Trend Micro’s Deep Discovery Solution¶
Minimum openNAC release required: 7105
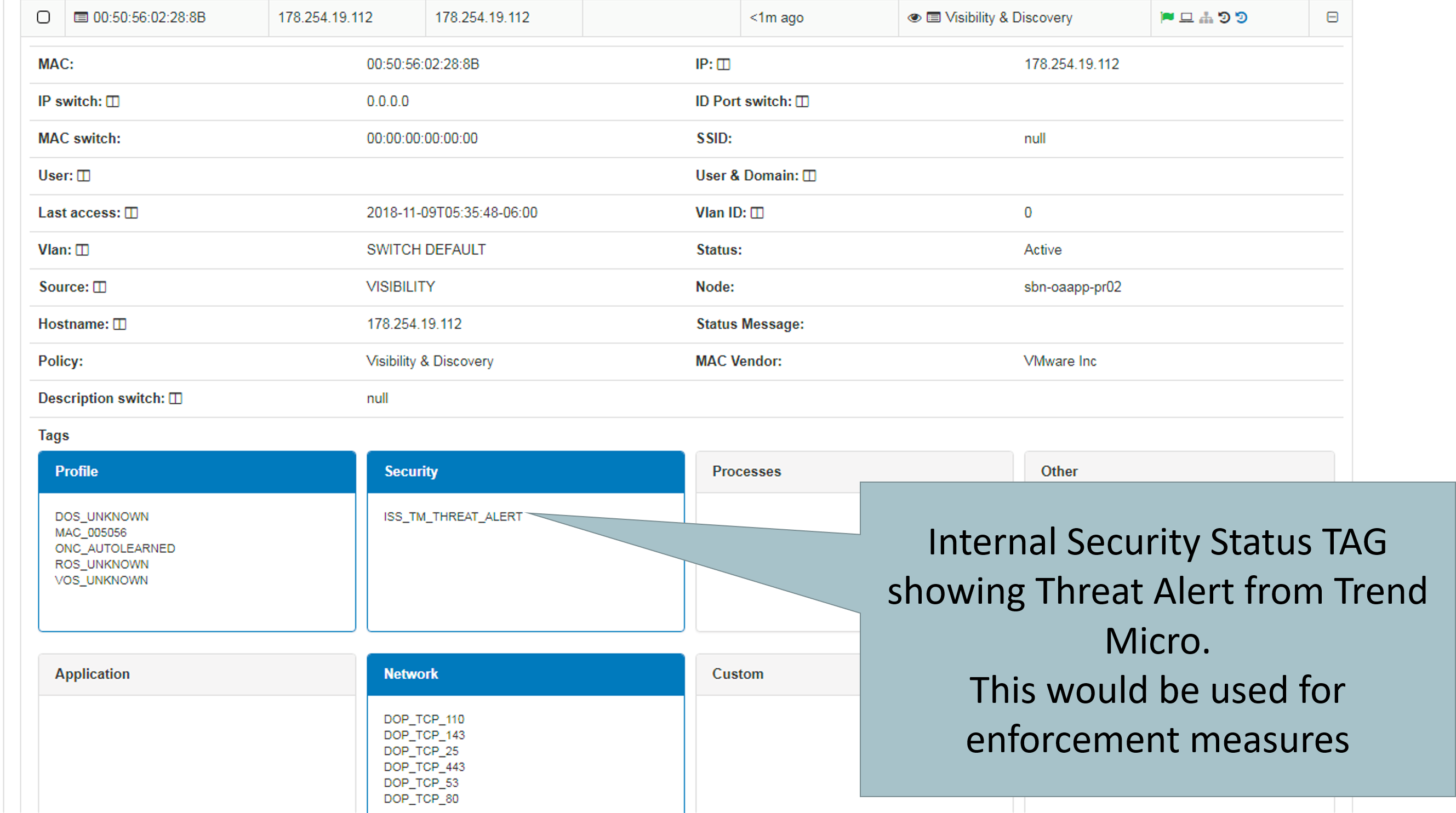
Based on data sent from TrendMicro’s Deep Security, Deep Discovery Inspector, OfficeScan or TMCM, we can analyze these kind of event logs and then be able to generate a TAG indicating that determinate device is a Threat, enabling us the possibility to isolate this device at layer 2 level.
