2.8.6. Agent Payload
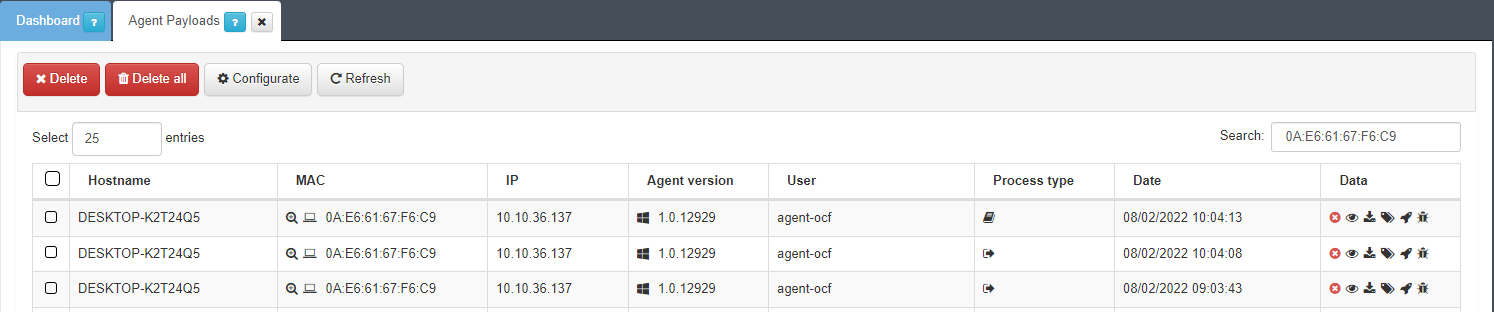
After the Agent is installed and communicating with the OpenNAC Enterprise Core, the Agent will send messages to the ON Core. These messages are called payloads and you can see them in the Agent payload section:
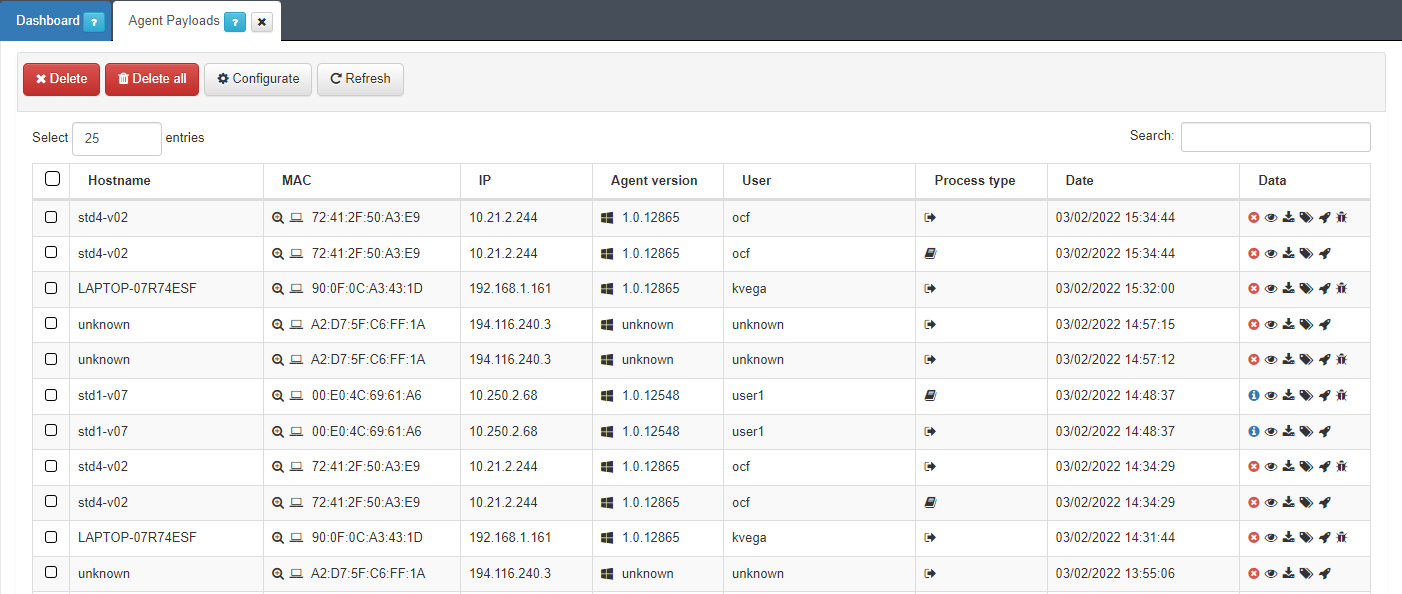
We can find the Hostname, the MAC, the IP, the User, and the Date of every corresponding payload. Apart from that, we can find the following columns:
2.8.6.1. Agent Versions
The version of the agent is represented in this column as an icon of the operating system where the agent is running.
2.8.6.2. Process type
There are different Process types for agent payloads and they are represented by icons. The following table indicates their meaning:
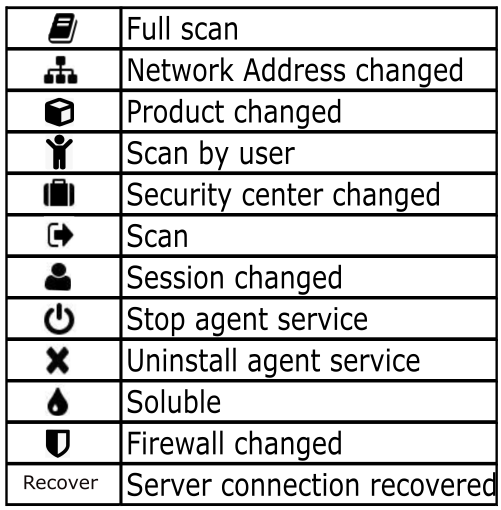
2.8.6.3. Data (Payload types)
There are different Payload types and they are also represented by icons. The following table indicate their meaning:
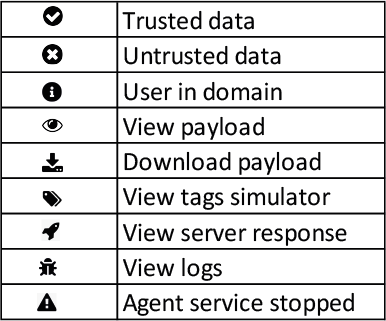
The first icon Trusted data indicates the data received from an authenticated user, a user in the domain. The Untrusted data displays Untrusted data. And the User in domain icon displays the user in domain.
2.8.6.4. View payloads
Administrators can see the content of the payload by clicking on the eye icon.
The payloads are organized in different sections to facilitate their readability.
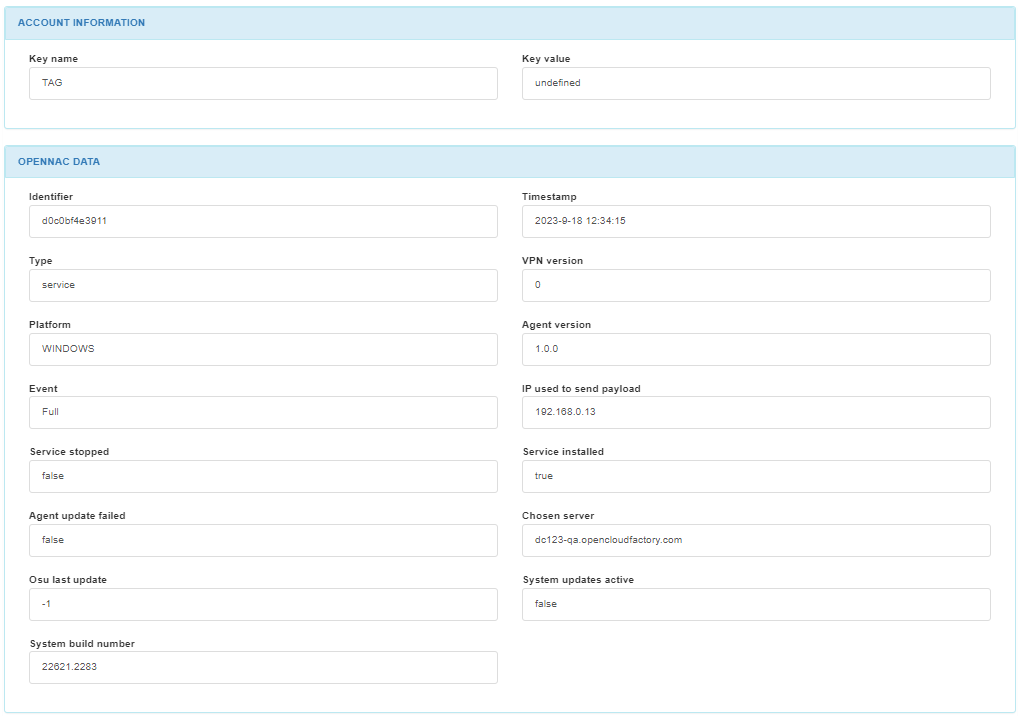
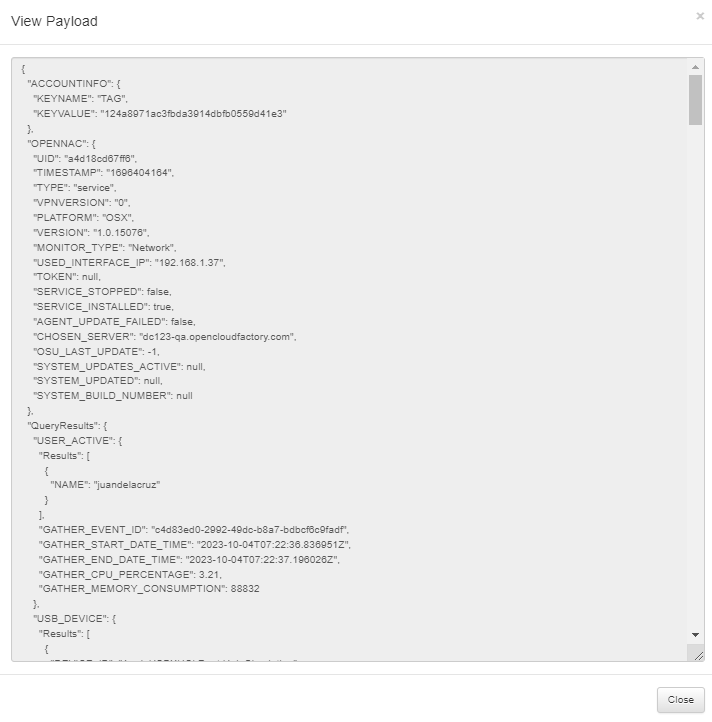
In the ACCOUNT INFORMATION section, we can find the key name and the key value.
