9.2.3.9. Extreme Networks
9.2.3.9.1. X440G2, X450G2 and X460G2
Firmware: ExtremeXOS 30.7.1.1-patch1-86 & 31.7.1.4 31.7.1.4-patch1-98
Administration Portal > ON CMDB > Network Devices Brand/Model: ExtremeNetworks/X440
9.2.3.9.1.1. RADIUS Configuration
Here we will configure the RADIUS server where the switch will send authentication requests when a user connects to one of the ports.
9.2.3.9.1.1.1. RADIUS Servers
Configure Radius Server:
configure radius netlogin primary server <OpenNAC IP> client-ip <SwitchIP> vr VR-Default
configure radius netlogin primary shared-secret <RadiusSharedKey>
enable radius netlogin
9.2.3.9.1.1.2. RADIUS Accounting Servers
Configure Radius Accounting Server:
configure radius-accounting netlogin primary server <OpenNAC IP> client-ip <SwitchIP> vr VR-Default
configure radius-accounting netlogin primary shared-secret <RadiusSharedKey>
enable radius-accounting netlogin
9.2.3.9.1.1.3. RADIUS Balance Algorithm
If we configure more than one RADIUS server, we have the possibility of configuring the type of balancing that we want the switch to perform. The options we have are:
Standard (default): It begins by sending the requests to the first server, if no response is obtained, it goes to the next one.
Round-Robin: Requests are distributed in rotation among those configured.
To set it up:
configure radius algorithm <standard/round-robin>
9.2.3.9.1.2. Dot1x Configuration
To configure the 802.1x functionality, we must configure a Policy and add to the authenticating interfaces:
configure netlogin vlan temp
enable netlogin dot1x
configure netlogin dynamic-vlan enable
configure netlogin dynamic-vlan uplink-ports 50
enable netlogin ports <portlist> dot1x
configure netlogin ports <portlist> mode port-based-vlans
configure netlogin ports <portlist> no-restart
configure netlogin dot1x ports <portlist> timers server-timeout 10 reauth-period 3600
9.2.3.9.1.2.1. MAC-Address Bypass (MAB)
To enable the MAC-Authentication functionality (used to perform MAB):
configure netlogin vlan temp
enable netlogin mac
configure netlogin add mac-list default
configure netlogin dynamic-vlan enable
configure netlogin dynamic-vlan uplink-ports 50
configure netlogin mac authentication database-order radius
enable netlogin ports <portlist> mac
configure netlogin ports <portlist> mode port-based-vlans
configure netlogin ports <portlist> no-restart
configure netlogin mac ports <portlist> timers reauth-period 3600 reauthentication on
9.2.3.9.1.2.2. 802.1x + MAB
To enable the 802.1x in conjunction with MAC-Authentication functionality :
enable netlogin ports <port-List> dot1x mac
configure netlogin mac ports <portlist> timers delay <Time to wait for 802.1x>
9.2.3.9.1.3. Dot1x Features
9.2.3.9.1.3.1. Default VLAN
The default VLAN will be the one that will be assigned in case of defining the default VLAN in the OpenNAC policy.
configure netlogin vlan <Default VLAN>
The default VLAN must be configured when authentication is globally disabled (disable netlogin <dot1x / mac>)
9.2.3.9.1.3.2. Critical VLAN
The critical VLAN will be the one in which the connections will be established in case the radius servers are not available for authorization.
configure netlogin authentication service-unavailable vlan <VlanID>
enable netlogin authentication service-unavailable vlan ports <Ports>
9.2.3.9.1.3.3. Reject VLAN
The Reject VLAN will be the one in which the connections will be established in case the radius servers are refuse the authentication of de device (Access-Reject).