- First of all, the customer needs to configure event log forwarding from Trend Micro’s tools, to the openNAC’s Aggregator TCP/5002 port;
- Now the next step is to generate an policy that will put devices containing the TAG ISS_THREAT_SCAN in Quarantine or in the VLAN that should work as isolation VLAN.
Who?
Trend Micro’s Deep Discovery is an IPS that analyzes network data and generates alerts based on threat events it may encounter in the customer’s network.
How?
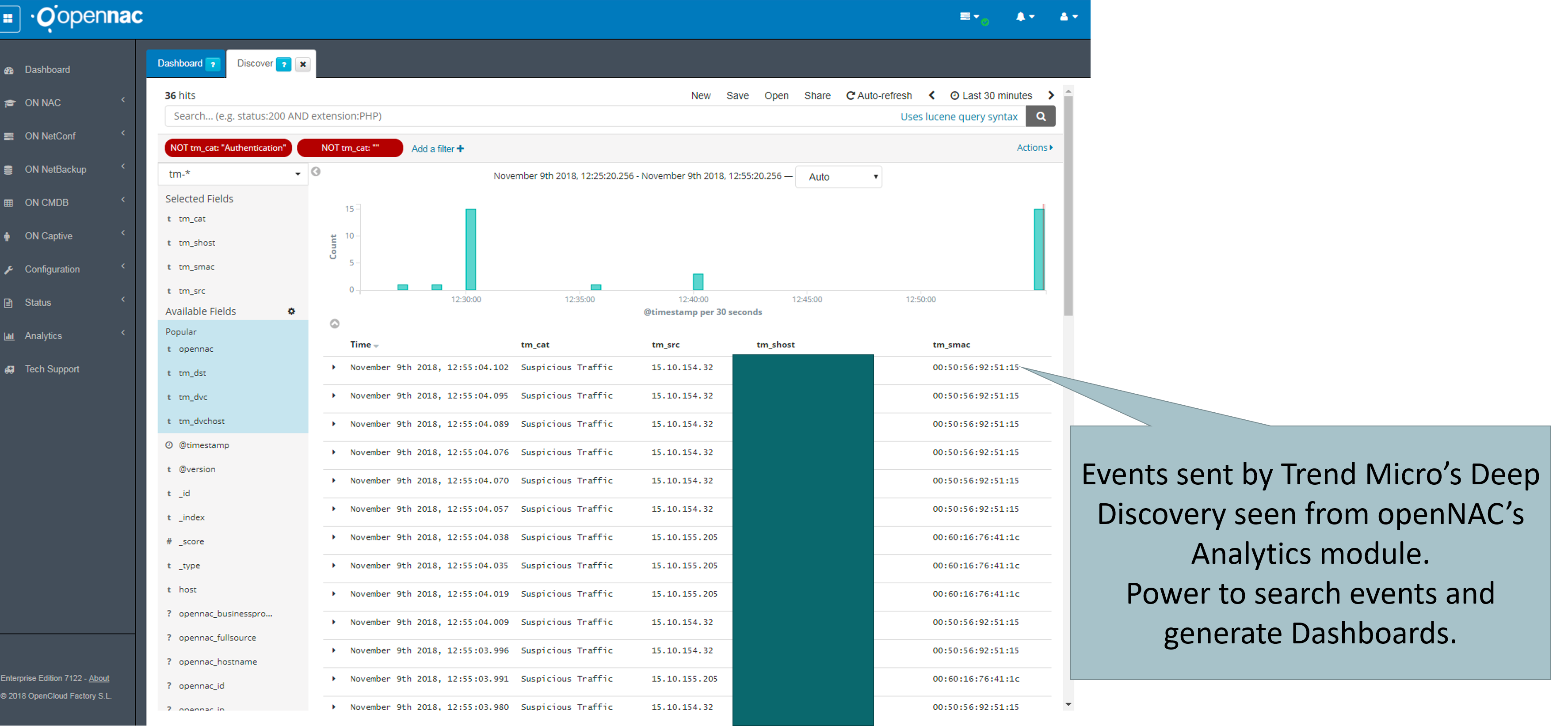
By receiving Deep Discovery’s logs, openNAC can, automatically, execute 2 tasks:
