UNAC¶
The Identity is the perimeter
Guarantee that identity and entitlements of users and devices/things are the first line of defense against advanced threats.
Simplify network control of assets in wired, wireless , VPNs and APPs
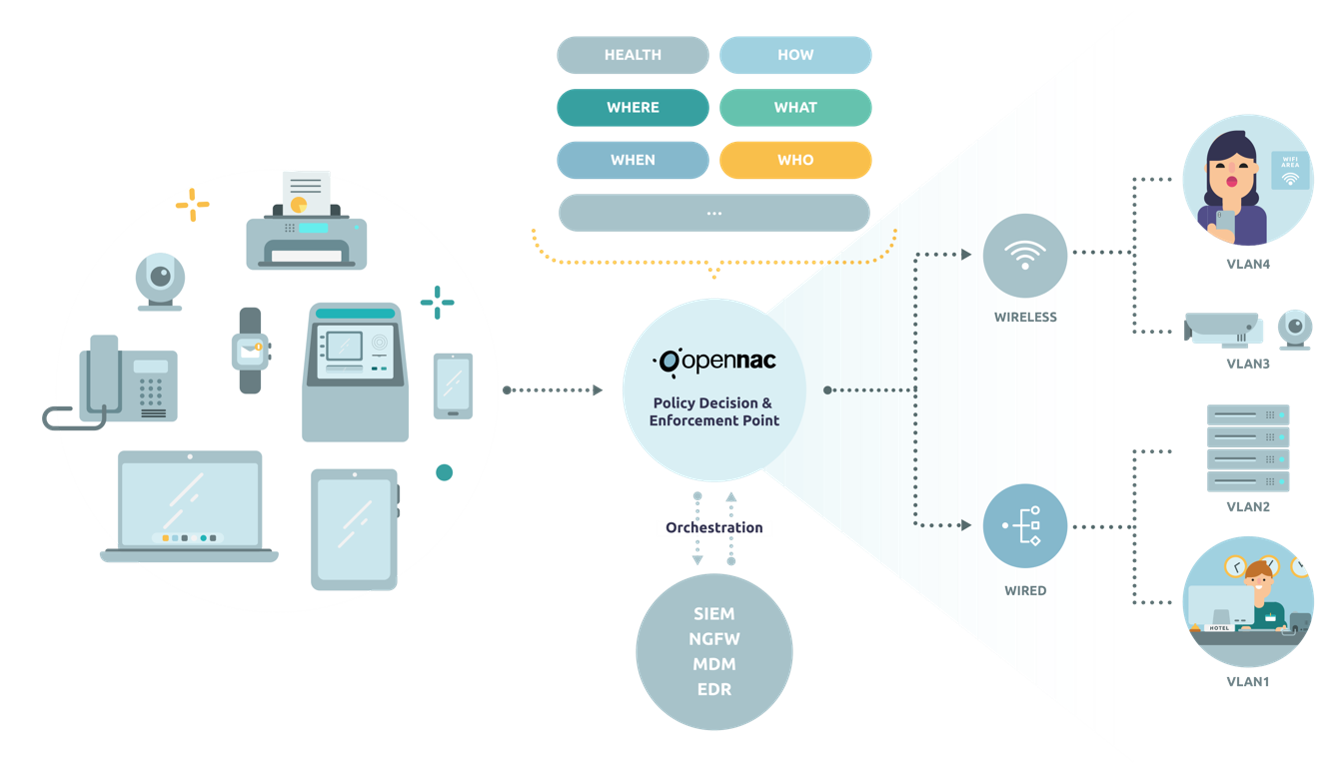
POLICY DECISION & ENFOREMENT POINT
Define and enforce policies (block, allow, limit) based on device/things, user and business critical nature of the asset
TOTAL INTEROPERABILITY AGNOSTICS
Enforce complete control in a multivendor network infrastructure using multiple protocols
TOTAL INTEGRATION / ADAPATION
Adaptive authentication and authorization via an IAM* holistic vision; share / gathered data, connectivity by API
AUDIT TRAILS
Via security orchestration and data / logs enables forensic trails