6.2.2. Data Sent to the OpenNAC Server
In the context of the Soluble Agent, information is sent only once during its execution. Once the application is launched and the user accepts the terms of use, the device scan initiates. Once the scan is complete, the application sends its results to the Core server.
In this section, we will first present the groups of information that are collected, showing each parameter with its description and example in a table format.
Following that, we will provide an explanation of the structure of the payload sent to the Core server, which contains all the gathered information. This explanation will help illustrate how the data is organized and formatted within the payload, giving you a clear understanding of its composition.
Finally, we will show an example of a real payload.
6.2.2.1. Data extracted from devices
This section provides an overview of the different groups of information that soluble Agent collects from a device on which it is running. The data includes details about your network status, hardware specifications, installed programs, system users’ session history, connected USB devices, device security status (antivirus, firewall), certificates, available WiFi networks, installed browser extensions, running processes, established socket connections, and open ports.
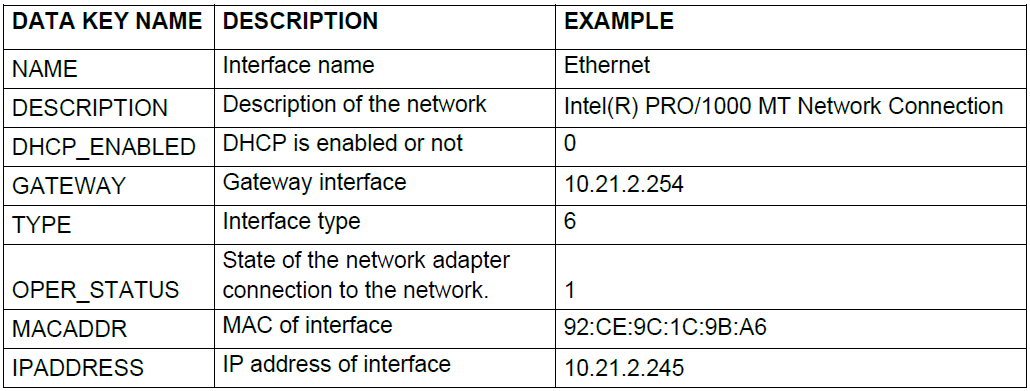
6.2.2.1.1. Networks

Knowing the status of the user’s networks is essential for identifying their current connections, determining the status of the connection (whether it is active or not), and determining if it is a VPN connection or any other type of connection.
The following attributes represent the Network entity.
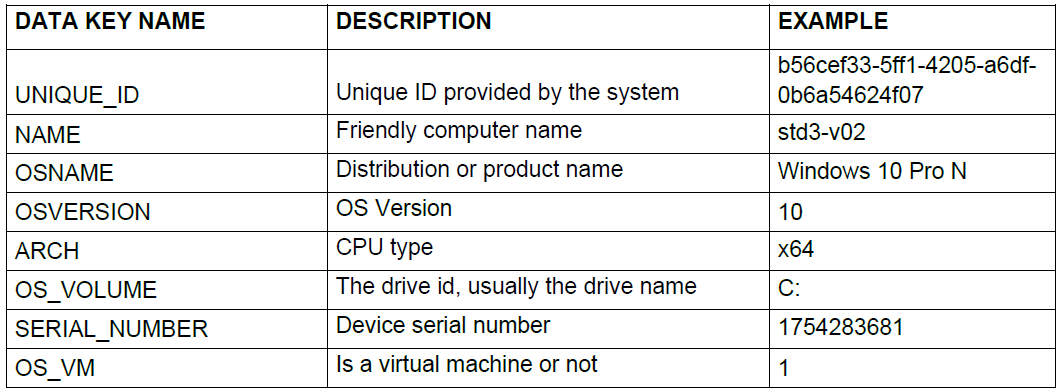
6.2.2.1.2. Hardware

Collecting data related to the device’s hardware provides valuable information about its operating system, version, virtual machine status, architecture, serial identifiers, and more. While not all the information would be about the hardware itself, certain details like the machine’s name are assigned by the user during installation.
