Logs
Logs related to the RADIUS module (authentication failures, wrong shared-key, etc.):
tail -100f /var/log/radius/radius.log
API log
Here we can see information about the calls to the Core API, for example the execution of synchronous plugins, evaluation of policies, etc:
tail -100f /var/log/opennac/opennac-api.log
Poleval Log
Logs related to the evaluation of policies defined in ON Core:
tail -100f /var/log/opennac/opennac-poleval.log
Jobs Log
Here we can see information about the jobs to be executed by the Core, for example the execution of asynchronous plugins:
tail -100f /var/log/opennac/opennac-job.log
Queues Log
Here we can see information about the ON Core execution queues, for example the automatic post-REEVAL Toggle Ports:
tail -100f /var/log/opennac/opennac-queues.log
4.2.8.1.1. Debug radius Module
To execute a more extensive debug of the radius module, we can execute the command:
raddebug -t0
This will show us a real-time debug of the radius module and its execution.
If we know any parameter of the connection that we want to debug, we can add it as a filter as follows:
raddebug -t0 -c 'Calling-Station-Id == "00-01-02-03-04-05"'
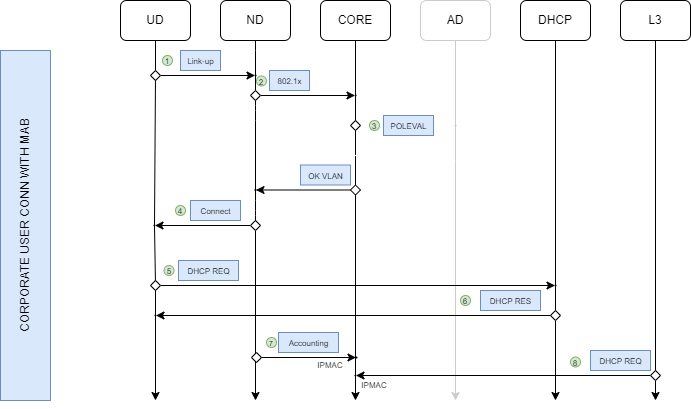
4.2.8.2. MAB Auth Flow
This is the flow of a MAB type authentication. We will have to delimit where the problem exists by doing a complete follow-up of the standard flow.
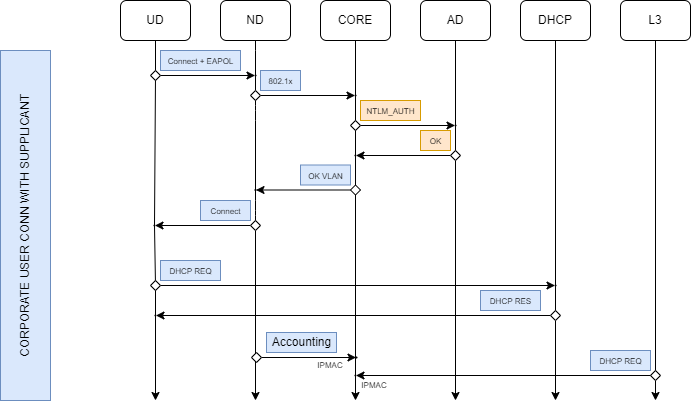
4.2.8.3. Supplicant Flow
This is the flow of a Suplicant type authentication. We will have to delimit where the problem exists by doing a complete follow-up of the standard flow.