1.5.2. CMIX to VPNGW Migration
This section covers the automatic migration from CMIX to the VPNGW node. This process relies on Ansible playbooks that will verify your original configurations and automatically migrate them to the VPNGW node.
The primary objective is to migrate all relevant files from Shorewall on the CMIX node to the VPNGW node.
Note
During the import process, all files related to zones, policies, rules, and parameters will be imported. However, files related to interfaces, hosts, WireGuard, and OpenVPN configurations will not be imported, requiring manual configuration through the Administration Portal.
1.5.2.1. Prerequisites
Before starting the migration process, fulfill the following conditions:
Ensure that the VPNGW node imported into the Core node is clean, meaning it has no pre-existing configurations (zones, rules, policies, wireguard configuration, etc).
The CMI node must have the sshpass installed.
dnf install sshpass
Ensure that you have internet connection.
[root@CORE ~]# ping google.com
PING google.com (142.250.200.142) 56(84) bytes of data.
64 bytes from mad41s14-in-f14.1e100.net (142.250.200.142): icmp_seq=1 ttl=117 time=13.10 ms
64 bytes from mad41s14-in-f14.1e100.net (142.250.200.142): icmp_seq=2 ttl=117 time=13.10 ms
64 bytes from mad41s14-in-f14.1e100.net (142.250.200.142): icmp_seq=3 ttl=117 time=13.6 ms
--- google.com ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 13.550/13.833/13.986/0.200 ms
Check you have access to the repository by trying to download the following file:
[root@onprincipal ~]# wget --user "repo_user" --ask-password https://repo-opennac.opencloudfactory.com/1.2.4/opennac-v1.2.4.repo
Password for user ‘repo_user’:
--2024-03-05 13:56:26-- https://repo-opennac.opencloudfactory.com/1.2.4/opennac-v1.2.4.repo
Resolving repo-opennac.opencloudfactory.com (repo-opennac.opencloudfactory.com)... 10.21.160.10
Connecting to repo-opennac.opencloudfactory.com (repo-opennac.opencloudfactory.com)|10.21.160.10|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 388 [application/x-troff-man]
Saving to: ‘opennac-v1.2.4.repo’
opennac-v1.2.4.repo 100%[===========================================================================================================================================>] 388 --.-KB/s in 0s
2024-03-05 13:56:26 (9.39 MB/s) - ‘opennac-v1.2.4.repo’ saved [388/388]
Once you verify you can access the repository, you can delete this file:
[root@onprincipal ~]# rm opennac-v1.2.4.repo
rm: remove regular file 'opennac-v1.2.4.repo'? y
Ensure the following node connectivity:
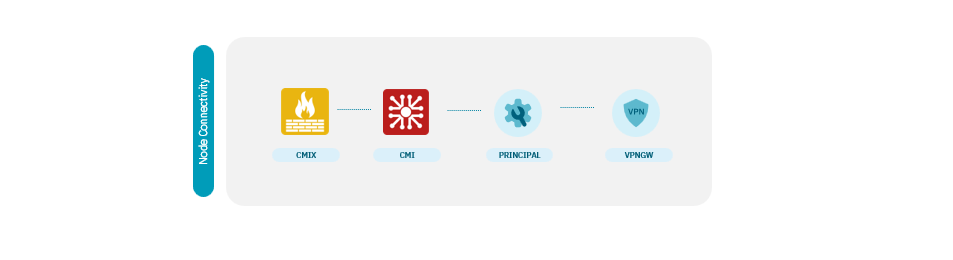
Where:
CMIX must have connection with CMI.
CMI must have connections with both CMIX and Principal.
Principal must have connections with both CMI and VPNGW.
1.5.2.2. Creating and copying the SSH key pair
Note
Perform the following steps on the ON Core Principal node.
