4.8.1. Third Party VPN
This section explains a use case consisting of VPN access in a third-party VPN where we are going to validate certain requirements of the device connected to the VPN to grant access to the internal network resources.
To do this we will use the ON Captive module with the guest profiling workflow. Profile Based workflow.
4.8.1.1. Flow
An external user connects to a VPN gateway (independent of the OpenNAC Enterprise Solution) and when the user tries to access to the internal resources through the internal firewall, the connection is redirected to the Captive Portal where it is evaluated.
The Captive Portal interacts with the ON Core and warns the internal firewall to grant or deny access to internal resources.
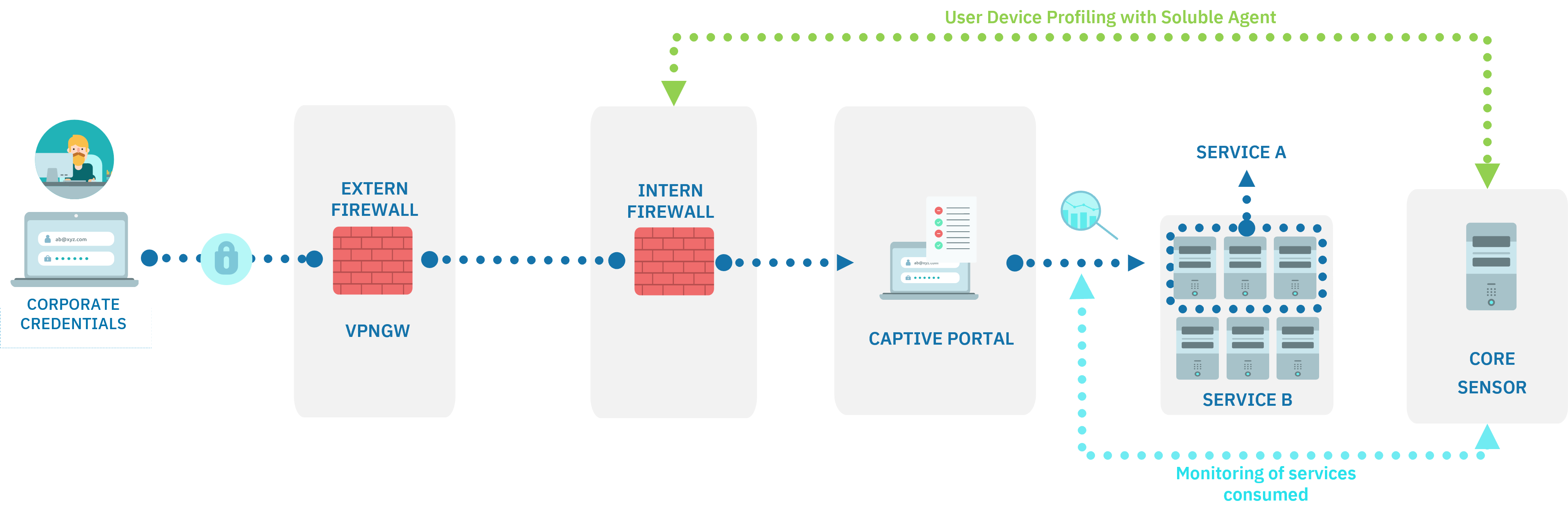
Note
If the portal is accessed with a device for which there is no agent available (e.g. android), the tag ONC_AGENT_UNAVAILABLE will be assigned and the captive portal flow will be finished.
To control these devices, the corresponding policy would have to be created.
4.8.1.2. Steps to reproduce
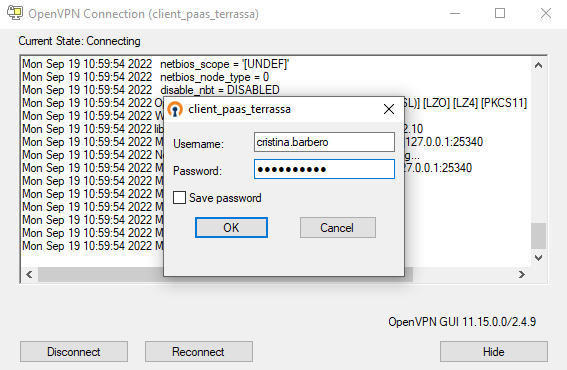
Connect to your corporate VPN using your corporate credentials. For example OpenVPN.
