5.1.3.3.1.12. User Data Source (UDS) TLS Certificate key too weak
When we register a UDS through LDAPS, an exchange of certificates occurs. it is possible to find clients who are using certificates that have keys generated with a low number of bits (normally < =1024). This number of bits is considered weak and therefore not secure for TLS.
Since by default OpenNAC requires secure keys to be used, and therefore, LDAPS communications with weakly signed certificates will fail.
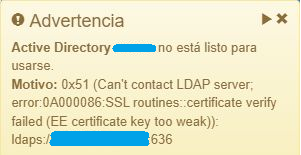
If we encounter this problem, it is possible that we have failed authentications on the platform. We can see this both in the OpenNAC default View and in the logs through the terminal.
Error:
If we want to debug through the console and verify the error, we can use the ldapsearch command with the -d8 flag to enable a debug that allows us to see the error.
Example:
verify error:num=66:EE certificate key too weak
5.1.3.3.1.12.1. Solution:
The correct solution to this error is to redistribute the certificates to clients with a greater number of bits for the keys (>=2048) since this way the problem is avoided and the minimum security standards are met.
Sometimes it is not possible to recreate and distribute these certificates, in this case we must follow an alternative solution.
5.1.3.3.1.12.2. Workaround:
The correct solution is to redeploy certificates using a higher bit RSA key. If this option is not possible, we must adjust the system to allow the use of smaller key sizes.
To do this we will use a modification of the system’s crypto policies:
Copy the file OPENNAC-WEAK-KEY.pmod to system policies modules directory:
cp /usr/share/opennac/utils/crypto-policies/OPENNAC-WEAK-KEY.pmod /etc/crypto-policies/policies/modules/OPENNAC-WEAK-KEY.pmod
Check which policy we have currently applied:
update-crypto-policies --show
Apply the policy mod:
update-crypto-policies --set <ACTUAL-POLICY+ACTUAL-PMOD>:OPENNAC-WEAK-KEY
Restart the php-fpm and httpd services:
systemctl restart php-fpm
systemctl restart httpd