In the OPENNAC DATA section we can find the identifier, the timestamp, the data type, the VPN version, the platform, the agent version, the event, the IP used to send the payload, if the service is stopped and finally if the service is installed.
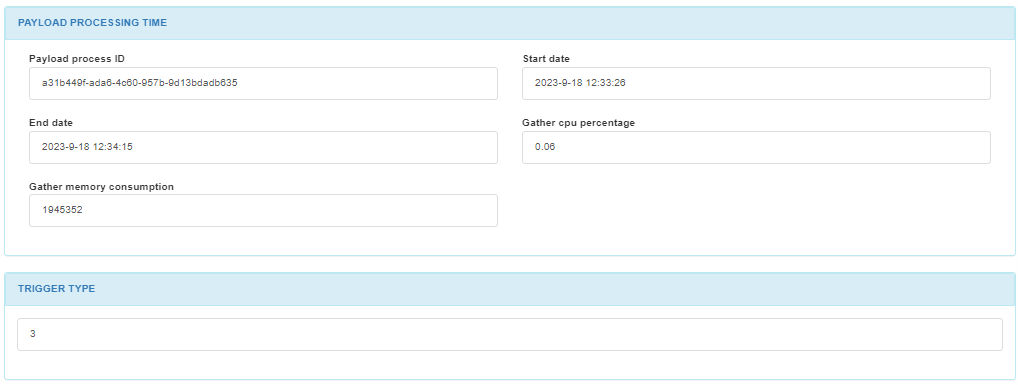
In the PAYLOAD PROCESSING TIME section, we can find the payloads process ID and the start and end time of the payload.
In the TRIGGER TYPE section, we can find the number corresponding to the trigger type.
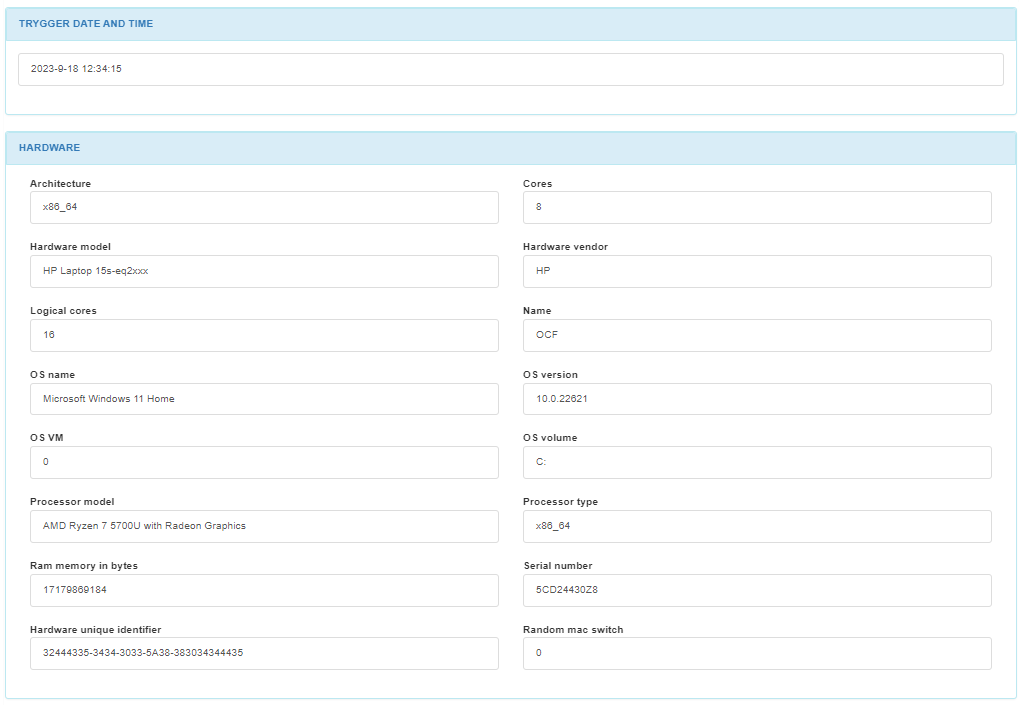
In the TRIGGER DATE AND TIME section, we can find the date and time the trigger is finished.
In the HARDWARE section, we can find the system architecture, the name of the system where the agent is, the OS name, the OS version, the OS VM, the OS volume, the serial number, the hardware unique identifier, and if the device is using random MAC. If the Random mac switch is set to true, the HDT_MACRANDOM tag is added to the device.
Note
If the ON Agent is soluble and is not executed as sudo, the machine UUID and OS_VM flags won’t be returned in the Hardware section.
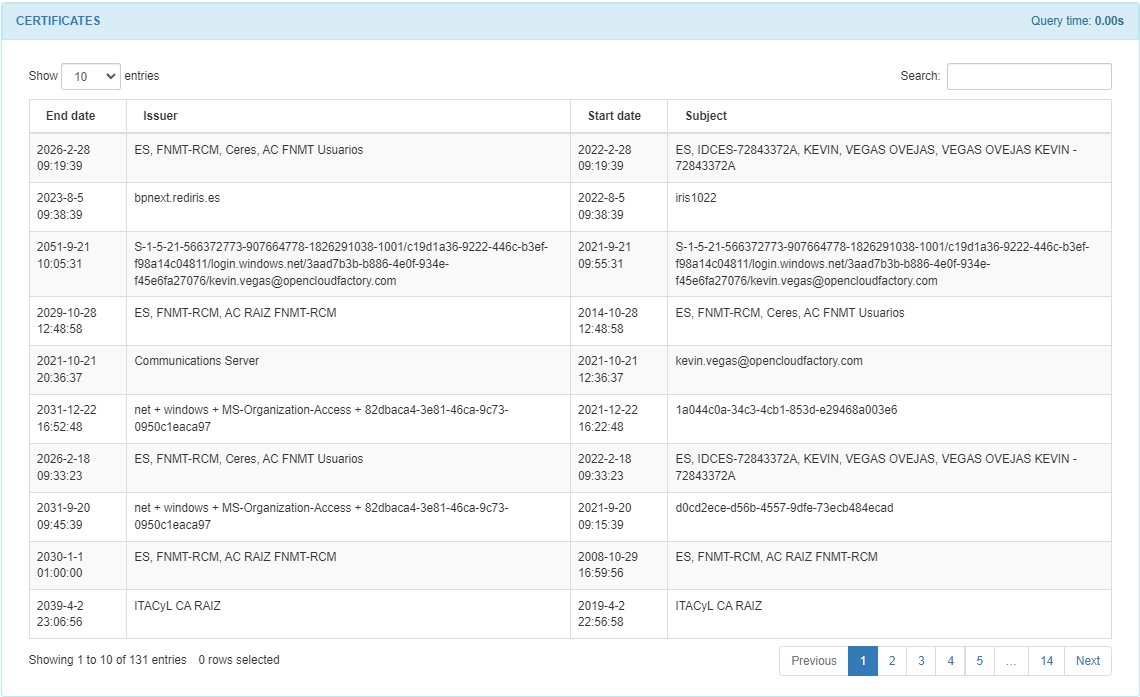
In the CERTIFICATES section, we can find a list of the certificates found on the host. We can find the end date, the issuer, the start date, and the subject from each certificate in the list.
