4.6.5. Administration
In this section, we will see the advanced operation of Guest management. The purpose of this section is to see how to create a captive workflow, how to customize it, and see what policies are needed.
4.6.5.1. Creating Network Devices in the ON Core CMDB
The CMDB is the ON Core database, in this database we find information related to the system, infrastructure, networks, VLANs, Security Profiles, user devices, network devices, etc.
The definition of network devices in the CMDB allows us to customize the characteristics of the device so that the system acts in one way or another with each of these devices.
If you want to register a predefined group of devices, consult Bulk import of devices.
Go to the “ON CMDB > Network Devices” section to create a new network device.
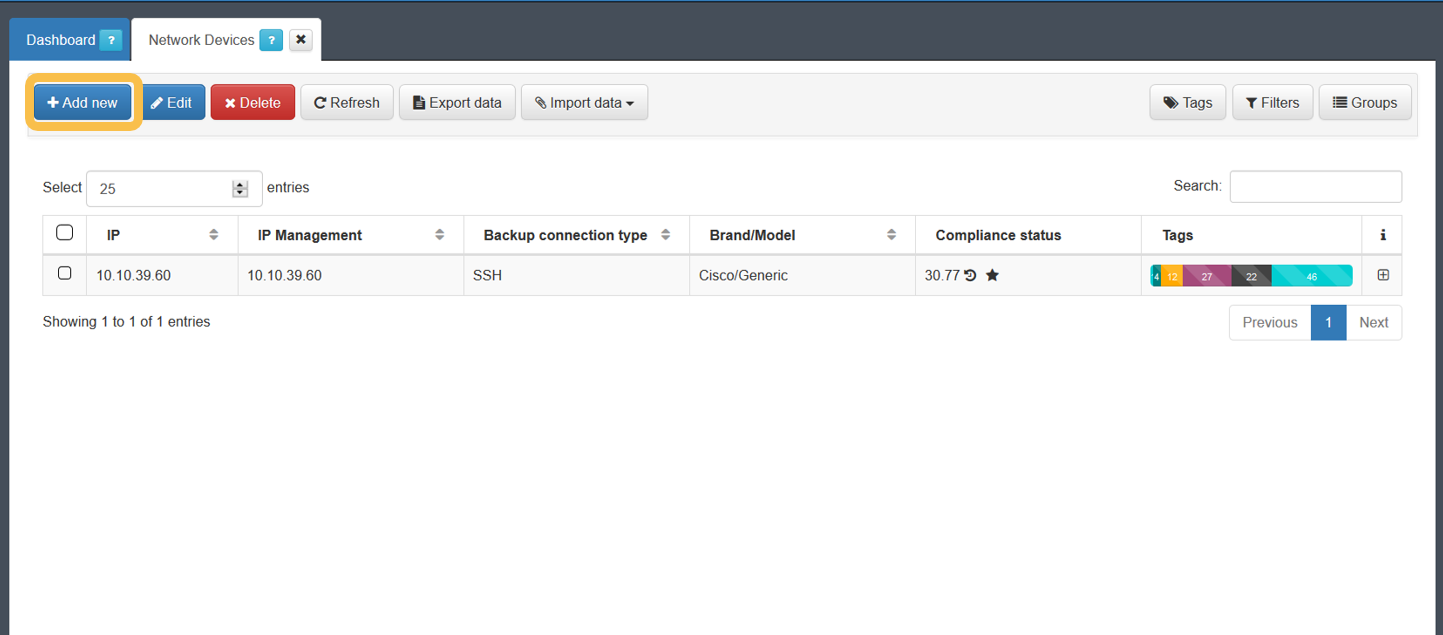
To register a new device, simply use the Add new button and complete the information on the form. After completing all the necessary information, we will press the Accept button on the form to save the configured network device.
By default, the device’s configuration will be applied to the one we have defined. This default configuration is found in Configuration -> Configuration Vars -> NetDev. The sections we will find here are the same ones we can find when configuring any of the devices.
The minimum information that must be filled in is indicated below.
4.6.5.1.1. General
In this tab, it is required to fill in at least the following fields.
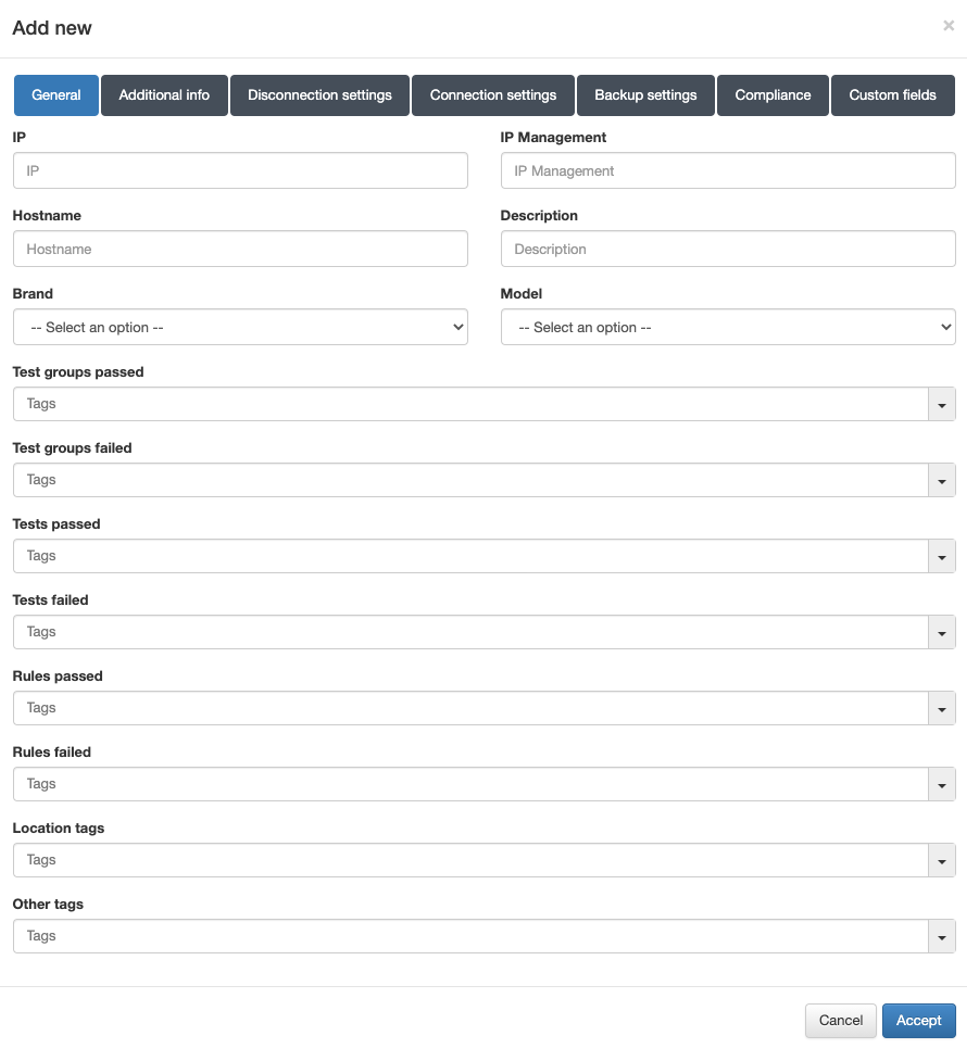
IP: IP address that identifies the device.
The IP address is only for identification (to see it in the device table).
Hostname: Hostname that identifies the device.
Brand / Model: Brand and model of the device.
It is important to correctly define the brand and model since these will be used to determine the behavior of the system in terms of communication with these devices.
4.6.5.1.2. APs Management controller
When there are many APs centrally controlled by a controller in the network, it is necessary to add the controller as a network device in the CMDB and additional information for each of the APs in the CMDB.
For these APs, apart from the minimum information detailed above, it will be necessary to add the information corresponding to IP Management:
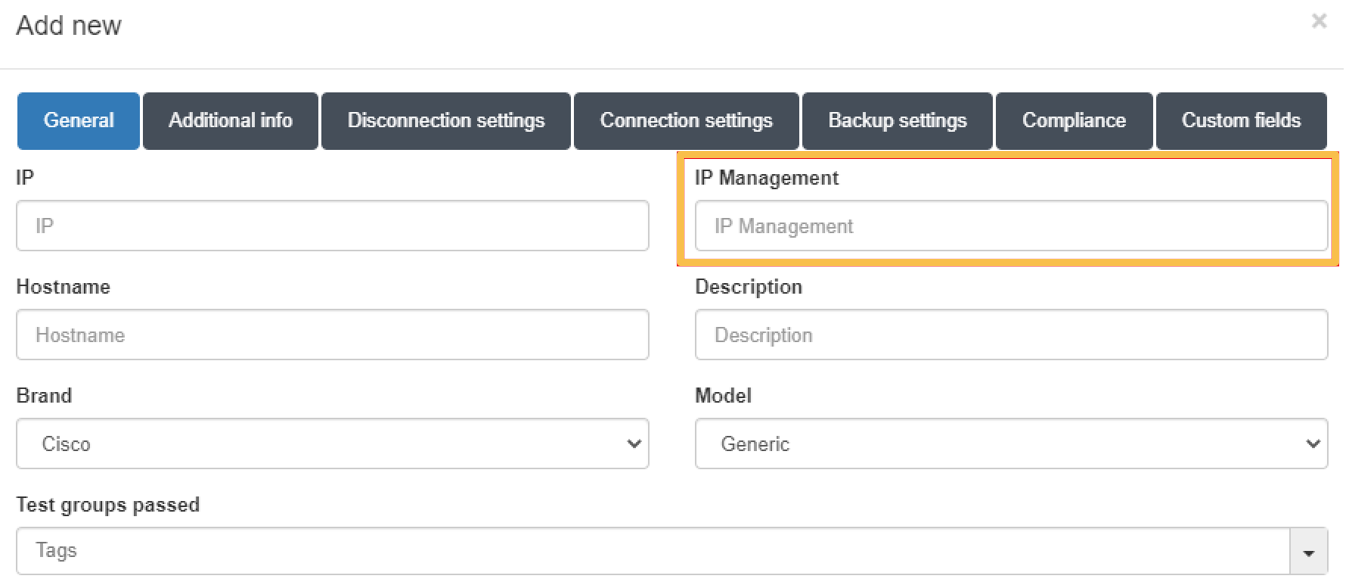
This IP must correspond to the IP associated with the controller that manages the AP.
4.6.5.1.3. Disconnection settings
In the “Disconnection settings” section, the configuration of the Toggle Port functionality is defined. This functionality allows you to force a disconnect from an authenticated session. This allows us, for example, to carry out a re-evaluation of the policies in case they have been modified, and the application of VLANs, ACLs, etc. to the session.
There are two methods of session disconnection:
CoA (Change of Authorization): CoA is a Radius mechanism that allows us to disconnect a specific session without the need to modify the port status (enable/disable) of the network device.
SNMP: Using SNMP, the interface where the device has been authenticated is disabled and enabled. This causes the device to have to re-authenticate and subsequently evaluate policies on the system.
Depending on the type of network device we have the following options:
Wired: SNMP or CoA
Wireless: CoA
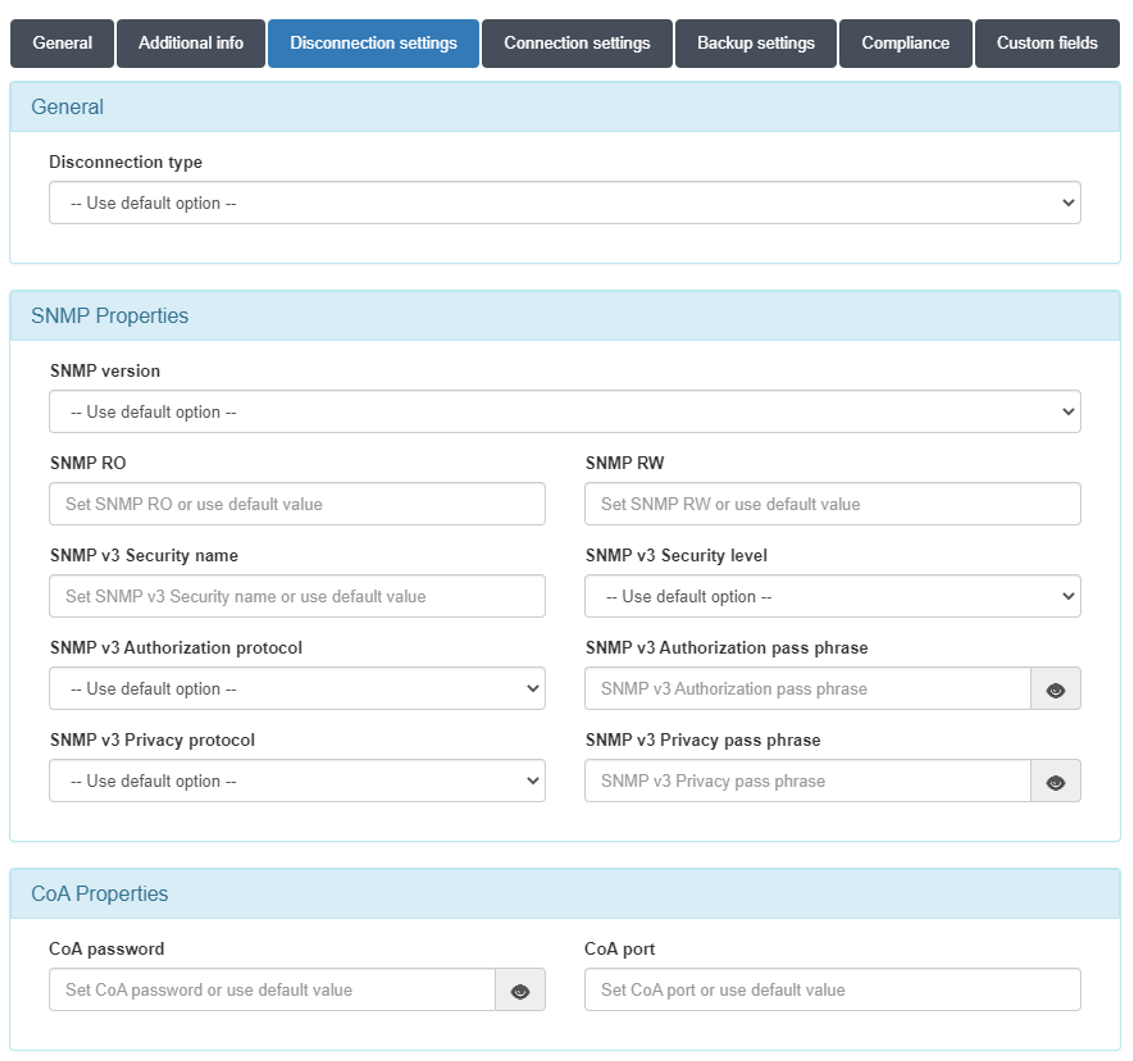
Disconnect type:
Use default option: The configuration defined in “Configuration vars” will be applied.
CoA: Use of CoA to perform session disconnections.
SNMP: Use of SNMP to perform session disconnections.
SNMPProperties
SNMP version: Version used for SNMP messages. The required attributes for each of the versions are:
V1 (not recommended):
SNMP RO: SNMP community with read permissions.
SNMP RW: SNMP community with write permissions.
V2c:
SNMP RO: SNMP community with read permissions.
SNMP RW: SNMP community with write permissions.
V3 (recommended):
SNMP v3 Security name: SNMP username.
SNMP v3 Security level: Security level (noAuthNoPriv/authNoPriv/authPriv).
Depending on the selection, it will be necessary or not to configure some of the following attributes.
SNMP v3 Authorization protocol: Authorization protocol (MD5/SHA).
SNMP v3 Authorization pass phrase: Password for authorization.
SNMP v3 Privacy protocol: Privacy protocol (DES/AES).
SNMP v3 Privacy pass phrase: Password for privacy.
CoAProperties
CoA password: Password defined in the network device to authenticate CoA requests.
CoA port: Port used for communication. (Usually 3799).
If you do not perform any of the configurations, those defined in Configuration -> Configuration Vars -> NetDev will be used.
4.6.5.2. Manage captive sponsors
In ON Captive -> Captive sponsors, we will be able to add, remove and edit the different sponsors.
The main function of a sponsor will be to validate requests from the users that want to register through a captive workflow. Once a user goes through a workflow where sponsor e-mail validation is required, a validation mail will be send to all the configured sponsors, so they will have to validate the user request and allow them to gain access to the network.
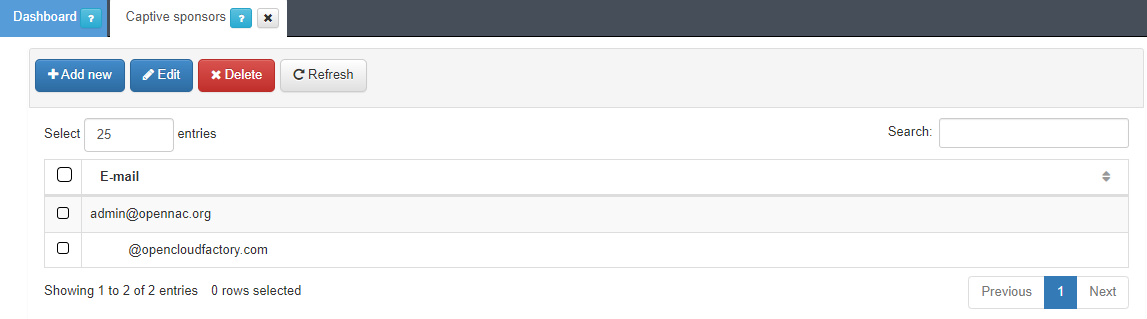
To add a new sponsor, click on the Add new button, a pop up window will appear. Introduce the desired mail and click accept.