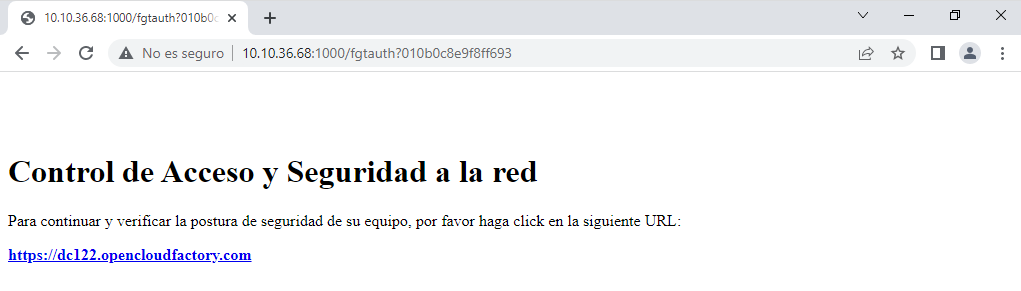
Once authenticated, when you try to access to your corporate resources via the web, you will be presented with a link to be redirected to the ON Captive Portal.
On the Captive Portal workflow, you will be required to accept the privacy terms and policies and log in.

This will automatically download the Soluble Agent. Following the browser instructions.
Note
If the portal is accessed with a device for which there is no agent available (e.g. android), the tag ONC_AGENT_UNAVAILABLE will be assigned and the captive portal flow will be finished.
To control these devices, the corresponding policy would have to be created.
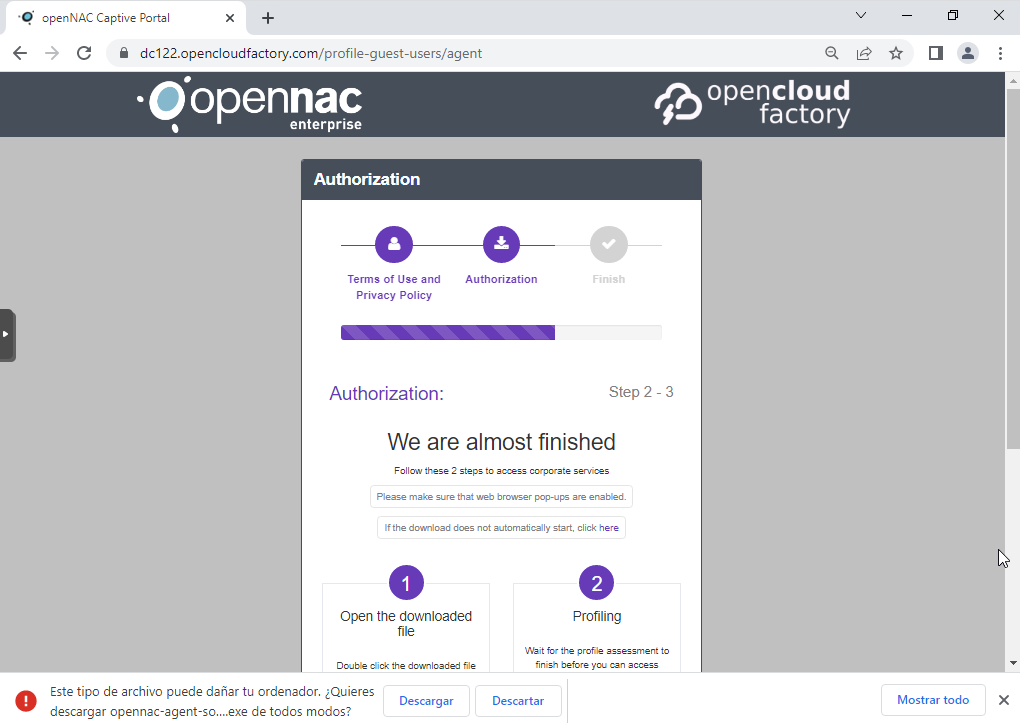
4.1. You should open the executable file.
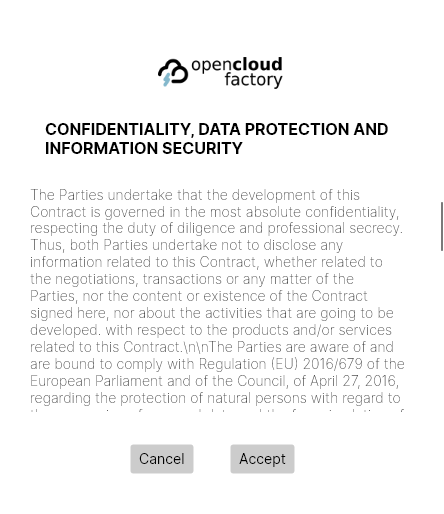
4.2. You should accept the license.
Once the process has finished (it will take a few seconds), it will send the payload to the ON Core. The web browser will be updated an you will be granted access to the corporate services.