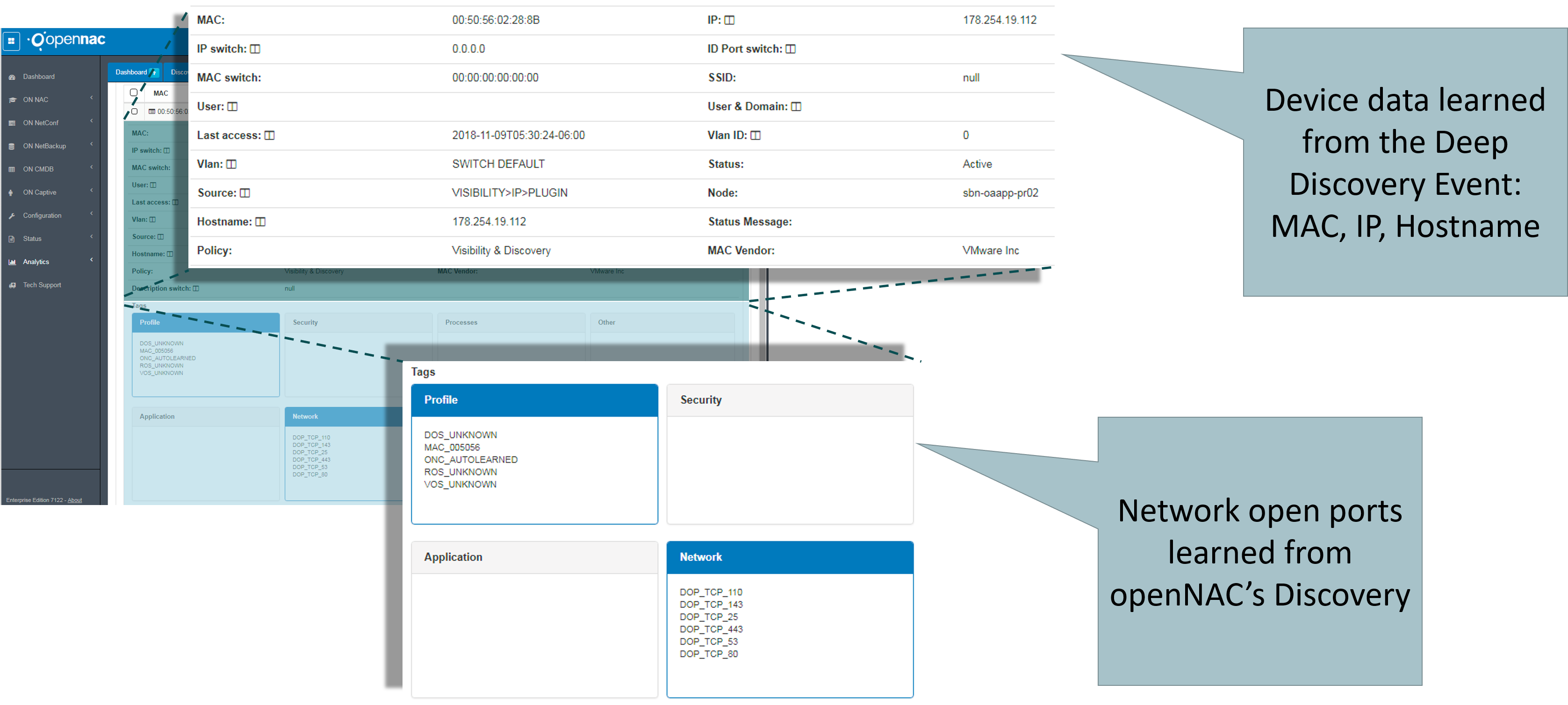
- Visibility and Discovery: By receiving the source device’s hostname, MAC Address and IP, we can learn the device and insert it into our CMDB, enabling the executon of our Discovery plugins and generating an correlated output showing data from Deep Discovery Alert’s, the perspective from openNAC Agent and also the network point of view from openNAC Discovery;
- Layer 2 blocking: By receiving an alert, an offending device that is being authenticated in a switch managed by openNAC can be isolated, being thrown to a Quarantine VLAN.