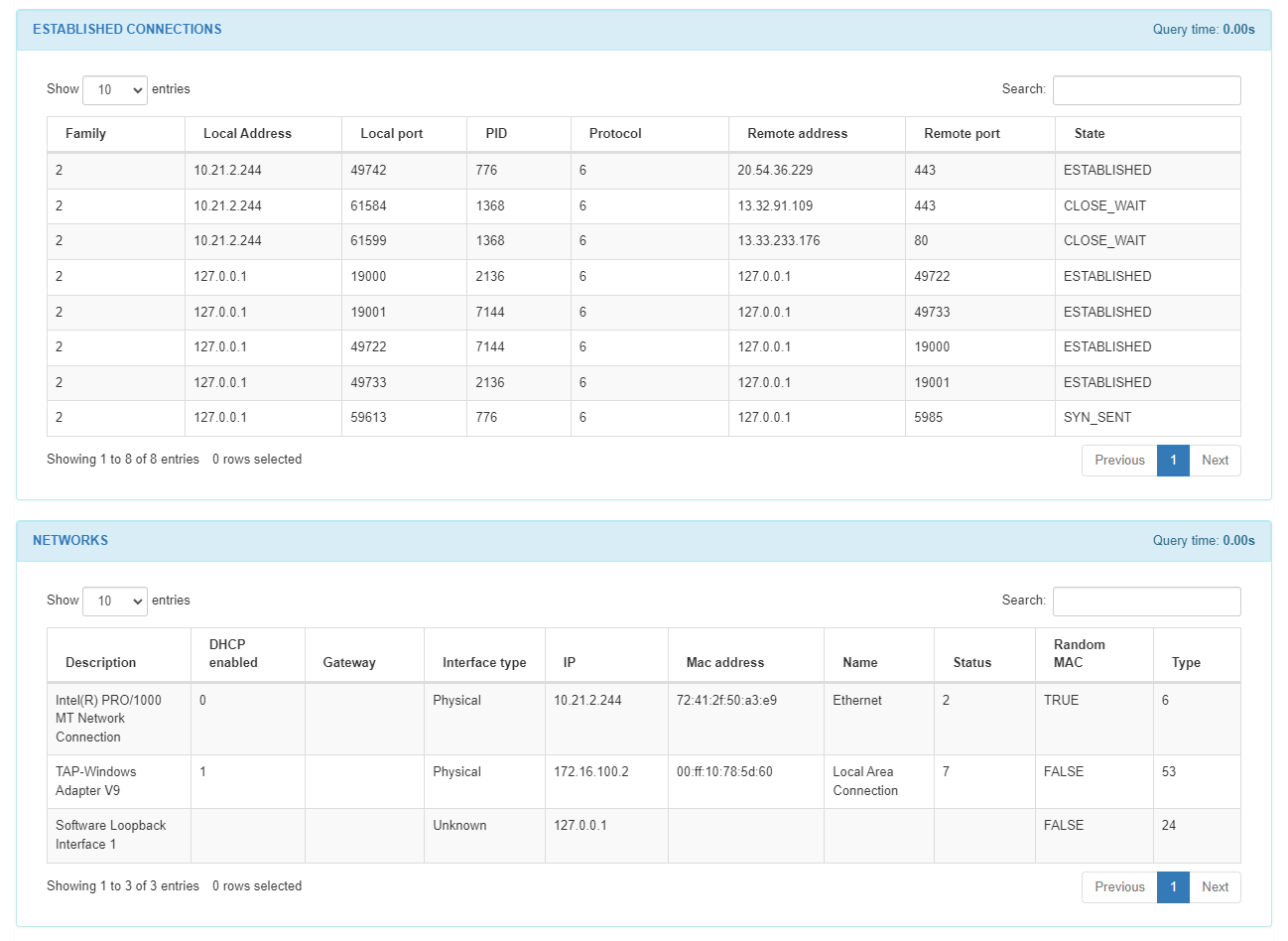
In the ESTABLISHED CONNECTIONS section we can find a list of the host connections: the family number, the local address, the local port, the process ID, the protocol, the remote address, the remote port, and the state from each connection in the list.
In the NETWORKS section, we can find a list of the interfaces of the host machine. We can find the description, if the DHCP is enabled, the default gateway, the interface type, the IP of the interface, the MAC address, the name, the status, if it has a random MAC, and the type from each interface in the list.
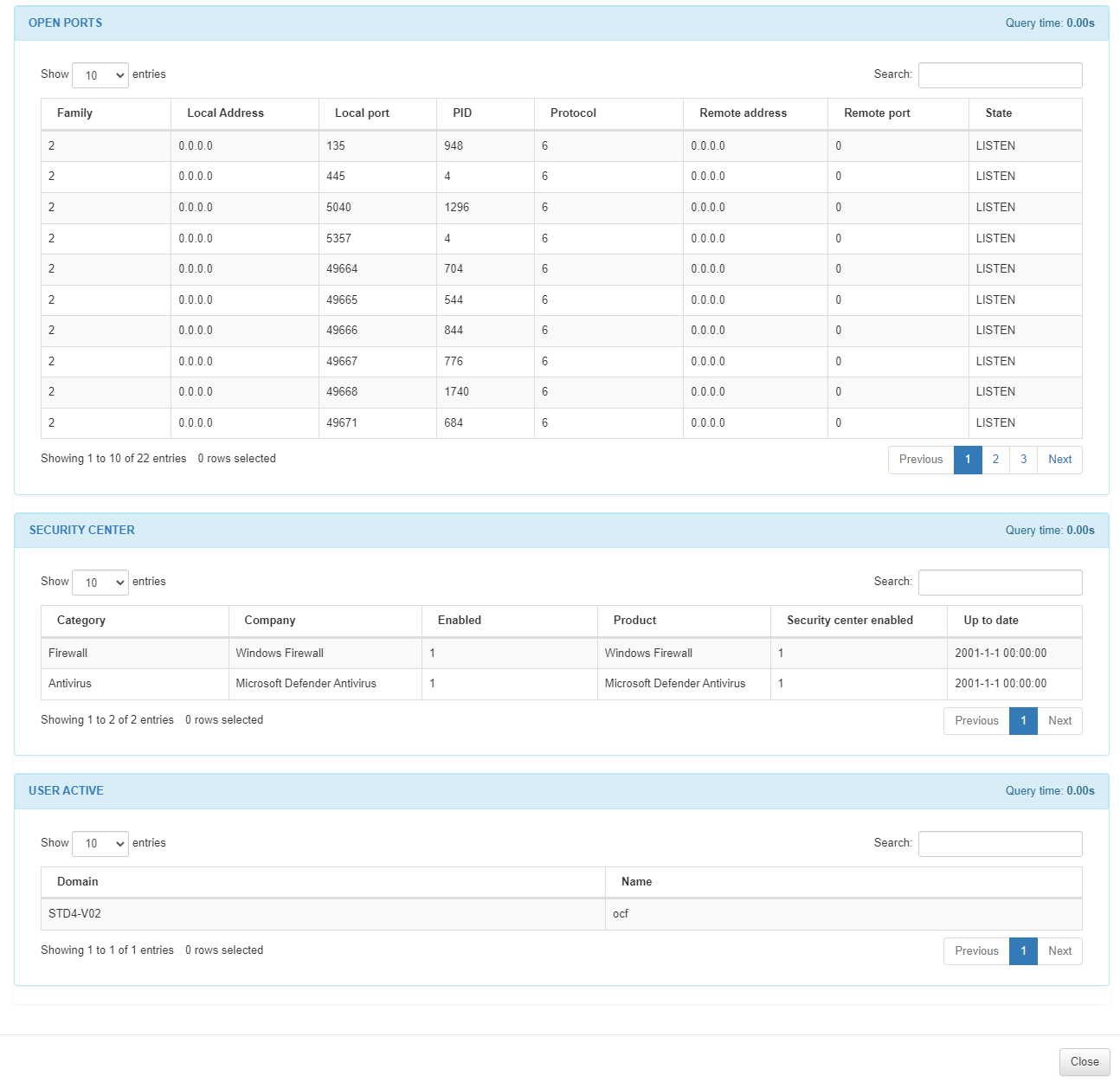
In the OPEN PORTS section we can find a list of all the open ports of the host. We can find the family number, the local address, the local port, the process ID, the protocol, the remote address, the remote port and the state from each open port in the list.
In the SECURITY CENTER section, we can see a list of the security instances running on the host, like firewalls and antivirus. We can find the category, the company, if it is enabled, the product, if the security center is enabled, and if it is up to date from each security center in the list.
In the USER ACTIVE section, we can see a list of the active users running on the host. We can find the domain and the name of the active user.When an OSQuery fails, this field will display the following error message: “A problem occurred when obtaining information about this entity”.