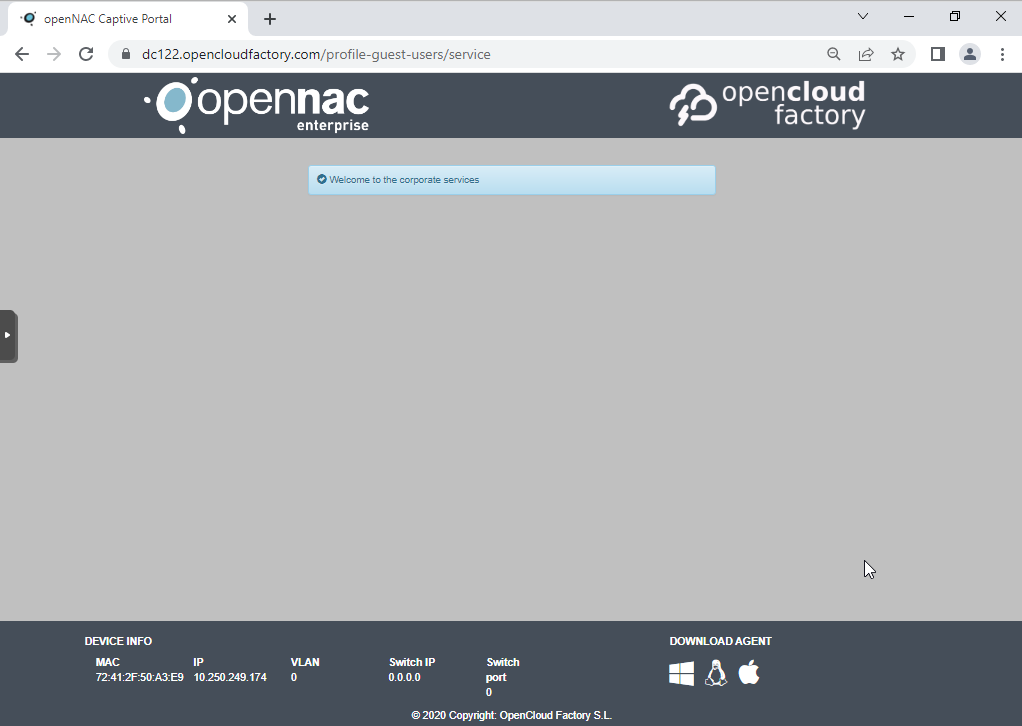
4.8.1.3. Validate the access
On the OpenNAC Enterprise Web Administration Portal, we should go to the correspondent Business Profile.
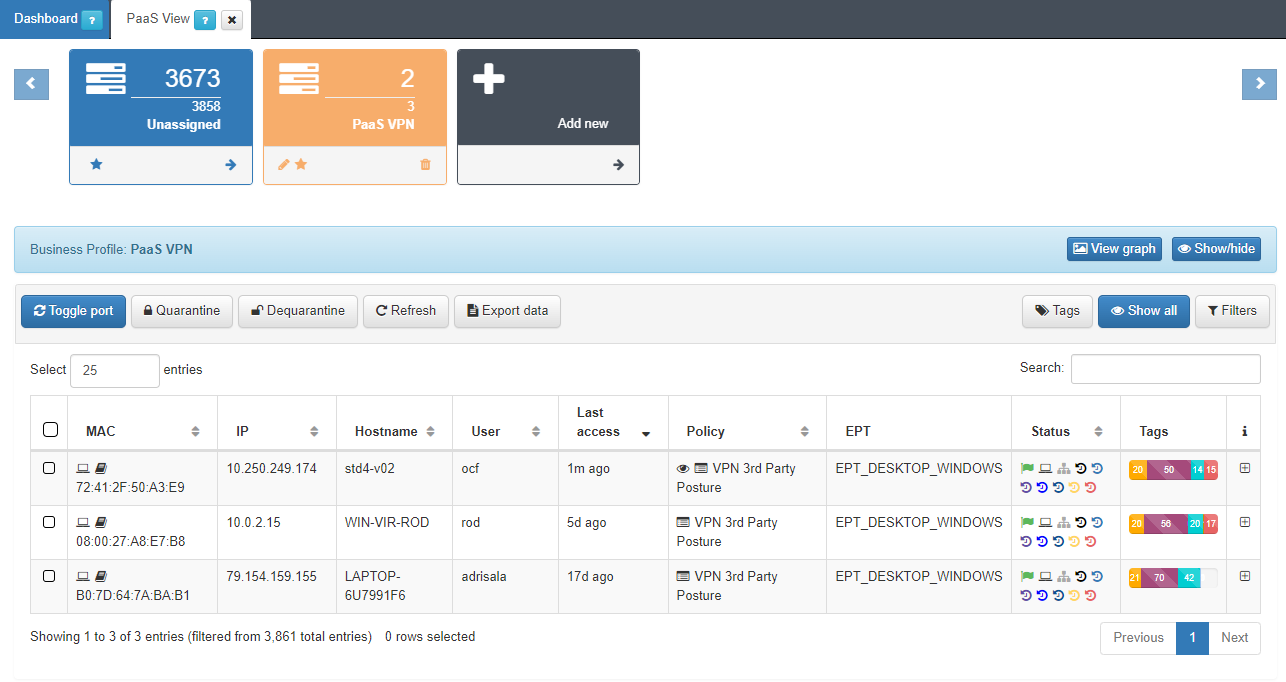
As we can see, the profile “ocf” is in the “VPN 3rd Party Posture” Policy. If we unfold the tab to reveal further information we can see details in the Tags such as:
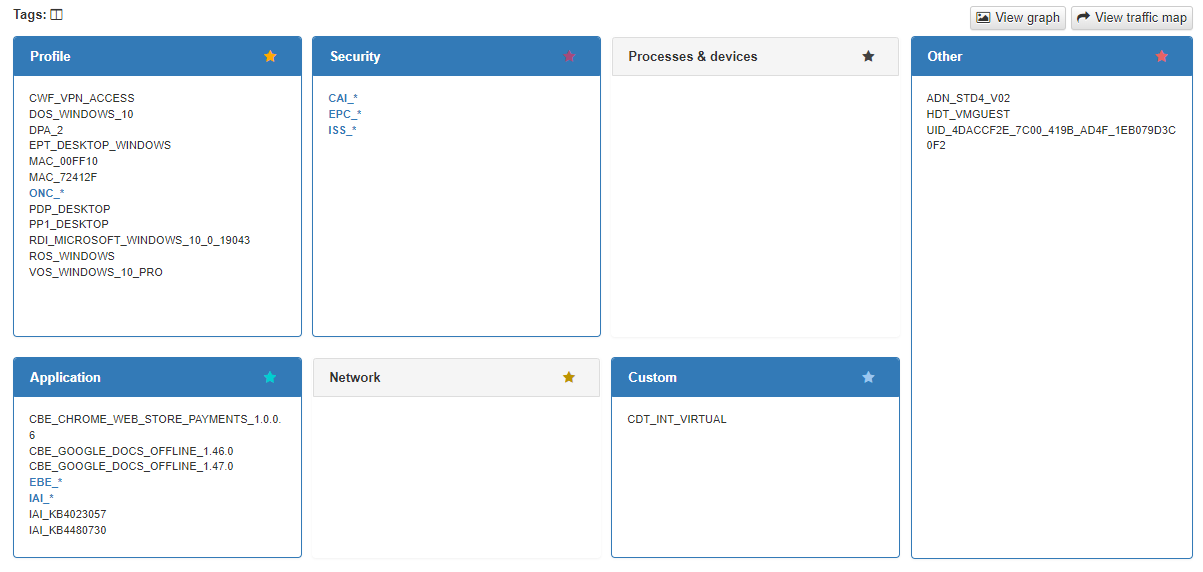
The Captive Workflow (CWF_VPN_ACCESS)
The Operating System (DOS_WINDOWS_10)
The installed OpenNAC components
The applications and its security patches
etc.
The ONC_AUTHORIZATION_DENIED tag will be added when a user enters a quarantine policy during a Captive workflow.
Clicking on the policy eye we can gather more information about the authorization steps.
