4.2.1. Introduction
On this page, we will see the use case of UNAC. This includes an explanation of what UNAC is, the benefits UNAC brings, the value it adds, and simple use-case scenarios.
4.2.1.1. What is UNAC?
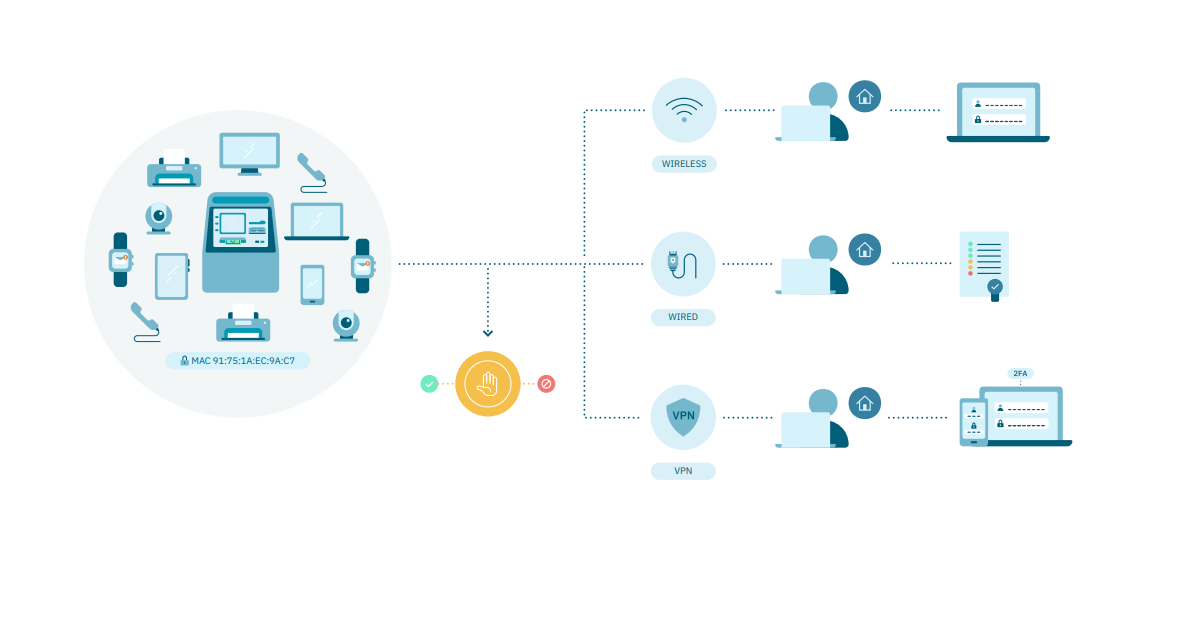
OpenNAC Enterprise is a module with the power to authenticate all users and devices in a corporate network (wired, wireless, and VPN).
Allows you to set:
The foundations of Zero Trust security strategy.
The security principles as the least privilege principle.
Allows users and/or devices authentication through:
Corporate user credentials
Corporate credentials + OTP. (2FA)
Certificates with internal CA
MAB for non-supplicant devices
802.1X protocol as the basis for establishing authentication policies. T understand the protocol fundamentals, see 802.1x Basic Concept
4.2.1.2. UNAC Benefits
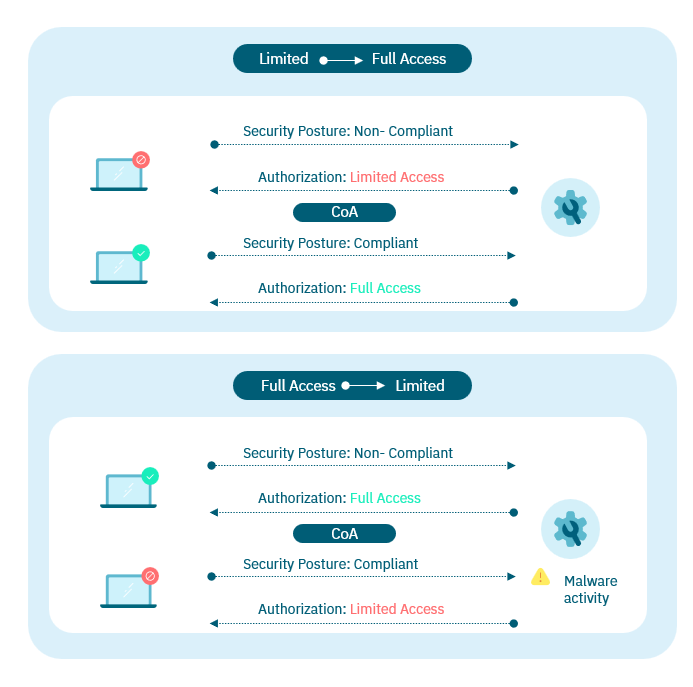
Establishes the foundations of the Zero Trust strategy, through the user’s identity validation and the entity of devices, mitigating the risk of identity fraud.