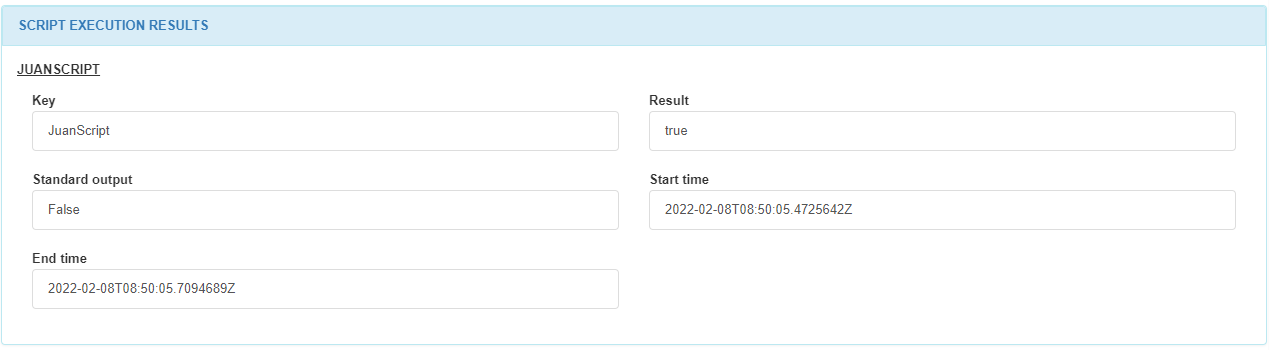
In the SCRIPT EXECUTION RESULTS section, we can find the name of the Script executing in the host, the key of the script, the result, the standard output and the start time and end type. These scripts are configured on ON Agent -> Agent scripts. You can find more information in ON Agent -> Agent scripts.
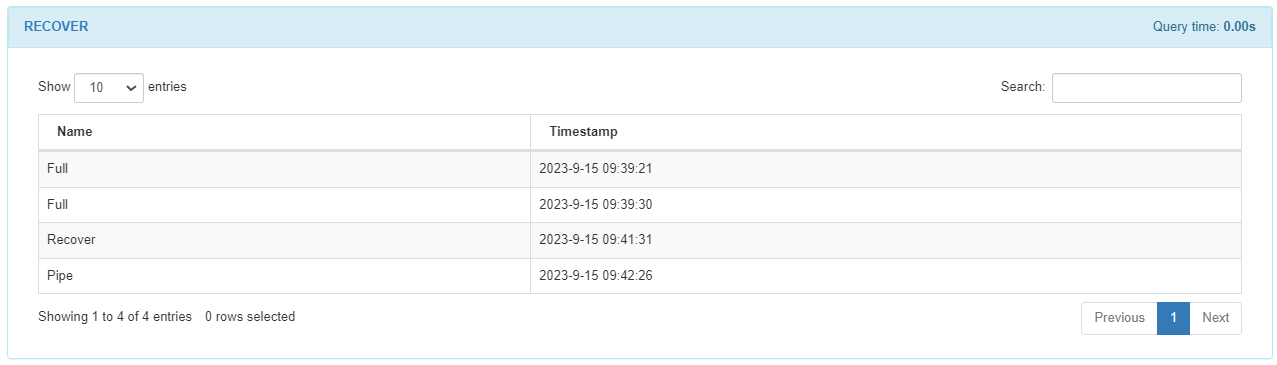
In the RECOVER module, you will see the recovered payloads displayed with their timestamp. These payloads will be sent in the event of a loss of connectivity with the server.
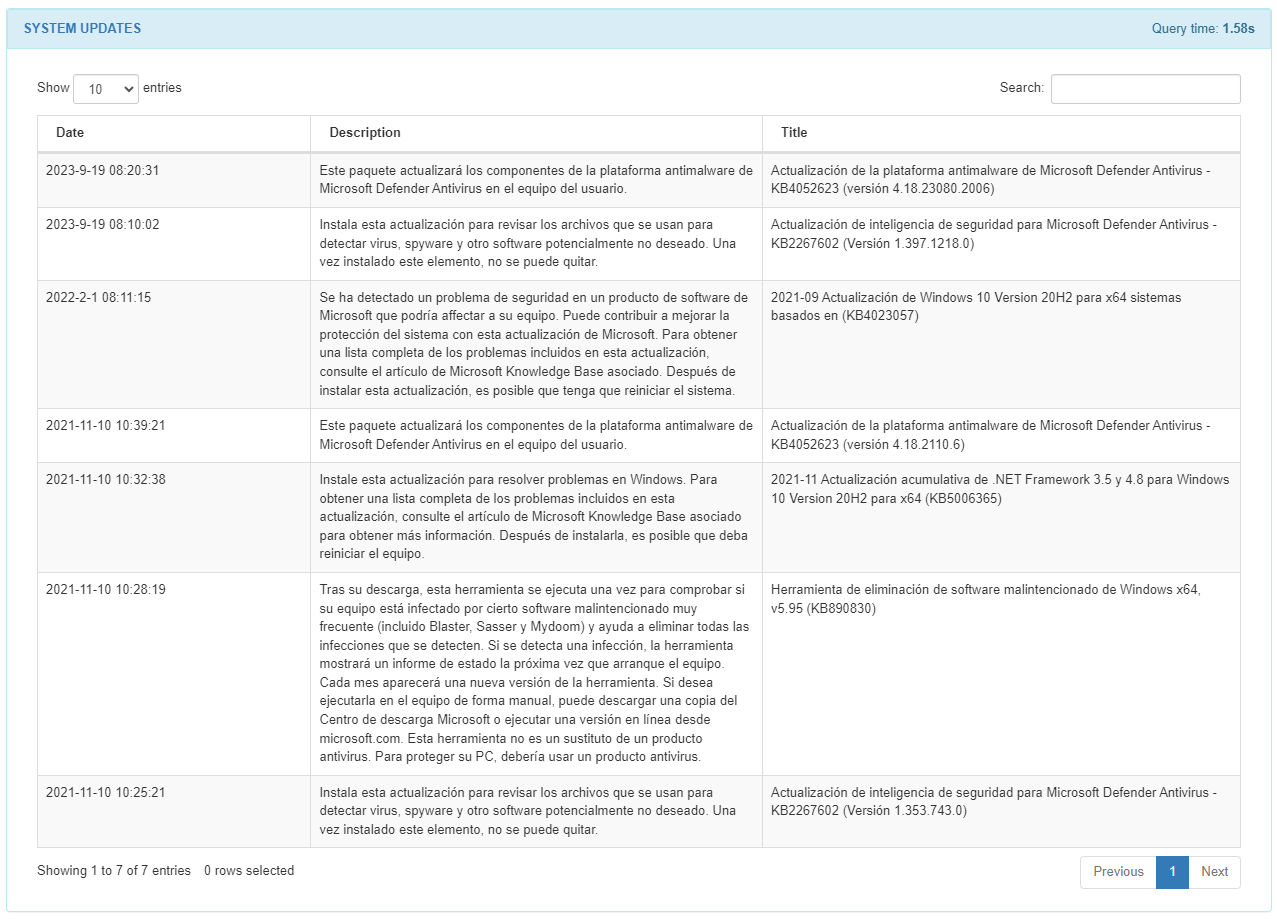
The SYSTEM UPDATES section displays installed updates with a description and date of the event.
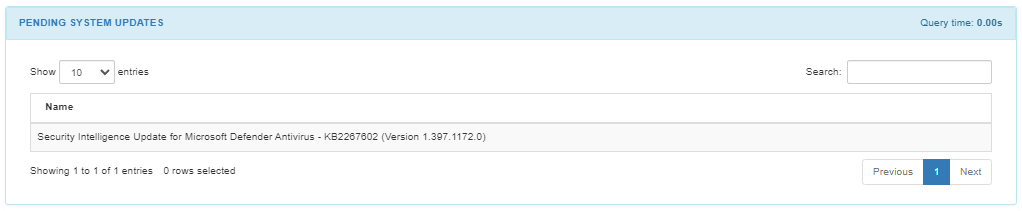
The PENDING SYSTEM UPDATES section displays pending uninstalled updates awaiting execution. For example, Security Intelligence Update for Microsoft Defender Antivirus.
Note
When the Windows Update is disabled by the user, SYSTEM_UPDATES_ACTIVE will return false, while SYSTEM_UPDATED and PENDING_SYSTEM_UPDATES fields will be set as “”null” making it impossible to accurately determine the machine’s update status.
Regarding System Update tags, understand three possible scenarios:
Disabled Updates
Scenario: When System Updates are disabled, the system enters a state where updates are not actively managed or applied.
Tags: The ISS_SYSTEM_UPDATES_DISABLED tag will be added to indicate that System Updates are disabled.
Enabled Updates & Not Updated
Scenario: In cases where System Updates are enabled, but some updates are pending installation or the system is not yet updated.
Tags: The ISS_SYSTEM_UPDATES_ENABLED tag indicates that System Updates are enabled. Additionally, the ISS_WINDOWS_PENDING_UPDATES tag is added, and UIP_KBxx tags are included for each pending update. Note that drivers may be present in the update payload but are usually ignored for tagging purposes.
Enabled Updates & Updated
Scenario: When System Updates are enabled and the system is up-to-date with all available updates.
Tags: The ISS_SYSTEM_UPDATES_ENABLED tag confirms that System Updates are active. Additionally, the ISS_WINDOWS_UPDATED tag is added to indicate that the system has been successfully updated with all available updates.
By clicking on “View Payload” at the upper-right corner of the Agent Payload window, it will display the following view:
The Download payload icon allows you to download the payload received.