4.6.5.3. Create a new captive workflow
A workflow is an authentication process that can be defined in ON Captive -> Captive workflows.
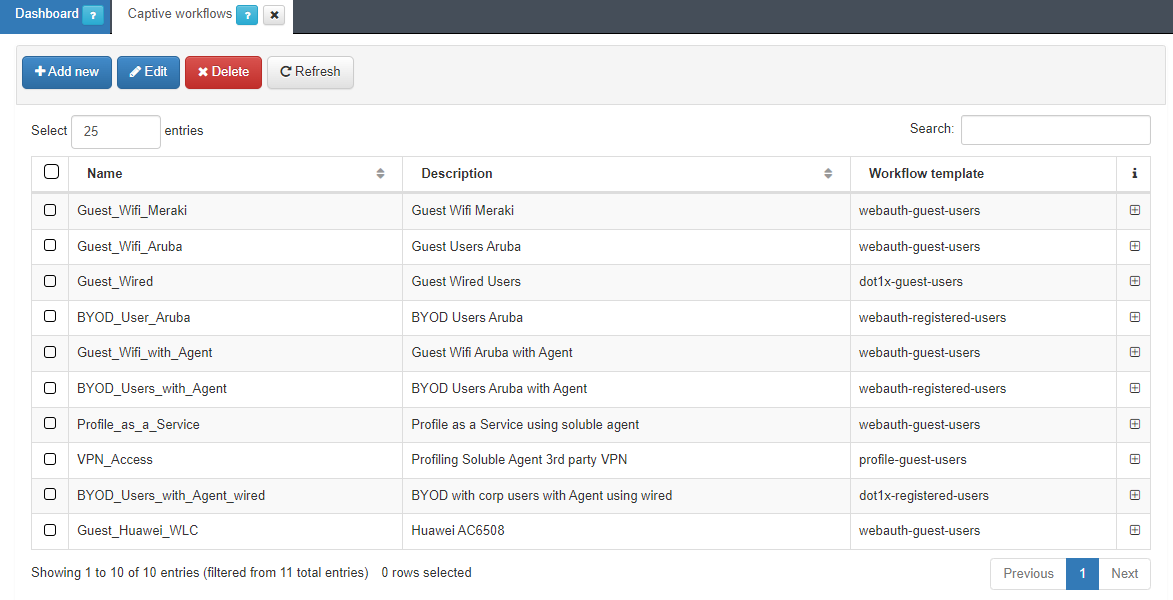
To add a new one, we need to click on the Add new.
We will find five different templates. Two of them are guest templates, one fore wire (dot1x-guest-users) and the other for Wi-Fi (webauth-guest-users).
4.6.5.3.1. Wired workflow
To create a wired workflow, we need set the following parameters in the General tab:
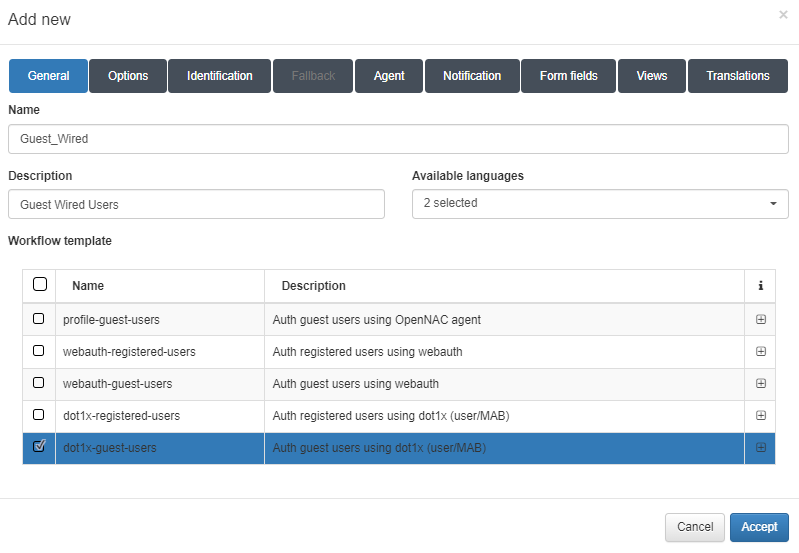
Name: Name of the workflow.
Description: Workflow description.
Available languages: Select all languages in which the workflow can be displayed.
Template: Workflow template. We will find two templates for the guest use case, one for wire and the other for Wi-Fi. We will also find two templates for the BYOD use case, one for wire and the other for Wi-Fi. And finally, we will find one for the OpenNAC agent.
In this case we have selected the dot1x-guest-users template because we want a wired workflow for the guest use case.
In the Options tab, we can find the following parameters to configure:
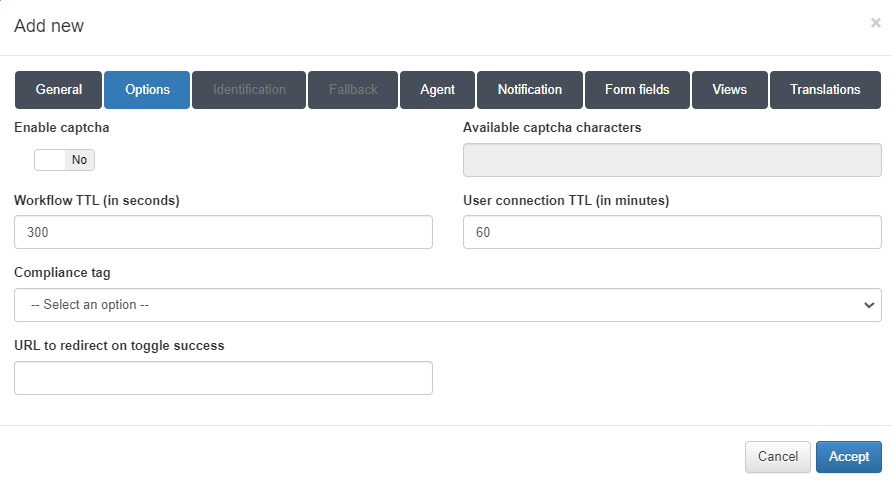
Enable captcha: Allows to enable a captcha in the workflow.
Available captcha characters: All the characters that are in this field, can be on the captcha.
Workflow TTL (in seconds): Seconds that limits the workflow duration.
User connection TTL (in minutes): Maximum minutes of a connection.
Compliance tag: Tag that needs to match to get access to the network. If the tag don’t match, it will show why the user don’t have access.
URL to redirect on toggle success: URL to redirect the guest when the workflow is finished.
Maximum number of attempts to toggle port: Number of the maximum attempts to a toggle port.
Time interval between each attempt (in seconds): Time that needs to pass between two attempts.
Toggle port timeout (in seconds): Timeout for a toggle port.
In the Identification tab we have two types possible to configure, the E-mail type, and the SMS type.
For the E-mail type we can find the next parameters to configure:
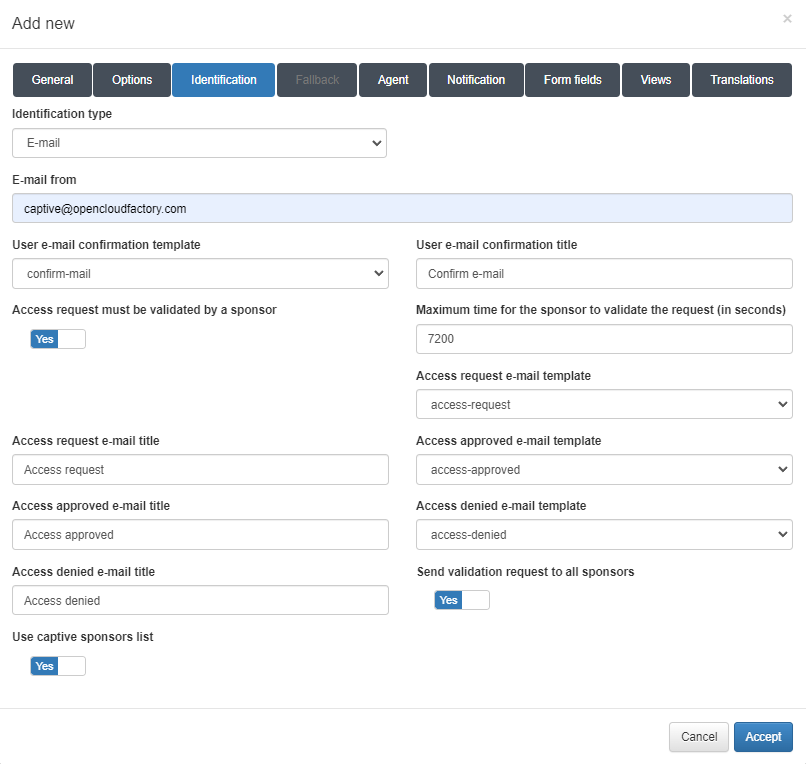
Identification type: Type of identification, in this case is going to be E-mail.
E-mail from: E-mail address that will send the mail to the user.
User e-mail confirmation template: Template of the E-mail.
User e-mail confirmation title: Tittle for the mail.
Access request must be validated by a sponsor: Enables the sponsor validation.
Maximum time for the sponsor to validate the request (in seconds): Time the sponsor has to validate the request.
Access request e-mail template: Template for the access request e-mail.
Access request e-mail title: Tittle for the access request e-mail.
Access approved e-mail template: Template for the access approved e-mail.
Access approved e-mail title: Tittle for the access approved e-mail.
Access denied e-mail template: Template for the access denied e-mail.
Access denied e-mail title: Tittle for the access denied e-mail.
Send validation request to all sponsors: Enables sending the validation to all the sponsors. If it is disabled we will find a sponsor field in the Form fields tab.
Use captive sponsors list: Enables the use of the sponsor list in On Captive -> Captive Sponsors. If it is not enabled, we need to fill the next fields:
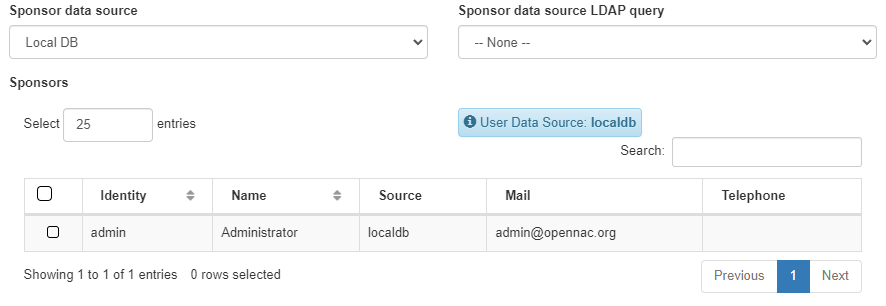
Sponsor data source: Source for the sponsors list.
Sponsor data source LDAP query: LDAP query for the sponsors list source.
Sponsors: Sponsors that can validate the E-mails.
For the SMS type we can find the following parameters to configure:
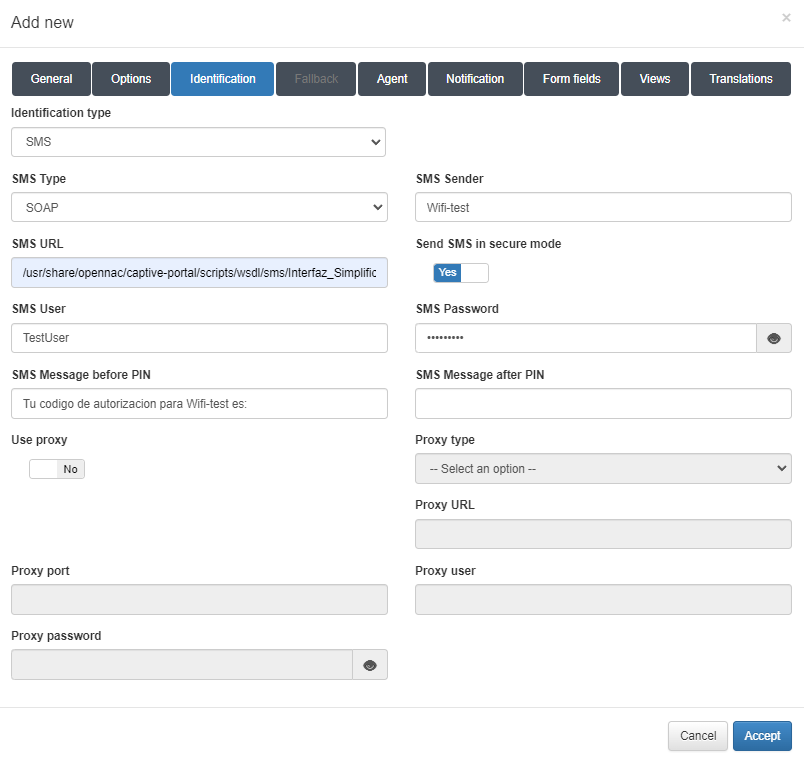
Identification type: Type of identification, in this case is going to be SMS.
SMS Type: Type of SMS, in this the only type we have hired is Mentes.
SMS Sender: Sender that will send the SMS.
SMS URL: URL of the SMS.
Send SMS in secure mode: Enables SMS secure mode.
SMS User: User for the SMS.
SMS Password: Password for the SMS user.
SMS Message before PIN: Text that will go before the PIN.
SMS Message after PIN: Text that will go after the PIN.
Use proxy: Enables to use proxy and activates proxy fields.
Proxy type: Selects the proxy types, HTTP or HTTPS.
Proxy URL: URL for the proxy.
Proxy port: Port for the proxy.
Proxy user: User fot the proxy.
Proxy password: Password for the proxy user.
In the Agent tab, we can enable the ON agent for that workflow.
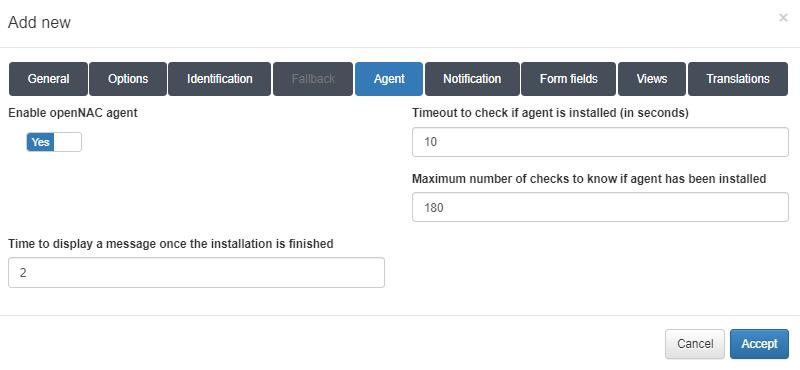
Enable openNAC agent: Enables the ON agent.
Timeout to check if agent is installed (in seconds): Timeout to check if an agent is installed.
Maximum number of checks to know if agent has been installed: Maximum number of checks for an agent installation.
Time to display a message once the installation is finished: Time to display a message when the installation is finished.
In the Notification tab we can enable notifications to the user.
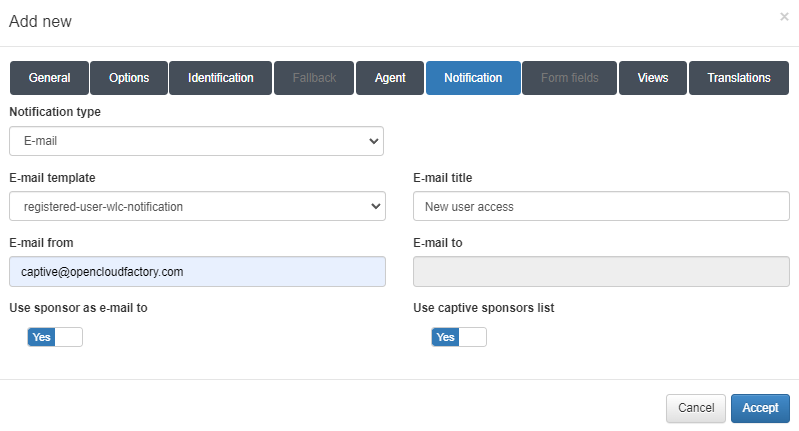
Notification type: Password for the SMS user.
E-mail template: Text that will go before the PIN.
E-mail title: Text that will go after the PIN.
E-mail from: Enables to use proxy and activates proxy fields.
E-mail to: Selects the proxy types, HTTP or HTTPS.
Use sponsor as e-mail to: Enables sending the notification to the sponsors.
Use captive sponsors list: Enables the use of the sponsor list in ON Captive -> Captive Sponsors. If it is not enabled, we need to fill the next fields:

Sponsor data source: Source for the sponsors list.
Sponsor data source LDAP query: LDAP query for the sponsors list source.
Sponsors: Sponsors that can validate the E-mails.
In the Form fields tab we can create forms that ask for fields in the workflow.
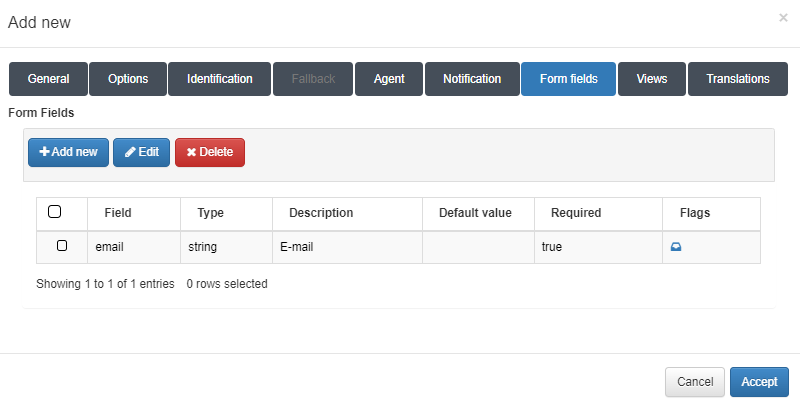
To add one form, click on the Add new button:
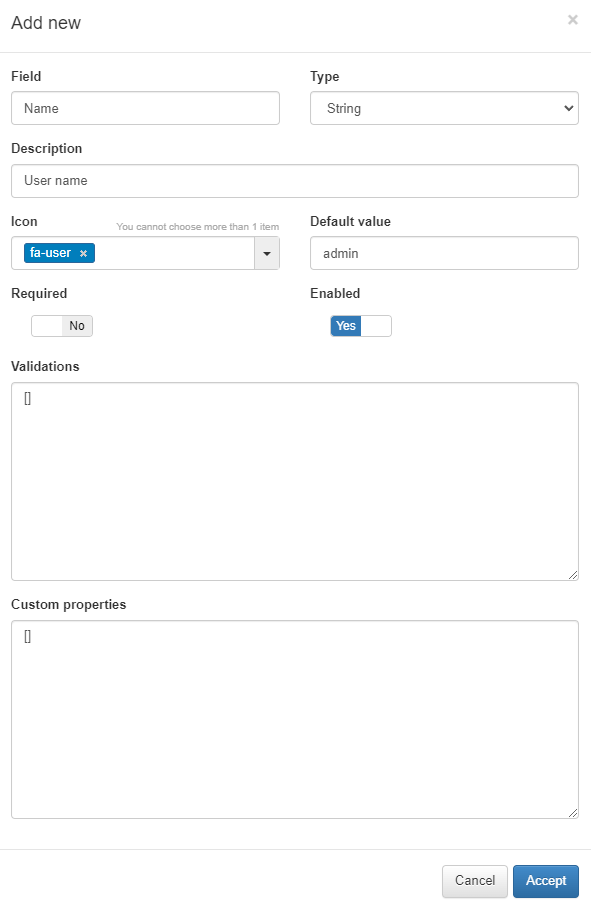
Field: The name of the field.
Type: This pop up menu have the set of data types corresponding to the form filed being created. The type selected must match with the type of information filled by the user. For example, if the information is an username, the type must be String, if the information is a password, then the type must be password, and so on.
Description: A meaningful description about the purpose of the form field.
Icon: The icon image that will be displayed on the column Flags of the form field. It helps to visually quickly guess what is the corresponding type of information.
Default value: (for what information?)
Required: Define if this form field must necessarily be filled by the user.
Enabled: Define if the form filed is enabled and will be displayed on the authentication screen along with other fields.
Validations: The type of validation to be performed by the ON Captive module during the authentication process to ensure if the information is really what is being expected on this particular form field.
Custom properties: Specific additional properties which can be necessary for validation of certain types of submitted data and/or to be further verified.
Finally, the Views section allow the insertion of custom code which will change the presentation layer behavior of the captive portal Web elements, according the specifics needs of the customer. In order to allow the insertion of code for each view, click on the toggle switch button which by default is on the Use Default position. It will change to Set Custom, this allowing you to insert the custom view code.
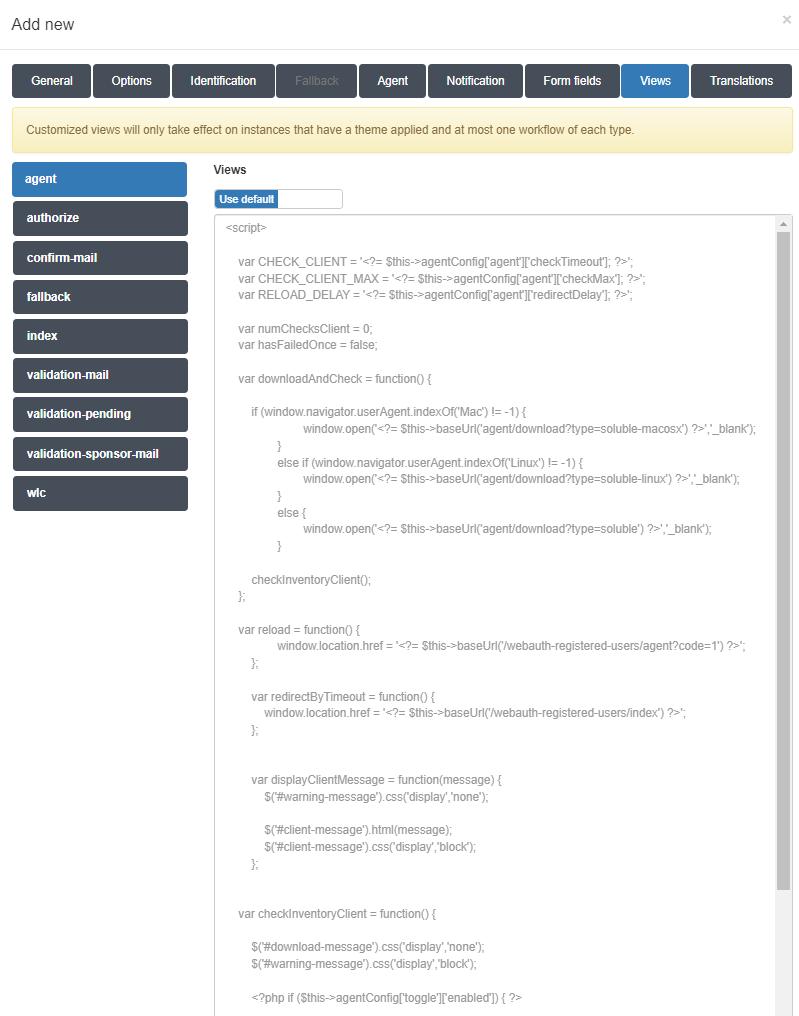
Finally, the Translations section allows adding translations for the workflow name and description in the workflow presentation. The languages we will find are the selected in the General section.
4.6.5.3.2. Wi-Fi workflow
To create a Wi-Fi workflow we need set the following parameters in the General tab:
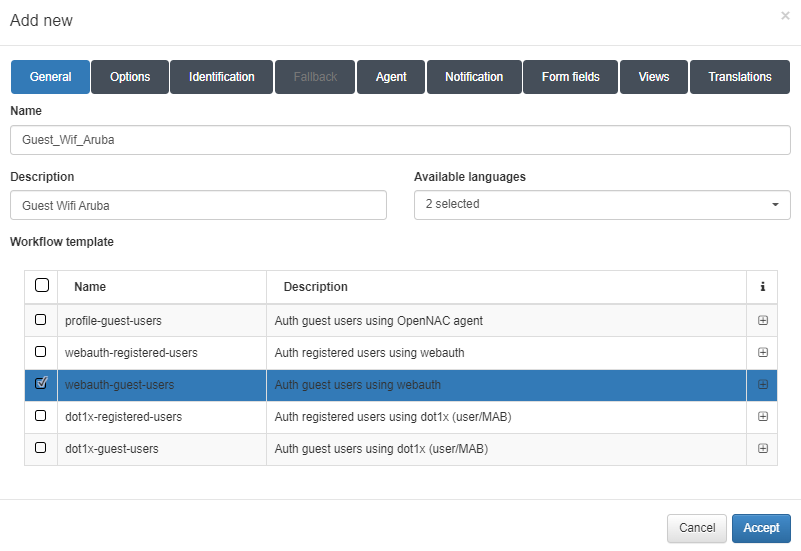
Name: Name of the workflow.
Description: Workflow description.
Available languages: Select all languages in which the workflow can be displayed.
Template: Workflow template. We will find two templates for the guest use case, one for wire and the other for Wi-Fi. We will also find two templates for the BYOD use case, one for wire and the other for Wi-Fi. And finally, we will find one for the OpenNAC agent.
In this case, we have selected the webauth-guest-users template because we want a Wi-Fi workflow for the guest use case.
In the Options tab, we can find the following parameters to configure:
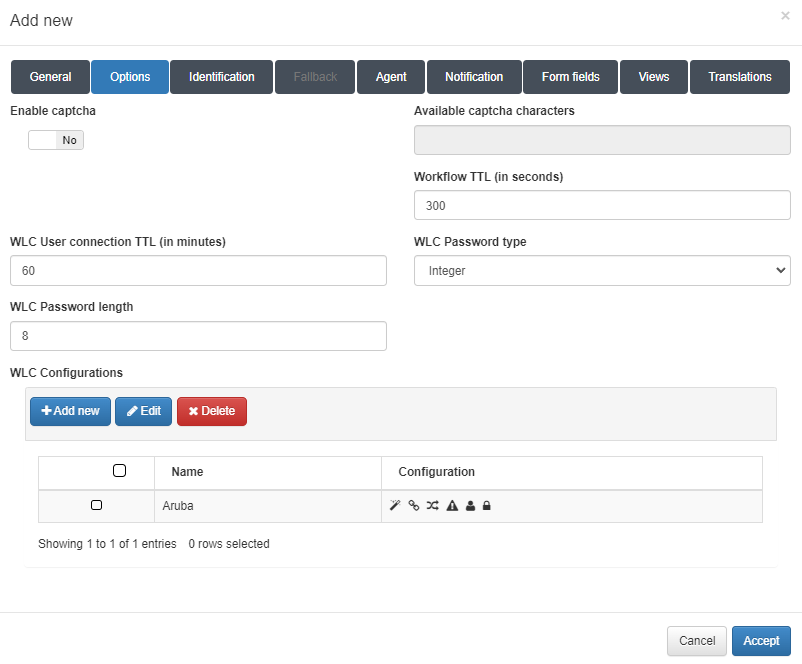
Enable captcha: Allows to enable a captcha in the workflow.
Available captcha characters: All the characters that are in this field, can be on the captcha.
Workflow TTL (in seconds): Seconds that limits the workflow duration.
WLC User connection TTL (in minutes): Maximum minutes of a WLC connection. It need to be synchronized with the WLC TTL, to avoid desynchronization.
WLC Password type: Type of the WLC password.
WLC Password length: WLC password length.
WLC Configurations: WLC type configuration. To add a new one, click on the Add new button:
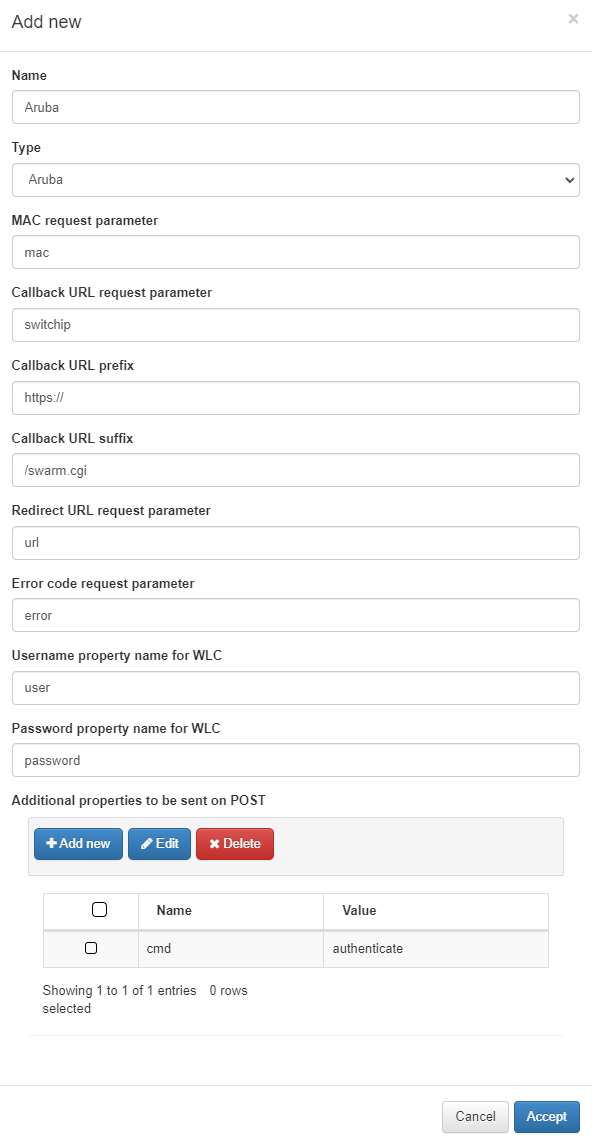
Name: Name for the WLC configuration.
Type: Type of configuration. We can select three templates (Aruba, Cisco and Meraki) or select Other to insert a custom one.
MAC request parameter: Parameter for MAC request.
Callback URL request parameter: URL for the request parameter callback.
Callback URL prefix: URL for the prefix callback.
Callback URL suffix: URL for the sufix callback.
Redirect URL request parameter: URL for the request parameter redirect.
Error code request parameter: URL for the request parameter error code.
Username property name for WLC: WLC username.
Password property name for WLC: Password fot the WLC username.
Additional properties to be sent on POST: Permits to add new properties to the POST.
In the Identification tab we have two types possible to configure, the E-mail type, and the SMS type.
For the E-mail type we can find the next parameters to configure:

Identification type: Type of identification, in this case is going to be E-mail.
E-mail from: E-mail address that will send the mail to the user.
User e-mail confirmation template: Template of the E-mail.
User e-mail confirmation title: Tittle for the mail.
Access request must be validated by a sponsor: Enables the sponsor validation.
Maximum time for the sponsor to validate the request (in seconds): Time the sponsor has to validate the request.
Access request e-mail template: Template for the access request e-mail.
Access request e-mail title: Tittle for the access request e-mail.
Access approved e-mail template: Template for the access approved e-mail.
Access approved e-mail title: Tittle for the access approved e-mail.
Access denied e-mail template: Template for the access denied e-mail.
Access denied e-mail title: Tittle for the access denied e-mail.
Send validation request to all sponsors: Enables sending the validation to all the sponsors. If it is disabled we will find a sponsor field in the Form fields tab.
Use captive sponsors list: Enables the use of the sponsor list in ON Captive -> Captive Sponsors. If it is not enabled, we need to fill the following fields:

Sponsor data source: Source for the sponsors list.
Sponsor data source LDAP query: LDAP query for the sponsors list source.
Sponsors: Sponsors that can validate the E-mails.
For the SMS type, we can find the following parameters to configure:

Identification type: Type of identification, in this case is going to be SMS.
SMS Type: Type of SMS, in this the only type we have hired is Mentes.
SMS Sender: Sender that will send the SMS.
SMS URL: URL of the SMS.
Send SMS in secure mode: Enables SMS secure mode.
SMS User: User for the SMS.
SMS Password: Password for the SMS user.
SMS Message before PIN: Text that will go before the PIN.
SMS Message after PIN: Text that will go after the PIN.
Use proxy: Enables to use proxy and activates proxy fields.
Proxy type: Selects the proxy types, HTTP or HTTPS.
Proxy URL: URL for the proxy.
Proxy port: Port for the proxy.
Proxy user: User fot the proxy.
Proxy password: Password for the proxy user.
In the Agent tab we can enable the ON agent for that workflow.

Enable openNAC agent: Enables the ON agent.
Timeout to check if agent is installed (in seconds): Timeout to check if an agent is installed.
Maximum number of checks to know if agent has been installed: Maximum number of checks for an agent installation.
Time to display a message once the installation is finished: Time to display a message when the installation is finished.
In the Notification tab we can enable notifications to the user.

Notification type: Password for the SMS user.
E-mail template: Text that will go before the PIN.
E-mail title: Text that will go after the PIN.
E-mail from: Enables to use proxy and activates proxy fields.
E-mail to: Selects the proxy types, HTTP or HTTPS.
Use sponsor as e-mail to: Enables sending the notification to the sponsors.
Use captive sponsors list: Enables the use of the sponsor list in ON Captive -> Captive Sponsors. If it is not enabled, we need to fill the following fields:

Sponsor data source: Source for the sponsors list.
Sponsor data source LDAP query: LDAP query for the sponsors list source.
Sponsors: Sponsors that can validate the E-mails.
In the Form fields tab, we can create forms that ask for fields in the workflow.

To add one form, click on the Add new button:

Field: The name of the field.
Type: This pop up menu have the set of data types corresponding to the form filed being created. The type selected must match with the type of information filled by the user. For example, if the information is an username, the type must be String, if the information is a password, then the type must be password, and so on.
Description: A meaningful description about the purpose of the form field.
Icon: The icon image that will be displayed on the column Flags of the form field. It helps to visually quickly guess what is the corresponding type of information.
Default value: (for what information?)
Required: Define if this form field must necessarily be filled by the user.
Enabled: Define if the form filed is enabled and will be displayed on the authentication screen along with other fields.
Validations: The type of validation to be performed by the ON Captive module during the authentication process to ensure if the information is really what is being expected on this particular form field.
Custom properties: Specific additional properties which can be necessary for validation of certain types of submitted data and/or to be further verified.
Finally, the Views section allow the insertion of custom code which will change the presentation layer behavior of the captive portal Web elements, according the specifics needs of the customer. In order to allow the insertion of code for each view, click on the toggle switch button which by default is on the Use Default position. It will change to Set Custom, this allowing you to insert the custom view code.

Finally, the Translations section allows adding translations for the workflow name and description in the workflow presentation. The languages we will find are the ones selected in the General section.