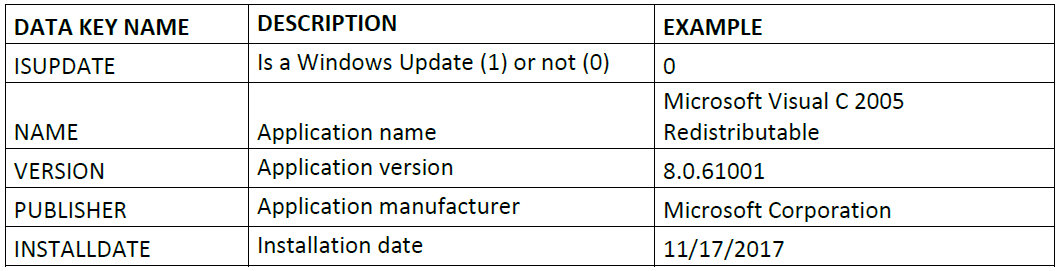
6.2.2.1.3. Softwares

The software or applications installed on a device provide valuable information that can be extracted for various purposes. Knowing the applications and their versions enables the generation of tags and facilitates device compliance assessment. If an application on a device has a version lower than the minimum expected, it will be classified as non-compliant. Additionally, these applications assist in identifying pending operating systems updates that the user needs to install.
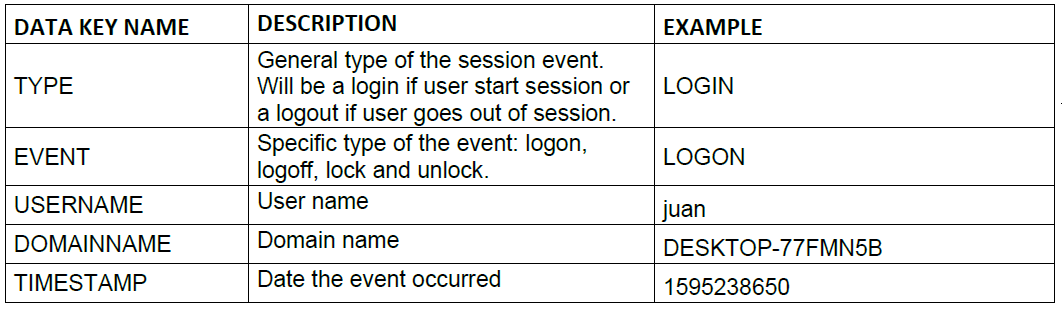
6.2.2.1.4. Session events

With this entity, we can have a record of the session events on a device. In this way, any session start, close, lock, or unlock will be sent to the Core.
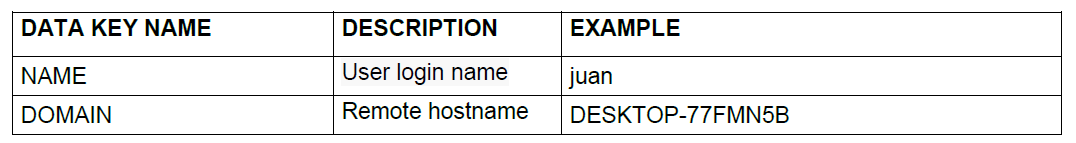
6.2.2.1.5. Active user

This entity is very simple; it only contains the name of the domain and the user who is currently logged into the device. In this way, we can identify in the Core which user is using that device with a specific MAC and IP interface.
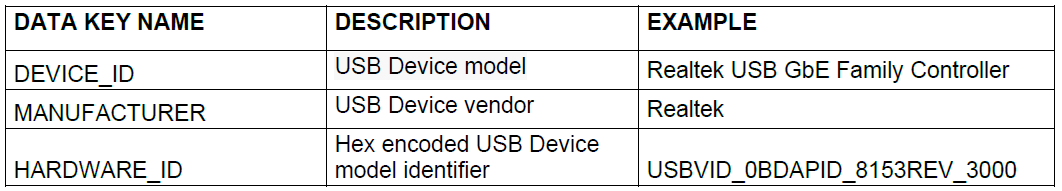
6.2.2.1.6. USB devices

This entity collects information about USB devices connected to a device.