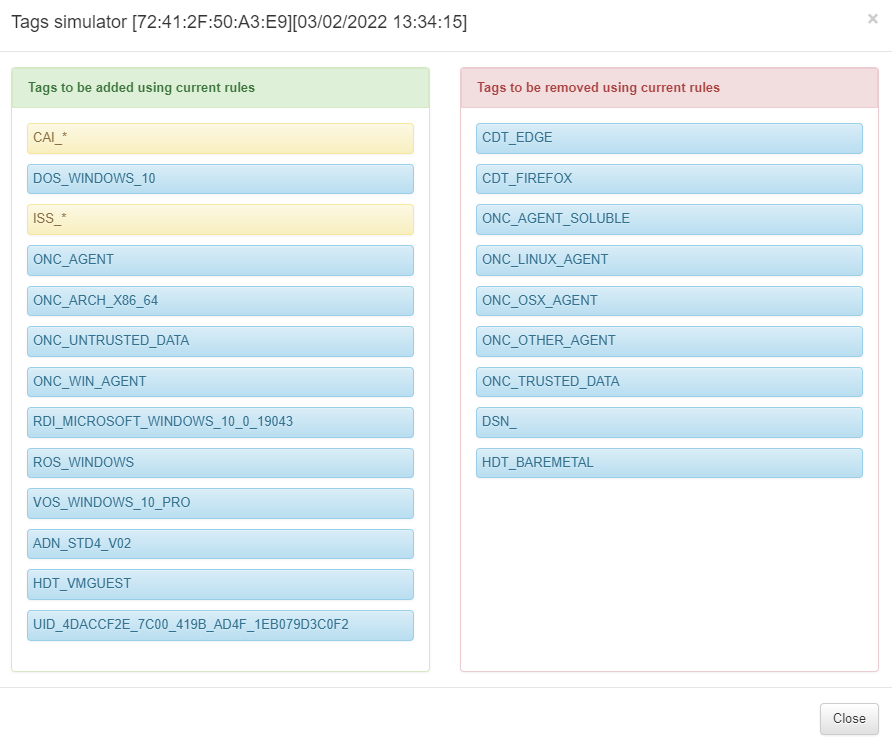
You can perform a tag simulation from the View tags simulator icon.
In View server response icon, we can see the Agent server response:
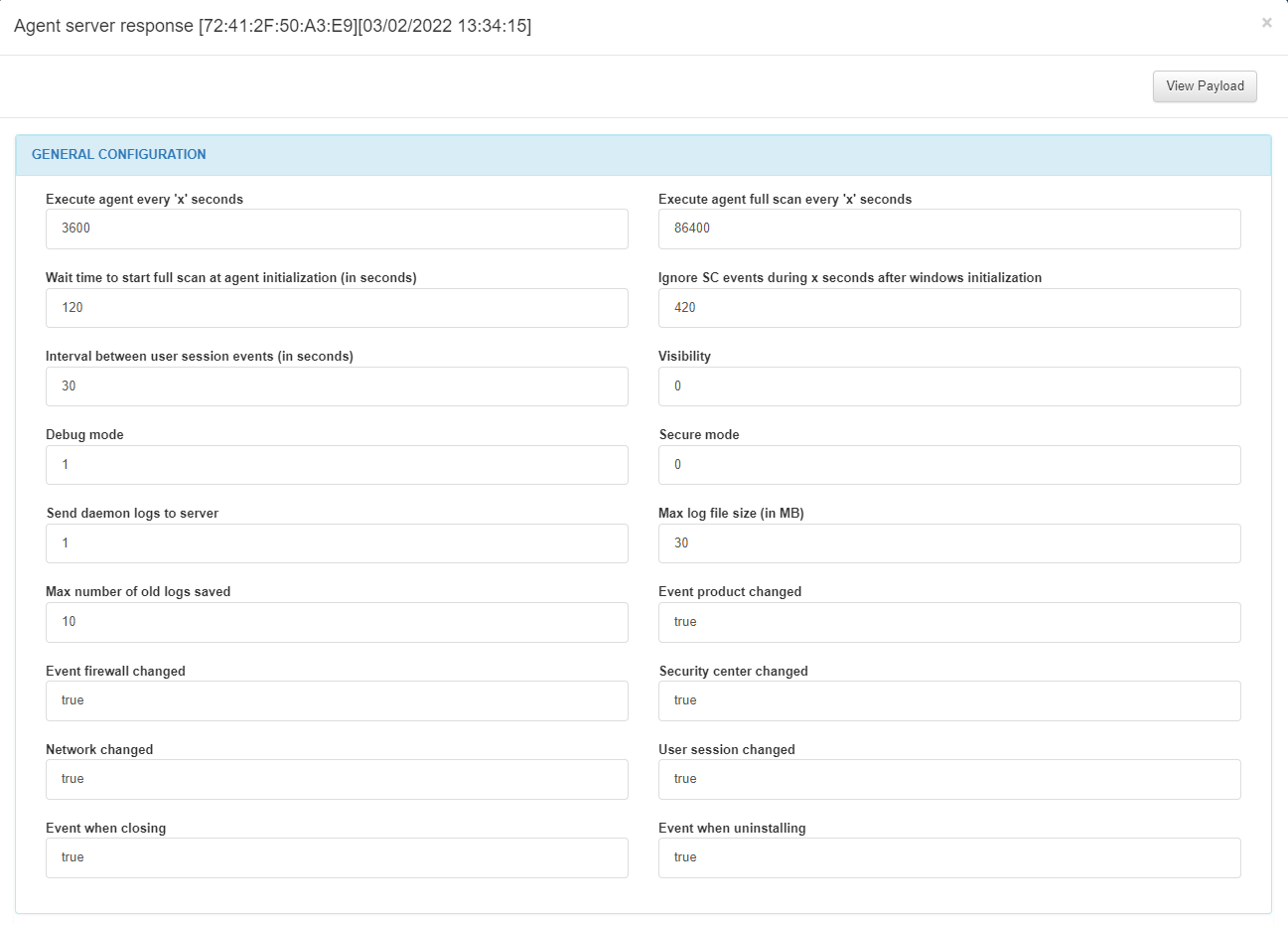
In the GENERAL CONFIGURATION section, we can find the periodicity of the script execution in seconds, the periodicity of the full scan in seconds, the waiting time before a script execution before initialization, the waiting time ignoring sc events before windows initialization, the interval between user session events, the visibility, the debug mode, the secure mode, the number of logs sent to the server, the max log file size in MB, the max number of old logs saved, if the event product changed, if the event firewall changed, if the security center changed, if the network changed, if the user session changed, if there is an event when closing and if there is an event when uninstalling.
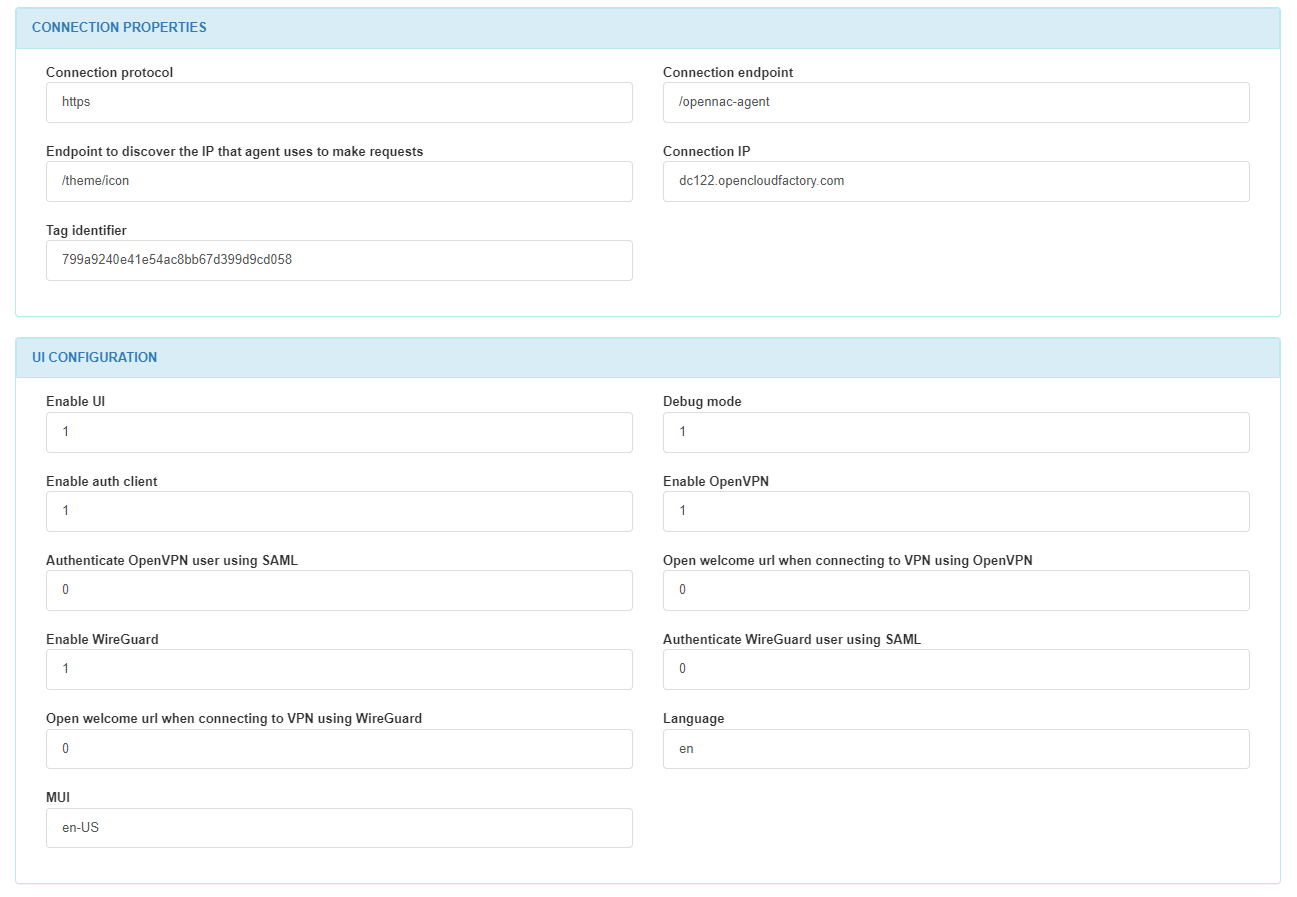
In the CONNECTION PROPERTIES section, we can find the connection protocol, the connection endpoint, the endpoint to discover the IP that the agent uses to make requests, the connection IP or domain, and the taf identifier.