4.6.5.3.3. Profile Based workflow
To create a Profile Based workflow, we need set the following parameters in the General tab:
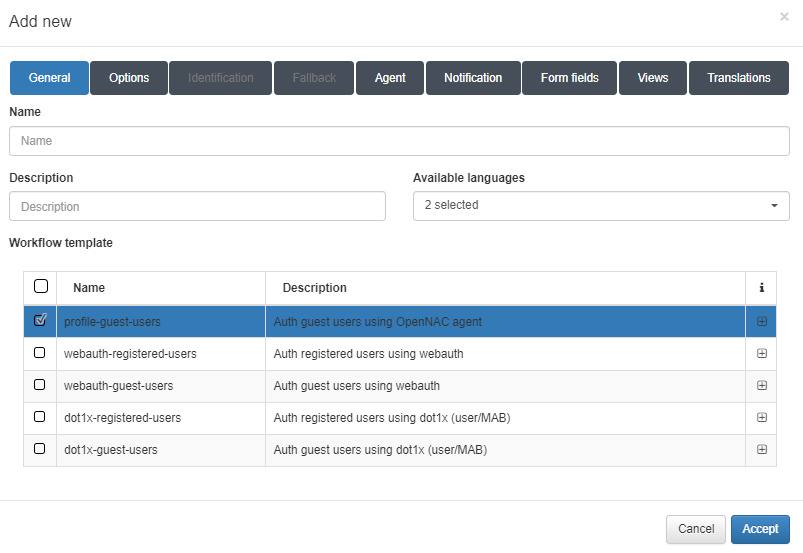
Name: Name of the workflow.
Description: Workflow description.
Available languages: Select all languages in which the workflow can be displayed.
Template: Workflow template. We will find two templates for the guest use case, one for wire and the other for Wi-Fi. We will also find two templates for the BYOD use case, one for wire and the other for Wi-Fi. And finally, we will find one for the Profile using ON Agent.
In this case, we have selected the profile-guest-users template because we want a profile workflow for the guest use case using the ON Agent.
In the Options tab we can find the following parameters to configure:
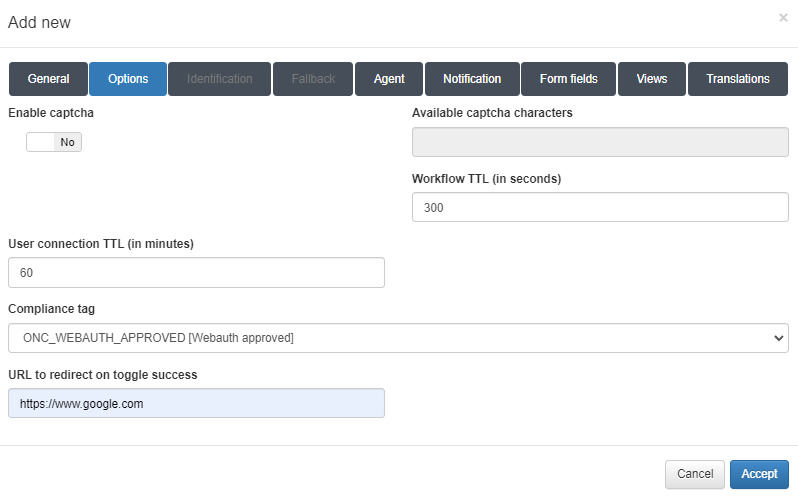
Enable captcha: Allows to enable a captcha in the workflow.
Available captcha characters: All the characters that are in this field, can be on the captcha.
Workflow TTL (in seconds): Seconds that limits the workflow duration.
User connection TTL (in minutes): Maximum minutes of a connection.
Compliance tag: Tag that needs to match to get access to the network. If the tag doesn’t match, it will show why the user doesn’t have access. The usual tag is ONC_WEBAUTH_APPROVED.
URL to redirect on toggle success: URL to redirect the guest when the workflow is finished.
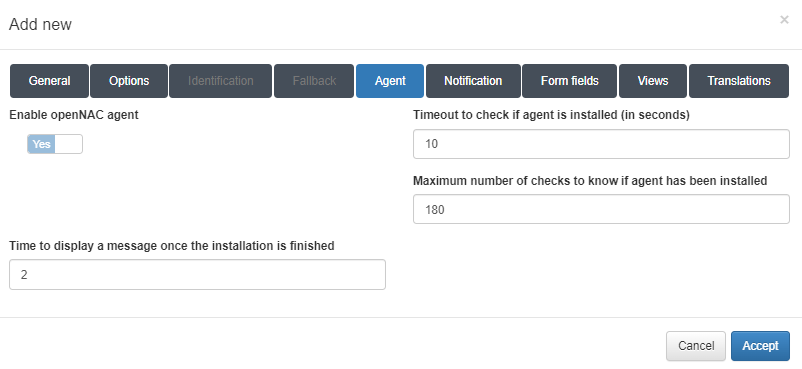
Enable openNAC agent: Enables the ON Agent.
Timeout to check if agent is installed (in seconds): Timeout to check if an Agent is installed. Since the agent is essential for this workflow, this field cannot be modified.
Maximum number of checks to know if agent has been installed: Maximum number of checks for an agent installation.
Time to display a message once the installation is finished: Time to display a message when the installation is finished.
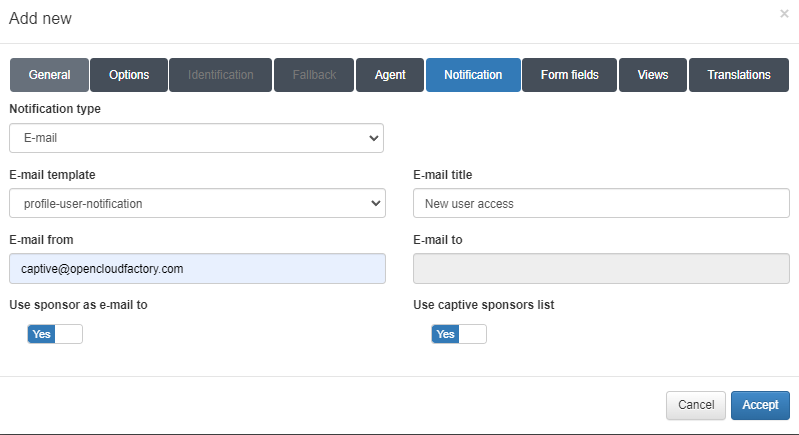
Notification type: Type of notification to use. We can use email notification or not use notification (None).
In case of using e-mail:
E-mail template: Text template for the notification to be sent.
E-mail title: Title of the email that will be sent as notification.
E-mail from: From which email address will the email be sent.
E-mail to: To which email address will the email be sent.
Use sponsor as e-mail to: Enables sending the notification to the sponsors.
Use captive sponsors list: Enables the use of the sponsor list in On Captive -> Captive Sponsors. If it is not enabled, we need to fill the next fields:
Important
Remember that for email notifications it is necessary to have the postfix email delivery service configured.
In the Form fields tab, we can create forms that ask for fields in the workflow.
Finally, the Views section allows the insertion of a custom code which will change the presentation layer behavior of the captive portal Web elements, according the specifics needs of the customer. To allow the insertion of a code for each view, click on the toggle switch button which by default is on the Use Default position. It will change to Set Custom, allowing you to insert the custom view code.
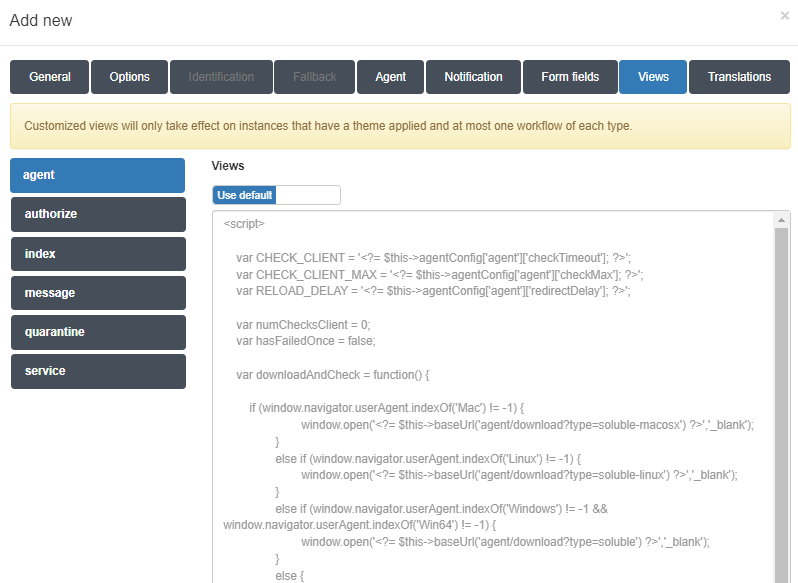
Finally, the Translations section allows adding translations for the workflow name and description in the workflow presentation. The languages we will find are the ones selected in the General section.