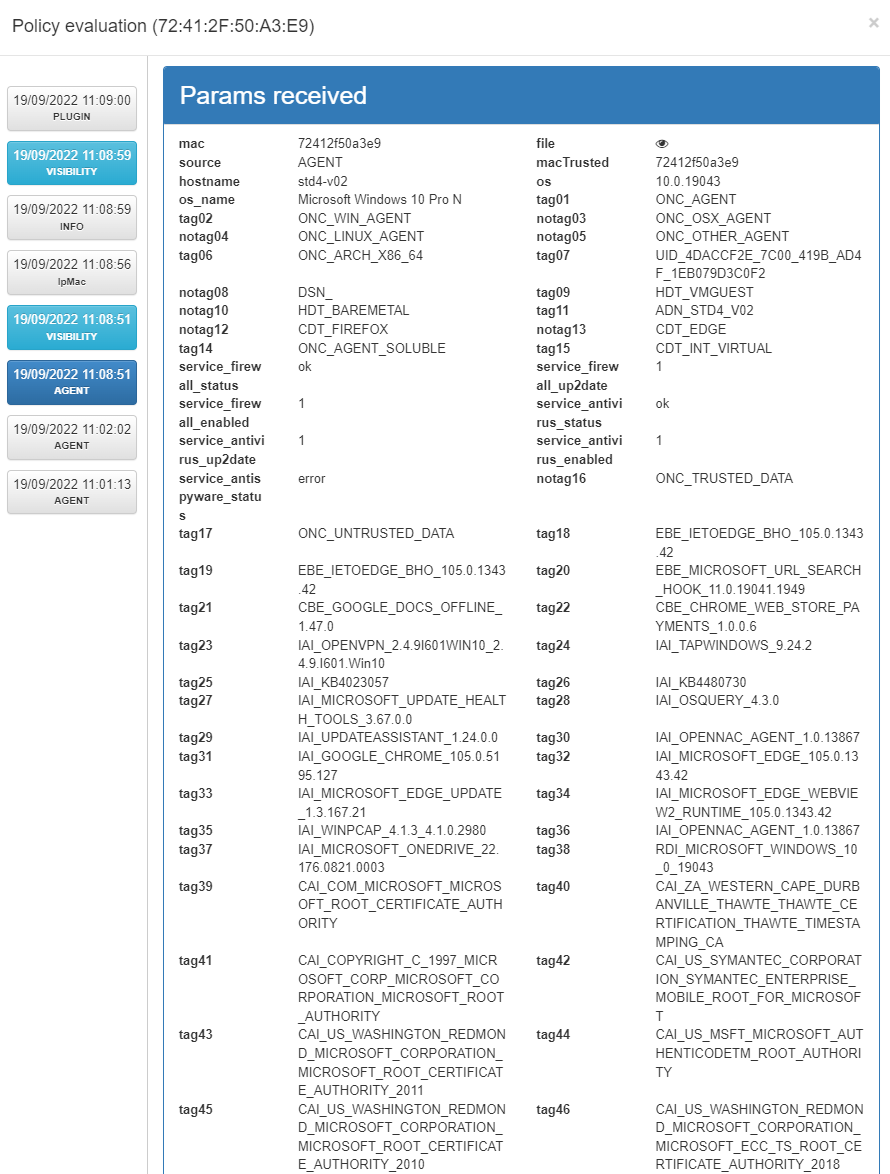
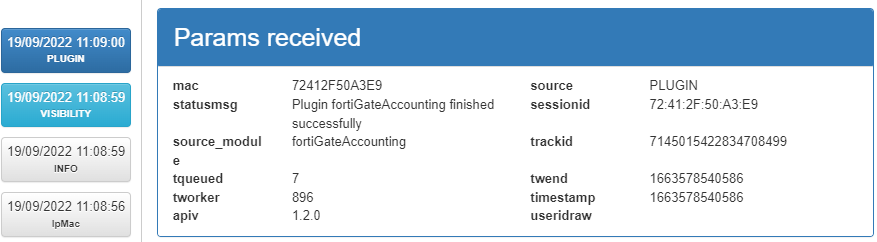
In the “PLUGIN” section we can see the source module as “fortiGateAccounting” as that is the way to interact with the firewall.