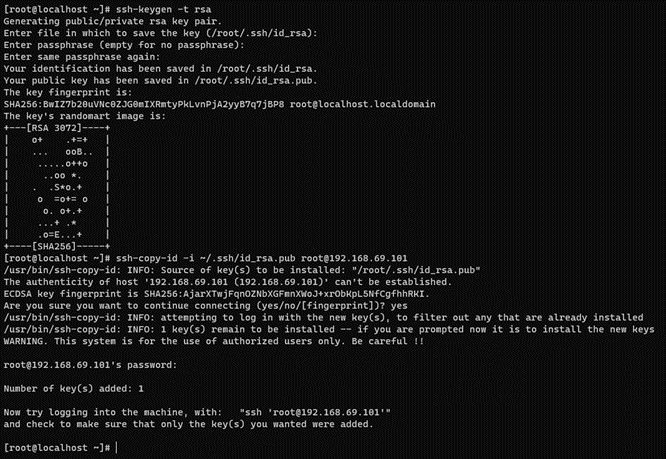
If you do not have an SSH key, execute the following command on the console:
ssh-keygen -t rsa -C ansibleKey
Answer all questions with an “Enter” to use default values. If the SSH key pair already exists and you want to overwrite it, you will be asked if you want to overwrite it, and you should answer the question with “y”.
Now, copy the generated public key to the nodes:
ssh-copy-id -i ~/.ssh/id_rsa.pub root@<nodes_IP>
Where <nodes_IP> are the IPs of the ON Principal itself, CMIX, CMI, and ON VPNGW.
Note
When copying the keys, it’s crucial to do so for all nodes, including the ON Core Principal itself from where the operation is executed.
1.5.2.3. Provisioning Ansible
After performing the previous steps, you can proceed to get the Ansible playbooks from our public repository by executing the following commands in the specified order:
Note
Download the Ansible file on the ON Core Principal machine, since the playbooks will be launched from this node.
wget --user "<username>" --ask-password https://repo-opennac.opencloudfactory.com/1.2.4/opennacansible8-1.2.4.zip
unzip -d opennacansible8-1.2.4 opennacansible8-1.2.4.zip
cd opennacansible8-1.2.4
1.5.2.4. Configuration steps
The Ansible playbooks downloaded in the previous step contains many files, the important ones are the following:
Inventory: In the
inventory.samplefile you will find the server names and IP addresses of the nodes.Ansible configuration:
ansible.cfg.samplefile contains the basic Ansible configuration. Here, you need to specify the path to the previously created SSH key.Variables file: Inside the vars/ directory, you will find a file containing variables. Replace the values of these variables as explained in more detail later.
Carefully follow the steps in the specified order.
1.5.2.4.1. Build the inventory file
Use the servers’ IPs to populate the inventory. First, copy the inventory_migrate_cmix_to_vpngw.sample to the inventory and then edit the file (using a tool like Vim, for instance) to add the IPs as shown below. Always check the .sample file first for any potential updates.
cp inventory_migrate_cmix_to_vpngw.sample inventory
vim inventory
The structure followed is:
<hostname> ansible_ssh_host=<SSH_IP> private_ip_address=<PRIVATE_IP> role_opennac=<role>
; This is the file where you must declare your server names and IP addresses
; The general syntax followed is:
; [group]
; <hostname> ansible_ssh_host=<SSH_IP> role_opennac=<role> ansible_python_interpreter=<python_interpreter>
[cmi]
oncmi ansible_ssh_host=10.21.65.103 role_opennac=cmi ansible_python_interpreter=/usr/bin/python
[principal]
onprincipal ansible_ssh_host=10.10.39.101 role_opennac=principal ansible_python_interpreter=/usr/bin/python3
1.5.2.4.2. Build the Ansible configuration file
Similar to the inventory setup:
Copy the
ansible.cfg.samplefile toansible.cfgand then edit it to include the path to your private_key_file (the ssh key that you previously have copied to the server).Indicate the path to your inventory file.
cp ansible.cfg.sample ansible.cfg
vim ansible.cfg
ansible.cfg.sample file:
timeout = 30
inventory = inventory
host_key_checking = False
remote_user = root
private_key_file = ~/.ssh/id_rsa
log_path = /var/log/ansible.log
roles_path = ./roles
display_skipped_hosts = False
show_task_path_on_failure = True
[ssh_connection]
control_path = %(directory)s/%%h-%%r
1.5.2.4.3. Configure the variables
There is a vars/ directory inside the opennacansible8-1.2.4/ directory in which you will find the vars_migrate_cmix_to_vpngw.yml variables.
vim vars/vars_migrate_cmix_to_vpngw.yml
CMIX variables
##########
# CMIX #
##########
cmix_pass: viapps
cmix_ip: 10.21.65.105
cmix_pass: The user to access the CMIX portal.
cmix_ip: The password to access the CMIX portal.