In the UI CONFIGURATION section, we can find if the UI is enabled, if the debug mode is enabled, if the client authentication is enabled, if OpenVPN is enabled, if the SAML for OpenVPN is enabled, if an URL is going to be open when connecting using OpenVPN, if Wireguard is enabled, if the SAML for Wireguard is enabled, if an url is going to be open when connecting using Wireguard, the UI language, and MUI.
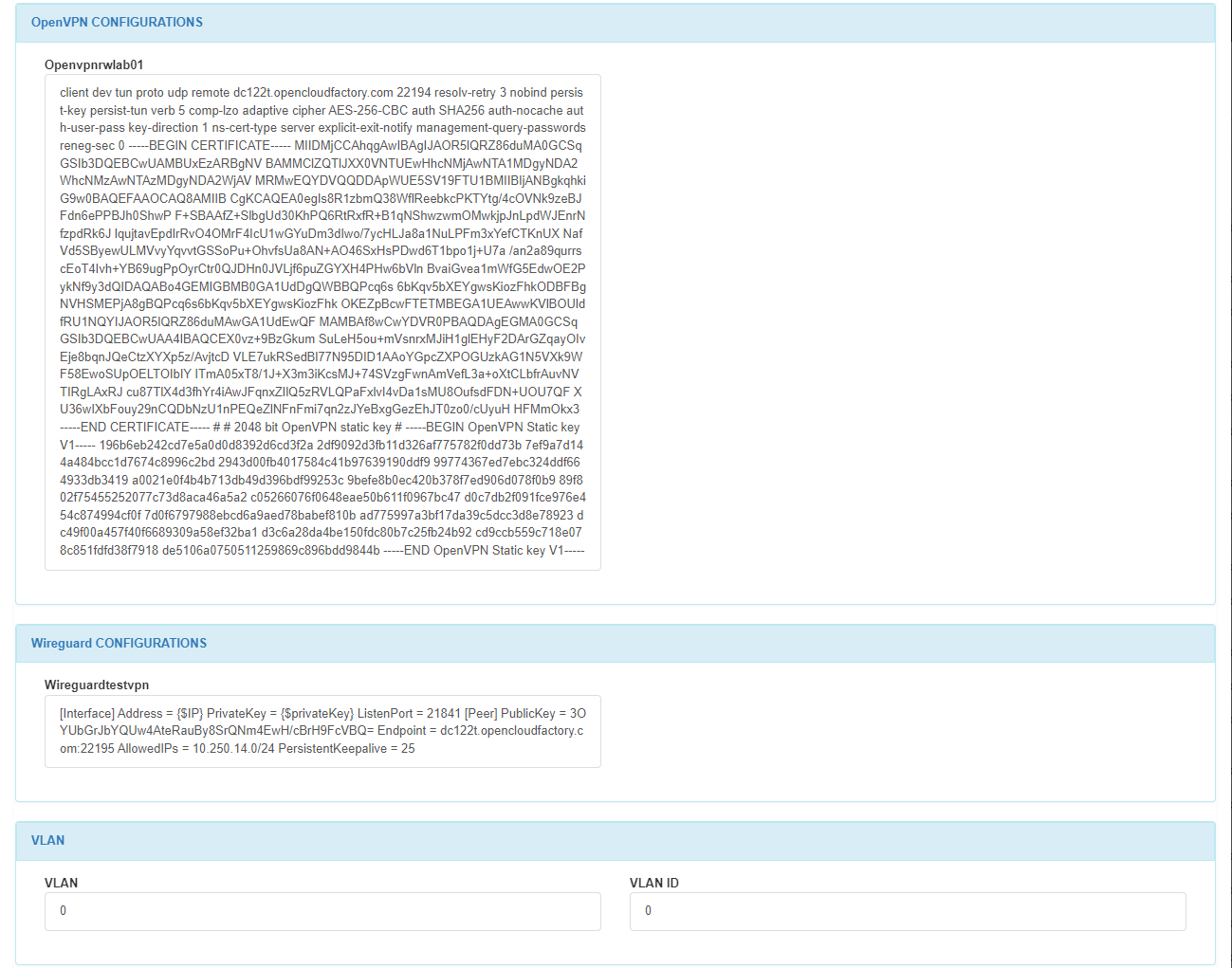
In the OpenVPN CONFIGURATIONS section, we can find the configuration of the OpenVPN server.
In the Wireguard CONFIGURATIONS section, we can find the configuration of the Wireguard server.
In the VLAN section, we can find the VLAN name and the VLAN ID.
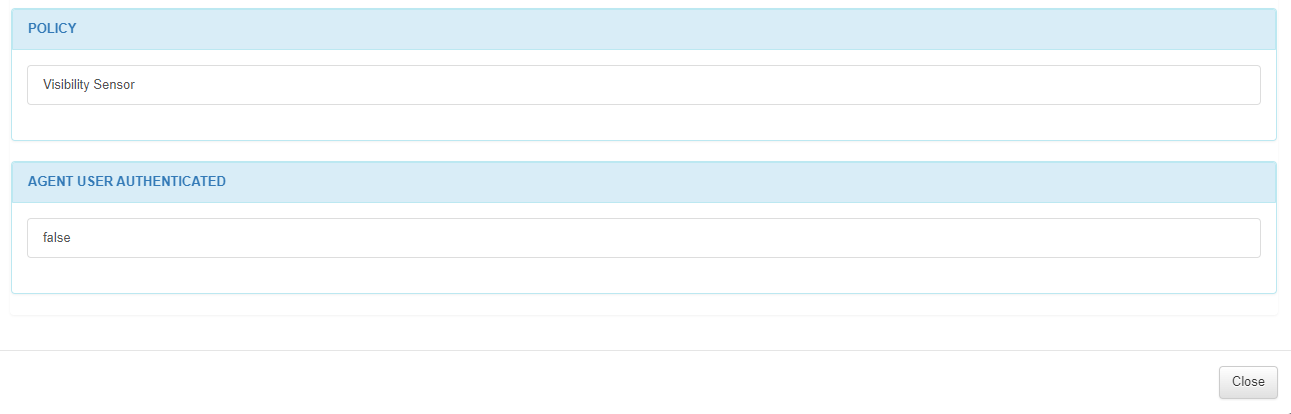
In the POLICY section, we can find the policy where the host matched.
In the AGENT USER AUTHENTICATED section, we can see if the user has been authenticated.
In View logs icon, we can see the agent logs.