4.6.5.4. Create a new captive domain
We will be able to create a new group of workflows in ON Captive -> Captive domains.
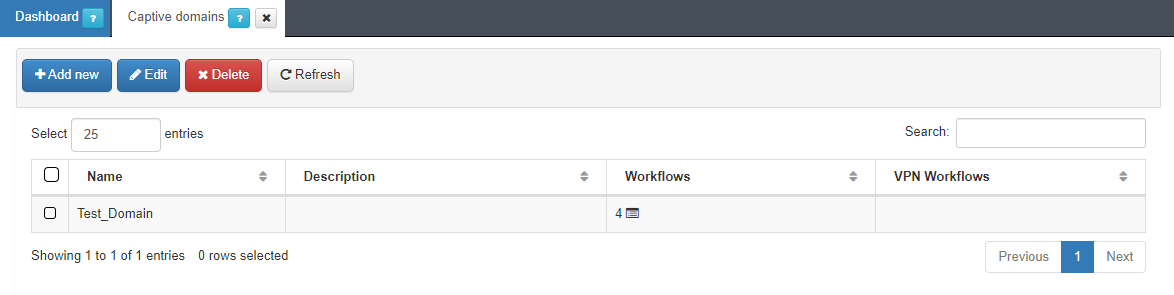
To create a new Captive domain, click on the Add new button to open the following window:
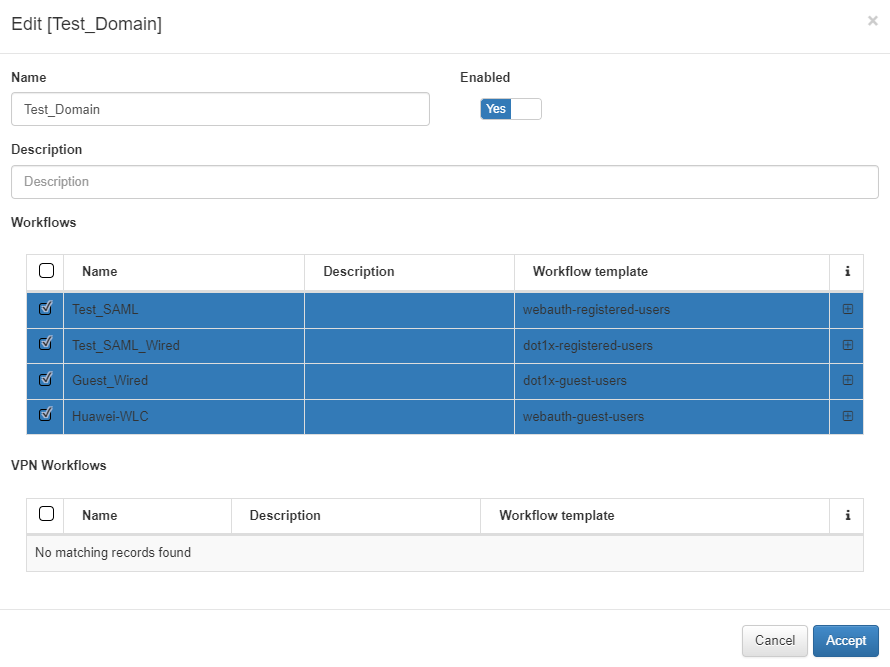
Name: The chosen name of this new Captive domain.
Enabled: This option defines if this Captive domain is active for use or not.
Description: A meaningful description about this now domain.
Workflows: Here you must to select one or more Captive workflows previously created.
VPN Workflows: Here you must to select one or more Captive VPN workflows previously created.
We will select the Guest_Wired workflow previously created and other workflows to join the Test_Domain.
To finish the creation of the new Captive domain, which will be used in the next steps, click on the button Accept.
4.6.5.5. Create a new captive instance
We can create a new instance for the captive domain in ON Captive -> Captive instances.
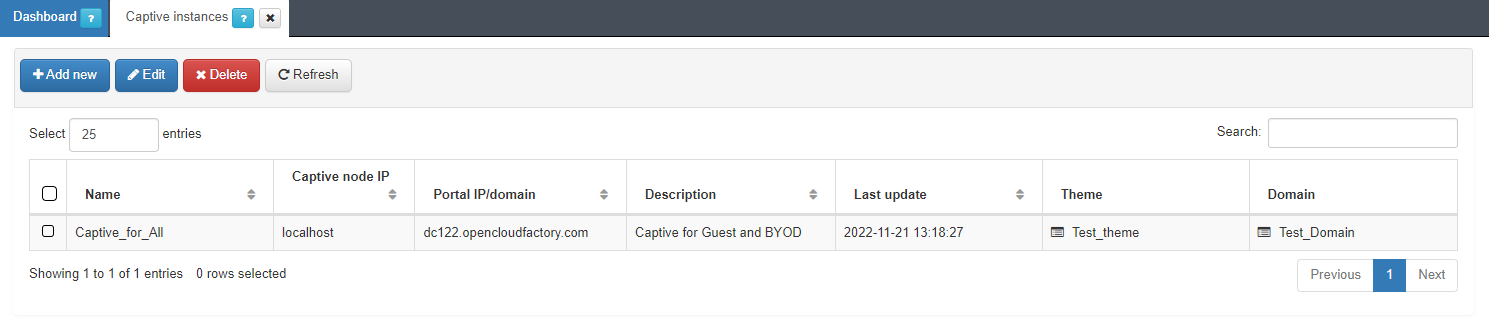
To create a new Captive instance, click on the Add new button to open the following window. The following configurations must be performed to get a working Captive instance which will be built over the configurations described in the previous topics:
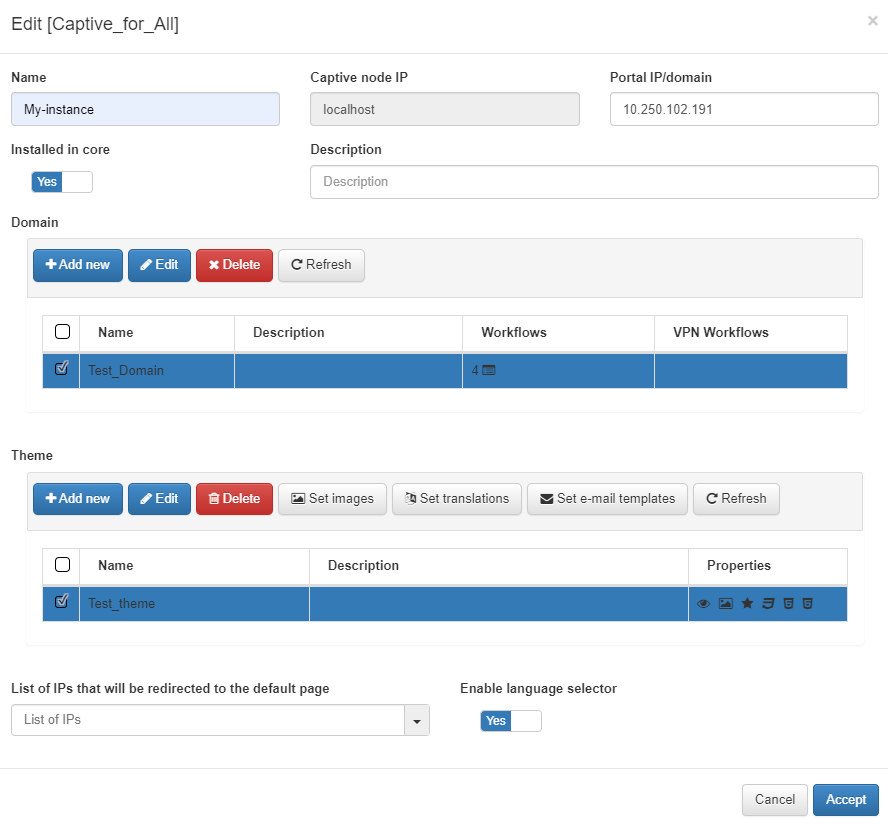
Name: The name of the new captive instance being created.
Captive node IP: The IP address for the Captive node.
Portal IP/Domain: The IP address or FQDN of the server running the openNAC Captive Portal. It can be the same IP of the ON Core server, if the captive portal will be running on this server along with ON Core or the address can be one of a separate server dedicated to run the openNAC Captive Portal.
Installed in core: Set to yes if the Captive Portal is running on the ON Core
Description: A meaningful description about this new Captive instance.
Domain: Select a previously created captive domain you want to associate with this new captive instance.
Theme: Select a captive theme. If there is not any theme select, a default one will be applied.
List of IPs that will be redirected to the default page: The IP or IPs that will be redirected
Enable language selector: Enables the language selector in the Captive portal instance. The shown languages depend on the languages configured inside ON Captive -> Captive themes in the General section, with the corresponding translations in Translations section. If this selector is not enabled, the language will be the browser language.
4.6.5.6. Creation of wired policies
It is necessary to add different policies for the wired Guest use case. This policies are added in ON NAC -> Policies. The policies to be configured are the following:
Important
The order is important. It goes from most restrictive to less.
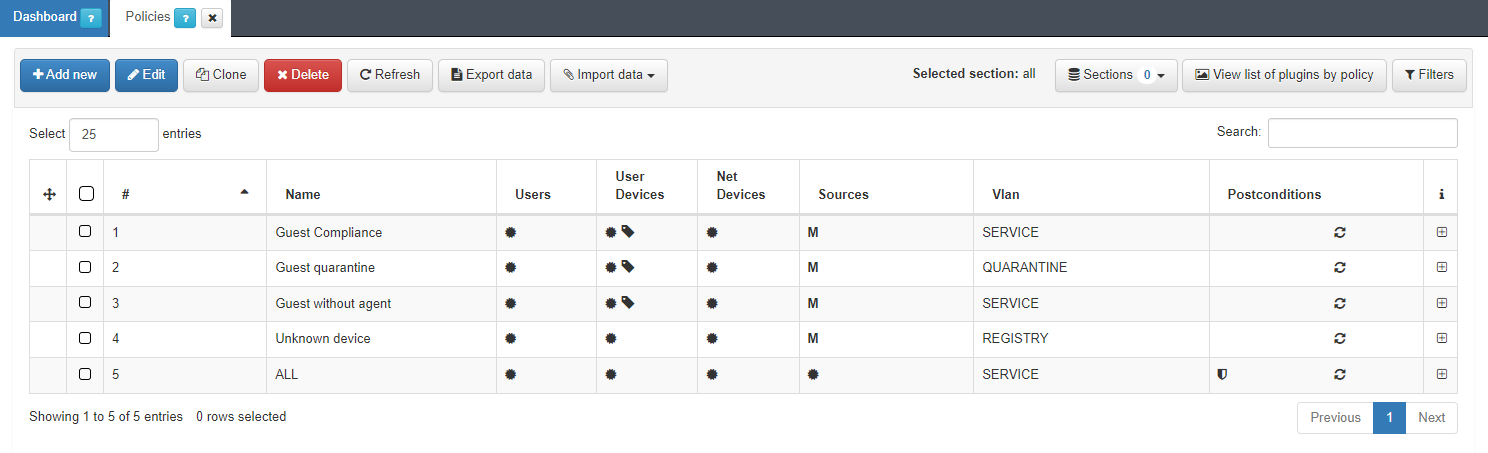
4.6.5.6.1. Unknown device
The first policy to be configured is the Unknown device. This policy matches all the devices connected by wire that don’t match any of the other policies.
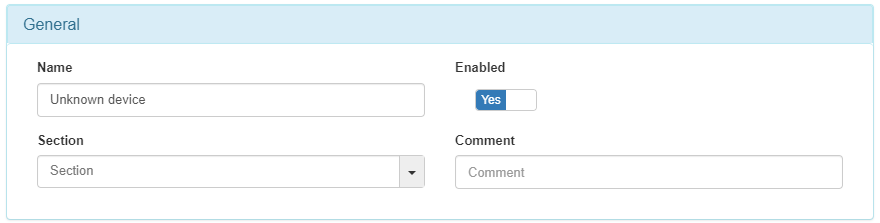
It is necessary to set MAB at Preconditions: Source.
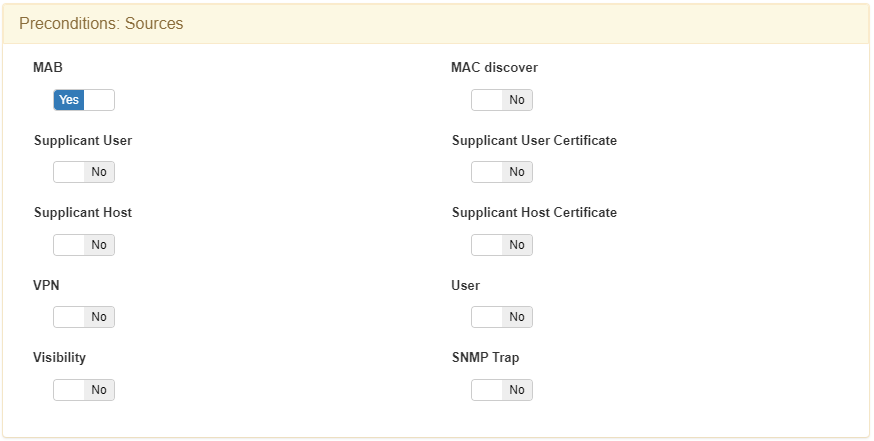
It sends the device to a VLAN of type Registry, because it needs to be registered.
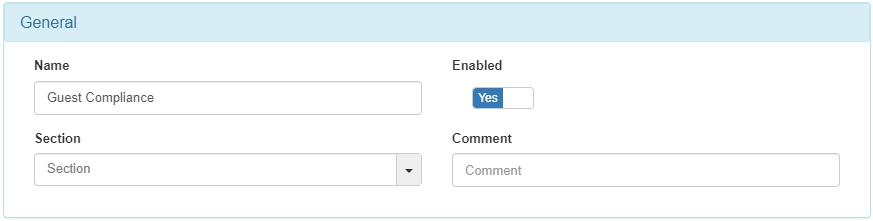
4.6.5.6.2. Guest Compliance
The next policy to configure is the Guest Compliance. This policy matches all the devices connected by wire that matched the guest workflow with compliance.
If the device needs to be compliant, it needs to have the following tags:
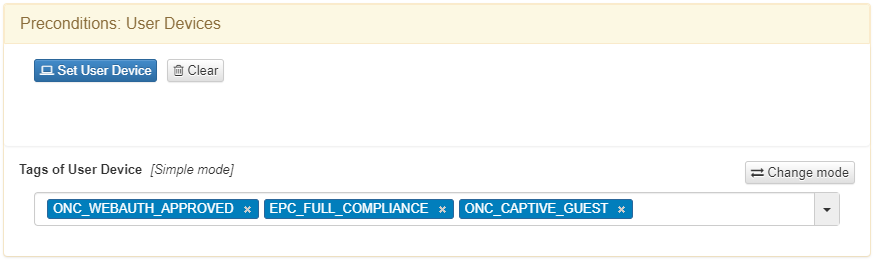
ONC_WEBAUTH_APPROVED: Indicates that the workflow is finished.
EPC_FULL_COMPLIANCE: Compliance tag that needs to match with the captive portal configuration.
ONC_CAPTIVE_GUEST: Indicates that is a guest workflow
It is necessary to set MAB at Preconditions: Source.

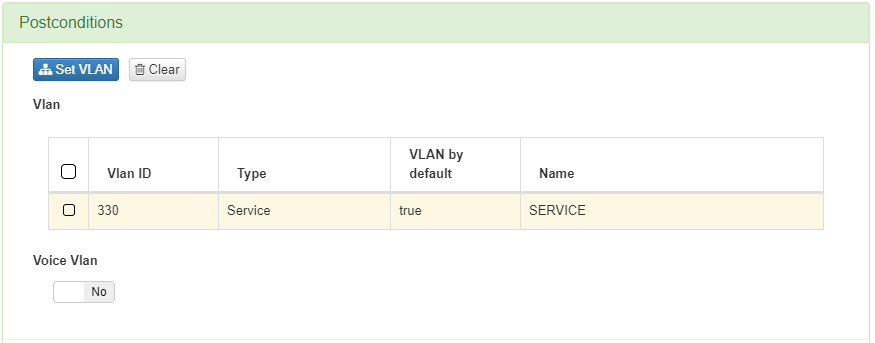
It sends the device to a VLAN of type Service, to give access to the device.
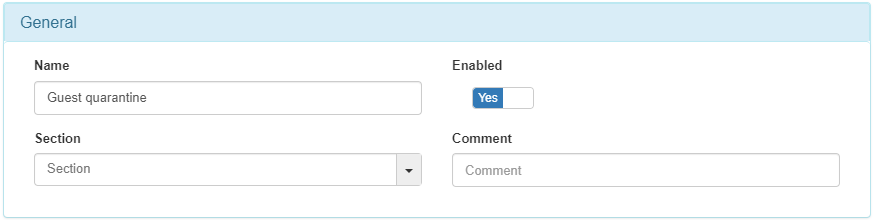
4.6.5.6.3. Guest quarantine
The next policy to configure is the Guest quarantine. This policy matches all the devices connected by wire that passed the guest workflow with agent authentication.
The tags that a device would have after a workflow if agent authentication is enabled are the following:
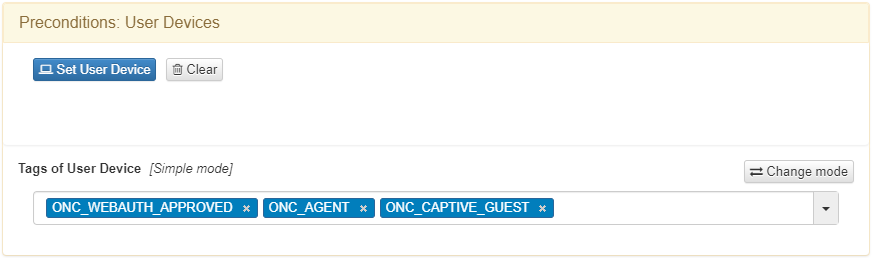
ONC_WEBAUTH_APPROVED: Indicates that the workflow is finished.
ONC_AGENT: Indicates that agent authentication is fine.
ONC_CAPTIVE_GUEST: Indicates that is a guest workflow
It is necessary to set MAB at Preconditions: Source.

It sends the device to a VLAN of type Quarantine, to notify the missing requirements for the device to be compliant.
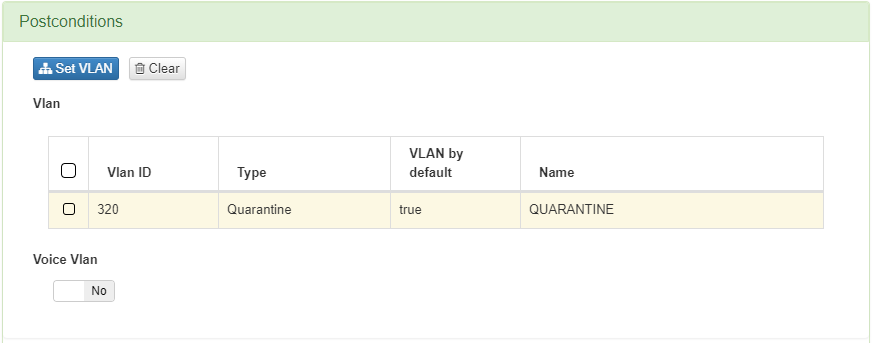
4.6.5.6.4. Guest without agent
The next policy to configure is the Guest without agent. This policy matches all the devices connected by wire that passed the a guest workflow.
The tags that a device would have after a workflow are the following:
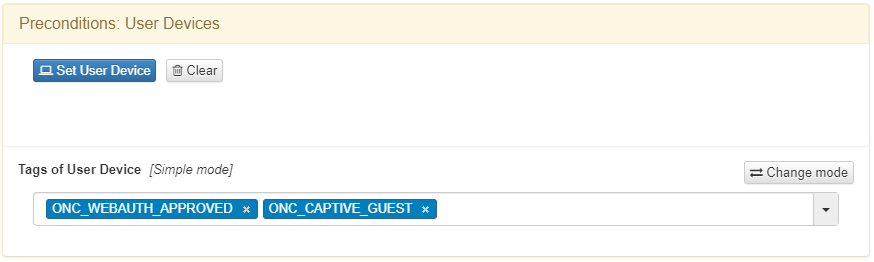
ONC_WEBAUTH_APPROVED: Indicates that the workflow is finished.
ONC_CAPTIVE_GUEST: Indicates that is a guest workflow
It is necessary to set MAB at Preconditions: Source.

It sends the device to a VLAN of type Service, to notify the missing requirements for the device to be compliant.