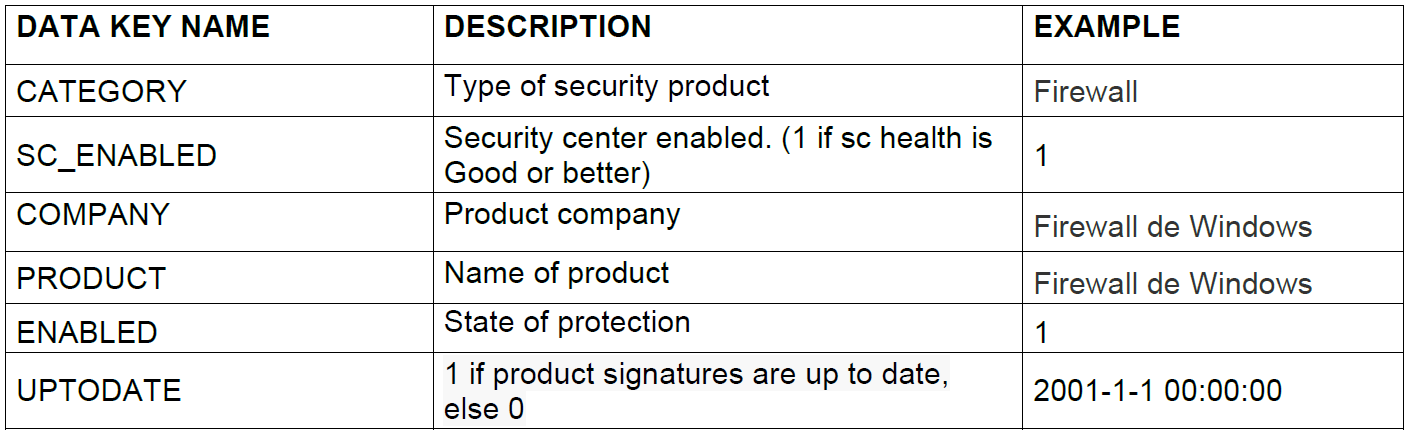
6.2.2.1.7. Security center

This is a Window only entity and is especially useful to know the current state of security on a device. In this way, you can know the health of the antivirus/firewall, if it is connected or disconnected, what product it is, etc.
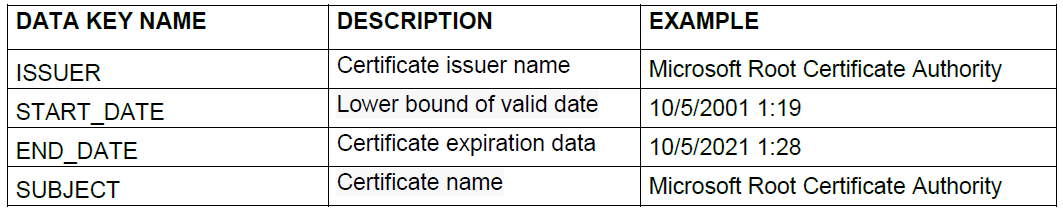
6.2.2.1.8. Certificates
The certificates available to the user on their device.
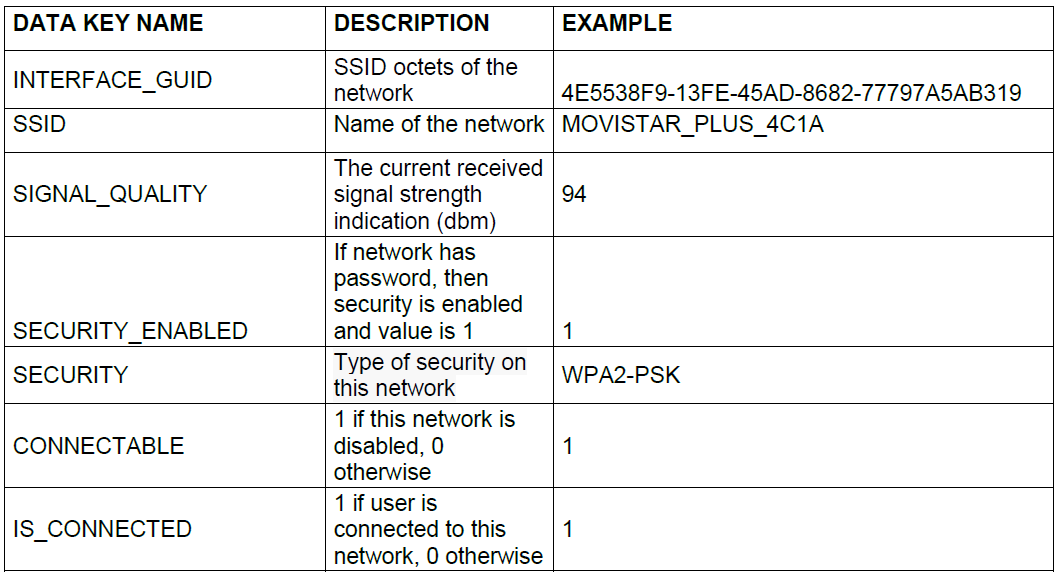
6.2.2.1.9. WiFi

The available WiFi networks in the range of the device. From them, we want to know its SSID, its current status, the type of security and the quality of the signal.
