3.1.10.2.20. openPorts
The openPorts plugin provides the ability to scan and discover open ports on devices requesting network access by authenticating through Opennac, helping the profiling process detect which UDP and TCP ports are open.
Whenever a device’s authentication matches with a policy rule where this plugin is enabled, an NMAP process is started and it will scan the open ports of that user device, according to the globally defined set of ports in plugin configuration or defined in the custom parameters in the rule itself, which will take precedence over the global configuration. At the end of the scan, the plugin will automatically create user device tags for the defined set of ports and apply those tags to the device being authenticated..
Later, these tags can be added to a policy rule. The policy rule should come before the rule activating the plugin. The purpose of the policy rule is to grant network access to devices with the discovered set of open ports.
The following fields must be configured to set up the plugin:
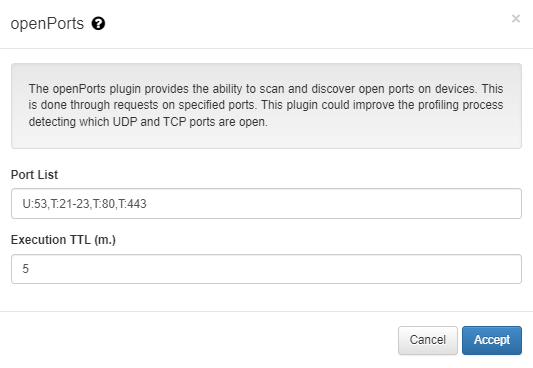
Port List: The ports and their respective protocols that will be targeted by the plugin are defined. In the example shown in the image above, the protocol type is represented by a letter, U for UDP protocol and T for TCP followed by “:” (colon) and port number. Each protocol:port pair must be separated from the other by commas, without any spaces.
Execution TTL (m.): This field must be filled with the interval, in minutes, between periodic port scans that will be performed by the plugin. In this example, the value of 5 is five minutes. For testing or debugging purposes, 5 minutes do not pose any problem, however, in production environment with large number of devices being authenticated this is not indicated. The recommendation is that this value in minutes corresponds to a certain amount of hours, for example, 600 to 10 hours between scans.
We can see an example of the tags generated by the openPorts plugin, when a device passes a policy that executes the plugin.
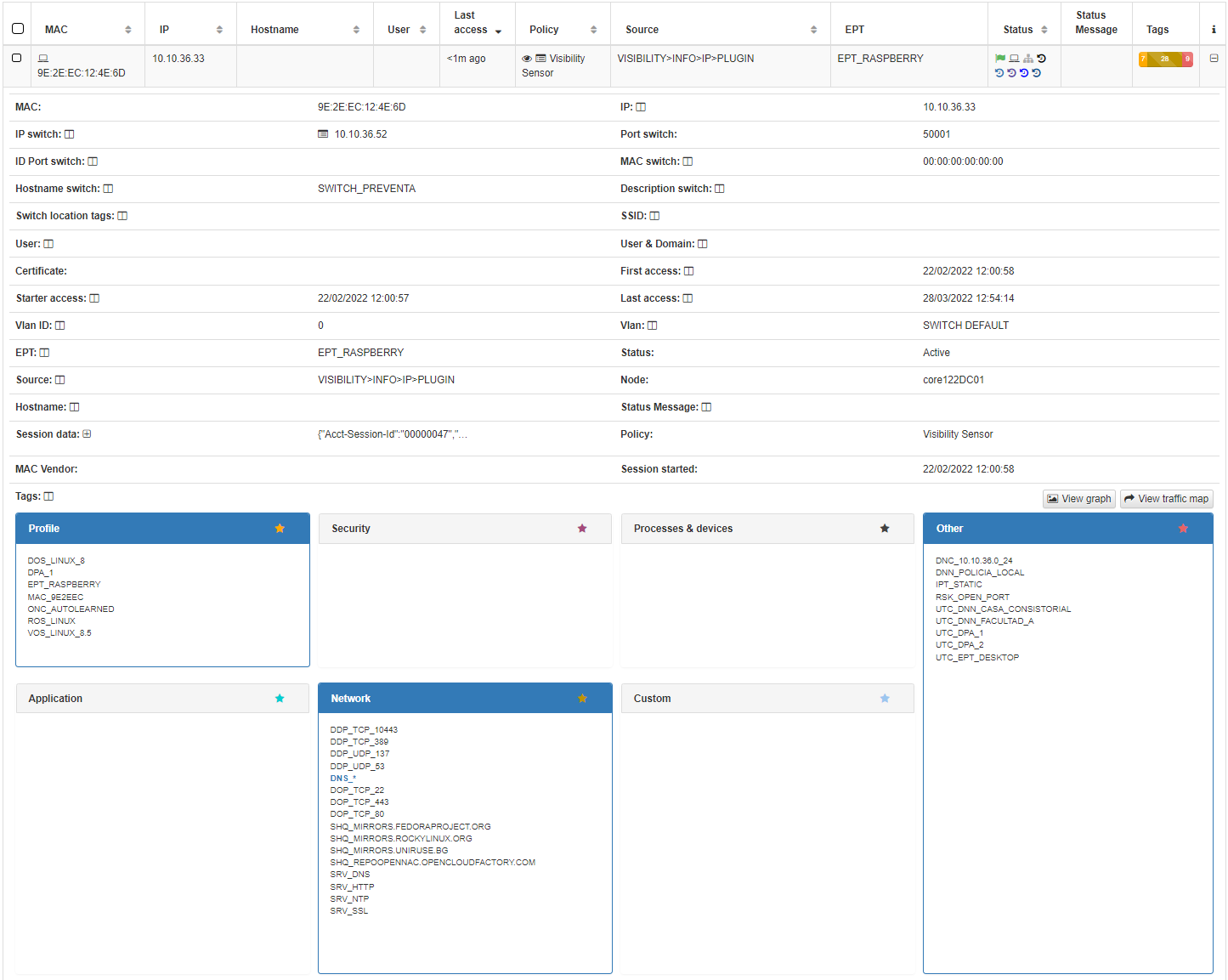
The plugin detected the TCP ports 22, 80 and 443 and created the corresponding tags with the prefix DOP.
DOP_TCP_22
DOP_TCP_443
DOP_TCP_80