Allows to setting up security principles, determining the identity of the users, and granting only the necessary permissions for performing the functions of each user -the principle of least privilege.
Defines a single point of control for network access. From this centralized point administrators can deploy access policies and other key aspects for network security orchestration, for take reactive and proactive actions.
Double authentication factor using (OTP) -for user’s identity validation in remote connections.
Shows the real-time statistics and authentication details in the network, using dashboards to monitor the authentication processes of users and devices.
Facilitates the adaptation of standards and frameworks such as ISO2700x, NIST, ENS etc.
4.2.1.3. UNAC in 4 Steps
The UNAC configuration and operation process involve the following 4 steps:
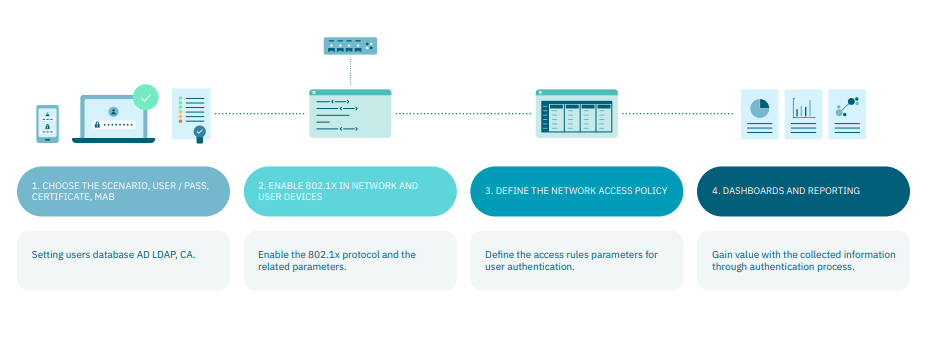
The first two steps are explained in the Configuration documentation and the last two are in the UNAC operation.
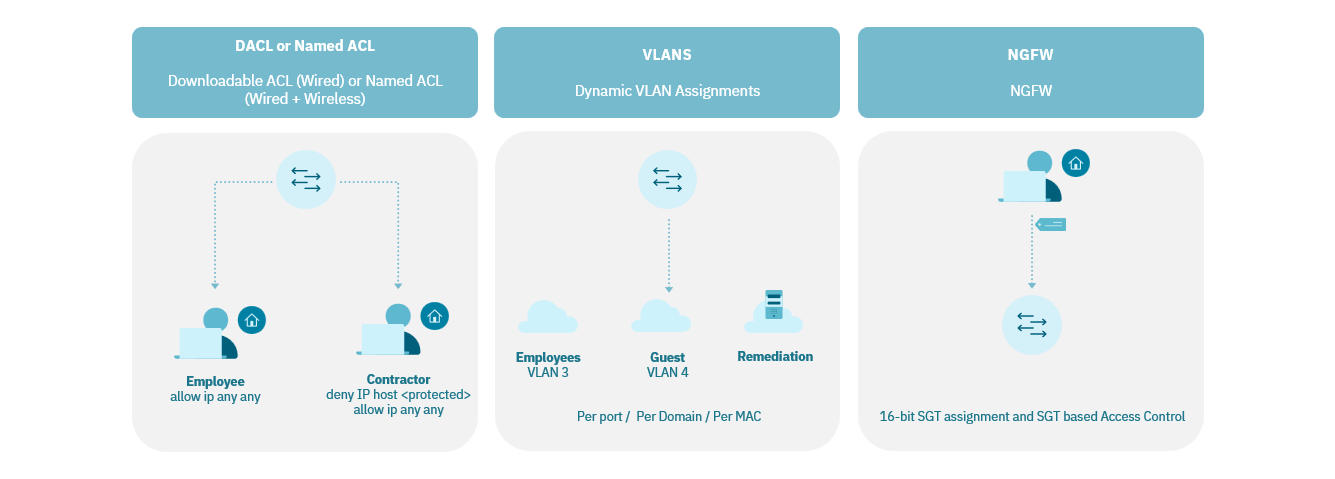
4.2.1.4. Authentication Scenarios
4.2.1.4.1. User and Password
User identity will be validated based on information that users know, such as their username and password. In this case, the user’s corporate credentials will be utilized for the validation process.