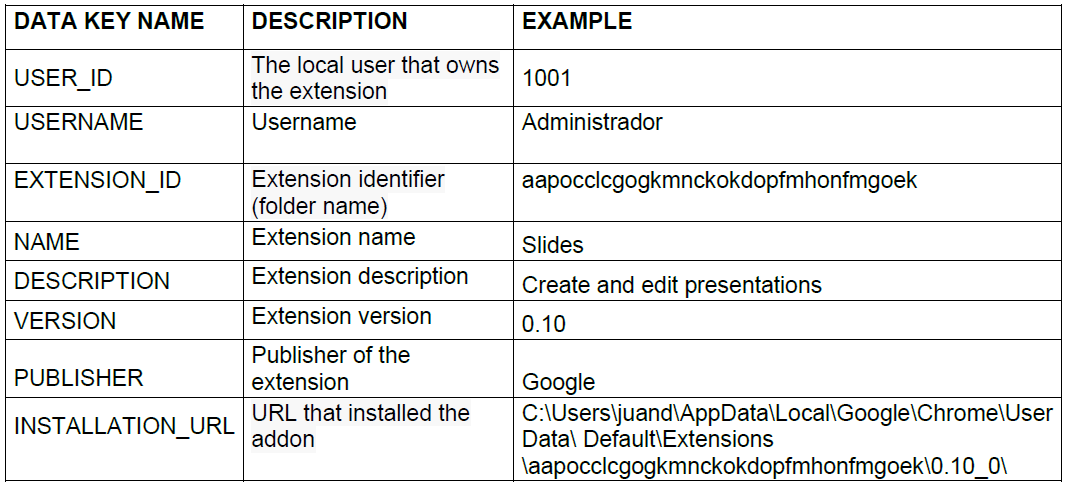
6.2.2.1.10. Browser extensions

The browser extensions are one of the last entities added in the Agent and it is used to know the services that have been given permissions in our browser.
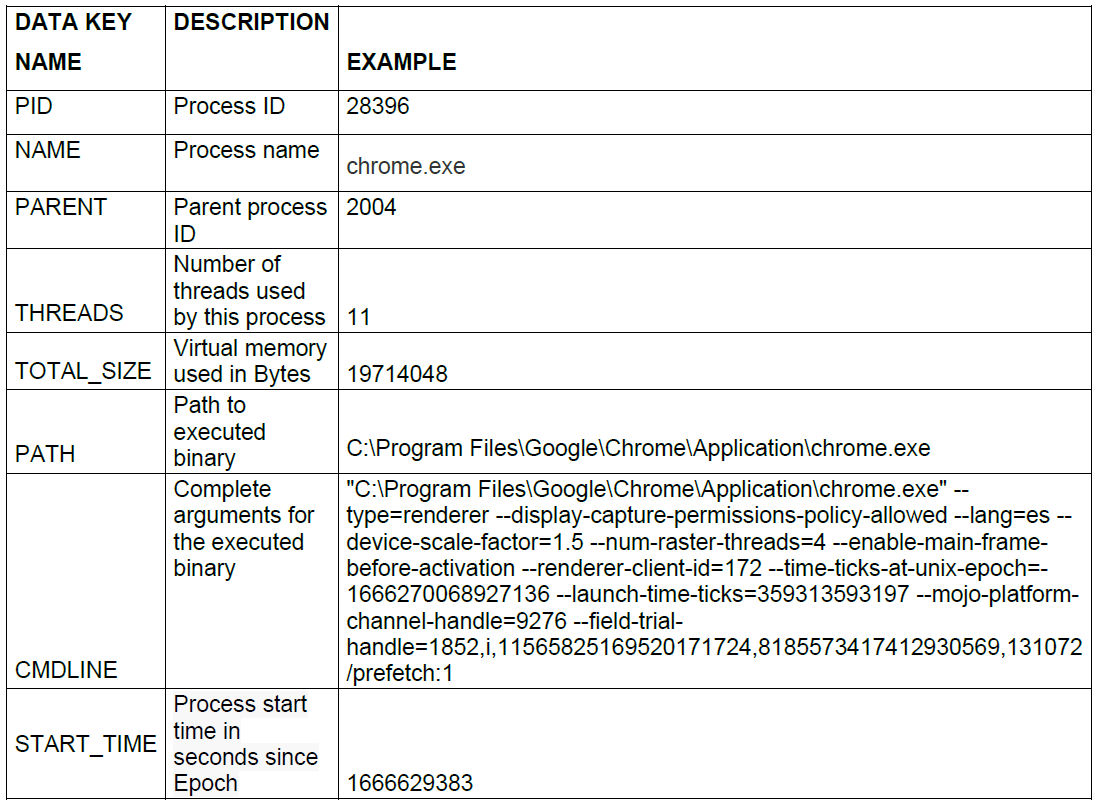
6.2.2.1.11. Processes

The process entity informs us about the active tasks in the machine. Every program or script that the processor is executing at the time of a payload will be in this list.