configure netlogin authentication failure vlan <VlanID>
enable netlogin authentication failure vlan ports <Ports>
9.2.3.9.1.3.4. Re-Auth Period
To configure the reauthentication period we must perform the following configuration in FortiSwitch:
Set Switch Default Config:
configure netlogin mac ports 1 timers reauth-period 3600 reauthentication on
configure netlogin dot1x ports 1 timers reauth-period 3600 reauthentication on
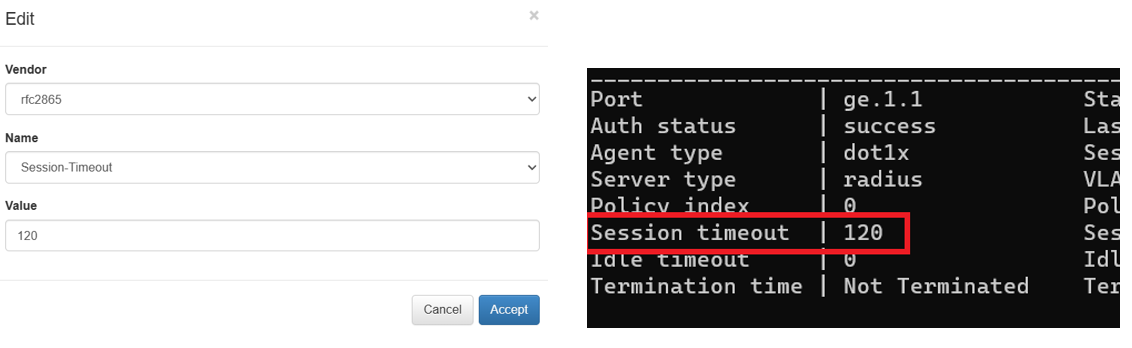
Additionally, if we want to define a reauthentication period for a certain session and assign it through OpenNAC, we use the following Extra Radius Param (Session-Timeout) in the OpenNAC policy (Value in seconds):
9.2.3.9.1.4. Security Profiles (ACLs)
To enable the dynamic security profiles functionality, we must configure the following:
configure policy maptable response both
configure policy vlanauthorization enable
configure policy rule-model access-list
configure policy slices tci-overwrite 2
configure policy slices shared 2
enable policy
9.2.3.9.1.4.1. Static Security Profile
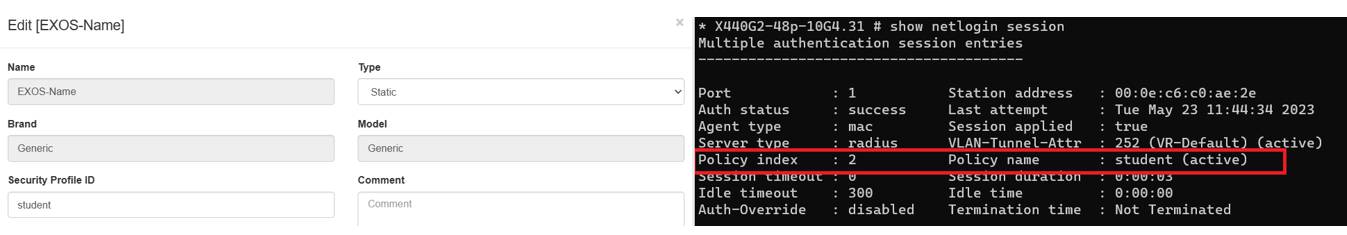
Static security profiles are those where from openNAC we will define which ACL (previously created on the network device) we want to apply to the connection that is established.
In the Extreme switch, we will not define ACLs directly, but we will apply a profile, which will have these ACLs associated:
To define an ACL on the switch, example:
#Example Profile .. code-block:: bash
configure policy profile 1 name “<PolicyName>” access-list “<Access-ListName>”
#Example ACL .. code-block:: bash
create policy access-list <PolicyName>.ACE1_Allow_ARP matches ether 0x0806 mask 16 actions forward
9.2.3.9.1.4.2. Dynamic Security Profile (Minimum Firmware ver. 31.2)
To be able to add ACLs through radius in a dynamic way, it will be necessary to have a profile created to which we will assign the clients and the ACLs defined in OpenNAC will be added.