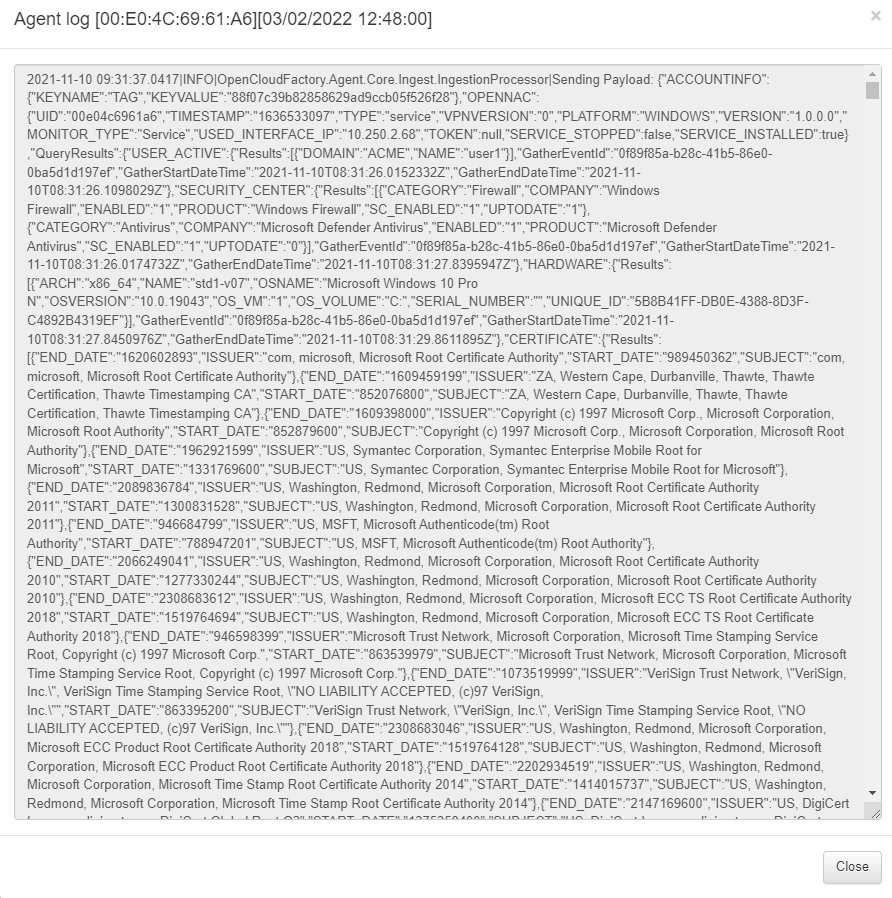
When inserting text in the Search box, it will search for that piece of text inside the JSON file. So we can use it to filter by software, hostname, IPs, processes and anything else that could reside into an agent’s JASON.
The Agent service stopped icon, indicates that the agent service has been stopped in that device.
2.8.6.6. The JSON sent from OpenNAC Enterprise to the Agent
{
$AGENT_CONFIG,
$AGENT_CONNECTION,
$AGENT_TASKBAR_CONFIG,
$AGENT_QUERY,
$USB_POLICY_CLASS_ALLOWLIST,
$USB_POLICY_CLASS_DENYLIST,
$USB_POLICY_PRODUCT_ALLOWLIST,
$USB_POLICY_PRODUCT_DENYLIST,
$AGENT_HASH_QUERY,
$AGENT_VPN_CONFIG,
$vlan,
$AGENT_POLICY_NAME,
$AGENT_POLICY_USER_MESSAGE,
$AGENT_DEVICE_TAGS
}
AGENT_CONFIG
Type: object
Description: Agent configuration settings.
Parameters:
- INTERVAL: The time in seconds between each agent scan on the device.
type: string
- FULL_INTERVAL: The time in seconds between each agent full scan on the device.
type: string
- START_MODE_INTERVAL: Start mode interval in seconds.
type: string
- IGNORE_SC_STATUS_INTERVAL: Ignore security center status interval in seconds.
type: string
- INTERVAL_BETWEEN_USER_SESSION_EVENTS: The interval between user session events in seconds.
type: string
- DISCOVERY: If discovery is enabled or not.
type: string
- DEBUG: If debugging is enabled or not.
type: string
- SENDLOGSTOSERVER: If send daemon logs to server is enabled or not.
type: string
- MAXLOGSIZE: Maximum log size.
type: string
- MAXCOMPRESSEDLOGS: Maximum compressed logs.
type: string
Example:
"AGENT_CONFIG": {
"INTERVAL": "3600",
"FULL_INTERVAL": "86400",
"START_MODE_INTERVAL": "120",
"IGNORE_SC_STATUS_INTERVAL": "420",
"INTERVAL_BETWEEN_USER_SESSION_EVENTS": "30",
"DISCOVERY": "0",
"DEBUG": "1",
"SENDLOGSTOSERVER": "1",
"MAXLOGSIZE": "30",
"MAXCOMPRESSEDLOGS": "10"
}
AGENT_CONNECTION
Type: object
Description: Agent connection settings.
Parameters:
- PROTOCOL: The protocol used for agent connection.
type: string
- ACTION: The action path used for agent connection.
type: string
- PING_ACTION: The ping action path used for agent connection.
type: string
Example:
"AGENT_CONNECTION": {
"PROTOCOL": "https",
"ACTION": "/opennac-agent",
"PING_ACTION": "/admin/favicon.ico"
}
AGENT_TASKBAR_CONFIG
Type: object
Description: Agent task bar settings.
Parameters:
- ENABLED: If task bar is enabled or not.
type: string
- DEBUG: If debugging is enabled or not.
type: string
- PLUGIN_VPN: Plugin VPN.
type: string
- LANGUAGE: The language used for agent task bar.
type: string
- MUI: Multilingual user interface languages.
type: string
Example:
"AGENT_TASKBAR_CONFIG": {
"ENABLED": "1",
"DEBUG": "1",
"PLUGIN_VPN": "1",
"LANGUAGE": "en",
"MUI": "en-US"
}
AGENT_QUERY
Type: array
Description: Agent query settings.
Parameters:
type: object
Parameters:
- TYPE: Type of agent query.
type: string
- KEY: Key for agent query.
type: string
- IMPERSONATE: Impersonate or not.
type: string
- SCRIPT: The script code to be executed.
type: string
Example:
"AGENT_QUERY": [
{
"TYPE":"CSCRIPT",
"KEY":"MCAFEE_DAT",
"IMPERSONATE":"0",
"SCRIPT":"Dim windowsShell,regValue, currentDate, maxDays, regKey#maxDays = 14#'regKey = "HKEY_LOCAL_MACHINE\SOFTWARE\McAfee\AVEngine\AVDatVersion\"#regKey = "HKEY_LOCAL_MACHINE\SOFTWARE\McAfee\MfeAV\Install Date\"#On Error Resume Next#Set windowsShell = CreateObject("WScript.Shell")#regValue = windowsShell.RegRead(regKey)#If err.number <> 0 then# 'Error reading regkey# Wscript.Echo "FALSE"#Else# If IsDate(regValue) then# currentDate = Now# If Abs(DateDiff("d",regValue,currentDate)) <= maxDays then# Wscript.Echo"TRUE"# Else# Wscript.Echo"FALSE"# End If# Else# Wscript.Echo regValue# End if#End if#"
}
]
USB_POLICY_CLASS_ALLOWLIST
Type: array
Description: USB Policy class white list.
Parameters:
- VENDOR_ID: The vendor identifier of the USB product.
type: string
- PRODUCT_ID: The product identifier.
type: string
Example:
"USB_POLICY_CLASS_ALLOWLIST": {
"VENDOR_ID": "0x090C",
"PRODUCT_ID": "0x1000"
}
USB_POLICY_CLASS_DENYLIST
Type: array
Description: USB Policy class black list.
Parameters:
- VENDOR_ID: The vendor identifier of the USB product.
type: string
- PRODUCT_ID: The product identifier.
type: string
Example:
"USB_POLICY_CLASS_DENYLIST": {
"VENDOR_ID": "0x090C",
"PRODUCT_ID": "0x1000"
}
USB_POLICY_PRODUCT_ALLOWLIST
Type: array
Description: USB Policy product white list.
Parameters:
- VENDOR_ID: The vendor identifier of the USB product.
type: string
- PRODUCT_ID: The product identifier.
type: string
Example:
"USB_POLICY_PRODUCT_ALLOWLIST": {
"VENDOR_ID": "0x090C",
"PRODUCT_ID": "0x1000"
}
USB_POLICY_PRODUCT_DENYLIST
Type: array
Description: USB Policy product black list.
Parameters:
- VENDOR_ID: The vendor identifier of the USB product.
type: string
- PRODUCT_ID: The product identifier.
type: string
Example:
"USB_POLICY_PRODUCT_DENYLIST": {
"VENDOR_ID": "0x090C",
"PRODUCT_ID": "0x1000"
}
AGENT_HASH_QUERY
Type: string
Description: Agent hash query.
Example:
"AGENT_HASH_QUERY": "105283bb5d45ebaa0f961f3303f7d268"
AGENT_VPN_CONFIG
Type: object
Description: Agent vpn configuration.