6.2.2.1.12. Established connections

This entity is formed by a list of open network sockets in the system. Those are, for example, ESTABLISHED state connections, but not as LISTEN.
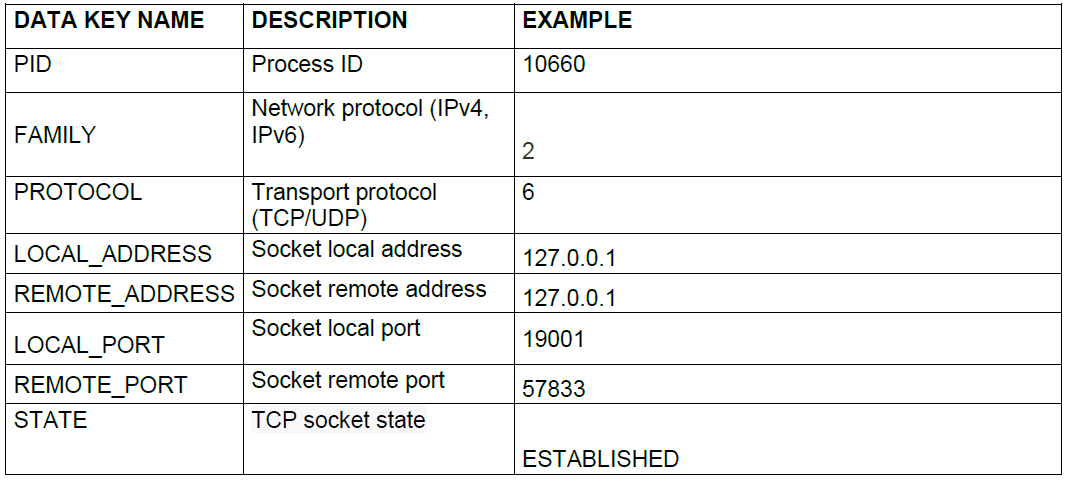
6.2.2.1.13. Open ports

This entity is formed by a list of open network sockets in the system. Those are only LISTEN state connections.