4.6.5.7. Creation of Wi-Fi policies
It is necessary to add different policies for Guest use case with Wi-Fi. This policies are added in ON NAC -> Policies. The policies to configure are the following:
Important
The order is important. It goes from most restrictive to less.
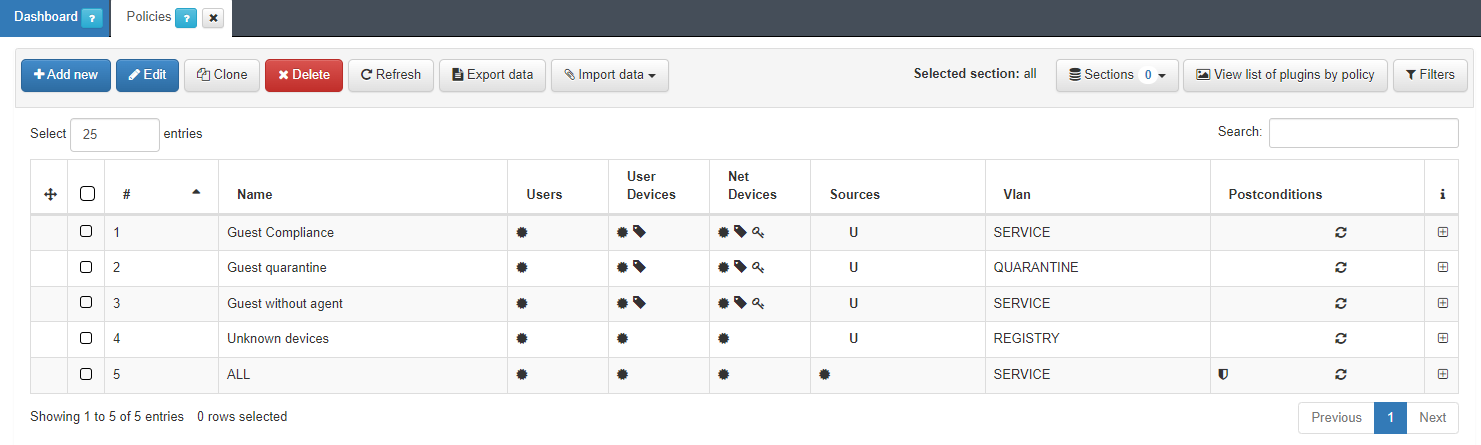
4.6.5.7.1. Unknown device
The first policy to configure is the Unknown device. This policy matches all the devices connected by Wi-Fi that don’t pass any of the other policies.

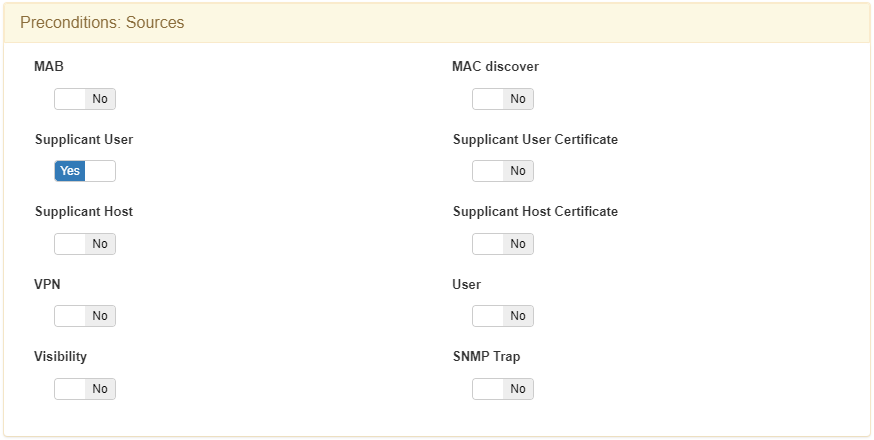
It is necessary to set Supplicant User at Preconditions: Source.
It sends the device to a VLAN of type Registry, because it needs to be registered.

4.6.5.7.2. Guest Compliance
The next policy to configure is the Guest Compliance. This policy matches all the devices connected by Wi-Fi that passed the guest workflow with compliance.

For a device to be compliant, it needs to have the following tags:

ONC_WEBAUTH_APPROVED: Indicates that the workflow is finished.
EPC_FULL_COMPLIANCE: Compliance tag that needs to match with the captive portal configuration.
ONC_CAPTIVE_GUEST: Indicates that is a guest workflow
It is necessary to set the NDT_WIFI tag, that filters by network device type, and the SSID of the WLC at Preconditions: Network Devices.
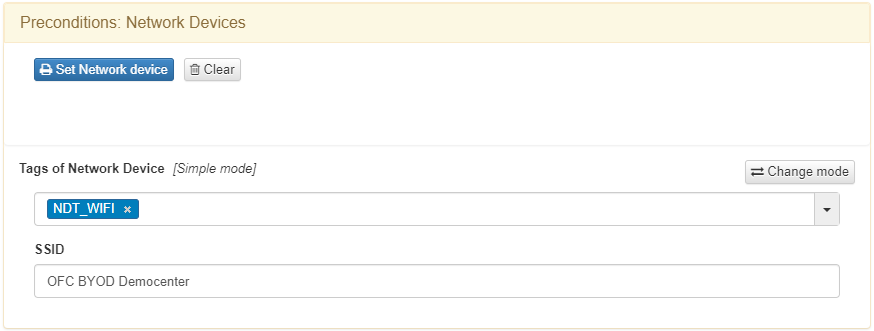
It is necessary to set Supplicant User at Precondition: Source.

It sends the device to a VLAN of type Service, to give access to the device.

4.6.5.7.3. Guest quarantine
The next policy to configure is the Guest quarantine. This policy matches all the devices connected by Wi-Fi that passed the guest workflow with agent authentication.

The tags that a device would have after a workflow if the Agent authentication is enabled are the following:

ONC_WEBAUTH_APPROVED: Indicates that the workflow is finished.
ONC_AGENT: Indicates that agent authentication is fine.
ONC_CAPTIVE_GUEST: Indicates that is a guest workflow
It is necessary to set the NDT_WIFI tag, that filters by network device type, and the SSID of the WLC at Preconditions: Network Devices.

It is necessary to set Supplicant User at Preconditions: Source.

It sends the device to a VLAN of type Quarantine, to notify the device of the missing requirements for compliance.

4.6.5.7.4. Guest without agent
The next policy to configure is the Guest without agent. This policy matches all the devices connected by Wi-Fi that passed the a guest workflow.

The tags that a device would have after a workflow are the following:

ONC_WEBAUTH_APPROVED: Indicates that the workflow is finished.
ONC_CAPTIVE_GUEST: Indicates that is a guest workflow
It is necessary to set the NDT_WIFI tag, that filters by network device type, and the SSID of the WLC at Preconditions: Network Devices.

It is necessary to set Supplicant User at Preconditions: Source.

It sends the device to a VLAN of type Service, to notify the device of the missing requirements for compliance