#Example Profile .. code-block:: bash
configure policy profile 1 name “<PolicyName>”
OpenNAC Security Profile:
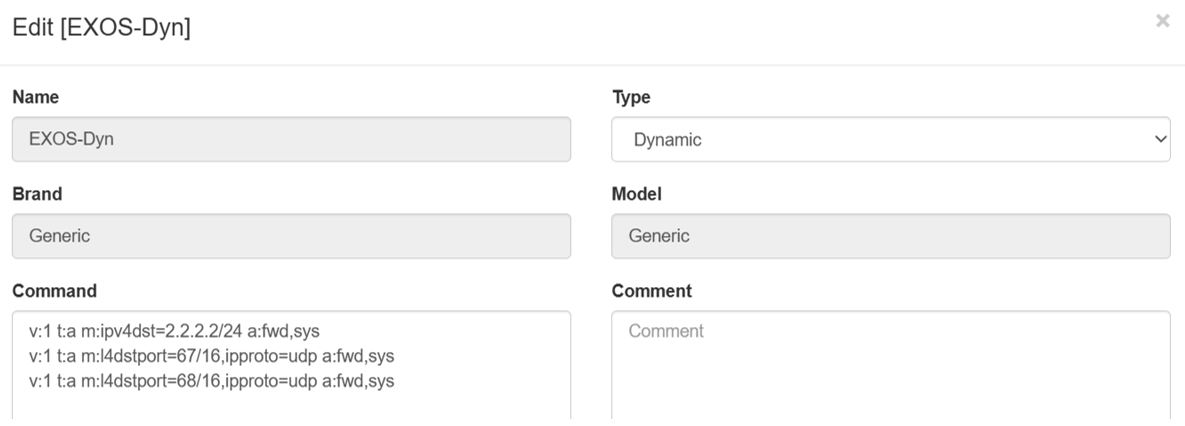
The configuration of the OpenNAC policy will be the following:
Security Profile: The security profile with the dynamic rules defined.
Extra Radius Params: Here the Filter-ID parameter will be included with the value of the profile to which we want to assign the client together with the defined ACLs.
Example:
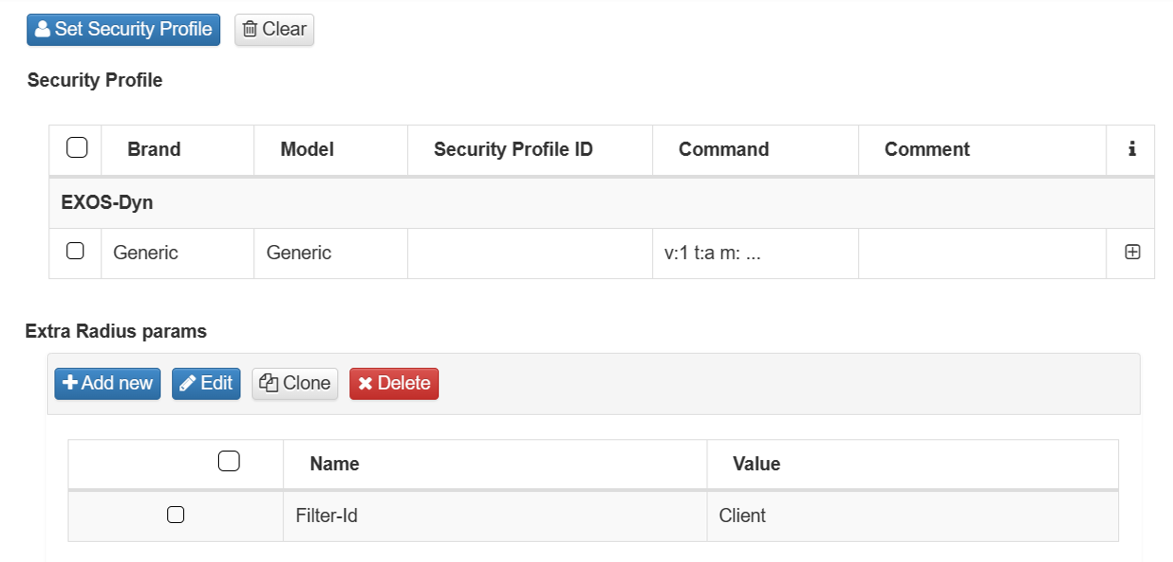
If we want to verify that the policies have been created and assigned to the corresponding mac we can see it with:
show access-list dynamic
For more information on how to create Dynamic ACLs: Q A: Extreme-Policy-ACL VSA 232 Syntax | Extreme Portal (force.com)
9.2.3.9.1.5. TogglePort
OpenNAC’s TogglePort allows us to reinitialize the session of authenticated users on the switches. This allows us to re-evaluate the policies and apply changes in the session if necessary. For this we have two methods, SNMP and CoA.
