Compliance¶
The weakest link: Each endpoint is a potential enabler of an “enterprise killer” attack
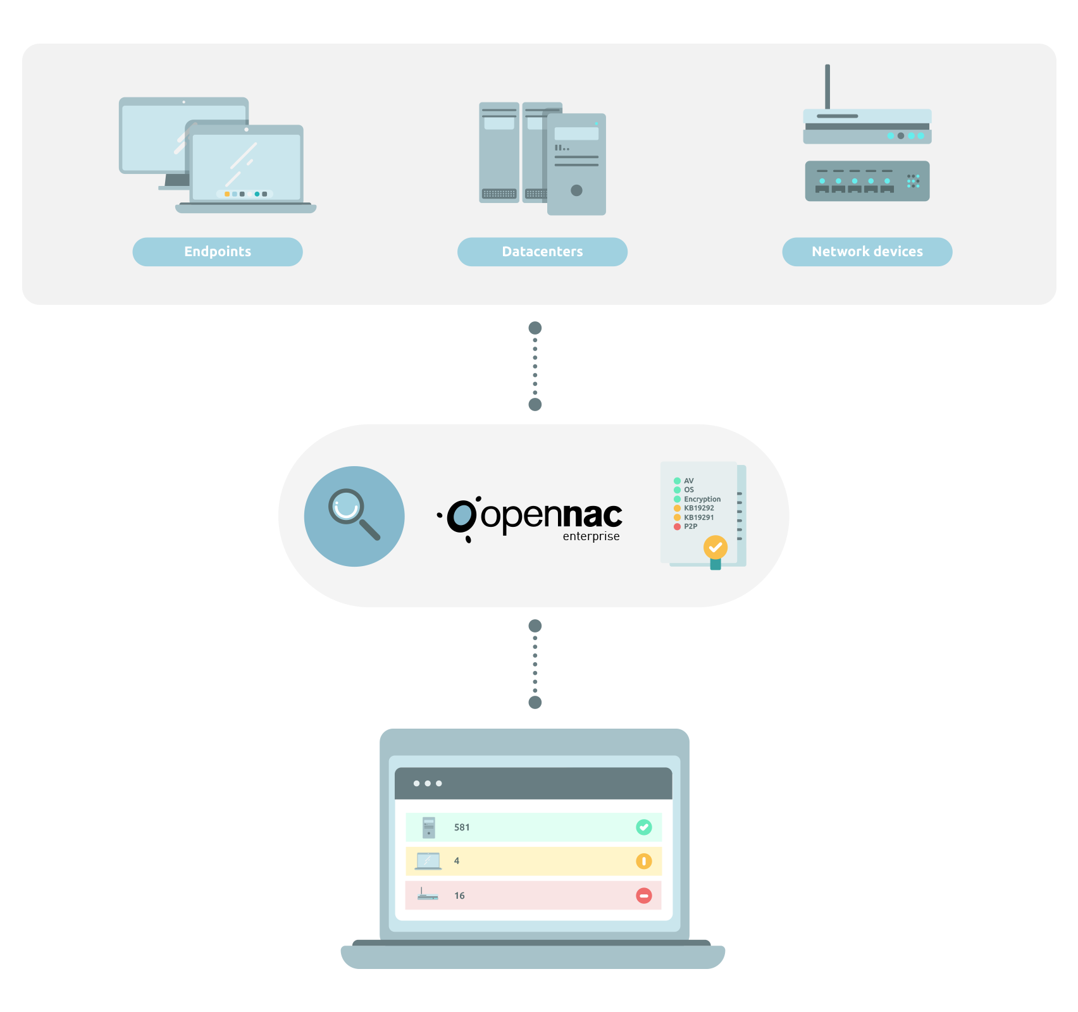
Guarantee infrastructure security compliance with corporate policies / regulatory mandates
DEFINE
Define the necessary security baselines for infrastructure. EP / Server (AV, FW, OS, patches etc. minimum versions).Switches and APs; IOS versions, configurations etc.
DISCOVER & CHECK
Automatically discover actual status and identify gaps. “99% of vulnerabilities exploited will continue to be ones known by security pros.. for at least 1 year” Gartner
RESPOND / ENFORCE
Centralized visibility, point of decision and enforcement empowers you to respond globally to attacks. Remediate issues immediately, automatically and continuously (isolation , remediation, information (dashboard)).
REPORT / AUDIT
Demonstrate response to attacks. Measure the effectiveness of security controls and demonstrate compliance with regulations.