Core variables
##########
# CORE #
##########
portal_user: admin
portal_pass: opennac
portal_user: The user to access the OpenNAC portal.
portal_pass: The password to access the OpenNAC portal.
VPNGW variables
##########
# VPNGW #
##########
farm_id: farm01
vpngw_hostname: onvpngw
vpngw_ip: 10.10.39.105
farm_id: ID of the VPNGW farm.
vpngw_hostname: VPNGW hostame.
vpngw_ip: VPNGW node IP address.
1.5.2.5. Launch the playbooks
Remember to launch the playbooks from the OpenNAC Enterprise Principal node.
Note
Make sure to launch Ansible within a screen. This is to ensure continuity in case the connection to the Principal is lost.
To launch the playbooks, go to the previously downloaded opennacansible8-1.2.4/ folder.
By running the following command, it will execute automatic CMIX to VPNGW migration process:
ansible-playbook migrate_cmix_to_vpngw.yml
The expected result should look like the following one:
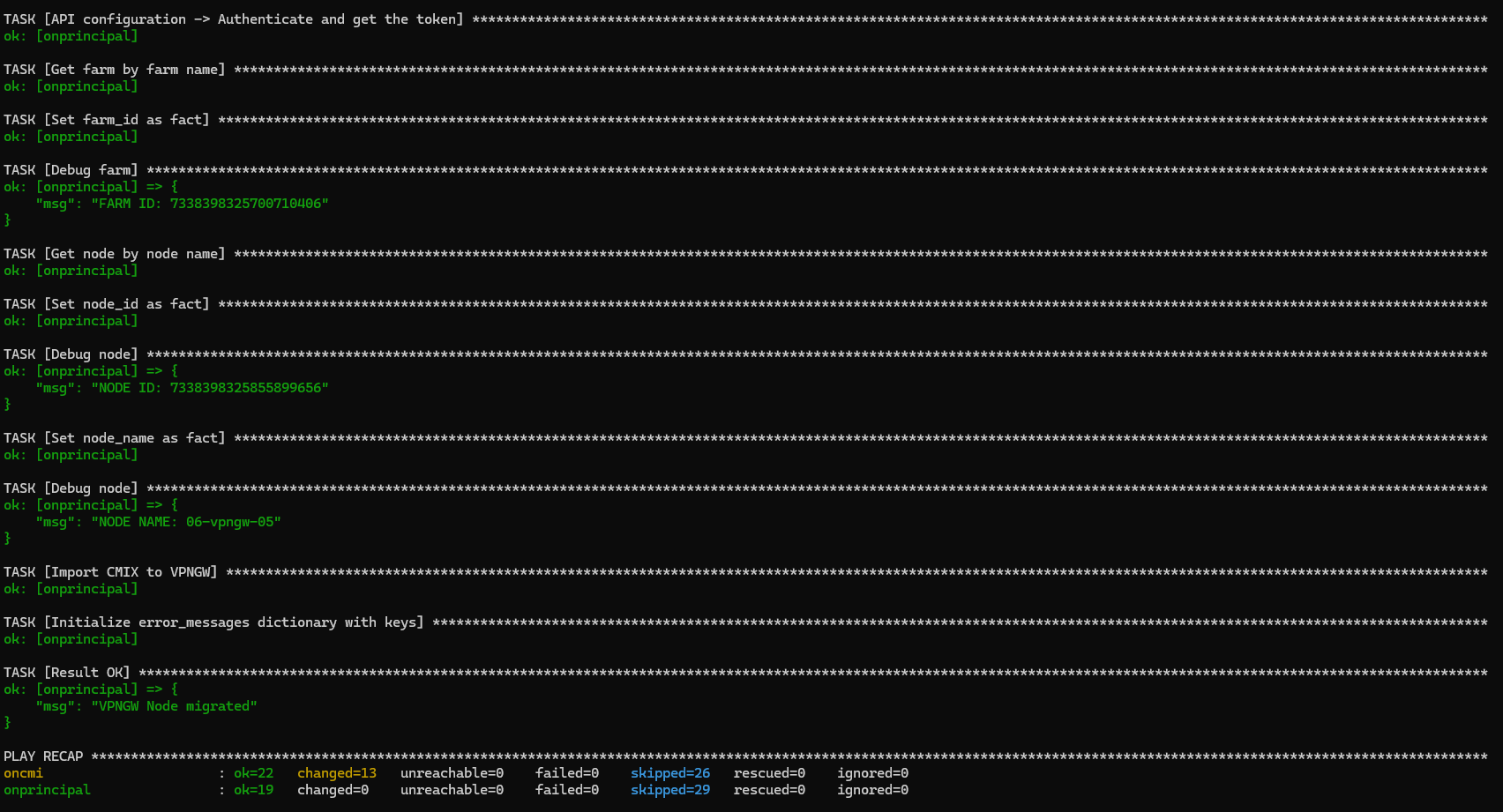
The process will import zones, policies, rules, and firewall objects (parameters). Configurations related to hosts and interfaces should be automatically handled upon completion of the import. However, configurations related to WireGuard or OpenVPN must be done manually.
1.5.2.6. Execution Result
As mentioned in the prerequisites, ensure that the VPNGW node imported into the Core node has no pre-existing configurations. Delete any configurations of zones, rules, policies, WireGuard configurations, etc. Otherwise, you will see the following error:
TASK [Import CMIX to VPNGW] ***************************************************************************************************************************************************************
task path: /root/opennacansible8-1.2.4/migrate_cmix_to_vpngw.yml:314