Step by Step
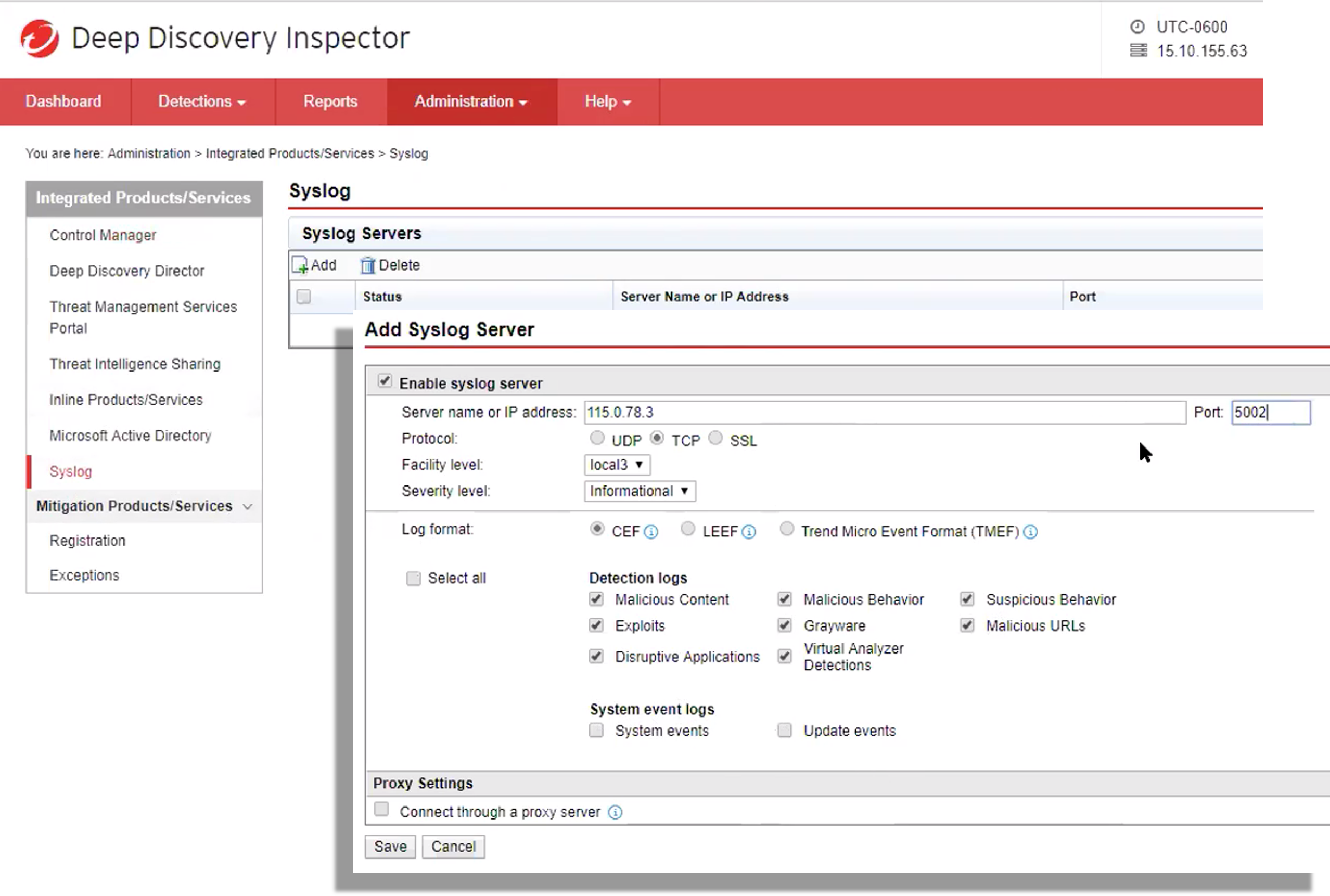
- Go to Administration
- Integrated Products/Services
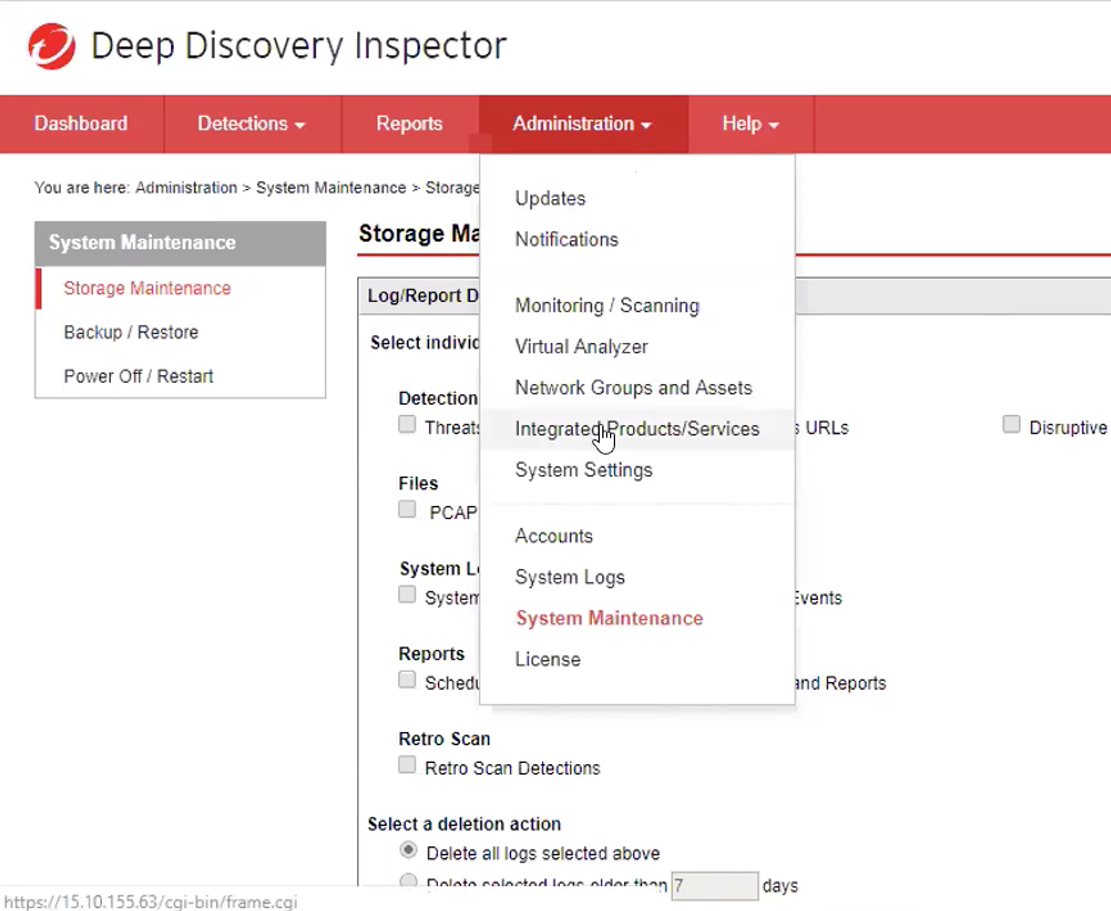
- Inside the lateral menu, click in Syslog
- Inside Syslog Servers, click in “Add”
- Configure the Server name or IP Address to your openNAC’s Analytics IP Adress and the port 5002
- Set the Protocol to TCP
- Log format should be CEF
- Define which of the Detection Logs you would like to send to openNAC
Results