4.8.1.4. Policy Configuration
To be able to match this policy:
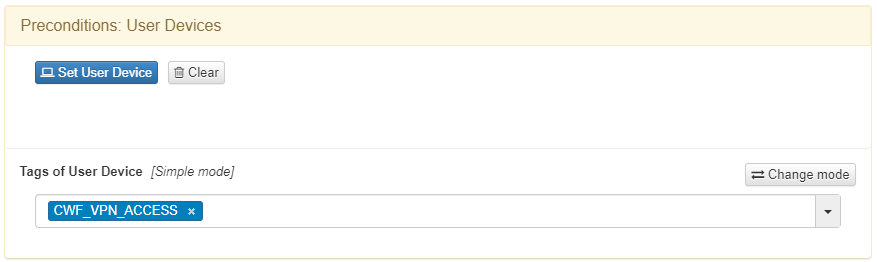
In Preconditions: User Devices we should indicate the VPN Access Workflow with the CWF_VPN_ACCESS tag
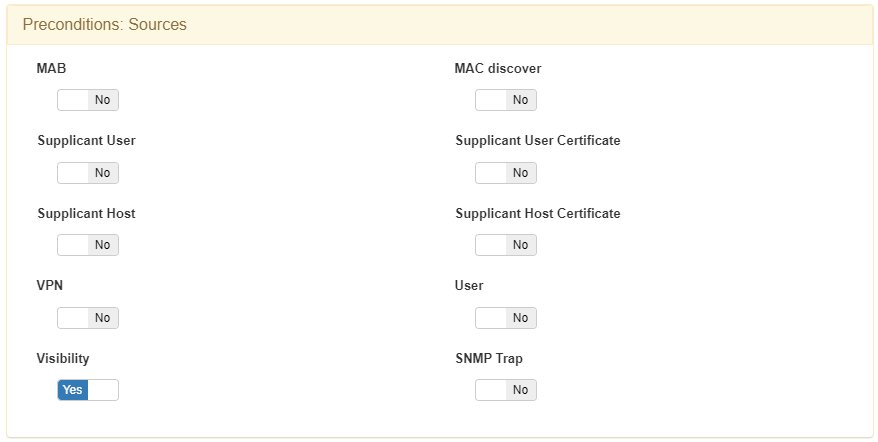
In Preconditions: Sources it should have the Visibility flag activated
In Postconditions
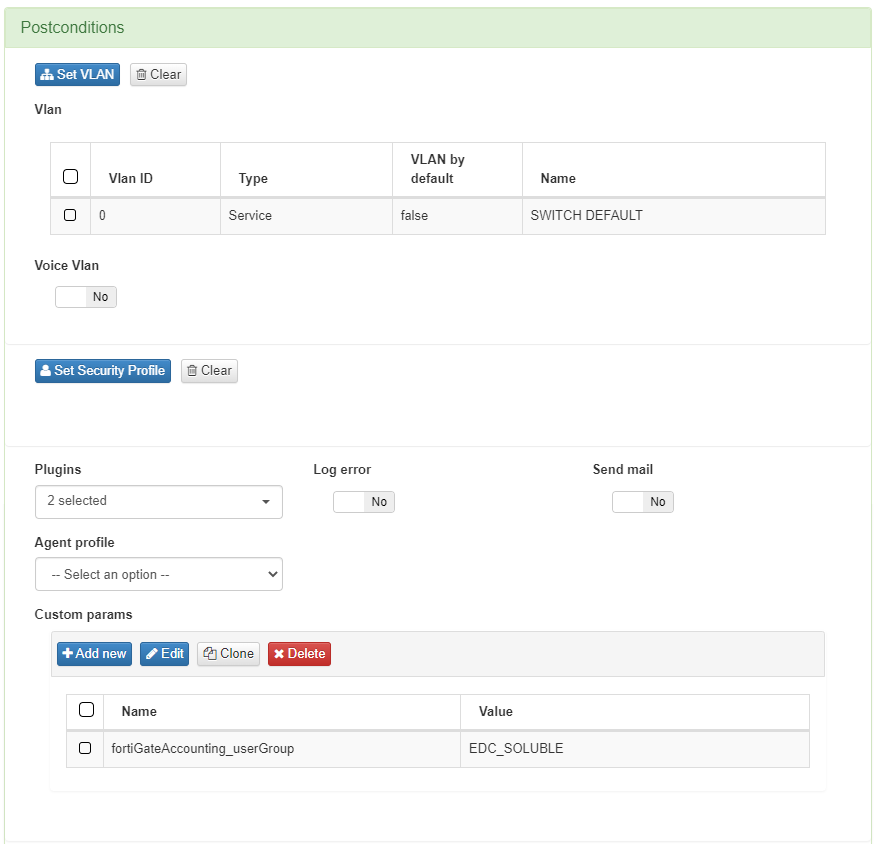
Vlan we should select the Switch Default VLAN as we do not interact with any Layer 3 device.
Plugins we should have the fortiGateAccounting plugin with a custom param where we specify the user group that it has to write in order to be accepted on the Fortinet Policy
4.8.1.5. UD Tag policies Configuration
To get compliance devices on this use case, we need to create the EPC_COMPLIANCE tag with our own compliance restrictions.
Note
If the tag used is not EPC_COMPLIANCE the dashboard will not be shown properly.