Parameters:
- vpn”name”: VPN configuration code.
type: string
- EmmaVPN”name”: Emma VPN configuration code.
type: string
Example:
"AGENT_VPN_CONFIG": {
"vpnPublicDemoCenter": "client\\r\\dev tun\\r\\proto udp\\r\remote 95.216.236.62 1296\\r\resolv-retry infinite\\r\nobind\\r\\persist-key\\r\\persist-tun\\r\\comp-lzo\\r\\verb 3\\r\\<ca>\\r\\-----BEGIN CERTIFICATE-----\\r\\MIIFLTCCBBWgAwIBAgIJALi8EuRPC3TCMA0GCSqGSIb3DQEBCwUAMIG\\/MQswCQYD\\r\\VQQGEwJFUzELMAkGA1UECBMCQkExETAPBgNVBAcTCFRlcnJhc3NhMR8wHQYDVQQK\\r\\ExZvcGVuY2xvdWQgZmFjdG9yeSBzLmwuMQ4wDAYDVQQLEwVDb21tczEiMCAGA1UE\\r\\AxMZb3BlbmNsb3VkIGZhY3Rvcnkgcy5sLiBDQTEQMA4GA1UEKRMHRWFzeVJTQTEp\\r\\MCcGCSqGSIb3DQEJARYaY2VydEBvcGVuY2xvdXlkZmFjdG9yeS5jb20wHhcNMTcw\\r\\MjE0MTcyOTA0WhcNMjcwMjEyMTcyOTA0WjCBvzELMAkGA1UEBhMCRVMxCzAJBgNV\\r\\BAgTAkJBMREwDwYDVQQHEwhUZXJyYXNzYTEfMB0GA1UEChMWb3BlbmNsb3VkIGZh\\r\\Y3Rvcnkgcy5sLjEOMAwGA1UECxMFQ29tbXMxIjAgBgNVBAMTGW9wZW5jbG91ZCBm\\r\\YWN0b3J5IHMubC4gQ0ExEDAOBgNVBCkTB0Vhc3lSU0ExKTAnBgkqhkiG9w0BCQEW\\r\\GmNlcnRAb3BlbmNsb3V5ZGZhY3RvcnkuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOC\\r\\AQ8AMIIBCgKCAQEArcwlJPSlR9\\/zw0xVO9DzTn+jpoAiqVL7R6eWXI7dkSC4Tq62\\r\\ul0QY6Cw6bSybiEJCYE7J2iCcIQN\\/0Lfa\\/lAzx4OSjVX8h+5bZQ6CJYtxajmJXWe\\r\\6L5QrCPMEYXgRS77uBUU3KKettNGK8Q4xhZEUZaVzf3QsHtpzDUpzqIdU2khmLF9\\r\\OpTzS5G76kcsH7oBCwiW6PTHTc1WuZZHWAIZOq7M\\/1lLqQE4dzC\\/tubWinhhy9kC\\r\\PszfmYCEwM0Ot4xqL1btkPFAOK3CtRhky+rlsnObVymqkUY41kjwqZxD6jEnzm4W\\r\\QaPehoQs77cdcCsQy9GTUvk5gMMvj+EWUYYtOQIDAQABo4IBKDCCASQwHQYDVR0O\\r\\BBYEFD\\/DqSfj4jKuG\\/RtQCCHK06HtWqwMIH0BgNVHSMEgewwgemAFD\\/DqSfj4jKu\\r\\G\\/RtQCCHK06HtWqwoYHFpIHCMIG\\/MQswCQYDVQQGEwJFUzELMAkGA1UECBMCQkEx\\r\\ETAPBgNVBAcTCFRlcnJhc3NhMR8wHQYDVQQKExZvcGVuY2xvdWQgZmFjdG9yeSBz\\r\\LmwuMQ4wDAYDVQQLEwVDb21tczEiMCAGA1UEAxMZb3BlbmNsb3VkIGZhY3Rvcnkg\\r\\cy5sLiBDQTEQMA4GA1UEKRMHRWFzeVJTQTEpMCcGCSqGSIb3DQEJARYaY2VydEBv\\r\\cGVuY2xvdXlkZmFjdG9yeS5jb22CCQC4vBLkTwt0wjAMBgNVHRMEBTADAQH\\/MA0G\\r\\CSqGSIb3DQEBCwUAA4IBAQBPC2UfU\\/ElhT2GDLhjxjGPM1aWA+G0r+zc7lD3FjaT\\r\\ud+MQa6s9loNaGvJqaHSm8IMWKbMuLSprvYrqLpmTC\\/sEtsnOLLOTh3bWV3vo6\\/p\\r\\QVGUhFsjG6G\\/Ad5Pwv6JoRAbCFcU5hvY66\\/B0YO49yEJ7VQ\\/\\/FNV8vTBws1ycLZM\\r\\JAtJA6pxSoyoMdBcW9x+ocDPQ6z0pKlcGH7PQt7SIFTW87Jf5uYcOcwAZ4ljBZHY\\r\\haMo7x+mBHE8Ev+hP4Ohzc3Xw5eBXp0jaM6GZWnPtsypJWGCu\\/il9Sc+r5BFOQfx\\r\\ZGRHcYohKx+AwqBynkOM3ou2+qLL84O5gFL25V3UuL9I\\r\\-----END CERTIFICATE-----\\r\\<\\/ca>\\r\\key-direction 1\\r\\cipher BF-CBC\\r\\auth SHA1\\r\\auth-user-pass\\r\ns-cert-type server\\r\\explicit-exit-notify\\r\\management-query-passwords",
"EmmaVPNRoadWarrior": "client\\r\\dev tun\\r\\proto udp\\r\remote 194.116.240.3 21196\\r\resolv-retry 3\\r\nobind\\r\\persist-key\\r\\persist-tun\\r\\cipher AES-256-CBC\\r\\verb 1\\r\\comp-lzo \\r\\explicit-exit-notify\\r\\auth SHA1\\r\\auth-nocache\\r\\<ca>\\r\\-----BEGIN CERTIFICATE-----\\r\\MIIDUzCCAjugAwIBAgIJAKvgHeau41AzMA0GCSqGSIb3DQEBCwUAMCAxHjAcBgNV\\r\\BAMMFUVtbWFWUE5Sb2FkV2Fycmlvcl9DQTAeFw0yMDAzMTcxMzExMTlaFw0zMDAz\\r\\MTUxMzExMTlaMCAxHjAcBgNVBAMMFUVtbWFWUE5Sb2FkV2Fycmlvcl9DQTCCASIw\\r\\DQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBANdpZY3xVEutc0ka8XrYjxGbfDyD\\r\\P8UnADCsOz2BFbYqC0ZI+RLxtYaGCdXCxRu1Ks7+iPk3KUled4qAaXPs2wA9dhIf\\r\\QUOQrPMp2UP8zB4PUuddL3q6rrx9hvuP4Srt9dZiX5TxEA3cVILNjoJ+\\/viOIlKJ\\r\\B\\/kHD4jnlSCVQ2hK1hEPnuMb6B60hwIo86gZb5D5W+f6UGEzE6kChHQdQjiF7sbo\\r\\coC9fatdhFHf5rS0ViR0lz+DhcbLa5egNXpKZXAERi25VVKA5eZqhkppVNB9vs9u\\r\\X9Q8G\\/wwHXtgrQeTLO\\/7pZ1V\\/275tL\\/6fhE1GBefaJby\\/\\/QqpyukHm+bJfMCAwEA\\r\\AaOBjzCBjDAdBgNVHQ4EFgQUkceeifX2OpBtZNQ0QPFuuzq6ErQwUAYDVR0jBEkw\\r\\R4AUkceeifX2OpBtZNQ0QPFuuzq6ErShJKQiMCAxHjAcBgNVBAMMFUVtbWFWUE5S\\r\b2FkV2Fycmlvcl9DQYIJAKvgHeau41AzMAwGA1UdEwQFMAMBAf8wCwYDVR0PBAQD\\r\\AgEGMA0GCSqGSIb3DQEBCwUAA4IBAQDNItJ792Ay22YyucV+CpRAvRxdxnm1rANM\\r\\z7JB9iOzItfRj+x1s+gKV7\\/hlDUjg9q7ms2Y2F8x2v83LiIyzperI3tXECI52QPF\\r\\GSHGnuDA6ZBak7CaH14vaetV128uTyIf746K9usmlqhZUv0OmayOlGRl22XOcAql\\r\\jgrzTEgNg8rxMFtAwzIhn97CGprTbXugbbFLtiyx8MzOgy50usBv+U9obwROWMbT\\r\\BqQXkUwIVT\\/YzQIOYOIKH4tIDCV1+6U1KwKgOdEXRtkxiSQagQlCOENvCkFwuwt6\\r\\uTRbZD8vMCmpMIGieUGDrt59N4zgGXnTGJrfOT1ysFafdTkNY7G5\\r\\-----END CERTIFICATE-----\\r\\<\\/ca>\\r\remote-cert-tls server\\r\\auth-user-pass\\r\\explicit-exit-notify\\r\\management-query-passwords\\r\"
}
VLAN
Type: string
Description: VLAN id.
Example:
"vlan": "253"
AGENT_POLICY_NAME
Type: string
Description: Last policy returned.
Example:
"AGENT_TASKBAR_CONFIG": "Corp. User & Corp. Device (AV & UPDATES)"
AGENT_POLICY_USER_MESSAGE
Type: string
Description: User message when matches the policy.
Example:
"AGENT_POLICY_USER_MESSAGE": "msg example"
AGENT_DEVICE_TAGS
Type: string
Description: Tags learned by matching the policy.
Example:
"AGENT_DEVICE_TAGS": "ONC_AUTOLEARNED,ONC_AGENT,ONC_WIN_AGENT,ISS_FW_STATUS,ISS_FW_UPDATE,ISS_FW_ENABLED,ISS_AV_STATUS,ISS_AV_UPDATE,ISS_AV_ENABLED,DOS_WINDOWS_10,ROS_WINDOWS"