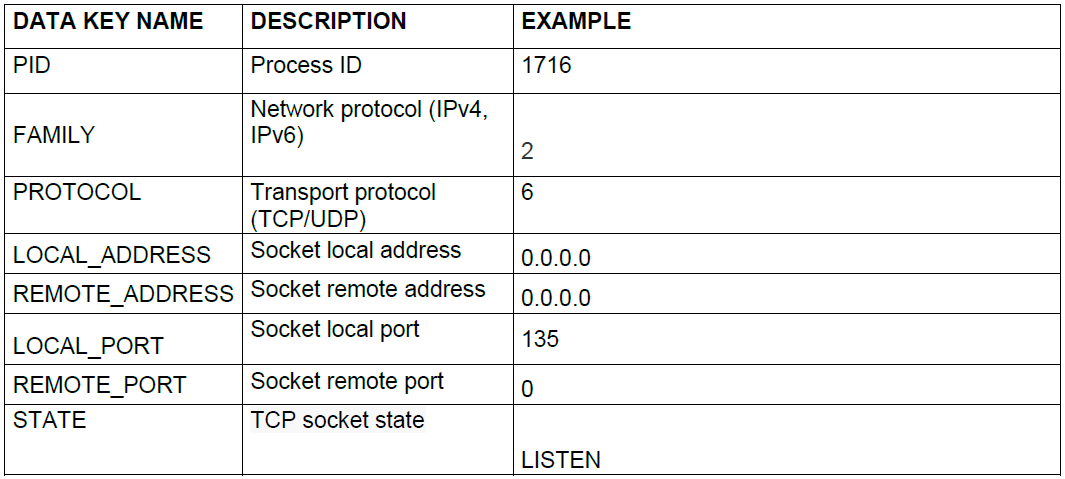
6.2.2.2. Example of payload
The payload sent to the core server always has the following format. As it can be very long, variables such as $NETWORKS have been used, in which there is a JSON object that is shown later.
{
"OPENNAC": {
"UID": "080027B598B8",
"TIMESTAMP": "1594630875",
"TYPE": "service",
"VPNVERSION": "1",
"PLATFORM": "WINDOWS",
"VERSION": "1.0.10000",
"MONITOR_TYPE": "Pipe",
"USED_INTERFACE_IP": "10.0.3.15",
"TOKEN": "164cc268-dd31-11ea-b9ca-6f6e636f7265"
},
"QueryResults": {
$NETWORKS,
$HARDWARE,
$SOFTWARES,
$SESSION_EVENTS,
$USER_ACTIVE,
$USB_DEVICES,
$SECURITY_CENTER,
$CERTIFICATES,
$WIFI,
$BROWSER_EXTENSIONS,
$PROCESSES,
$ESTABLISHED_CONNECTIONS,
$OPEN_PORTS
},
"GatherEvents": [
{
"GatherEventId": "31e3139f-d8cf-4c22-83bf-1101c8d64fec",
"GatherStartDateTime": "2020-08-04T14:25:00.0090714Z",
"GatherEndDateTime": "2020-08-04T14:25:50.9126218Z"
}
],
"IngestTriggerType": 1,
"IngestTriggerDateTime": "2020-08-04T14:25:50.9127245Z"
}
OPENNAC: This JSON object provides useful information to OpenNAC Enterprise about the Agent and the device running it.
UID: Unique identifier of the agent.
TIMESTAMP: Timestamp in which the agent payload is generated.
TYPE: The type of VLAN associated with the agent’s connection to the server.
VPNVERSION: Agent VPN version.
PLATFORM: Platform running the Agent.
VERSION: Agent version.
MONITOR_TYPE: Monitor type.
USED_INTERFACE_IP: IP address of the interface used by the agent.
TOKEN: Token generated to verify if the agent comes from a trusted source (registered agent) or not. If the agent is not registered yet, then this parameter will not exist in the payload.
QueryResults: This JSON object contains all the objects that contain device information. That is, an object for the information about the network interfaces, another object for the information regarding the hardware of the device, etc. Variables have been used to show the JSON object of each entity below.