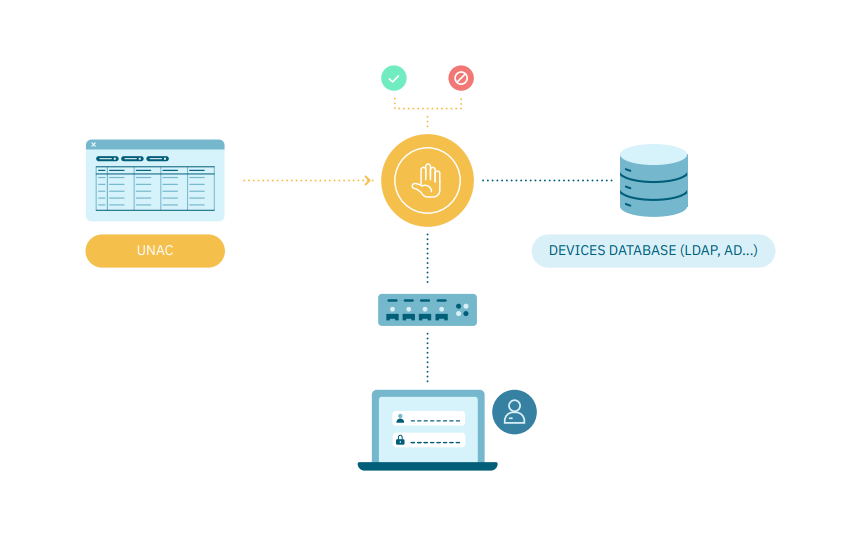
Requirements
Integration with User Database (LDAP, AD).
Enable 802.1x supplicant in user device.
Enable 802.1X protocol settings in network devices.
Access rules in OpenNAC Enterprise.
Outputs
Authentication metrics
Control Dashboards
Connected devices information: Connected devices information: IP, MAC, Switch Interface, VLAN, Hostname, User, and last access.
4.2.1.4.2. Certificate
Every user and/or device will possess a unique certificate generated by a Certificate Authority (CA). These certificates can be issued for either devices or individual users.
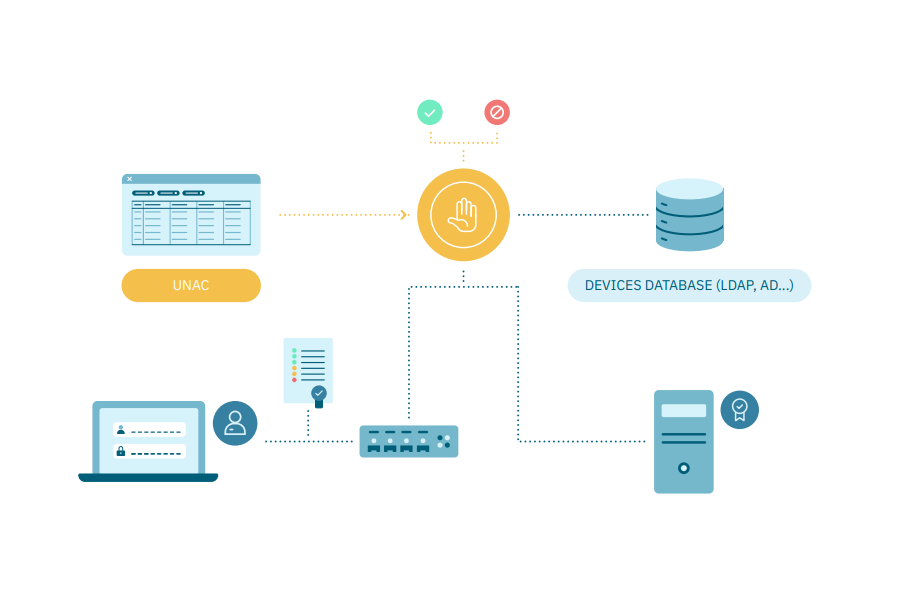
Requirements
CA Settings
Certificates generation
Certificates Deployment
Enable 802.1X protocol settings in network devices
Access rules in OpenNAC Enterprise
Outputs
Authentication metrics
Control Dashboards
Connected devices information: IP, MAC, Switch Interface, VLAN, Hostname, User, and last access.
