Deployment Captive Portal¶
Guest, BYOD, Partners, External staff users management are the main use cases used by captive Portal, flexible and customizable workflow is available for customers. Sponsor based, auto registering and other deployment options are ready to be used.
Please follow the next steps in order to deploy it, Captive Portal is flexible and can be customized.
- We have to deploy a VLAN for Registry.
- Make sure we have available a DHCP Server and its IP scope to provide IP configuration for Clients.
- DNS Server with DNS Poisoning capabilities, this means that any DNS Queries will be answered with the IP of Captive Portal, in that way the clients will be forwarded to Captive Portal (Guest and Registry forms)
- openNAC Core includes a DNS Server ready to be used in this kind of deployments
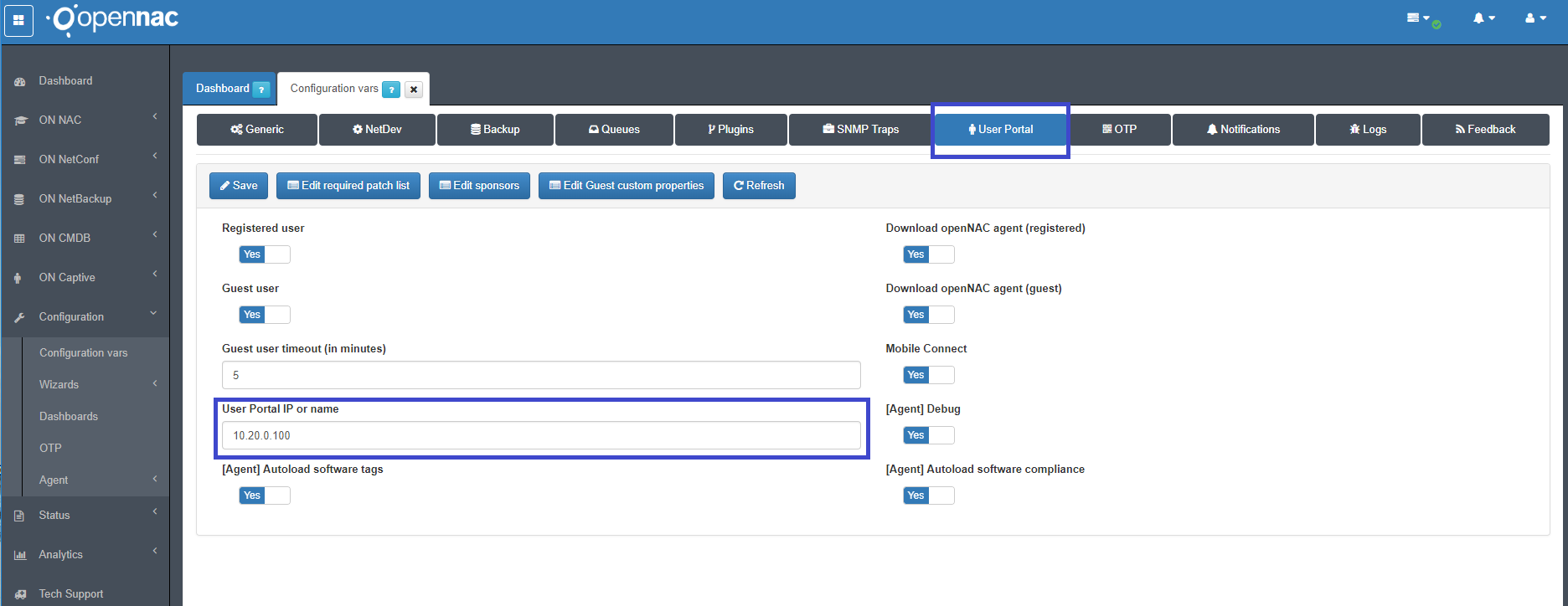
- Configure the captive portal IP on configuration vars Configuration vars -> User Portal, basically this service is provided by openNAC Core so the IP should be one of the configured interfaces of openNAC Core.
- Create a Security Policy on administration portal going to ON NAC -> Policies assigning only the registry VLAN.
- As you can see above we can use the same captive portal for many user cases, Guest (Guest, Partners, External Staff, Consultants) and Register Devices (BYOD) are available .
- A customizable workflow is available, sponsor (Approval based) and auto-registering are available, remember that email notification should be active and the URL accessible to all the Sponsors users
- As well as you can see above sponsors can be managed very easy and the Guest users should select the assigned to them. Go to ON NAC -> Policies “Edit sponsors”**
- Check email services are active, remember that this can be test from command line.
mailx -s "Email test" -r from_user@opennac.org user_dest@opennac.org Testing email
Note
You can check “/var/log/maillog” file, if any error exists.
- Optionally, some additional configuration can be defined in “/etc/postfix/main.cf” file or install an extra package to send emails (for example: “ssmtp”)
- Workflow, email notification and portal appearance can be easily customized.