6.2.2.2.1. $NETWORKS
"NETWORKS": {
"Results": [
{
"DESCRIPTION": "TAP-Windows Adapter V9",
"DHCP_ENABLED": "1",
"GATEWAY": "172.16.250.254",
"IPADDRESS": "172.16.250.2",
"MACADDR": "00:ff:d4:02:ee:ff",
"NAME": "Conexión de área local",
"OPER_STATUS": "2",
"TYPE": "53"
},
{
"DESCRIPTION": "Software Loopback Interface 1",
"DHCP_ENABLED": "",
"GATEWAY": "",
"IPADDRESS": "127.0.0.1",
"MACADDR": "",
"NAME": "",
"OPER_STATUS": "",
"TYPE": "24"
}
],
"GatherEventId": "31e3139f-d8cf-4c22-83bf-1101c8d64fec",
"GatherStartDateTime": "2020-08-04T14:25:00.0153703Z",
"GatherEndDateTime": "2020-08-04T14:25:00.0189955Z"
}
6.2.2.2.2. $HARDWARE
"HARDWARE":{
"Results":[
{
"ARCH":"x86_64h",
"NAME":"MacOCF",
"OSNAME":"macOS",
"OSVERSION":"11.3.1",
"OS_VM":"0",
"SERIAL_NUMBER":"C02CQ2QDMD6N",
"UNIQUE_ID":"17FA250E-DE71-5E84-8F6F-BCC7C139FA4D"
}
],
"GatherEventId":"5729a147-f64c-411a-a122-d11d4d712355",
"GatherStartDateTime":"2021-06-07T10:07:18.448242Z",
"GatherEndDateTime":"2021-06-07T10:07:18.596513Z"
}
6.2.2.2.3. $SOFTWARES
"SOFTWARES":{
"Results":[
{
"NAME":"loginwindow",
"PUBLISHER":"",
"VERSION":"9.0"
}
],
"GatherEventId":"5729a147-f64c-411a-a122-d11d4d712355",
"GatherStartDateTime":"2021-06-07T10:07:18.448242Z",
"GatherEndDateTime":"2021-06-07T10:07:18.596513Z"
}
6.2.2.2.4. $SESSION_EVENTS
"SESSION_EVENTS":{
"Results":[
{
"DOMAINNAME":"",
"EVENT":"LOGON",
"TIMESTAMP":"1623053900",
"TYPE":"LOGIN",
"USERNAME":"ocf"
}
],
"GatherEventId":"5729a147-f64c-411a-a122-d11d4d712355",
"GatherStartDateTime":"2021-06-07T08:18:41.69713Z",
"GatherEndDateTime":"2021-06-07T08:18:42.08067Z""
}
6.2.2.2.5. $USER_ACTIVE
"USER_ACTIVE":{
"Results":[
{
"NAME":"ocf"
}
],
"GatherEventId":"5729a147-f64c-411a-a122-d11d4d712355",
"GatherStartDateTime":"2021-06-07T08:18:41.69713Z",
"GatherEndDateTime":"2021-06-07T08:18:42.239818Z"
}
6.2.2.2.6. $USER_DEVICE
"USER_DEVICE":{
"Results":[
{
"DEVICE_ID":"Apple Internal Keyboard \/ Trackpad",
"HARDWARE_ID":"0280",
"MANUFACTURER":"Apple Inc."
},
{
"DEVICE_ID":"Touch Bar Backlight",
"HARDWARE_ID":"8102",
"MANUFACTURER":"Apple Inc."
},
{
"DEVICE_ID":"Headset",
"HARDWARE_ID":"8103",
"MANUFACTURER":"Apple"
},
{
"DEVICE_ID":"USB Audio",
"HARDWARE_ID":"49c5",
"MANUFACTURER":"Generic"
},
{
"DEVICE_ID":"2.4G Mouse",
"HARDWARE_ID":"0064",
"MANUFACTURER":""
}
],
"GatherEventId":"5729a147-f64c-411a-a122-d11d4d712355",
"GatherStartDateTime":"2021-06-07T08:18:41.69713Z",
"GatherEndDateTime":"2021-06-07T08:18:42.239818Z"
}
6.2.2.2.7. $SECURITY_CENTER
"SECURITY_CENTER":{
"Results":[
{
"CATEGORY":"Firewall",
"COMPANY":"Firewall de Windows",
"ENABLED":"1",
"PRODUCT":"Firewall de Windows",
"SC_ENABLED":"1",
"UPTODATE":"1"
},
{
"CATEGORY":"Antivirus",
"COMPANY":"Antivirus de Microsoft Defender",