4.2.1.4.3. MAB
The authentication process will accommodate devices that do not have an 802.1x supplicant. In such cases, the MAC address of the device will be validated for authentication purposes.
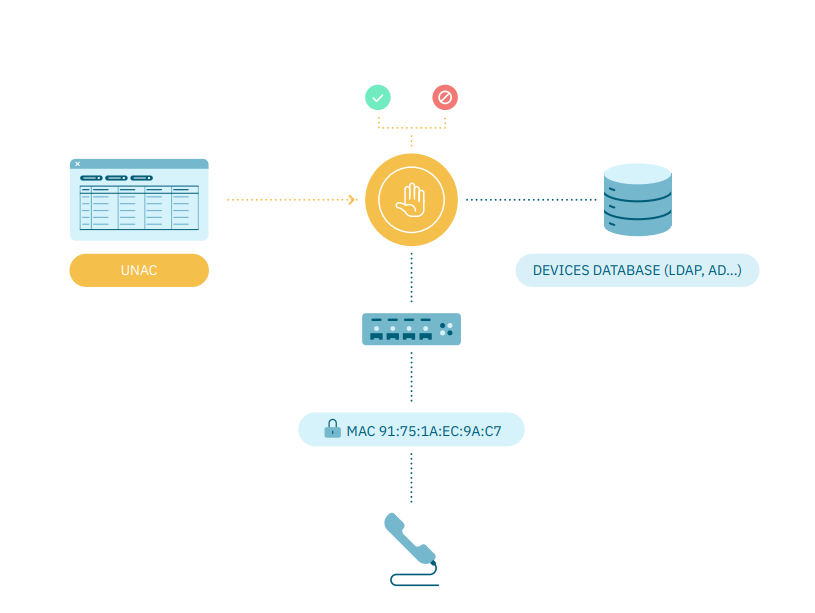
Requirements
Enable 802.1X protocol settings in network devices
Access rules in OpenNAC Enterprise
Outputs
Authentication metrics
Control Dashboards
Connected devices information: IP, MAC, Switch Interface, VLAN, Hostname, User, and last access.
4.2.1.6. UNAC Value
4.2.1.6.1. IT Support/ Help Desk
Reducing incidents response time: identify the affected device from the CMDB (username, IP, MAC, etc.) and toggle the related port on the switch (Toggle Port).
4.2.1.6.2. Monitoring - IT management
Real-time connections information Control Dashboards.
- Users’ connection metrics:
Wi-Fi users
Wired users
User’s information (location)
User’s rol
- Devices Information:
Device topology
Device location
Device information
MAC
Vendor
4.2.1.6.3. Adaptability
The value is subjective. The perception of the value of an IT tool increases as they solve a given problem.
The adaptability degree of IT tools will determine the value they provide.
UNAC module integrates with the current company’s infrastructure. It does not add administration efforts, but rather automates some recurring tasks, removing some mechanical tasks from the technical team.
Eliminate technological rigidity
Task automation
Multi-vendor, agnostic technology
Plugins, integrations
4.2.1.6.4. Dashboards Customization

The administrator selects the visualization type to set the Dashboard graphics(Bars, cake, etc).
Select the information, the device data (TAGS) that you want to show from the CMDB.
Set the structure of dashboards and selects all visualization.
Generate a new dashboard adding all the visualizations you want.
Add the dashboard to the OpenNAC Enterprise web console.
4.2.1.6.5. Reports. Audit Teams.
Management and audit reports in real-time:
Dashboards with users authentication details are automatically updated in real-time.
Companies can choose how to segment authenticated users on the network to have a report available at any time.
Examples:
Authenticated users
Authentication sources
Connected users from a certain group.
Users location