Review the following link for more information about user portal configuration, User Portal Configuration.
Captive portal is a capability that allows to covert network access controls request, when supplicant is not installed or credentials are not valid o when the device is unknown can be sent to openNAC Captive portal.
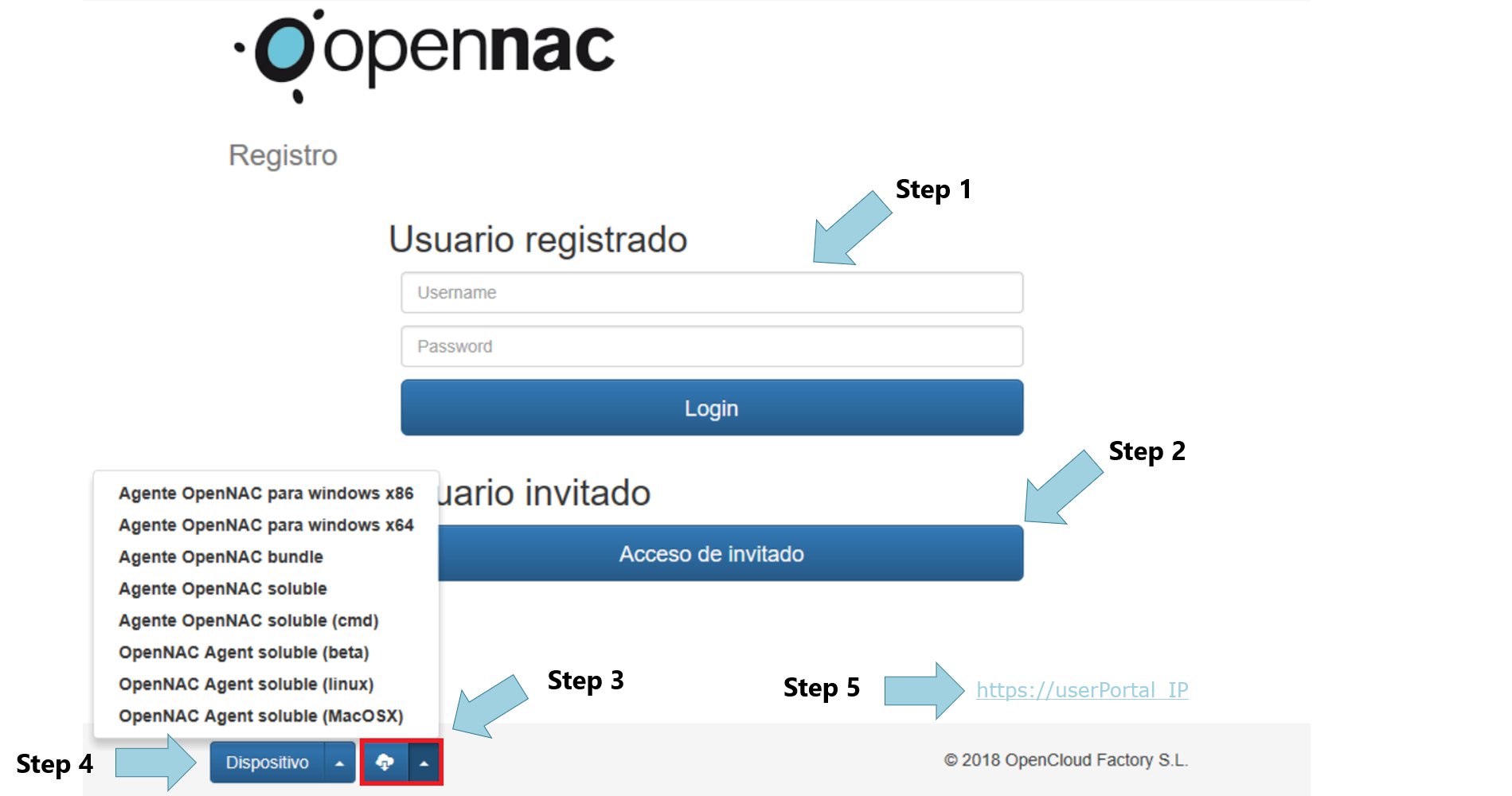
From captive portal is possible to enable different forms (Register User and Guest Users).
Registered user: Allows to use a valid credentials to be authenticated in the network , this helps to register personal device using a valid credentials as shown by Step 1
Guest User: Allows to request network access to any sponsor or automatically through registration process as shown by Step2, MobileConnect can be used as 2FA to enforce security access.
If possible to extract IP information from user devices when this reach the captive portal, this information is provide to facilitate the support for end users, as shown by shown by Step 4 and clicking on Device buttom.
openNAC Agent configured can be download as shown by Step 3 or using a direct request as shown by Step 5.
Review the following link for more information about ON Captive configuration, ON Captive Configuration.