"ENABLED":"0",
"PRODUCT":"Antivirus de Microsoft Defender",
"SC_ENABLED":"1",
"UPTODATE":"1"
},
{
"CATEGORY":"Antivirus",
"COMPANY":"Avast Antivirus",
"ENABLED":"1",
"PRODUCT":"Avast Antivirus",
"SC_ENABLED":"1",
"UPTODATE":"1"
}
],
"GatherEventId":"5729a147-f64c-411a-a122-d11d4d712355",
"GatherStartDateTime":"2021-06-07T08:18:41.69713Z",
"GatherEndDateTime":"2021-06-07T08:18:42.239818Z"
}
6.2.2.2.8. $CERTIFICATE
"CERTIFICATE":{
"Results":[
{
"END_DATE":"1755523200",
"ISSUER":"US, California, San Jose, Adobe Systems, Cloud Technology, Adobe Intermediate CA 10-4",
"START_DATE":"1534771200",
"SUBJECT":"US, California, San Jose, Adobe Systems, Cloud Technology, Adobe Content Certificate 10-6"
}
],
"GatherEventId":"5729a147-f64c-411a-a122-d11d4d712355",
"GatherStartDateTime":"2021-06-07T08:18:41.69713Z",
"GatherEndDateTime":"2021-06-07T08:18:42.239818Z"
}
6.2.2.2.9. $WIFI
"WIFI":{
"Results":[
{
"CONNECTABLE":"1",
"INTERFACE_GUID":"4d4f5649 53544152 5f453543 385f4558 54",
"IS_CONNECTED":"1",
"SECURITY":"",
"SECURITY_ENABLED":"Unknown",
"SIGNAL_QUALITY":"-68",
"SSID":"MOVISTAR_E5C8_EXT"
},
{
"CONNECTABLE":"1",
"INTERFACE_GUID":"52454d4f 54453535 73787261",
"IS_CONNECTED":"0",
"SECURITY":"",
"SECURITY_ENABLED":"Unknown",
"SIGNAL_QUALITY":"-91",
"SSID":"REMOTE55sxra"
}
],
"GatherEventId":"5729a147-f64c-411a-a122-d11d4d712355",
"GatherStartDateTime":"2021-06-07T08:18:41.69713Z",
"GatherEndDateTime":"2021-06-07T08:18:42.239818Z"
}
6.2.2.2.10. $PROCESSES”:
"PROCESSES":":{
"Results":[
{
"CMDLINE": "\\??\\C:\\WINDOWS\\system32\\conhost.exe 0x4",
"NAME": "conhost.exe",
"PARENT": "28464",
"PATH": "C:\\Windows\\System32\\conhost.exe",
"PID": "9688",
"START_TIME": "1666694790",
"THREADS": "4",
"TOTAL_SIZE": "5595136"
}
],
"GatherEventId":"5729a147-f64c-411a-a122-d11d4d712355",
"GatherStartDateTime":"2021-06-07T08:18:41.69713Z",
"GatherEndDateTime":"2021-06-07T08:18:42.239818Z"
}
6.2.2.2.11. $ESTABLISHED_CONNECTIONS
"ESTABLISHED_CONNECTIONS":{
"Results":[
{
"FAMILY": "2",
"LOCAL_ADDRESS": "10.20.250.34",
"LOCAL_PORT": "57811",
"PID": "0",
"PROTOCOL": "6",
"REMOTE_ADDRESS": "10.21.1.24",
"REMOTE_PORT": "443",
"STATE": "TIME_WAIT"
}
],
"GatherEventId":"5729a147-f64c-411a-a122-d11d4d712355",
"GatherStartDateTime":"2021-06-07T08:18:41.69713Z",
"GatherEndDateTime":"2021-06-07T08:18:42.239818Z"
}
6.2.2.2.12. $OPEN_PORTS
"OPEN_PORTS":{
"Results":[
{
"FAMILY": "2",
"LOCAL_ADDRESS": "0.0.0.0",
"LOCAL_PORT": "135",
"PID": "1716",
"PROTOCOL": "6",
"REMOTE_ADDRESS": "0.0.0.0",
"REMOTE_PORT": "0",
"STATE": "LISTEN"
}
],
"GatherEventId":"5729a147-f64c-411a-a122-d11d4d712355",
"GatherStartDateTime":"2021-06-07T08:18:41.69713Z",
"GatherEndDateTime":"2021-06-07T08:18:42.239818Z"
}