9.2.3.9.1.5.1. SNMP
In order to perform the policy reevaluation through SNMP, it will be necessary to activate this functionality and define the keys of the reading and writing communities:
SNMP v2:
enable snmp access snmp-v1v2c
configure snmp add community readonly <RO-Community>
configure snmp add community readwrite <RW-Community>
enable snmp community <RO-Community>
enable snmp community <RW-Community>
SNMP v3:
configure snmpv3 add user <User> authentication <AuthMethod> <AuthCredentials> priv <EncryptionMethod> <EncryptionCredentials>
configure snmpv3 add group <Group> user <User> sec-model usm
configure snmpv3 add access <Group> sec-model usm sec-level priv read-view defaultAdminView write-view defaultAdminView notify-view defaultAdminView
enable snmp access snmpv3
9.2.3.9.1.5.2. CoA
In order to perform the policy reevaluation through CoA, it will be necessary to activate this functionality and define de clients with their shared-key:
configure radius dynamic-authorization 1 server 192.168.1.5 client-ip 10.0.0.8 vr VR-Default shared-secret useStrongerSecret
enable radius dynamic-authorization
9.2.3.9.1.6. NetConf & NetBackup
We can apply remote configuration and get a configuration backup from the opennac administration portal.
9.2.3.9.1.7. SNMP Traps
Through SNMP Traps, we can make network visibility since these will provide us with information about the connections in the switch ports in OpenNAC. This includes the MAC, port, and connection status.
Do not enable MAC Notification traps on uplink ports (such as inter-switch links, trunks, port channels).
To configure SNMP traps on the switch:
enable snmp traps fdb mac-tracking
configure fdb mac-tracking add ports <portlist>
configure snmp add trapreceiver <OpenNAC Core IP> community <Community>
9.2.3.9.1.8. Troubleshooting & Monitoring
Show configuration:
show full-configuration
Show open sessions (802.1x /mac):
show netlogin session
show netlogin port 1
Check dynamic vlan assignement:
show ports 1 vlan
Show critical vlan config:
show netlogin authentication service-unavailable vlan
9.2.3.9.2. B5 (Enterasys)
Firmware: 06.81.10.0001
Administration Portal > ON CMDB > Network Devices Brand/Model: ExtremeNetworks/B5
9.2.3.9.2.1. VLAN Definition
In Extreme B5, to be able to assign VLANs dynamically through RADIUS, it is necessary to define the VLANs as follows:
9.2.3.9.2.1.1. Create VLAN
In Extreme Switch, to be able to assign VLANs dynamically through RADIUS, it is necessary to define the VLANs as follows:
set vlan create <VlanID>
set vlan name <VlanID> <VlanName>
set vlan egress <VlanID> ge.1.48 tagged
9.2.3.9.2.2. RADIUS Configuration
Here we will configure the RADIUS server where the switch will send authentication requests when a user connects to one of the ports.
9.2.3.9.2.2.1. RADIUS Server
Configure Radius Auth Server:
set radius server 1 <RadiusServer-IP > 1812 <Radius-SharedKey>
set radius timeout <timeout>
set radius retries <retries>
set radius realm network-access all
set radius enable
9.2.3.9.2.2.2. RADIUS Accounting Server
Configure Radius Acct Server:
set radius accounting server 10.21.49.2 1813 testing123
set radius accounting timeout <timeout>
set radius accounting retries <retries>
set radius accounting updateinterval <Interval>
set radius accounting intervalminimum <Interval>
set radius accounting enable
9.2.3.9.2.3. Dot1x Configuration
To configure the 802.1x functionality, we must configure the following:
Note: Globally enabling 802.1x on a switch sets the port-control type to auto for all ports. Be sure to set port-control to forced-auth on all ports that will not be authenticating using 802.1x and no other authentication method is configured. Otherwise these ports will fail authentication and traffic will be blocked.