To do so, we need to go to ON NAC -> Tag policies -> UD Tag policies and create this tag.
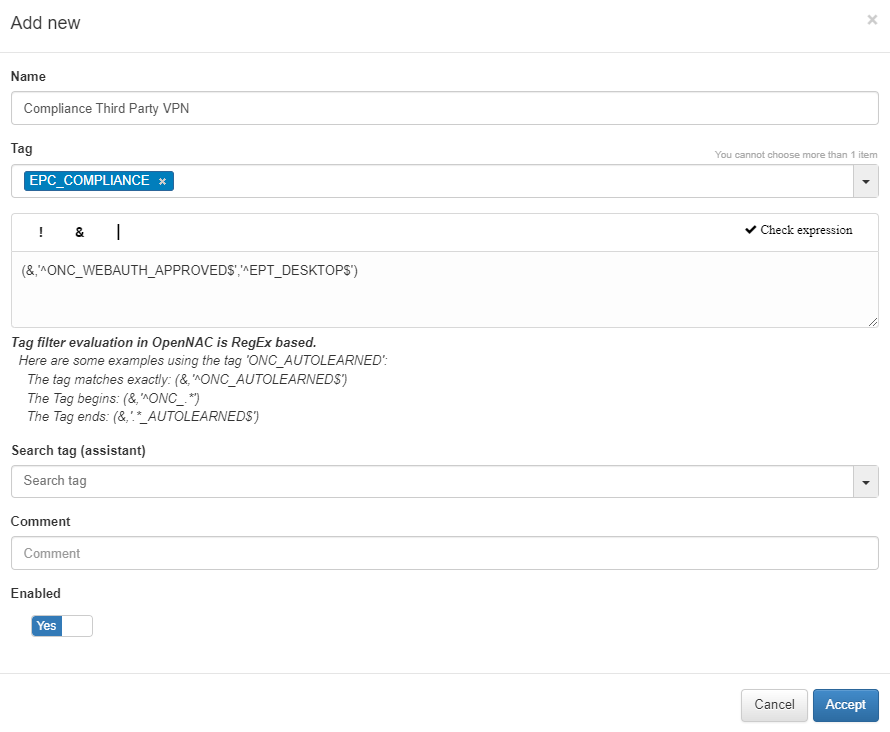
4.8.1.6. Monitoring
The Third party VPN dashboard displays all the events related to the Third Party VPN use case.
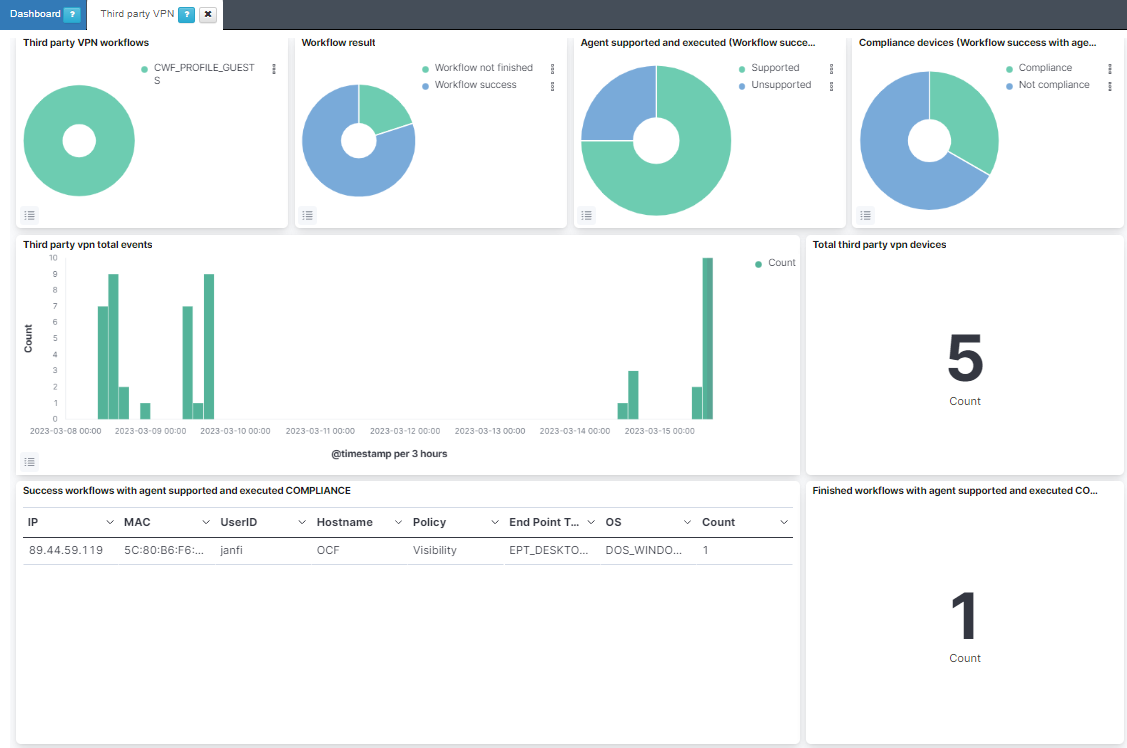
Third party VPN workflows: A pie chart that shows the Captive Workflow used.