fatal: [onprincipal]: FAILED! => {"changed": false, "connection": "close", "content_type": "text/html; charset=UTF-8", "date": "Tue, 05 Mar 2024 14:19:44 GMT", "elapsed": 0, "msg": "Status code was 400 and not [200, 201]: HTTP Error 400: Bad Request", "redirected": false, "server": "Apache", "status": 400, "strict_transport_security": "max-age=63072000; includeSubdomains;", "transfer_encoding": "chunked", "url": "https://10.10.39.101:443/api/vpngw/farm", "x_content_type_options": "nosniff", "x_frame_options": "SAMEORIGIN"}
After finishing the execution, the output may display several validation messages. Those validation results will help you understand the manual configurations necessary to finish importing the CMIX configurations into your VPNGW.
If the import process fails with the following error, check the Shorewall files on the CMIX node to ensure that the information contained is not erroneous and that there are no problems when importing into the VPNGW node, follow the error messages displayed to try to solve the errors:
TASK [Result Failed] **********************************************************************************************************************************************************************
ok: [onprincipal] => {
"msg": {
"fwhost": [
{
"message": "Zone ServCrit not found in zones file.",
"result": "error",
"row": "ServCrit eth0:10.250.14.0/25 -"
}
],
"fwinterface": [
{
"message": "Zone vpnwg not found in zones file.",
"result": "error",
"row": "vpnwg TestVPN - -"
}
],
"fwobject": [
{
"message": "Host 'onprincipal' not found.",
"result": "error",
"row": "???"
}
],
"fwpolicy": [],
"fwrule": [
{
"message": "Protocol is empty.",
"result": "error",
"row": "ACCEPT all fw - - - - -"
},
{
"message": "Source SICCOM not found in zones file.",
"result": "error",
"row": "ACCEPT SICCOM all:10.21.65.167/32 all - - - -"
}
],
"fwzone": []
}
}
Once you have fixed the errors, you must re-launch ansible to perform the import.
ansible-playbook migrate_cmix_to_vpngw.yml