set dot1x auth-config authcontrolled-portcontrol forced-auth <NoAuthPort>
set eapol auth-mode forced-auth <NoAuthPort>
set multiauth mode multi
set eapol enable
set dot1x enable
9.2.3.9.2.4. MAC-Address Bypass (MAB)
To enable the MAC-Authentication functionality (used to perform MAB):
set macauthentication port enable <ports>
set macauthentication enable
9.2.3.9.2.5. 802.1x + MAB
To be able to perform both 802.1x and MAB on the same port, we will need to activate the following:
set multiauth mode multi
9.2.3.9.2.6. Dot1x Features
9.2.3.9.2.6.1. Default VLAN
The default VLAN will be the one that will be assigned in case of defining the default VLAN in the OpenNAC policy.
set port vlan <port> <DefaultVLAN>
9.2.3.9.2.6.2. Dynamic VLAN
The dynamic VLAN will allow us to send the desired VLAN which the client must belong.
set vlanauthorization enable
set policy maptable response both
9.2.3.9.2.6.3. Critical VLAN
The critical VLAN is the VLAN that is assigned to a client when the RADIUS server is unavailable. The critical VLAN of this switch works differently than the standard way.
To make use of this operating mode, the ports must be configured with:
set multiauth port mode auth-opt <port>
In this operating mode, before the authentication is carried out, the default VLAN or policy will be assigned to the port. In case the authentication fails, no change will be made and the port will remain open with said default VLAN. In the event that the RADIUS server did respond, the changes sent from RADIUS would be applied to the authenticated session.
This is the default behaviour.
Warning
Keep in mind that this applies when authentication fails, so if for some reason we send an Access-Reject (for policy or failed authentication), the switch will interpret it as an authentication failure and assign the device to the VLAN defined by default.
9.2.3.9.2.6.4. Re-Auth Period
To configure the reauthentication period we must perform the following configuration in FortiSwitch:
Set Switch Default Config:
set dot1x auth-config reauthenabled true
set dot1x auth-config <reauthperiod>
Additionally, if we want to define a reauthentication period for a certain session and assign it through OpenNAC, we use the following Extra Radius Param (Session-Timeout) in the OpenNAC policy (Value in seconds):
9.2.3.9.2.7. Security Profiles (Policy Profile)
9.2.3.9.2.7.1. Static Security Profile
In this switch model, the security profiles do not correspond to ACLs per se. Here the Security profiles that we can apply through OpenNAC are called “policy profiles”.
For this we can only do it statically, that is to say by defining the profile in the switch and sending the number of the profile in the OpenNAC policy.
Needed configuration:
set vlanauthorization enable
set policy maptable response both
9.2.3.9.2.8. TogglePort
OpenNAC’s TogglePort allows us to reinitialize the session of authenticated users on the switches.
set snmp access groupRW security-model v2c exact read All write All notify All
set snmp community <SNMP Community>
set snmp group groupRW user public security-model v2c
set snmp view viewname All subtree 1
set snmp view viewname All subtree 0.0
This allows us to re-evaluate the policies and apply changes in the session if necessary. For this we have two methods, SNMP and CoA.
9.2.3.9.2.8.1. SNMP
In order to perform the policy reevaluation through SNMP, it will be necessary to activate this functionality and define the keys of the reading and writing communities:
Global switch configuration settings
set snmp community public
set snmp targetparams v2cON user public security-model v2c message-processing v2c
set snmp notify entryON tag TrapON
set snmp targetaddr tr <OpenNAC IP> param v2cON taglist TrapON
set maclock enable
Individual interface configuration settings
set vlan egress 1,2,3 ge.1.xx untagged
set port trap ge.1.xx disable
set maclock enable ge.1.xx
set maclock static ge.1.xx 1
set maclock firstarrival ge.1.xx 0
set maclock trap ge.1.xx enable
Note
Extreme Networks B5 lacks SNMP logout support. Device logouts are replicated via maclock, generating only login traps, not logout.
9.2.3.9.2.8.2. CoA
Not supported.
9.2.3.9.2.9. NetConf & NetBackup
We can apply remote configuration and get a configuration backup from the OpenNAC Enterprise administration portal.
9.2.3.9.2.10. Troubleshooting & Monitoring
Show configuration:
show full-configuration
Show auth status port:
show eapol <port>
Show MAB sessions:
show macauthentication session
Show dynamic vlan assignment:
show vlanauthorization <port>
Show multiauth sessions:
show multiauth session