4.6.5.8. Create a new captive theme
In ON Captive -> Captive themes we will be able to create and modify different themes that will affect to the appearance in the captive portal web.
In the ON Captive menu, click on the Captive themes tab and there you can create and modify different themes that will affect to the appearance of the Captive Portal web.
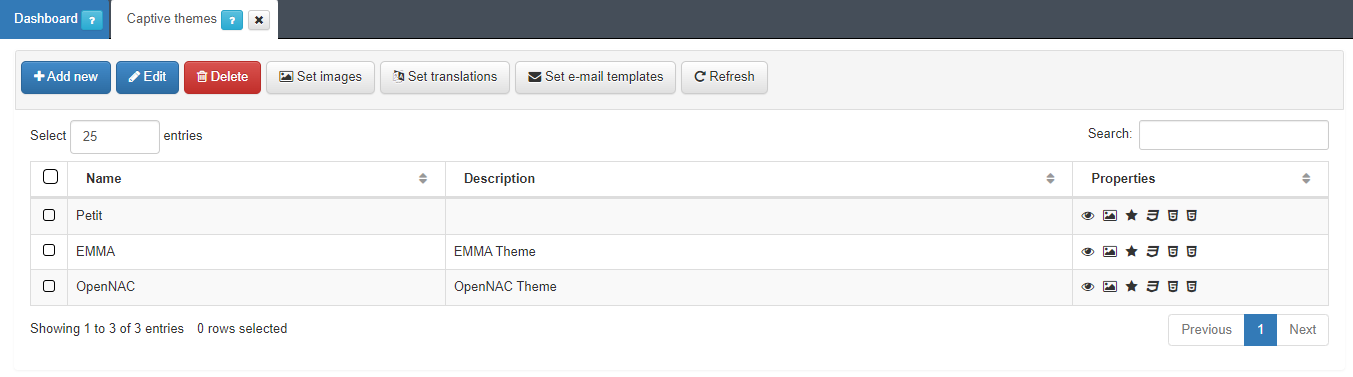
To create a new Captive theme, click on the Add new button, a pop up window will appear and you’ll be able to modify multiple parameters.
By default, the window displays the configurations related to the General tab:
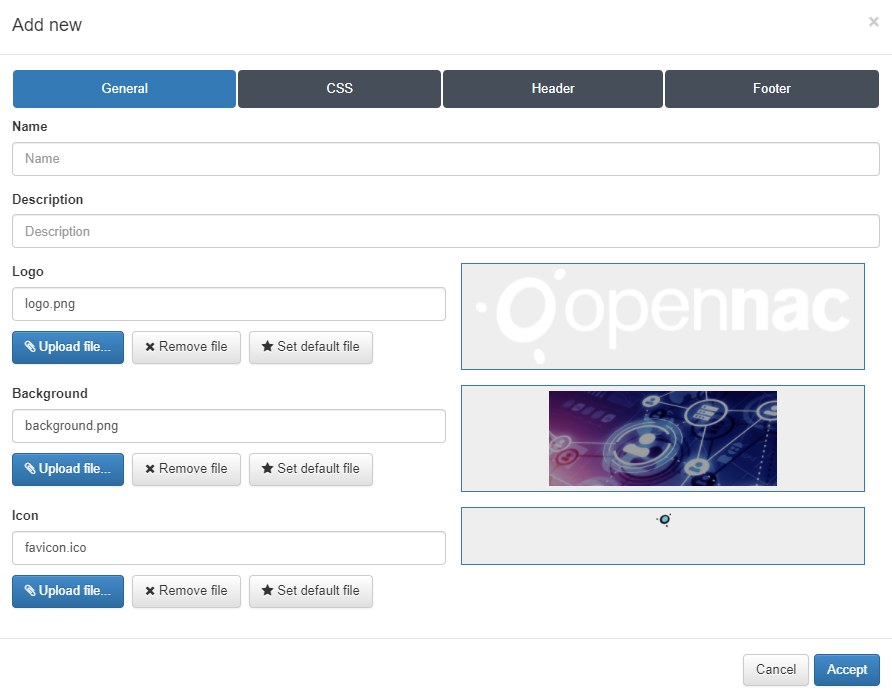
Name: Enter with the name of this Captive theme;
Description: Type a meaningful description for this theme;
Logo: This field defines what .png image will be used as the logo for this new captive theme. By default, the logo.png file is already configured and it corresponds to the default OpenNac logo.
Background: This field defines what .png image will be used as the background for this new captive theme. By default, the background.png file is already configured and it corresponds to the default OpenNac background.
Icon: This field defines what .ico image will be used as the favicon for this new captive theme. By default, the favicon.ico file is already configured and it corresponds to the default OpenNac favicon. The favicon is displayed on the user’s browser address bar, just before the URL.
In the case of the customer wants to use its own logo, which meets the visual identity of the organization, there are three buttons for each field that allow change the images:
Upload file: Permit pick the desired logo image and upload it this Captive logo. The preview of the image will be displayed within the square of the right side of the field.
Remove file: Useful if you want to remove this element.
Set default file: Defines the chosen file as default for the creation of new themes.
We will custom it with the following images:
In the second tab, CSS, we can insert a CSS code to modify the Captive web portal as we desire.
In the Header tab we will be able to insert a custom HTML code for the header of the Captive theme.
In the Footer tab we will be able to insert a custom HTML code for the footer of the Captive theme.
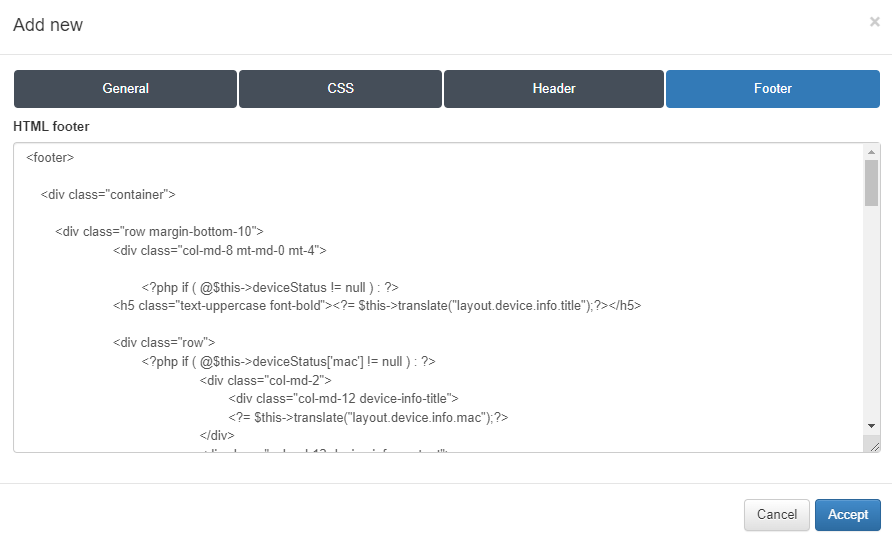
To finish the creation of the new Captive domain, which will be used on the next steps, click on the button Accept.
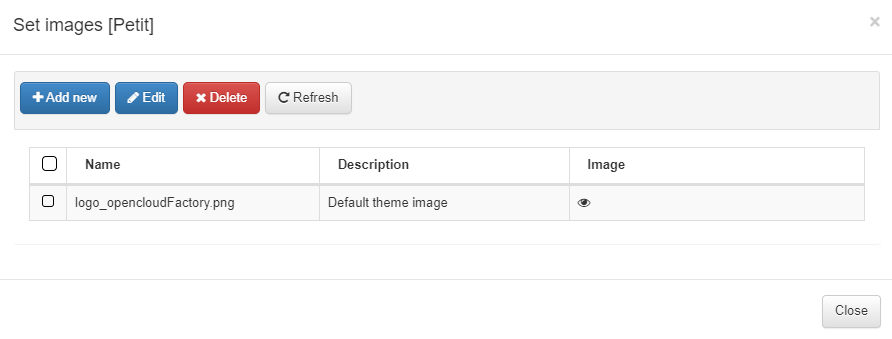
To upload the images that we want to use when we configure a theme, we can select an already created theme, and click the Set images button.
Once the pop up window appears, we will see all the images that have already been uploaded, we will be able to edit the existing images and see a preview by clicking on the eye icon.
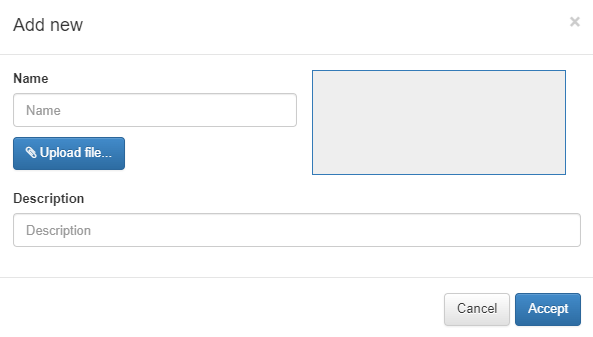
To upload a new image, click on the Add new button, a new dialogue will appear. Here we can set a name and a description and select the image that we want to upload.
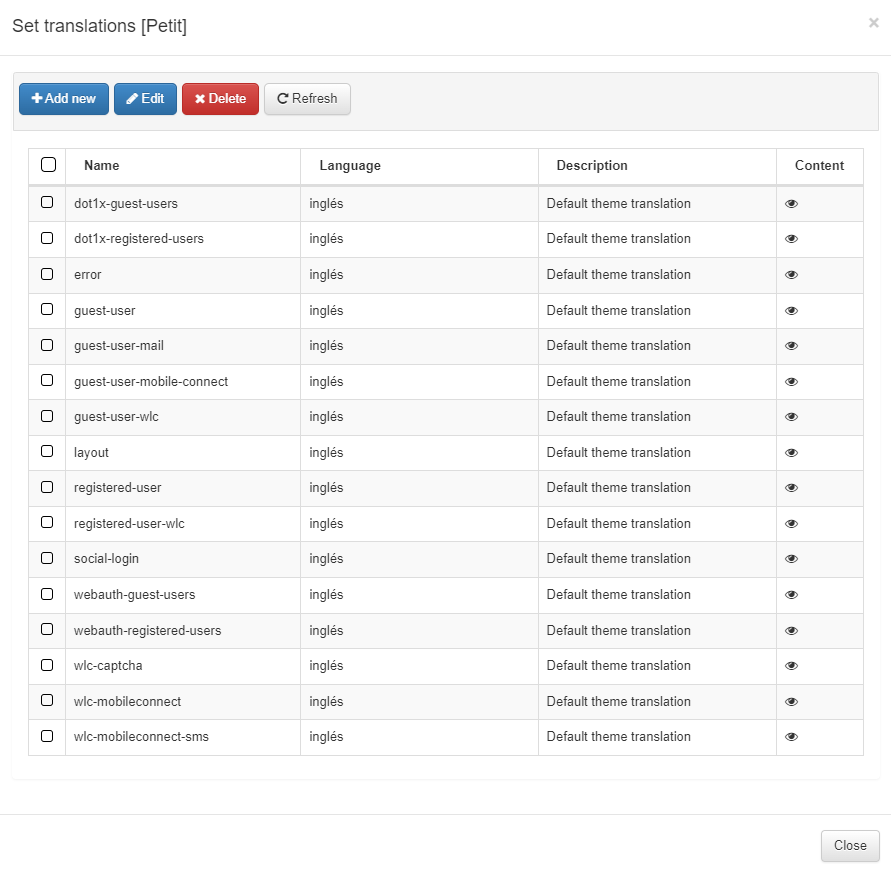
We can also set different translations or adapt the actual text from the different captive portal workflows and it’s sections. To modify it, we can select an already created theme, and click the Set translations button.
Once the pop up window appears, we will see all the translations for the different modules that are already done. We can edit the existing ones and see a preview of their content by clicking on the eye icon.
To translate a new section, click on the Add new button and a new window will appear. In the name filed, we can select all the different modules that can be translated. Once we select the module that we want to translate, the content of the module, variables and the associated text will appear on the content field, so we will have to translate the text associated to the variables to the desired language. The next step will be to select the language to which we are going to translate the selected module. Also, we will be able to add a description.
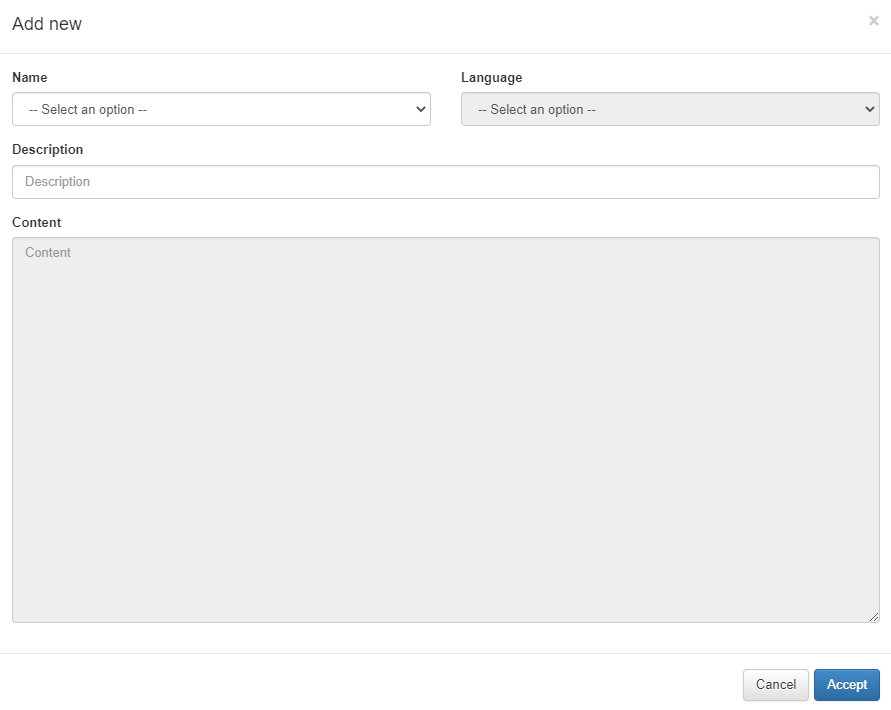
We can also set different e-mail templates or adapt the actual ones by configuring the HTML code that is send via e-mail from the different captive portal workflows. To modify it, we can select an already created theme, and click the Set e-mail templates button.
Once the pop up window appears, we will see all the already templates for the different workflows, we will be able to edit the existing ones and see a preview of the content by clicking on the eye icon.
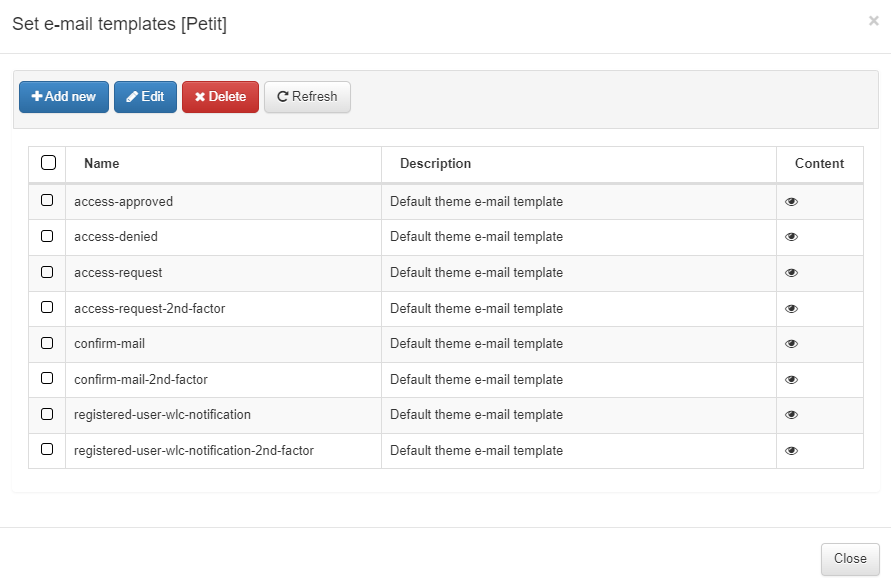
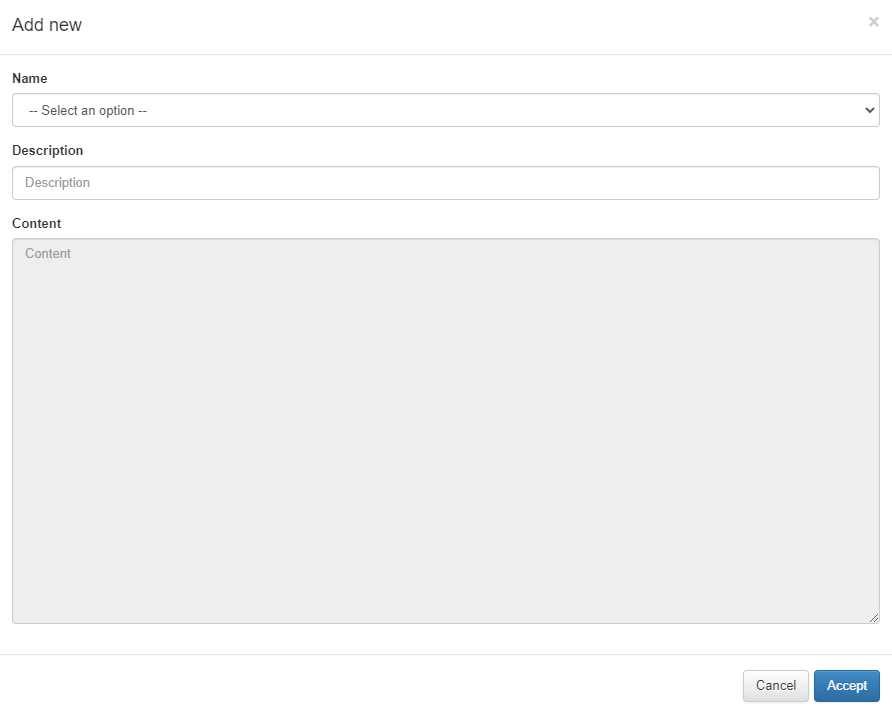
To configure a new email template, click on the Add new button, a new dialogue will appear. In the name filed, we can select all the different modules that can be configured. Once we select the module that we want to modify, the content of the module, variables and the associated text will appear on the content field in HTML format so we can modify it. Also, we will be able to add a description.
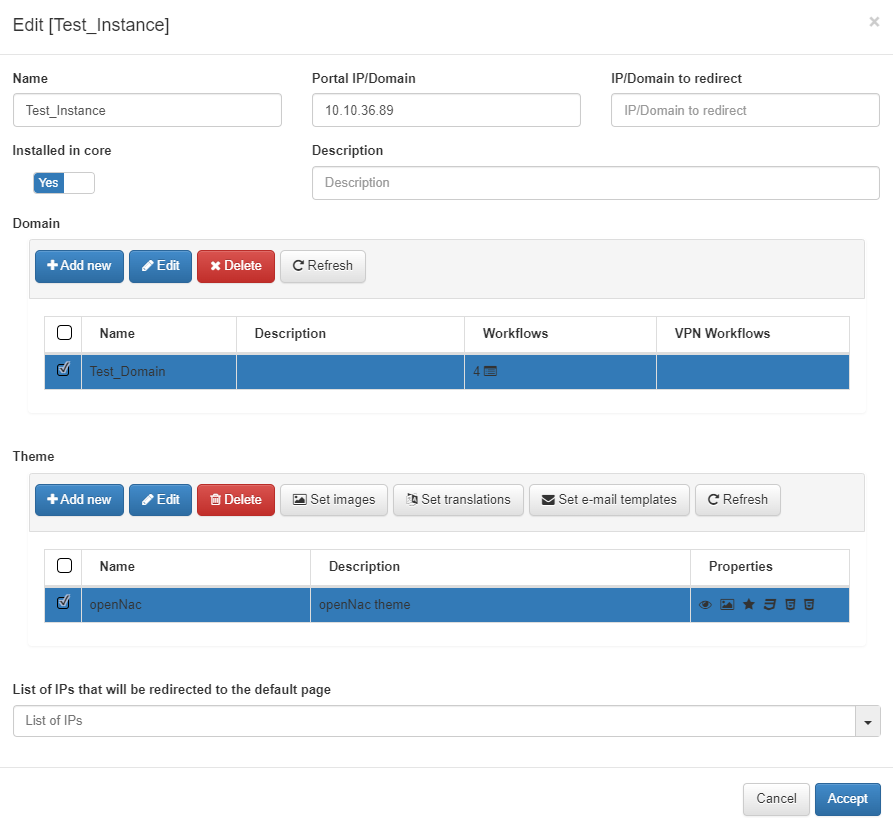
To select the created theme to an instance, we need to go to the instance created in ON Captive -> Captive instances and select the theme:
Then, if we go to the captive portal again, we will see the new theme applied.