Workflow result: A pie chart that shows the result of the workflow (success/not finished).
Agent supported and executed (Workflow success): A pie chart that shows the agent executed whether it is supported by the browser or not (and later executed or not) (supported/unsupported).
Compliance devices (Workflow success with agent supported): A pie chart that shows the relationship between compliance and not compliance devices.
Third party vpn total events: Third party VPN total events on a timeline.
Total third party vpn devices: The total number of third party VPN devices.
Success workflows with agent supported and executed COMPLIANCE: The workflows executed with the supported agent that are compliant.
Finished workflows with agent supported and executed COMPLIANCE count: The total number of workflows executed with the supported agent that are compliant.
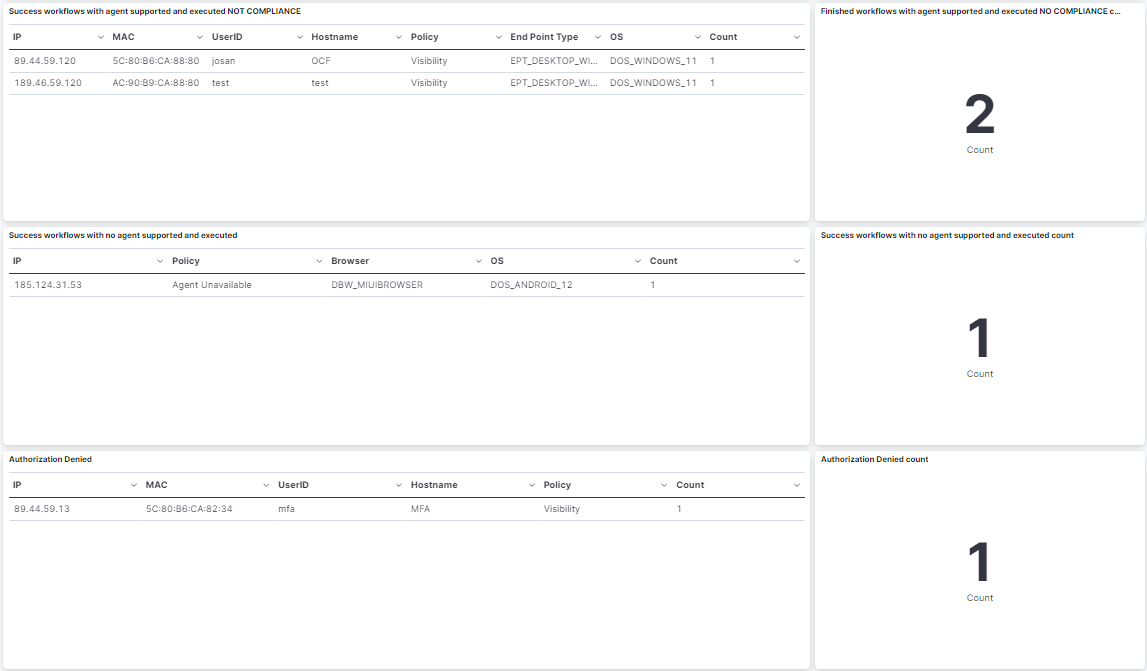
Success workflows with agent supported and executed NOT COMPLIANCE: The workflows executed with the supported agent that are NOT compliant.
Finished workflows with agent supported and executed NO COMPLIANCE count: The total number of workflows executed with the supported agent that are NOT compliant.
Success workflows with no agent supported and executed: The workflows executed but without the agent because of the browser.
Success workflows with no agent supported and executed count: The total number of workflows executed but without the agent because of the browser.
Authorization Denied: The authorizations that have been denied.
Authorization Denied count: The number of authorizations that have been denied.
Total third party vpn events: List of third party VPN events that includes their time, opennac_ip, opennac_mac, host, opennac_userid, and opennac_rule.